A slightly optimistic tale of how patching went for CVE-2019-19781
Since we could all probably use a little distraction from the current Solarigate/SUNBURST news[1,2,3], I thought it might be good to look at something a little bit more positive today. Specifically, at how patching of CVE-2019-19781 AKA “Shitrix” AKA “one of the more famous named vulnerabilities from the end of 2019” went.
Given that my last couple of diaries dealing with vulnerabilities discussed mainly the surprisingly high number of systems still affected by fairly old CVEs[4,5], you might reasonably ask what “positive” information might await us in this one with regards to Shitrix. In its case, however, the situation truly seems to have taken a turn for the better during 2020.
You may remember that Xavier covered the number of unpatched systems accessible from the internet in May[6] and the situation has been steadily improving since then. Based on data from Shodan, it seems that only approximately 4.5 % of the originally affected number of machines are still vulnerable.
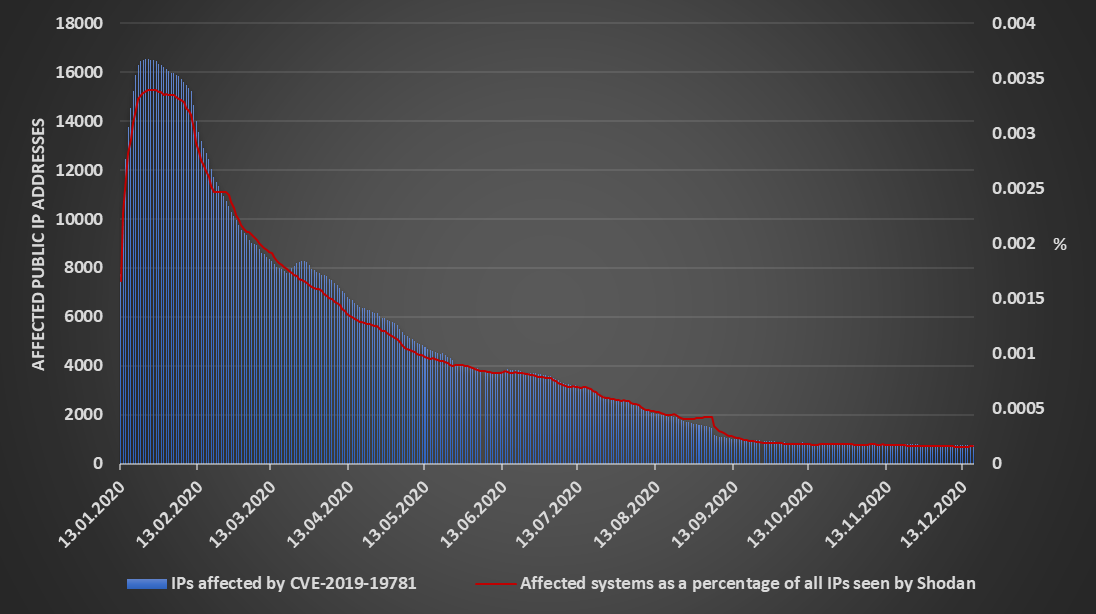
Don’t get me wrong – since vulnerable Citrix ADCs may provide (in the case of systems which are still vulnerable read “have almost certainly already provided”) a way for attackers into internal networks, even one exposed vulnerable machine is one too many. We only need to look to the Düsseldorf University Hospital ransomware attack[7] to see how significant issue an exploitation of a system affected by Shitrix many months after the first exploit was published[8] may be.
But when we compare the significant decrease in the number of systems affected by CVE-2019-19781 in 2020 with the much slower decrease we’ve seen for SMBGhost[4] or even BlueKeep[5], the situation does seem much more optimistic. We can of course hardly compare the impact of a vulnerability like Shitrix with the impact of a trojanized software update for a critical network management system, so let us hope that the response to the crisis currently facing us will be even faster than that...
Although even when it comes to and NMS such as SolarWinds Orion, one can hardly expect that all of the affected systems would eventually be free of malicious code, since not all organizations have the wherewithal to monitor security issues and mitigate them. Or, as Johannes recently put it, “some organizations care, others do not”[9].
[1] https://isc.sans.edu/forums/diary/SolarWinds+Breach+Used+to+Infiltrate+Customer+Networks+Solarigate/26884/
[2] https://www.bleepingcomputer.com/news/security/solarwinds-hackers-breach-us-nuclear-weapons-agency/
[3] https://www.reuters.com/article/us-global-cyber-microsoft-idUSKBN28R3BY
[4] https://isc.sans.edu/forums/diary/SMBGhost+the+critical+vulnerability+many+seem+to+have+forgotten+to+patch/26732/
[5] https://isc.sans.edu/forums/diary/Heartbleed+BlueKeep+and+other+vulnerabilities+that+didnt+disappear+just+because+we+dont+talk+about+them+anymore/26798/
[6] https://isc.sans.edu/forums/diary/Flashback+on+CVE201919781/26178/
[7] https://www.zdnet.com/article/first-death-reported-following-a-ransomware-attack-on-a-german-hospital/
[8] https://isc.sans.edu/forums/diary/Citrix+ADC+Exploits+Update/25724/
[9] https://www.sans.org/newsletters/newsbites/xxii/91


Comments