PATCH NOW - SIGRed - CVE-2020-1350 - Microsoft DNS Server Vulnerability
* THIS POST WILL BE UPDATED AS NEW INFORMATION BECOMES AVAILABLE *
Yesterday, Microsoft released a patch for CVE-2020-1350, fixing a critical vulnerability in it's DNS server. The vulnerability is 17 years old. All current versions of Microsoft's server back to 2003 are affected. The vulnerability earned a CVSS score of 10, indicating that it allows a full remote system compromise without any authentication. An exploit could likely spread without user interaction ("wormable").
A server is vulnerable if the DNS role is enabled. Note that Active Directory and Kerberos require DNS, and domain controllers usually have the DNS role enabled. This will put the domain controller at risk!
The vulnerability is triggered by an oversized DNS response containing a "SIG" record.
The basic exploit flow would look like:
- The attacker triggers a DNS query (for example, the victim visits a web page, or the attacker is sending an email to the victim). For a badly configured ("open recursive") name server, the attacker may just send a query to the name server directly.
- The victim DNS server will query the attacker's name server via UDP. By default, name servers will send queries via UDP first.
- The attacker responds with a truncated response, indicating that the response is too large for UDP.
- The victim will now re-send the request via TCP
- The attacker will respond with the exploit.
To trigger the exploit, the size of the response has to exceed 64kBytes. However, this does not mean that the attacker has to send more then 64kBytes (the attacker can't! DNS replies over TCP max out at 64kBytes). Instead, the attacker's response will take advantage of "pointers", to compress the response. It will be expanded (and trigger the exploit) on the victim's DNS server.
Note that some fake (prank) exploits are being advertised.
So far, one "real" PoC was released. It does not execute code but may cause the DNS server to crash. The exploit implements a simple DNS server that will respond with a truncated response to UDP queries, and an oversized SIG record if a query is sent via TCP.
Exploit: hxxps://github[.]com/maxpl0it/CVE-2020-1350-DoS [ Download at your own risk ]
PCAP collected using the exploit: https://isc.sans.edu/diaryimages/sigxploit.pcap
zeek script to detect the exploit:
event dns_unknown_reply(c: connection, msg: dns_msg, ans: dns_answer) {
if ( ans$qtype==24 && c$resp$size > 65000 ) {
print "CVE-2020-1350 Exploit";
}
}
Cisco published a rule for it's Talos/Snort subscribers (for pay only). In my experiments and as I read the rule, the rule does not work and does not look for the correct artifacts. There is an Emerging Threats rule that I have not had a chance to review.
We are monitoring for actual exploits, and expect to adjust the Infocon level to "yellow" if a working RCE exploit is released (see our Infocon page at https://isc.sans.edu/infocon.html ).
For more details, see Checkpoint's blog:
For mitigation techniques, see Microsoft's article.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
Twitter|
Word docs with macros for IcedID (Bokbot)
Introduction
Today's diary reviews Microsoft Word documents with macros to infect vulnerable Windows hosts with IcedID malware (also known as Bokbot) on Tuesday 2020-07-14. This campaign has previously pushed Valak or Ursnif, often with IcedID as the follow-up malware to these previous infections.
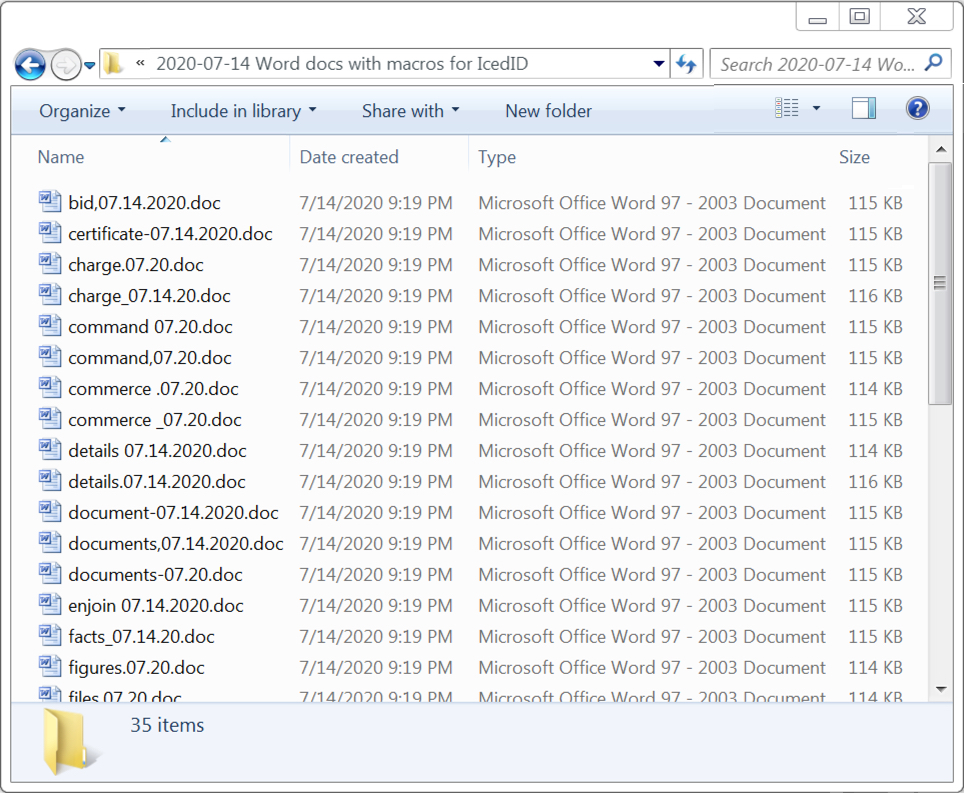
Shown above: A list for some of the Word documents seen from this campaign on 2020-07-14.
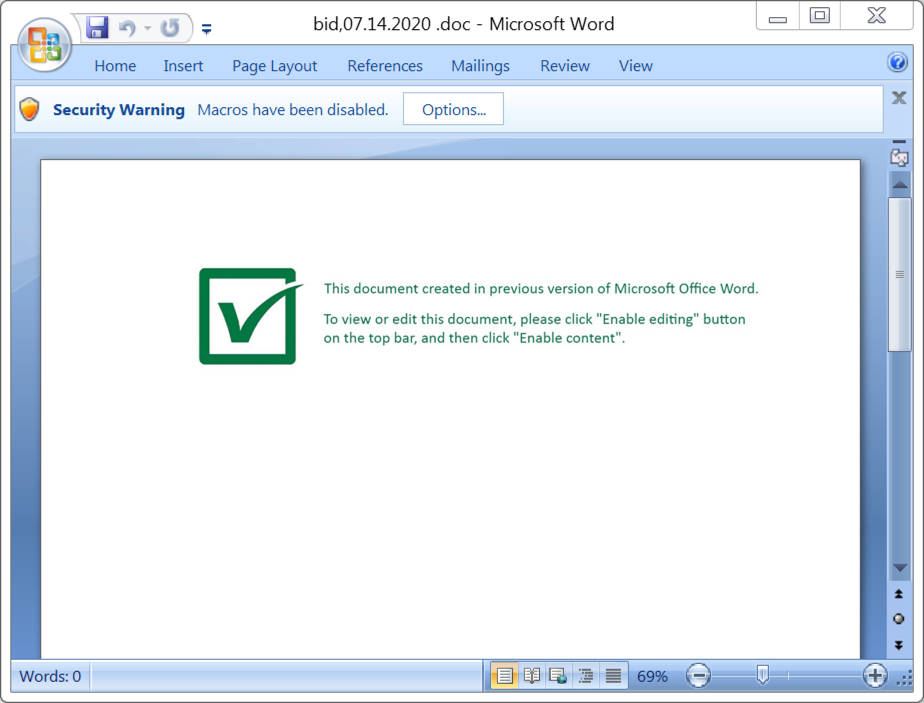
Shown above: Screenshot from one of the Word documents.
Infection activity
Enabling macros caused the victim host to generate an HTTP request ending in .cab that returned a Windows DLL file.
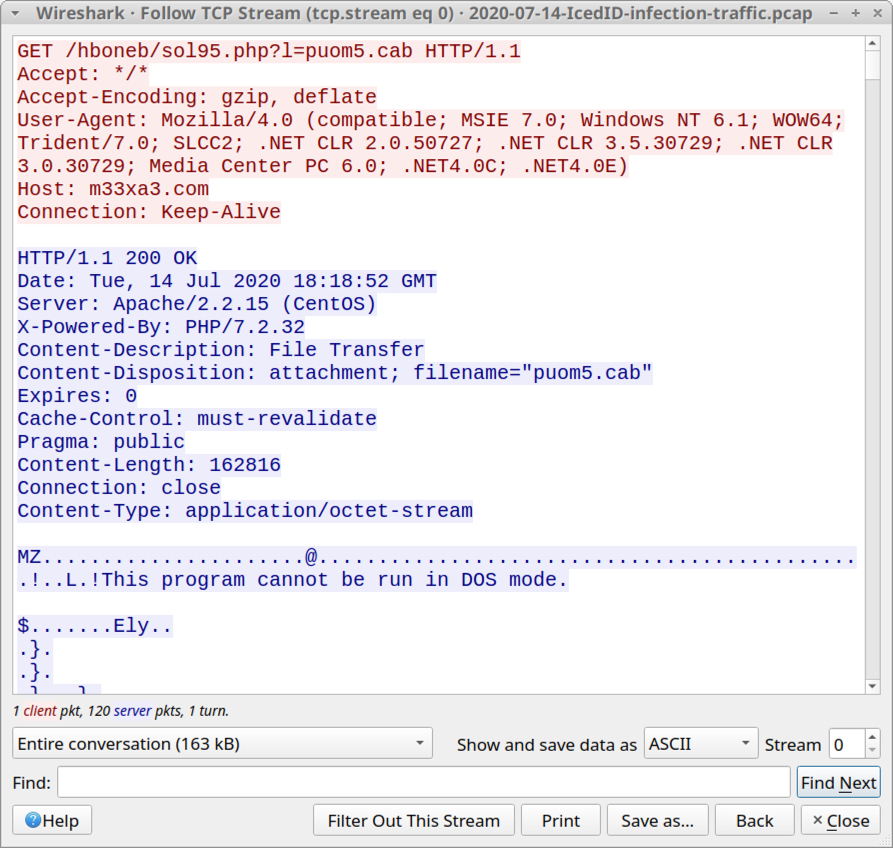
Shown above: HTTP request ending in .cab that returned a DLL file.
This DLL file was saved to the victim host in the same directory as the Word document, and it was run using regsvr32.exe [filename].
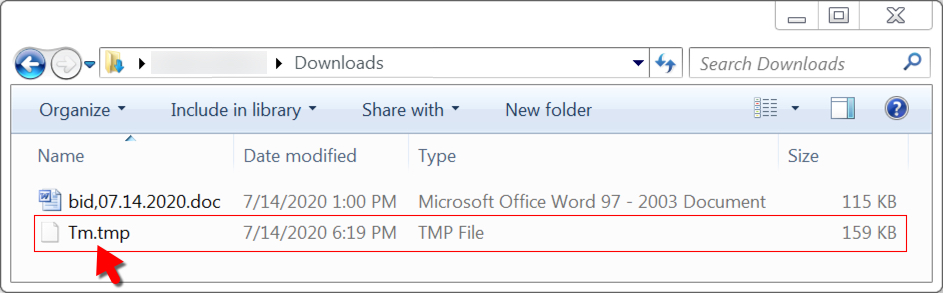
Shown above: Location the DLL was saved to on the victim host, run with regsvr32.exe.
During a successful infection, we saw HTTPS traffic to ldrglobal[.]casa and subsequent HTTPS traffic to various domain names ending in .top.
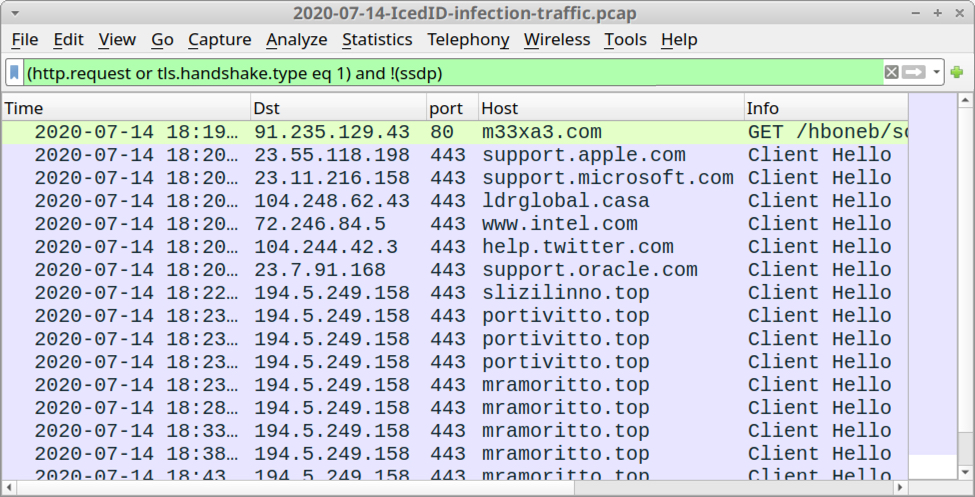
Shown above: Traffic from an infection filtered in Wireshark.
The IcedID installer uses steganography as part of its infection process, something reported in December 2019 by Malwarebytes and described by other vendors since then. We saw evidence of steganography typical with IcedID in the infected user's AppData\Local\Temp directory. In this directory, we found a file name ending in .tmp that was a PNG image file, and we also found a Windows executable (EXE) file for IcedID with a file name ending in .exe.
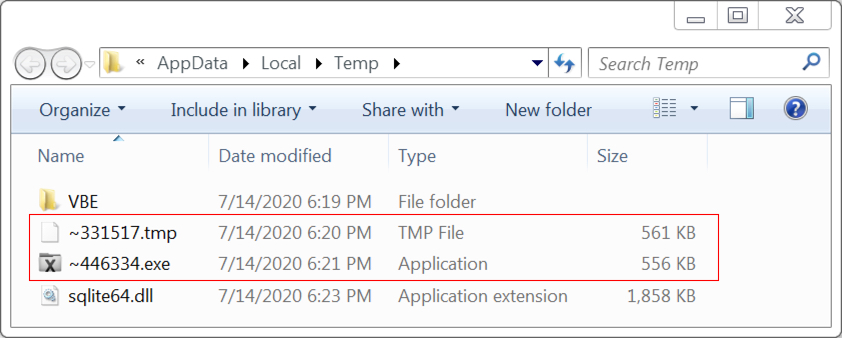
Shown above: PNG image (file name ending in .tmp) with encoded data used to create EXE for IcedID (file name ending in .exe).
During the infection process, we saw another PNG image that also has encoded data associated with the IcedID infection.
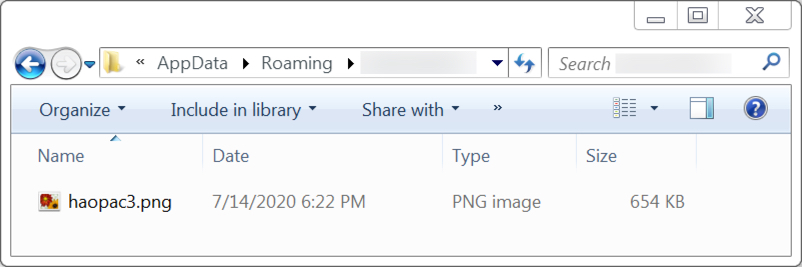
Shown above: Another PNG file containing encoded data associated with the IcedID infection.
IcedID was made persistent on the Infected Windows host through a scheduled task as shown below.
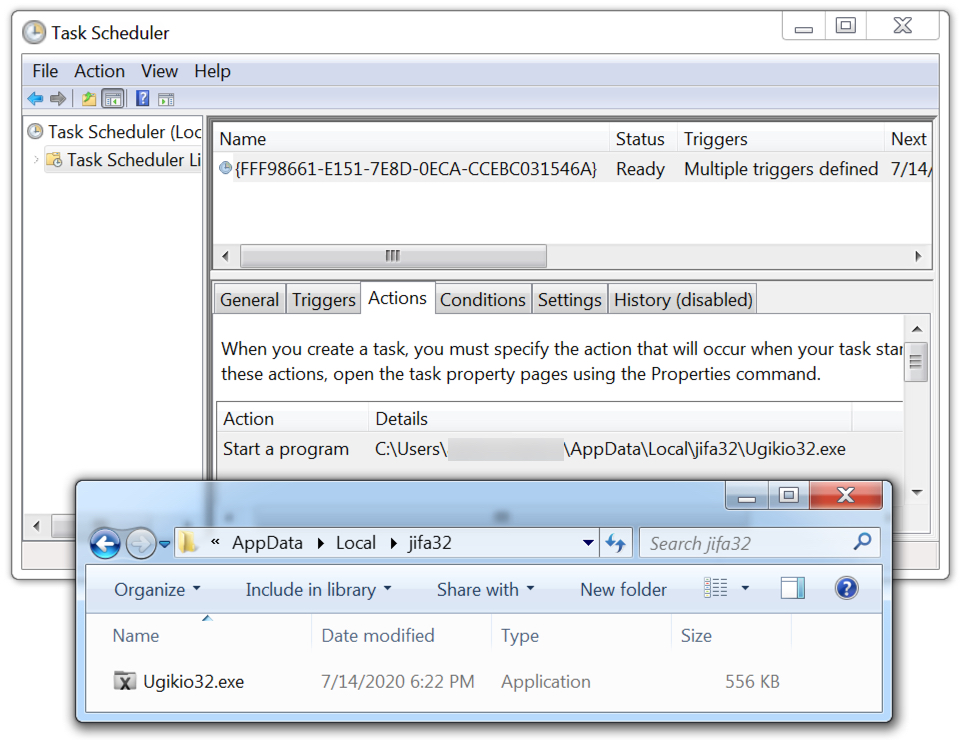
Shown above: IcedID malware persistent on the infected Windows host.
Indicators of Compromise (IOCs)
35 examples of Word docs with macros for IcedID (read: SHA256 hash file name)
- 0eb595354a8cdc77bf0a777c6d4ea5f0140ea5c7e26050325b1db7f7de50aa23 certificate-07.14.2020.doc
- 10eaa9b156e265fb23cd715743f6a99529cea188ab99a3e298a6e6ae2f957ca0 legislate 07.14.2020.doc
- 23309566de8ac0c7ae3331db0acbbc0e2d73948e83e18d17d428f38660105262 charge_07.14.20.doc
- 27c347612d0c45694f12436b87212c0bd97c7d5c9762c47364f2ade9facf5d7a bid,07.14.2020.doc
- 2bfe81e6ce5bb447a54de0aa7f99f85d893d9ac2927b03265f2faacef1533ff7 document-07.14.2020.doc
- 341c393143004d48287b363bc116151c64354ab7cbcec5dadc030e4846865486 files_07.20.doc
- 37d476eace9a5e5658238378c20ac8c58a2f20388999c32bc5519ed922fbff6f legal paper,07.14.20.doc
- 3d022cb2a7f029d9c957a4f8a34df81aa344ee081625d0d074ea3301460912ff material 07.14.20.doc
- 4362dd22eeabc132303d483dc8af3a667a8f6e7078e86df02019141bcd6a831f documents,07.14.2020.doc
- 46c0995eaebefc10ea612e09933f665883317154515e31468e135b20db433473 documents-07.20.doc
- 4a2254691a0f7724ab775469c53a01154eacb2d014cf04b71f9aa5a93834e320 instrument indenture_07.14.2020.doc
- 54a1b9d8fde754952b2e4afacc10457bdfb13325d440988cc7424984153caab3 command 07.20.doc
- 5ff7136ff81c7c7e4b324430a5a0ee98989ca597d40d4d395eda50031994fc7d legislate_07.14.2020.doc
- 67794894846550f29040574d2d2aeb8002225c17bbd47090c6d221022e9cb368 details.07.14.2020.doc
- 6c21170ee4c310fad7a989bae8c08f591f0648c4099822d7931efbbaec99fa39 legislate.07.20.doc
- 78a95425c0214c050fafa5a3cc6f40d8799a37910100781020120d12cf04dd00 charge.07.20.doc
- 7bee429e343d642a0ec076b2835e59d220374d038318a3ff87e2883b2d97df46 order,07.20.doc
- 7f4c6a6b241a89531e909def54254f995865431ae7d00ba5722b0bcdf52fb7ff inquiry,07.20.doc
- 9df7c9ac68abc525fbb685d88a91dc9fb0a62d565a61d99b1b4a9e64d2441da5 enjoin 07.14.2020.doc
- b2303e5ce1a67a85d66031163421fdb221a021fda89d21a1dba1b448acfae8eb commerce .07.20.doc
- b4810d726b778bc2f48443157985fdc981e1065454c3dfecec758a0ba39c8789 official paper,07.20.doc
- b7f2dddd27a7118f6f6cc3923f2af1f83ca5b8ea722ea05f6b27845469899c67 files.07.20.doc
- bb9b7bf7e2fdefe4fcb05e44f267239955d6c75db7ebf1d6b9926b8e4b1f3330 intelligence.07.20.doc
- bdda92c5990ded4fd7ef2c4acfa840c0c94d2d56979b99aa4c6284f33cd9d87c input_07.14.2020.doc
- c309791c87fb74d43b2b1717c6885ee38cc79971a843f14b46ccf9425fea40ea instruct_07.14.20.doc
- c91a48ee32bf0d27b05dfc3703a4ecc96941485b23055e023d0dcffccebdb802 facts_07.14.20.doc
- d089f14ebdb9ef21a02788fc7d6ee4e32667f5b9fee4ed35e871658f612766eb figures.07.20.doc
- d56151602f8851a8113244d0cd38a98a04f743abc6f1b1f0cc29fa9df9c92e9a ordain,07.14.2020.doc
- d885d083270df417a78eef7ed4d5d45111ee20e942db3500a2c48699cf8107eb inquiry_07.20.doc
- db86431d984efcabaa6645e31eb1fe9bc8ba3b5cf5b80f4eff9306c792301473 order,07.14.2020.doc
- ddf852ab72ee8ef151f6631bc3fffecd5c71ed240c53005d06d8c677a98d8725 command,07.20.doc
- eba61461d1da64f0276919d253c8eac99c6381abbab51fcf3e61b1df18fdc1d7 details 07.14.2020.doc
- ec4749ccc459451f550ef4203595161d31fd393ad2a7ef0147af060faa627308 input,07.14.2020.doc
- f68bb42ce6d65902275468d5589521805e76a06b724824eb72c6bc1754359d9e commerce _07.20.doc
- f9255ededfb06ea33aa41c77a7e664c84951fbd6f8222cf0e49340a8510b4452 inquiry_07.14.20.doc
Domains called by the Word macros for the initial malware DLL (read: domain name - IP address)
- 1bwsl4[.]com - 37.230.113[.]85
- 804gtd[.]com - 185.139.70[.]165
- m33xa3[.]com - 91.235.129[.]43
- n9i9ep[.]com - 185.144.31[.]90
- nm5oi0[.]com - 81.29.134[.]62
- uhq943[.]com - 95.181.187[.]5
HTTP GET requests for the initial malware DLL
- GET /hboneb/sol95.php?l=puom1.cab
- GET /hboneb/sol95.php?l=puom2.cab
- GET /hboneb/sol95.php?l=puom3.cab
- GET /hboneb/sol95.php?l=puom4.cab
- GET /hboneb/sol95.php?l=puom5.cab
- GET /hboneb/sol95.php?l=puom6.cab
- GET /hboneb/sol95.php?l=puom7.cab
- GET /hboneb/sol95.php?l=puom8.cab
- GET /hboneb/sol95.php?l=puom9.cab
18 examples of the initial malware DLL, all installers for IcedID (Read: SHA256 hash file name)
- 09a643588abf74030e68df106c9432ae3c5bc4fecd2afb1cca5a82b28fe30223 Tm.tmp
- 11e539a659db77e56b85608659f513e4f97b2b2d6a757b4376141eeecd3728f5 lV.tmp
- 135aecd78ba525b2cbb5547b3e43d5713fd43e3e5a9c14452fc6e25ce85998fc uZ.tmp
- 2ea61a28711cd9ac50e849c85c041faf5799e306beedaf0444df3a00a4aa0ea6 Mb.tmp
- 2f2683e21a11c6ce0848ad2a6ecc8999c91967c15a20bf2ccafe0fb9720b7607 nl.tmp
- 3fa22573e71c3c461a84acc5c469b5ec5955d317e506c854e7d2d1faea7868ea Q9.tmp
- 6fede71248803463757ea05e875e0cdb97d38245c0d28597639aa797a90987ce qg.tmp
- 7c06717c56a7890c1763ecc52950dbe81265e15910508e29c79a47a23804aec2 C8.tmp
- 7eff8901e4f77417a33b4d017a84636d2d8e04c520440511743f945e29e5dda0 d6.tmp
- a421e1ac6cd39b7709d8929329b2135cb0f1eaea48edc296d03f0b3f41058282 Hf.tmp
- a59ac4ed7c883d86bac18305763a43e86438455f259560f21fe30a10c2adb6b8 q4.tmp
- a8967cdcb91ea12285cd9f365ef73895bf90283dbc00f197cfb49cec3c8c3886 nl.tmp
- b225c3f7f23b2952c54b5d6f7b68f5b90fceb57465e552be33da54e375aab57a d6.tmp
- c1a91bfb28f0b216ccb04c7b704dfb4167a2e498cbd4c10bb954529608033aba nl.tmp
- c7fd1d9a9cd1fd3351c43763d262ba441d725ad6e34f6a842edb8ce77ac7a614 yH.tmp
- de5b9a63d071b34ca0951e2c078687d9f8ac5626eec37792c94287608da177c0 E5.tmp
- ea01f383b43070155d6ce02e6123e53f4aa29488b087f631c9ee4c8afa9da674 FZ.tmp
- ffb08f27fe1710bc42fed4f350c79885d1a176111b9e4fdcc0b077cb2fe983a7 FZ.tmp
- Note 1: These DLL files are usually located in the same directory as the Word doc. In one case, the Word doc was in the Downloads folder, but the DLL appeared in C:\Users\[username]\Documents instead.
- Note 2: Run method for these DLLs is regsvr32.exe [filename]
Traffic from a successful IcedID infection on a Windows 7 host
- port 443 (HTTPS) - support.apple.com - decoy traffic caused by IcedID (not malicious)
- port 443 (HTTPS) - support.microsoft.com - decoy traffic caused by IcedID (not malicious)
- 104.248.62[.]43 port 443 (HTTPS) - ldrglobal[.]casa - GET /background.png
- port 443 (HTTPS) - www.intel.com - decoy traffic caused by IcedID (not malicious)
- port 443 (HTTPS) - help.twitter.com - decoy traffic caused by IcedID (not malicious)
- port 443 (HTTPS) - support.oracle.com - decoy traffic caused by IcedID (not malicious)
- 194.5.249[.]158 port 443 (HTTPS) - slizilinno[.]top - HTTPS traffic caused by IcedID
- 194.5.249[.]158 port 443 (HTTPS) - portivitto[.]top - HTTPS traffic caused by IcedID
- 194.5.249[.]158 port 443 (HTTPS) - mramoritto[.]top - HTTPS traffic caused by IcedID
Malware and artifacts from the IcedID infection
SHA256 hash: a7ad6e44b04de2a1ee35ea4db024efd60d5d49a075491592ed666d187797dfd7
- File size: 573,767 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\~331517.tmp
- File type: PNG image data, 762 x 400, 8-bit/color RGB, non-interlaced
- File description: PNG image with encoded data used to create IcedID EXE below, not inherently malicious on its own
SHA256 hash: f7ba573893a9c59c66d4d54c8259ab6ac1e6e8b90c580f267a10bf333bcfd531
- File size: 569,344 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\~446334.exe
- File description: Windows executable for IcedID malware created using encoded data from the above PNG file
SHA256 hash: 9ad02a119c0df3fb652557b2b5c3136a3fb7f80e78774f1bffd5237eb2d9a514
- File size: 569,344 bytes
- File location: C:\Users\[username]\AppData\Local\jifa32\Ugikio32.exe
- File description: Windows executable IcedID malware persistent on infected host (same file as above with different hash)
SHA256 hash: e6e0adcc94c3c4979ea1659c7125a11aa7cdabe24a36f63bfe1f2aeee2c5d3a1
- File size: 669,381 bytes
- File location: C:\Users\[username]\AppData\Roaming\[username]\haopac3.png
- File type: PNG image data, 614 x 514, 8-bit/color RGB, non-interlaced
- File description: PNG image with encoded data associated with IcedID infection, not inherently malicious on its own
Final words
I normally run malware in a Windows 10 environment, but when testing these Word docs, I was unable to generate a full infection chain until I used a Windows 7 host.
This is a good reminder of how Windows 10 provide a more secure environment compared to Windows 7. People who follow best security practices while running the latest version of Windows are unlikely to get infected from this malware. However, we continue to see this and other campaigns on a daily basis. So this type of distribution apparently remains profitable for the criminals behind the malware.
A pcap of the infection traffic and malware samples for today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments