Dridex malspam seen on Monday 2017-04-10
Introduction
Malicious spam (malspam) pushing the Dridex banking Trojan disappeared in mid-2016, but it reappeared in January 2017 starting with a small campaign targeting UK financial institutions [1]. Since then, we've seen a handful of reporting about Dridex, but I hadn't noticed the same large-scale distribution like we saw in 2015 and 2016. At least not until recently.
Less than two weeks ago on 2017-03-30, high-volume waves of malspam pushing Dridex reappeared [2]. Because my last in-depth look at Dridex for the ISC was in January 2016 [3], I think it's high time we take a more current look at this malspam.
Thursday 2017-03-30
On Thursday 2017-03-30, we saw Dridex from at least two different waves of malspam [4]. In one wave of emails, attachments were zip archives containing a Visual Basic Script (.vbs) file. In the other wave, attachments were zip archives containing a Windows executable. Both attachments were double-zipped, meaning they contained a zip archive within the zip archive before you got to the malware.
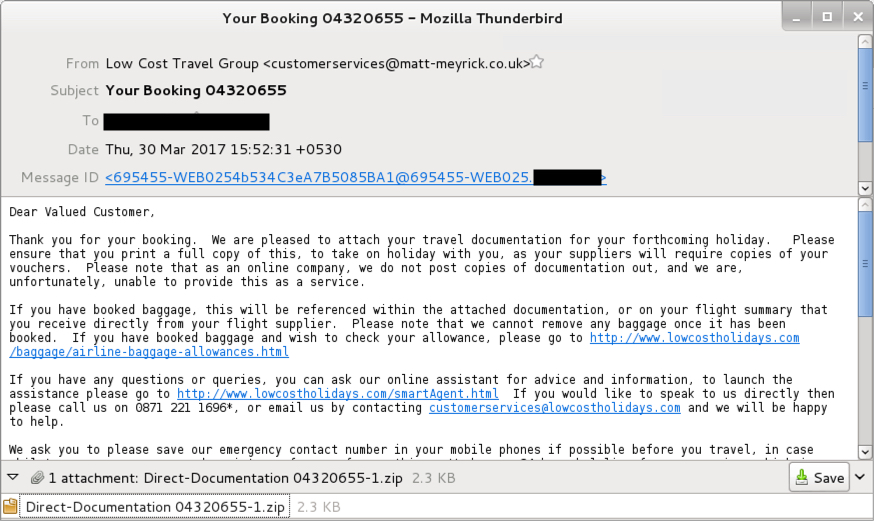
Shown above: Email from a wave of Dridex malspam on 2017-03-30.
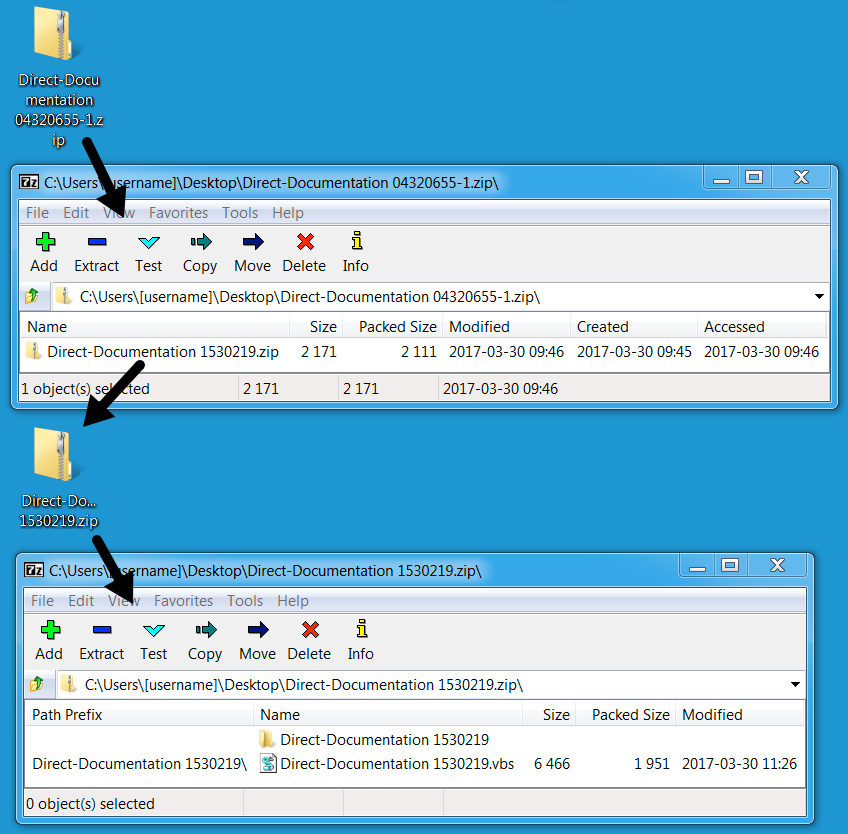
Shown above: Attachment from the above email.
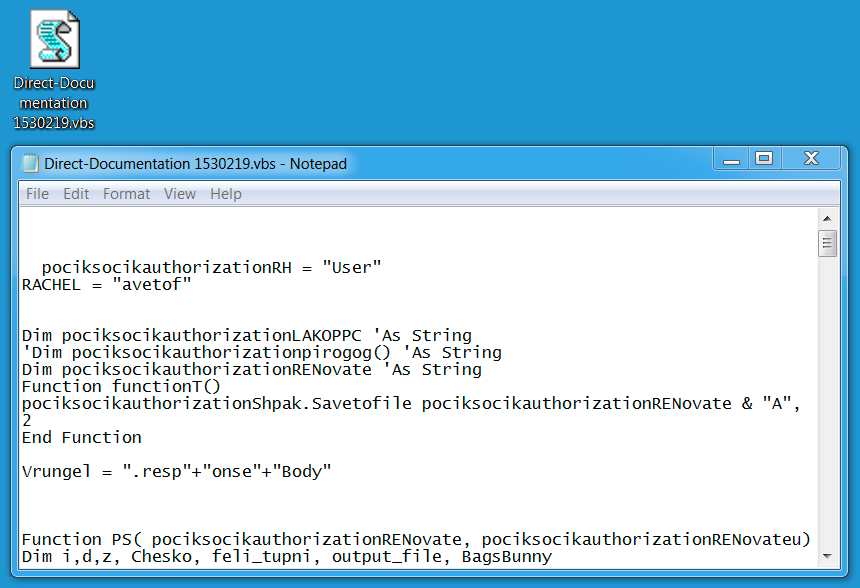
Shown above: Extracted .js file designed to download/install Dridex.

Shown above: Email from another wave of Dridex malspam on 2017-03-30.
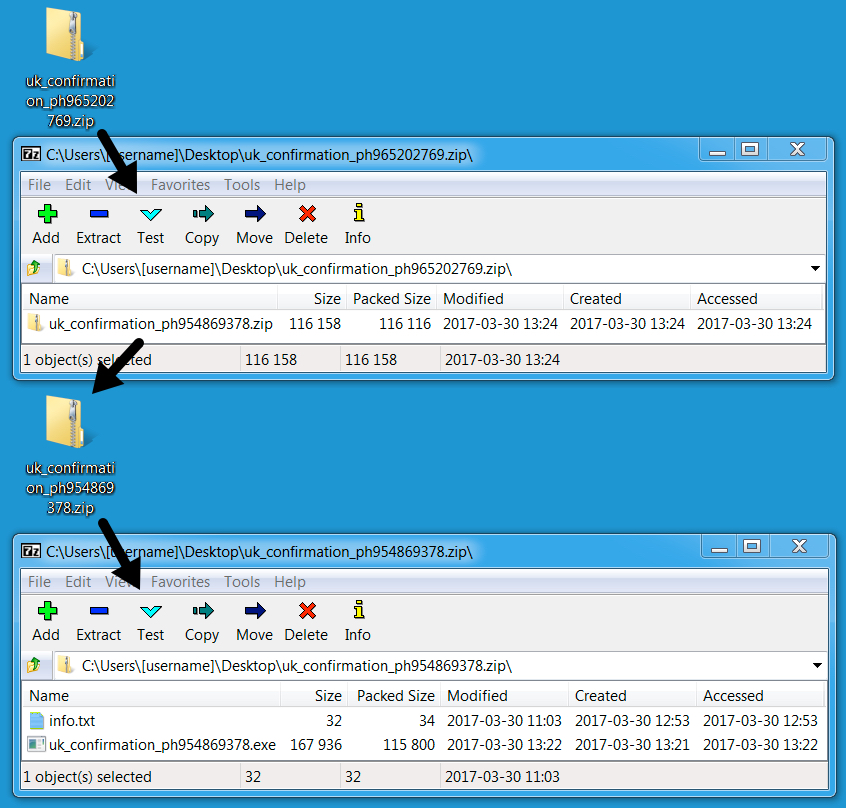
Shown above: Attachment from the above email.
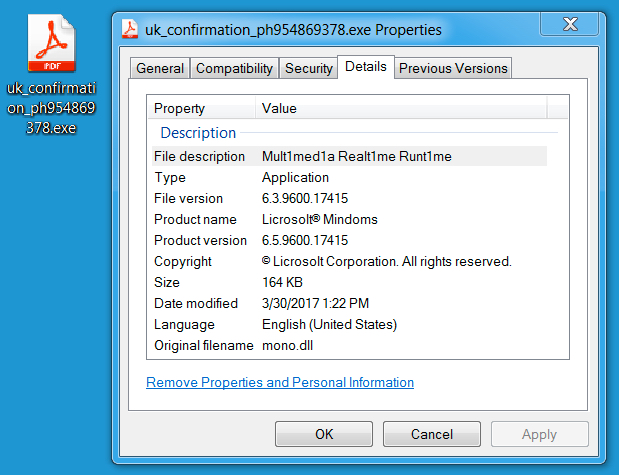
Shown above: Extracted executable (Dridex).
On Friday 2017-04-07, I saw another wave of Dridex that I didn't have time to document. Attachments were now zip archives containing Word documents. These Word documents had macros designed to download and install Dridex. Like Dridex malspam from the previous week, these archives were double-zipped.
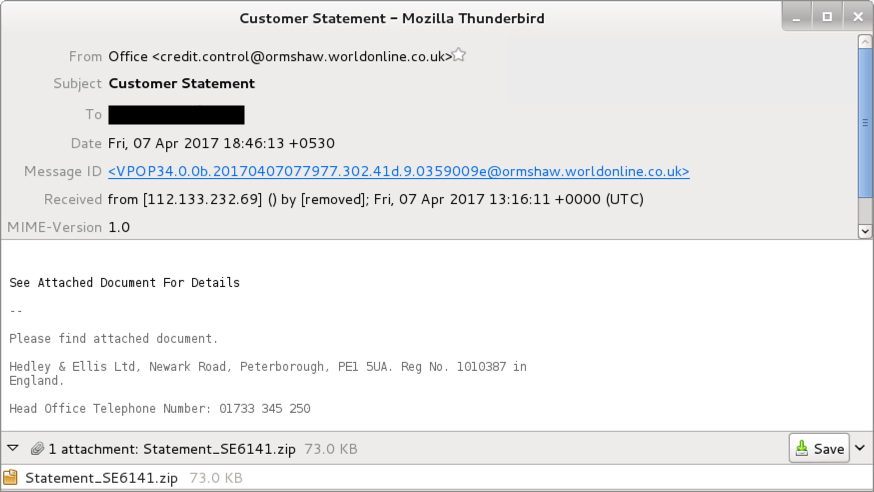
Shown above: Email from a wave of Dridex malspam on 2017-04-07.
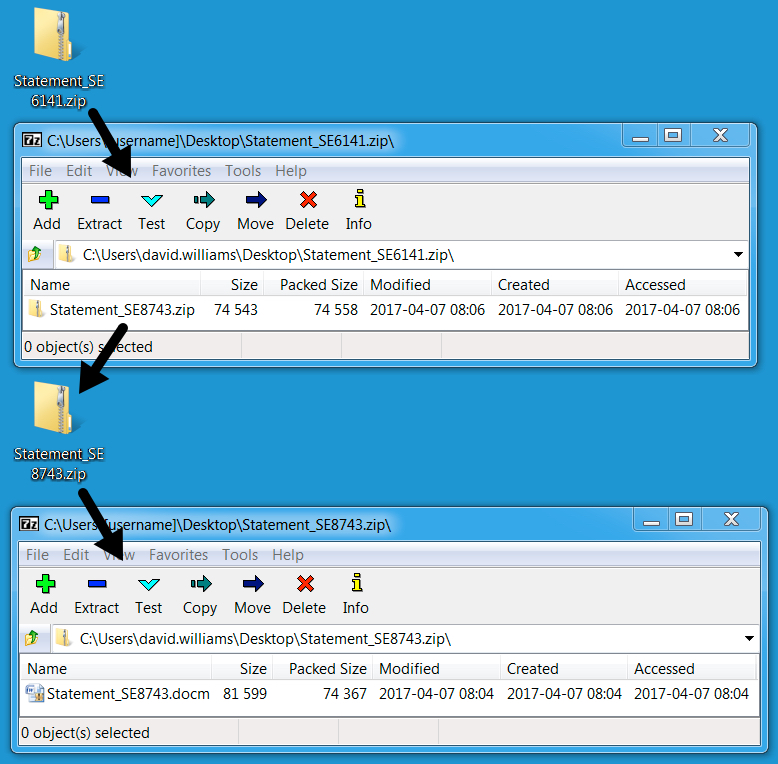
Shown above: Attachment from the above email.
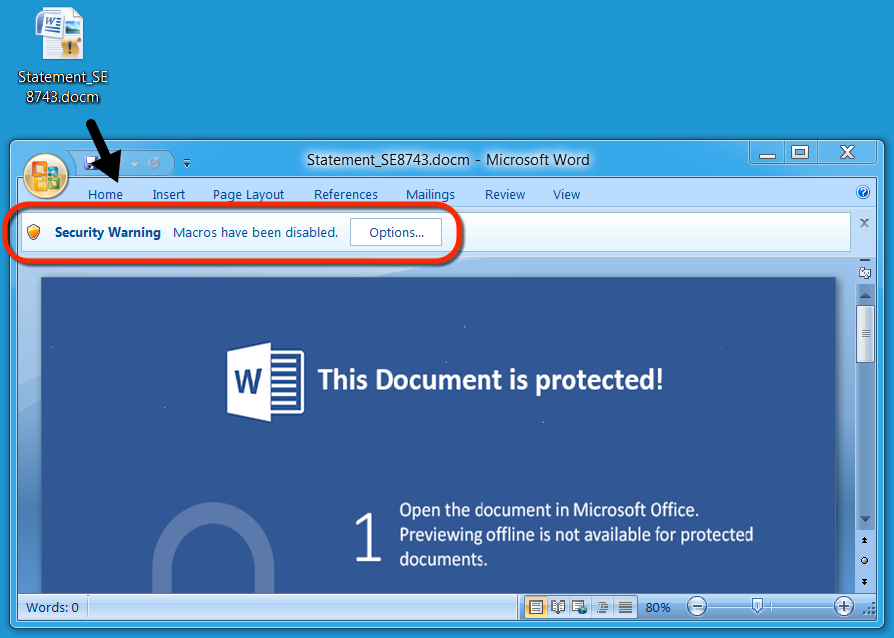
Shown above: Extracted Word document with macros designed to download/install Dridex.
Monday 2017-04-10
On Monday 2017-04-10, another wave of Dridex malspam occurred. This wave of malspam tried a new tactic. Attachments from were now PDF files with embedded Word documents. These PDF files required user action to open the Word document. Then the user had to enable macros to infect a Windows computer.
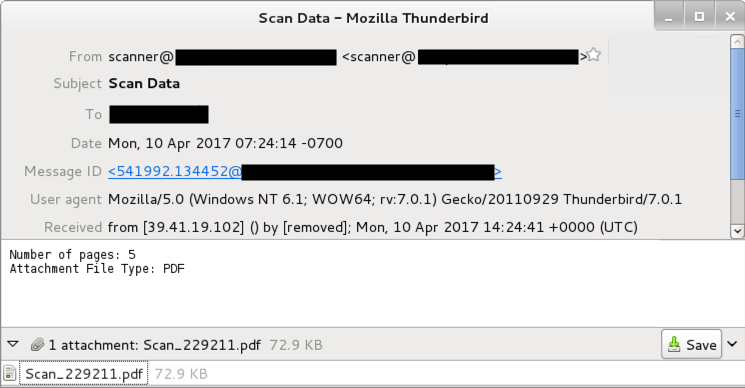
Shown above: Email from a wave of Dridex malspam on 2017-04-07.
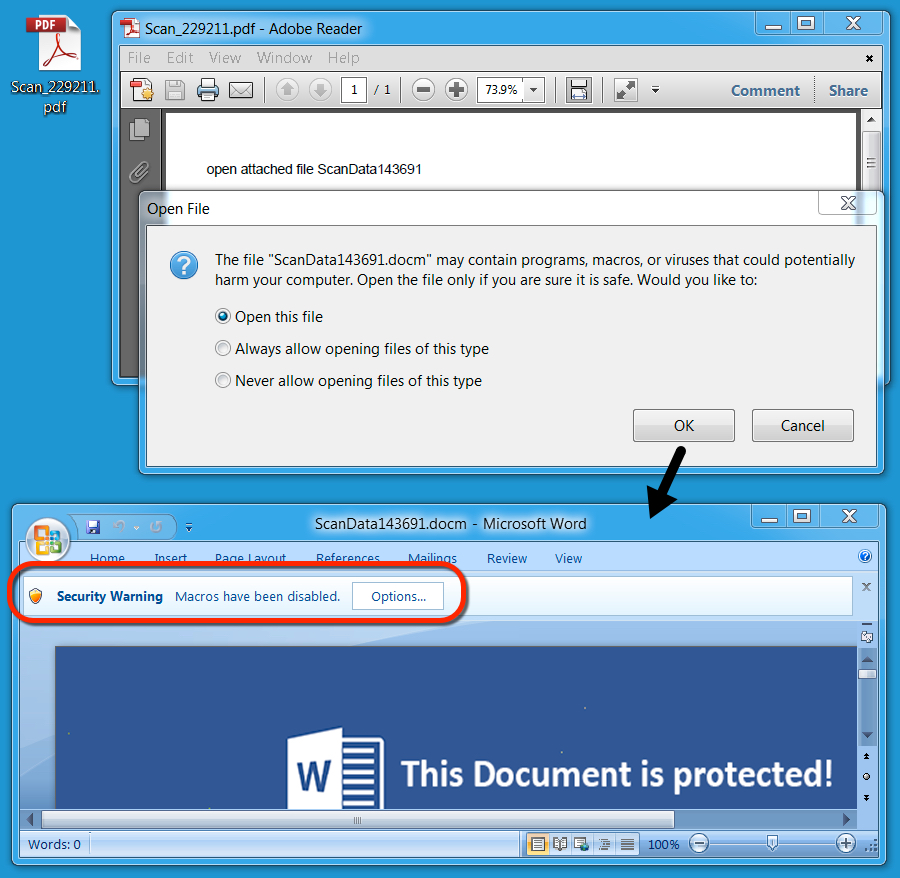
Shown above: Opening the PDF file on a Windows host leads to the embedded Word document.
I infected a Windows host by opening one of the PDF files and enabling macros for the embedded Word document. Filtering on the traffic in Wireshark, you'll see the initial HTTP request to download Dridex. Then you'll find three different IP addresses for post-infection SSL/TLS traffic associated with Dridex.
The Dridex binary was encoded while it was sent over the network. The encoded binary was saved to the Windows host at C:\Users\[username]\AppData\Local\Temp\ferbys2 where it was decoded and saved in the same directory as redchip2.exe.

Shown above: Infection traffic filtered in Wireshark: http.request or (!(tcp.port eq 80) and tcp.flags eq 0x0002).
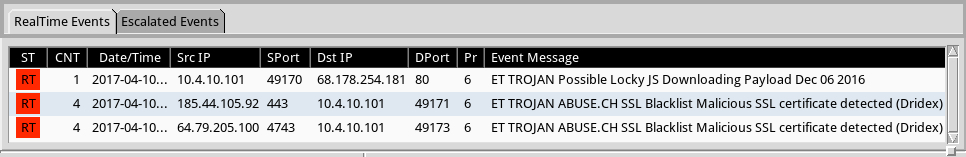
Shown above: Alerts on the traffic using Security Onion running Suricata with the Proofpoint/ET open ruleset.
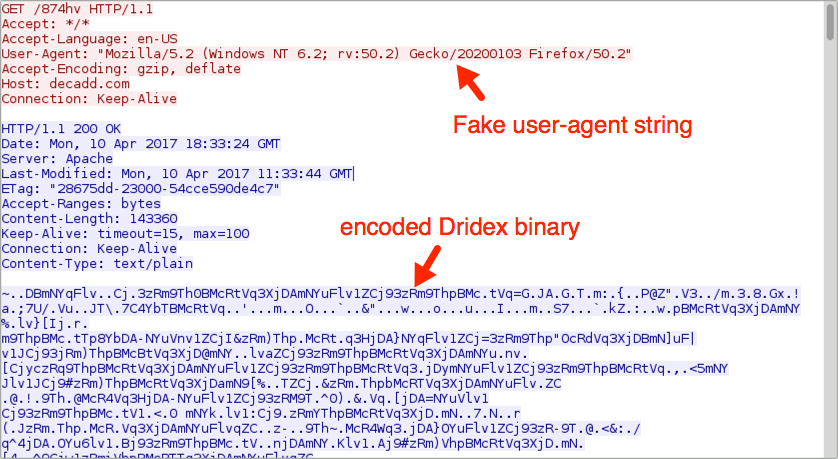
Shown above: Encoded Dridex binary retrieved by the Word macro.
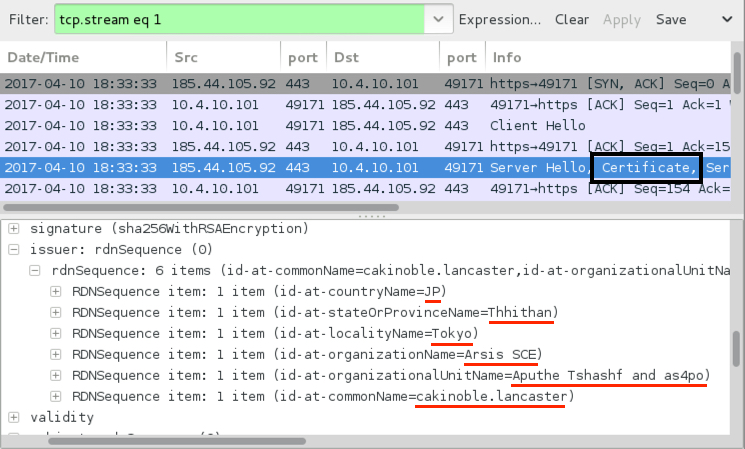
Shown above: Certificate data associated with Dridex post-infection SSL/TLS traffic.
Indicators of Compromise (IOC) from Monday 2017-04-10
The following URLs were extracted from the Word document macros seen on Monday 2017-04-10. These URLs retrieved the encoded Dridex binary. Many of these have already been taken off-line.
- 211shap.ru - GET /874hv
- anticon.net - GET /874hv
- cardoso1.com - GET /874hv
- centralsecuritybureau.com - GET /874hv
- decadd.com - GET /874hv
- designbyli.com - GET /874hv
- hiddencreek.comcastbiz.net - GET /874hv
- jheroen.nl - GET /874hv
- kapil.50webs.com - GET /874hv
- kpwc.comcastbiz.net - GET /874hv
- marinusjanssen.nl - GET /874hv
- ncdive.com - GET /874hv
- produlav.com.br - GET /874hv
- RussellYermal.com - GET /874hv
- solucionesfenix.net - GET /874hv
- super-marv.com - GET /874hv
- trans-atm.com - GET /874hv
- tserv.su - GET /874hv
- usawaterproofing.com - GET /874hv
- www.mdfond.ru - GET /874hv
Below is SSL/TLS post-infection traffic and associated certificate data from my infected Windows host on 2017-04-10:
IP address 64.79.205.100 over TCP port 4743
- countryName = ID
- stateOrProvinceName = upind0
- localityName = Jakarta
- organizationName = Tbreimem SAS
- organizationUnitName = Ptb@enc Cindusto Atoumo
- commonName = halindngofol.weadtrgtutmt.gn
IP address 185.25.184.214 over TCP port 4743
- countryName = CY
- stateOrProvinceName = Meourep Seinhadth tberese0
- localityName = Nicosia
- organizationName = Tteeran SNC
- commonName = llrrofom.fo
IP address 185.44.105.92 over TCP port 443:
- countryName = JP
- stateOrProvinceName = Thhithan
- localityName = Tokyo
- organizationName = Arsis SCE
- organizationUnitName = Aputhe Tshashf and as4po
- commonName = cakinoble.lancaster
Final words
For now, it looks like high-volume Dridex distribution through malspam is once again a feature of our current threat landscape. But how much of a threat is it?
As always, if you have a properly-configured Windows host in a well-administered environment, your risk of infection is low. But as usual, humans are the weakest link in this infection chain. If people are determined to bypass all warnings, and their systems are configured to allow it, they may very well become infected.
Emails, malware samples, and the pcap associated with 2017-04-10 Dridex malspam can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
References
[1] FlashPoint: Dridex Banking Trojan Returns, Leverages New UAC Bypass Method
[2] Proofpoint: High-Volume Dridex Campaigns Return, First to Hit Millions Since June 2016
[3] SANS Internet Storm Center (ISC): Dridex malspam example from January 2016
[4] Malware-traffic-analysis.net: 2017-03-30 - Dridex malspam (2 waves)
April 2017 Microsoft Patch Tuesday
Today on Tuesday 2017-04-11, Microsoft announced its monthly security release (also known as "Patch Tuesday). Reviewing Microsoft's Security Update Guide, it looks like there's 644 updates with 210 of them listed as "Critical" severity.
The highest profile issue from this set of updates invovles CVE-2017-0199. This vulnerablility was actively being exploited through malicious email campaigns sending Microsoft Office RTF documents as early as this past weekend.
Microsoft's April 2017 security release consists of security updates for the following software:
- Internet Explorer
- Microsoft Edge
- Microsoft Windows
- Microsoft Office and Microsoft Office Services and Web Apps
- Visual Studio for Mac
- .NET Framework
- Silverlight
- Adobe Flash Player
A full list of the 210 critical items from 2017-04-11, sorted by Knowledge Base (KB) designator, follows:
(Read: KB article -- Product -- Platform -- Details -- Severity)
- KB3118388 -- Microsoft Outlook 2010 Service Pack 2 (32-bit editions) -- N/A -- CVE-2017-0106 -- Critical
- KB3118388 -- Microsoft Outlook 2010 Service Pack 2 (64-bit editions) -- N/A -- CVE-2017-0106 -- Critical
- KB3127890 -- Microsoft Outlook 2007 Service Pack 3 -- N/A -- CVE-2017-0106 -- Critical
- KB3141529 -- Microsoft Office 2007 Service Pack 3 -- N/A -- CVE-2017-0199 -- Critical
- KB3141538 -- Microsoft Office 2010 Service Pack 2 (32-bit editions) -- N/A -- CVE-2017-0199 -- Critical
- KB3141538 -- Microsoft Office 2010 Service Pack 2 (64-bit editions) -- N/A -- CVE-2017-0199 -- Critical
- KB3172519 -- Microsoft Outlook 2013 Service Pack 1 (32-bit editions) -- N/A -- CVE-2017-0106 -- Critical
- KB3172519 -- Microsoft Outlook 2013 Service Pack 1 (64-bit editions) -- N/A -- CVE-2017-0106 -- Critical
- KB3178664 -- Microsoft Outlook 2016 (32-bit edition) -- N/A -- CVE-2017-0106 -- Critical
- KB3178664 -- Microsoft Outlook 2016 (64-bit edition) -- N/A -- CVE-2017-0106 -- Critical
- KB3178703 -- Microsoft Office 2016 (32-bit edition) -- N/A -- CVE-2017-0199 -- Critical
- KB3178703 -- Microsoft Office 2016 (64-bit edition) -- N/A -- CVE-2017-0199 -- Critical
- KB3178710 -- Microsoft Office 2013 Service Pack 1 (32-bit editions) -- N/A -- CVE-2017-0199 -- Critical
- KB3178710 -- Microsoft Office 2013 Service Pack 1 (64-bit editions) -- N/A -- CVE-2017-0199 -- Critical
- KB3211308 -- Windows Server 2008 for x64-based Systems Service Pack 2 -- N/A -- CVE-2017-0163 -- Critical
- KB3211308 -- Windows Server 2008 for x64-based Systems Service Pack 2 -- N/A -- CVE-2017-0180 -- Critical
- KB3211308 -- Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation) -- N/A -- CVE-2017-0163 -- Critical
- KB3211308 -- Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation) -- N/A -- CVE-2017-0180 -- Critical
- KB4014661 -- Internet Explorer 9 -- Windows Server 2008 for 32-bit Systems Service Pack 2 -- CVE-2017-0201 -- Critical
- KB4014661 -- Internet Explorer 9 -- Windows Server 2008 for x64-based Systems Service Pack 2 -- CVE-2017-0201 -- Critical
- KB4014661 -- Internet Explorer 9 -- Windows Vista Service Pack 2 -- CVE-2017-0201 -- Critical
- KB4014661 -- Internet Explorer 9 -- Windows Vista x64 Edition Service Pack 2 -- CVE-2017-0201 -- Critical
- KB4014981 -- Microsoft .NET Framework 3.5.1 -- Windows 7 for 32-bit Systems Service Pack 1 -- CVE-2017-0160 -- Critical
- KB4014981 -- Microsoft .NET Framework 3.5.1 -- Windows 7 for x64-based Systems Service Pack 1 -- CVE-2017-0160 -- Critical
- KB4014981 -- Microsoft .NET Framework 3.5.1 -- Windows Server 2008 R2 for Itanium-Based Systems Service Pack 1 -- CVE-2017-0160 -- Critical
- KB4014981 -- Microsoft .NET Framework 3.5.1 -- Windows Server 2008 R2 for x64-based Systems Service Pack 1 -- CVE-2017-0160 -- Critical
- KB4014981 -- Microsoft .NET Framework 3.5.1 -- Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation) -- CVE-2017-0160 -- Critical
- KB4014981 -- Microsoft .NET Framework 4.5.2 -- Windows Server 2008 for 32-bit Systems Service Pack 2 -- CVE-2017-0160 -- Critical
- KB4014981 -- Microsoft .NET Framework 4.5.2 -- Windows Server 2008 for x64-based Systems Service Pack 2 -- CVE-2017-0160 -- Critical
- KB4014981 -- Microsoft .NET Framework 4.5.2 -- Windows Vista Service Pack 2 -- CVE-2017-0160 -- Critical
- KB4014981 -- Microsoft .NET Framework 4.5.2 -- Windows Vista x64 Edition Service Pack 2 -- CVE-2017-0160 -- Critical
- KB4014981 -- Microsoft .NET Framework 4.6.2 -- Windows 7 for 32-bit Systems Service Pack 1 -- CVE-2017-0160 -- Critical
- KB4014981 -- Microsoft .NET Framework 4.6.2 -- Windows 7 for x64-based Systems Service Pack 1 -- CVE-2017-0160 -- Critical
- KB4014981 -- Microsoft .NET Framework 4.6.2 -- Windows Server 2008 R2 for x64-based Systems Service Pack 1 -- CVE-2017-0160 -- Critical
- KB4014981 -- Microsoft .NET Framework 4.6.2 -- Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation) -- CVE-2017-0160 -- Critical
- KB4014981 -- Microsoft .NET Framework 4.6/4.6.1 -- Windows 7 for 32-bit Systems Service Pack 1 -- CVE-2017-0160 -- Critical
- KB4014981 -- Microsoft .NET Framework 4.6/4.6.1 -- Windows 7 for x64-based Systems Service Pack 1 -- CVE-2017-0160 -- Critical
- KB4014981 -- Microsoft .NET Framework 4.6/4.6.1 -- Windows Server 2008 R2 for x64-based Systems Service Pack 1 -- CVE-2017-0160 -- Critical
- KB4014981 -- Microsoft .NET Framework 4.6/4.6.1 -- Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation) -- CVE-2017-0160 -- Critical
- KB4014982 -- Microsoft .NET Framework 3.5 -- Windows Server 2012 -- CVE-2017-0160 -- Critical
- KB4014982 -- Microsoft .NET Framework 3.5 -- Windows Server 2012 (Server Core installation) -- CVE-2017-0160 -- Critical
- KB4014982 -- Microsoft .NET Framework 4.5.2 -- Windows Server 2012 -- CVE-2017-0160 -- Critical
- KB4014982 -- Microsoft .NET Framework 4.5.2 -- Windows Server 2012 (Server Core installation) -- CVE-2017-0160 -- Critical
- KB4014982 -- Microsoft .NET Framework 4.6.2 -- Windows Server 2012 -- CVE-2017-0160 -- Critical
- KB4014982 -- Microsoft .NET Framework 4.6.2 -- Windows Server 2012 (Server Core installation) -- CVE-2017-0160 -- Critical
- KB4014982 -- Microsoft .NET Framework 4.6/4.6.1 -- Windows Server 2012 -- CVE-2017-0160 -- Critical
- KB4014982 -- Microsoft .NET Framework 4.6/4.6.1 -- Windows Server 2012 (Server Core installation) -- CVE-2017-0160 -- Critical
- KB4014983 -- Microsoft .NET Framework 3.5 -- Windows 8.1 for 32-bit systems -- CVE-2017-0160 -- Critical
- KB4014983 -- Microsoft .NET Framework 3.5 -- Windows 8.1 for x64-based systems -- CVE-2017-0160 -- Critical
- KB4014983 -- Microsoft .NET Framework 3.5 -- Windows Server 2012 R2 -- CVE-2017-0160 -- Critical
- KB4014983 -- Microsoft .NET Framework 3.5 -- Windows Server 2012 R2 (Server Core installation) -- CVE-2017-0160 -- Critical
- KB4014983 -- Microsoft .NET Framework 4.5.2 -- Windows 8.1 for 32-bit systems -- CVE-2017-0160 -- Critical
- KB4014983 -- Microsoft .NET Framework 4.5.2 -- Windows 8.1 for x64-based systems -- CVE-2017-0160 -- Critical
- KB4014983 -- Microsoft .NET Framework 4.5.2 -- Windows RT 8.1 -- CVE-2017-0160 -- Critical
- KB4014983 -- Microsoft .NET Framework 4.5.2 -- Windows Server 2012 R2 -- CVE-2017-0160 -- Critical
- KB4014983 -- Microsoft .NET Framework 4.5.2 -- Windows Server 2012 R2 (Server Core installation) -- CVE-2017-0160 -- Critical
- KB4014983 -- Microsoft .NET Framework 4.6.2 -- Windows 8.1 for 32-bit systems -- CVE-2017-0160 -- Critical
- KB4014983 -- Microsoft .NET Framework 4.6.2 -- Windows 8.1 for x64-based systems -- CVE-2017-0160 -- Critical
- KB4014983 -- Microsoft .NET Framework 4.6.2 -- Windows RT 8.1 -- CVE-2017-0160 -- Critical
- KB4014983 -- Microsoft .NET Framework 4.6.2 -- Windows Server 2012 R2 -- CVE-2017-0160 -- Critical
- KB4014983 -- Microsoft .NET Framework 4.6.2 -- Windows Server 2012 R2 (Server Core installation) -- CVE-2017-0160 -- Critical
- KB4014983 -- Microsoft .NET Framework 4.6/4.6.1 -- Windows 8.1 for 32-bit systems -- CVE-2017-0160 -- Critical
- KB4014983 -- Microsoft .NET Framework 4.6/4.6.1 -- Windows 8.1 for x64-based systems -- CVE-2017-0160 -- Critical
- KB4014983 -- Microsoft .NET Framework 4.6/4.6.1 -- Windows RT 8.1 -- CVE-2017-0160 -- Critical
- KB4014983 -- Microsoft .NET Framework 4.6/4.6.1 -- Windows Server 2012 R2 -- CVE-2017-0160 -- Critical
- KB4014983 -- Microsoft .NET Framework 4.6/4.6.1 -- Windows Server 2012 R2 (Server Core installation) -- CVE-2017-0160 -- Critical
- KB4014984 -- Microsoft .NET Framework 2.0 Service Pack 2 -- Windows Server 2008 for 32-bit Systems Service Pack 2 -- CVE-2017-0160 -- Critical
- KB4014984 -- Microsoft .NET Framework 2.0 Service Pack 2 -- Windows Server 2008 for Itanium-Based Systems Service Pack 2 -- CVE-2017-0160 -- Critical
- KB4014984 -- Microsoft .NET Framework 2.0 Service Pack 2 -- Windows Server 2008 for x64-based Systems Service Pack 2 -- CVE-2017-0160 -- Critical
- KB4014984 -- Microsoft .NET Framework 2.0 Service Pack 2 -- Windows Vista Service Pack 2 -- CVE-2017-0160 -- Critical
- KB4014984 -- Microsoft .NET Framework 2.0 Service Pack 2 -- Windows Vista x64 Edition Service Pack 2 -- CVE-2017-0160 -- Critical
- KB4014984 -- Microsoft .NET Framework 4.5.2 -- Windows 7 for 32-bit Systems Service Pack 1 -- CVE-2017-0160 -- Critical
- KB4014984 -- Microsoft .NET Framework 4.5.2 -- Windows 7 for x64-based Systems Service Pack 1 -- CVE-2017-0160 -- Critical
- KB4014984 -- Microsoft .NET Framework 4.5.2 -- Windows Server 2008 R2 for x64-based Systems Service Pack 1 -- CVE-2017-0160 -- Critical
- KB4014984 -- Microsoft .NET Framework 4.5.2 -- Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation) -- CVE-2017-0160 -- Critical
- KB4014984 -- Microsoft .NET Framework 4.6 -- Windows Server 2008 for 32-bit Systems Service Pack 2 -- CVE-2017-0160 -- Critical
- KB4014984 -- Microsoft .NET Framework 4.6 -- Windows Server 2008 for x64-based Systems Service Pack 2 -- CVE-2017-0160 -- Critical
- KB4014984 -- Microsoft .NET Framework 4.6 -- Windows Vista Service Pack 2 -- CVE-2017-0160 -- Critical
- KB4014984 -- Microsoft .NET Framework 4.6 -- Windows Vista x64 Edition Service Pack 2 -- CVE-2017-0160 -- Critical
- KB4015067 -- Windows Server 2008 for 32-bit Systems Service Pack 2 -- N/A -- CVE-2017-0158 -- Critical
- KB4015067 -- Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation) -- N/A -- CVE-2017-0158 -- Critical
- KB4015067 -- Windows Server 2008 for Itanium-Based Systems Service Pack 2 -- N/A -- CVE-2017-0158 -- Critical
- KB4015067 -- Windows Server 2008 for x64-based Systems Service Pack 2 -- N/A -- CVE-2017-0158 -- Critical
- KB4015067 -- Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation) -- N/A -- CVE-2017-0158 -- Critical
- KB4015067 -- Windows Vista Service Pack 2 -- N/A -- CVE-2017-0158 -- Critical
- KB4015067 -- Windows Vista x64 Edition Service Pack 2 -- N/A -- CVE-2017-0158 -- Critical
- KB4015217 -- Internet Explorer 11 -- Windows 10 Version 1607 for 32-bit Systems -- CVE-2017-0202 -- Critical
- KB4015217 -- Internet Explorer 11 -- Windows 10 Version 1607 for x64-based Systems -- CVE-2017-0202 -- Critical
- KB4015217 -- Internet Explorer 11 -- Windows Server 2016 -- CVE-2017-0202 -- Critical
- KB4015217 -- Microsoft .NET Framework 3.5 -- Windows 10 Version 1607 for 32-bit Systems -- CVE-2017-0160 -- Critical
- KB4015217 -- Microsoft .NET Framework 3.5 -- Windows 10 Version 1607 for x64-based Systems -- CVE-2017-0160 -- Critical
- KB4015217 -- Microsoft .NET Framework 3.5 -- Windows Server 2016 -- CVE-2017-0160 -- Critical
- KB4015217 -- Microsoft .NET Framework 3.5 -- Windows Server 2016 (Server Core installation) -- CVE-2017-0160 -- Critical
- KB4015217 -- Microsoft .NET Framework 4.6.2 -- Windows 10 Version 1607 for 32-bit Systems -- CVE-2017-0160 -- Critical
- KB4015217 -- Microsoft .NET Framework 4.6.2 -- Windows 10 Version 1607 for x64-based Systems -- CVE-2017-0160 -- Critical
- KB4015217 -- Microsoft .NET Framework 4.6.2 -- Windows Server 2016 -- CVE-2017-0160 -- Critical
- KB4015217 -- Microsoft .NET Framework 4.6.2 -- Windows Server 2016 (Server Core installation) -- CVE-2017-0160 -- Critical
- KB4015217 -- Microsoft Edge -- Windows 10 Version 1607 for 32-bit Systems -- CVE-2017-0093 -- Critical
- KB4015217 -- Microsoft Edge -- Windows 10 Version 1607 for 32-bit Systems -- CVE-2017-0200 -- Critical
- KB4015217 -- Microsoft Edge -- Windows 10 Version 1607 for 32-bit Systems -- CVE-2017-0205 -- Critical
- KB4015217 -- Microsoft Edge -- Windows 10 Version 1607 for x64-based Systems -- CVE-2017-0093 -- Critical
- KB4015217 -- Microsoft Edge -- Windows 10 Version 1607 for x64-based Systems -- CVE-2017-0200 -- Critical
- KB4015217 -- Microsoft Edge -- Windows 10 Version 1607 for x64-based Systems -- CVE-2017-0205 -- Critical
- KB4015217 -- Windows 10 Version 1607 for 32-bit Systems -- N/A -- CVE-2017-0158 -- Critical
- KB4015217 -- Windows 10 Version 1607 for x64-based Systems -- N/A -- CVE-2017-0158 -- Critical
- KB4015217 -- Windows 10 Version 1607 for x64-based Systems -- N/A -- CVE-2017-0162 -- Critical
- KB4015217 -- Windows 10 Version 1607 for x64-based Systems -- N/A -- CVE-2017-0163 -- Critical
- KB4015217 -- Windows 10 Version 1607 for x64-based Systems -- N/A -- CVE-2017-0180 -- Critical
- KB4015217 -- Windows 10 Version 1607 for x64-based Systems -- N/A -- CVE-2017-0181 -- Critical
- KB4015217 -- Windows Server 2016 -- N/A -- CVE-2017-0158 -- Critical
- KB4015217 -- Windows Server 2016 -- N/A -- CVE-2017-0162 -- Critical
- KB4015217 -- Windows Server 2016 -- N/A -- CVE-2017-0163 -- Critical
- KB4015217 -- Windows Server 2016 -- N/A -- CVE-2017-0180 -- Critical
- KB4015217 -- Windows Server 2016 -- N/A -- CVE-2017-0181 -- Critical
- KB4015217 -- Windows Server 2016 (Server Core installation) -- N/A -- CVE-2017-0158 -- Critical
- KB4015217 -- Windows Server 2016 (Server Core installation) -- N/A -- CVE-2017-0162 -- Critical
- KB4015217 -- Windows Server 2016 (Server Core installation) -- N/A -- CVE-2017-0163 -- Critical
- KB4015217 -- Windows Server 2016 (Server Core installation) -- N/A -- CVE-2017-0180 -- Critical
- KB4015217 -- Windows Server 2016 (Server Core installation) -- N/A -- CVE-2017-0181 -- Critical
- KB4015219 -- Internet Explorer 11 -- Windows 10 Version 1511 for 32-bit Systems -- CVE-2017-0202 -- Critical
- KB4015219 -- Internet Explorer 11 -- Windows 10 Version 1511 for x64-based Systems -- CVE-2017-0202 -- Critical
- KB4015219 -- Microsoft .NET Framework 3.5 -- Windows 10 Version 1511 for 32-bit Systems -- CVE-2017-0160 -- Critical
- KB4015219 -- Microsoft .NET Framework 3.5 -- Windows 10 Version 1511 for x64-based Systems -- CVE-2017-0160 -- Critical
- KB4015219 -- Microsoft .NET Framework 4.6.1 -- Windows 10 Version 1511 for 32-bit Systems -- CVE-2017-0160 -- Critical
- KB4015219 -- Microsoft .NET Framework 4.6.1 -- Windows 10 Version 1511 for x64-based Systems -- CVE-2017-0160 -- Critical
- KB4015219 -- Microsoft Edge -- Windows 10 Version 1511 for 32-bit Systems -- CVE-2017-0093 -- Critical
- KB4015219 -- Microsoft Edge -- Windows 10 Version 1511 for 32-bit Systems -- CVE-2017-0205 -- Critical
- KB4015219 -- Microsoft Edge -- Windows 10 Version 1511 for x64-based Systems -- CVE-2017-0093 -- Critical
- KB4015219 -- Microsoft Edge -- Windows 10 Version 1511 for x64-based Systems -- CVE-2017-0205 -- Critical
- KB4015219 -- Windows 10 Version 1511 for 32-bit Systems -- N/A -- CVE-2017-0158 -- Critical
- KB4015219 -- Windows 10 Version 1511 for x64-based Systems -- N/A -- CVE-2017-0158 -- Critical
- KB4015219 -- Windows 10 Version 1511 for x64-based Systems -- N/A -- CVE-2017-0162 -- Critical
- KB4015219 -- Windows 10 Version 1511 for x64-based Systems -- N/A -- CVE-2017-0163 -- Critical
- KB4015219 -- Windows 10 Version 1511 for x64-based Systems -- N/A -- CVE-2017-0180 -- Critical
- KB4015219 -- Windows 10 Version 1511 for x64-based Systems -- N/A -- CVE-2017-0181 -- Critical
- KB4015221 -- Internet Explorer 11 -- Windows 10 for 32-bit Systems -- CVE-2017-0202 -- Critical
- KB4015221 -- Internet Explorer 11 -- Windows 10 for x64-based Systems -- CVE-2017-0202 -- Critical
- KB4015221 -- Microsoft .NET Framework 3.5 -- Windows 10 for 32-bit Systems -- CVE-2017-0160 -- Critical
- KB4015221 -- Microsoft .NET Framework 3.5 -- Windows 10 for x64-based Systems -- CVE-2017-0160 -- Critical
- KB4015221 -- Microsoft .NET Framework 4.6 -- Windows 10 for 32-bit Systems -- CVE-2017-0160 -- Critical
- KB4015221 -- Microsoft .NET Framework 4.6 -- Windows 10 for x64-based Systems -- CVE-2017-0160 -- Critical
- KB4015221 -- Windows 10 for 32-bit Systems -- N/A -- CVE-2017-0158 -- Critical
- KB4015221 -- Windows 10 for x64-based Systems -- N/A -- CVE-2017-0158 -- Critical
- KB4015221 -- Windows 10 for x64-based Systems -- N/A -- CVE-2017-0162 -- Critical
- KB4015221 -- Windows 10 for x64-based Systems -- N/A -- CVE-2017-0163 -- Critical
- KB4015221 -- Windows 10 for x64-based Systems -- N/A -- CVE-2017-0180 -- Critical
- KB4015221 -- Windows 10 for x64-based Systems -- N/A -- CVE-2017-0181 -- Critical
- KB4015549 -- Windows 7 for 32-bit Systems Service Pack 1 -- N/A -- CVE-2017-0158 -- Critical
- KB4015549 -- Windows 7 for x64-based Systems Service Pack 1 -- N/A -- CVE-2017-0158 -- Critical
- KB4015549 -- Windows Server 2008 R2 for Itanium-Based Systems Service Pack 1 -- N/A -- CVE-2017-0158 -- Critical
- KB4015549 -- Windows Server 2008 R2 for x64-based Systems Service Pack 1 -- N/A -- CVE-2017-0158 -- Critical
- KB4015549 -- Windows Server 2008 R2 for x64-based Systems Service Pack 1 -- N/A -- CVE-2017-0180 -- Critical
- KB4015549 -- Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation) -- N/A -- CVE-2017-0158 -- Critical
- KB4015549 -- Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation) -- N/A -- CVE-2017-0163 -- Critical
- KB4015549 -- Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation) -- N/A -- CVE-2017-0180 -- Critical
- KB4015550 -- Internet Explorer 11 -- Windows 8.1 for 32-bit systems -- CVE-2017-0202 -- Critical
- KB4015550 -- Internet Explorer 11 -- Windows 8.1 for x64-based systems -- CVE-2017-0202 -- Critical
- KB4015550 -- Internet Explorer 11 -- Windows RT 8.1 -- CVE-2017-0202 -- Critical
- KB4015550 -- Internet Explorer 11 -- Windows Server 2012 R2 -- CVE-2017-0202 -- Critical
- KB4015550 -- Windows 8.1 for 32-bit systems -- N/A -- CVE-2017-0158 -- Critical
- KB4015550 -- Windows 8.1 for x64-based systems -- N/A -- CVE-2017-0158 -- Critical
- KB4015550 -- Windows 8.1 for x64-based systems -- N/A -- CVE-2017-0162 -- Critical
- KB4015550 -- Windows 8.1 for x64-based systems -- N/A -- CVE-2017-0163 -- Critical
- KB4015550 -- Windows 8.1 for x64-based systems -- N/A -- CVE-2017-0180 -- Critical
- KB4015550 -- Windows RT 8.1 -- N/A -- CVE-2017-0158 -- Critical
- KB4015550 -- Windows Server 2012 R2 -- N/A -- CVE-2017-0158 -- Critical
- KB4015550 -- Windows Server 2012 R2 -- N/A -- CVE-2017-0162 -- Critical
- KB4015550 -- Windows Server 2012 R2 -- N/A -- CVE-2017-0163 -- Critical
- KB4015550 -- Windows Server 2012 R2 -- N/A -- CVE-2017-0180 -- Critical
- KB4015550 -- Windows Server 2012 R2 (Server Core installation) -- N/A -- CVE-2017-0158 -- Critical
- KB4015550 -- Windows Server 2012 R2 (Server Core installation) -- N/A -- CVE-2017-0162 -- Critical
- KB4015550 -- Windows Server 2012 R2 (Server Core installation) -- N/A -- CVE-2017-0163 -- Critical
- KB4015550 -- Windows Server 2012 R2 (Server Core installation) -- N/A -- CVE-2017-0180 -- Critical
- KB4015551 -- Internet Explorer 10 -- Windows Server 2012 -- CVE-2017-0201 -- Critical
- KB4015551 -- Windows Server 2012 -- N/A -- CVE-2017-0158 -- Critical
- KB4015551 -- Windows Server 2012 -- N/A -- CVE-2017-0163 -- Critical
- KB4015551 -- Windows Server 2012 -- N/A -- CVE-2017-0180 -- Critical
- KB4015551 -- Windows Server 2012 (Server Core installation) -- N/A -- CVE-2017-0158 -- Critical
- KB4015551 -- Windows Server 2012 (Server Core installation) -- N/A -- CVE-2017-0163 -- Critical
- KB4015551 -- Windows Server 2012 (Server Core installation) -- N/A -- CVE-2017-0180 -- Critical
- KB4015583 -- Internet Explorer 11 -- Windows 10 Version 1703 for 32-bit Systems -- CVE-2017-0202 -- Critical
- KB4015583 -- Internet Explorer 11 -- Windows 10 Version 1703 for x64-based Systems -- CVE-2017-0202 -- Critical
- KB4015583 -- Microsoft .NET Framework 3.5 -- Windows 10 Version 1703 for 32-bit Systems -- CVE-2017-0160 -- Critical
- KB4015583 -- Microsoft .NET Framework 3.5 -- Windows 10 Version 1703 for x64-based Systems -- CVE-2017-0160 -- Critical
- KB4015583 -- Microsoft .NET Framework 4.7 -- Windows 10 Version 1703 for 32-bit Systems -- CVE-2017-0160 -- Critical
- KB4015583 -- Microsoft .NET Framework 4.7 -- Windows 10 Version 1703 for x64-based Systems -- CVE-2017-0160 -- Critical
- KB4015583 -- Microsoft Edge -- Windows 10 Version 1703 for 32-bit Systems -- CVE-2017-0093 -- Critical
- KB4015583 -- Microsoft Edge -- Windows 10 Version 1703 for 32-bit Systems -- CVE-2017-0205 -- Critical
- KB4015583 -- Microsoft Edge -- Windows 10 Version 1703 for x64-based Systems -- CVE-2017-0093 -- Critical
- KB4015583 -- Microsoft Edge -- Windows 10 Version 1703 for x64-based Systems -- CVE-2017-0205 -- Critical
- KB4015583 -- Windows 10 Version 1703 for 32-bit Systems -- N/A -- CVE-2017-0158 -- Critical
- KB4015583 -- Windows 10 Version 1703 for x64-based Systems -- N/A -- CVE-2017-0158 -- Critical
- KB4015583 -- Windows 10 Version 1703 for x64-based Systems -- N/A -- CVE-2017-0162 -- Critical
- KB4015583 -- Windows 10 Version 1703 for x64-based Systems -- N/A -- CVE-2017-0163 -- Critical
- KB4015583 -- Windows 10 Version 1703 for x64-based Systems -- N/A -- CVE-2017-0180 -- Critical
- KB4015583 -- Windows 10 Version 1703 for x64-based Systems -- N/A -- CVE-2017-0181 -- Critical
- KB4018483 -- Adobe Flash Player -- Windows 10 for 32-bit Systems -- 2017-3447 -- Critical
- KB4018483 -- Adobe Flash Player -- Windows 10 for x64-based Systems -- 2017-3447 -- Critical
- KB4018483 -- Adobe Flash Player -- Windows 10 Version 1511 for 32-bit Systems -- 2017-3447 -- Critical
- KB4018483 -- Adobe Flash Player -- Windows 10 Version 1511 for x64-based Systems -- 2017-3447 -- Critical
- KB4018483 -- Adobe Flash Player -- Windows 10 Version 1607 for 32-bit Systems -- 2017-3447 -- Critical
- KB4018483 -- Adobe Flash Player -- Windows 10 Version 1607 for x64-based Systems -- 2017-3447 -- Critical
- KB4018483 -- Adobe Flash Player -- Windows 10 Version 1703 for 32-bit Systems -- 2017-3447 -- Critical
- KB4018483 -- Adobe Flash Player -- Windows 10 Version 1703 for x64-based Systems -- 2017-3447 -- Critical
- KB4018483 -- Adobe Flash Player -- Windows 8.1 for 32-bit systems -- 2017-3447 -- Critical
- KB4018483 -- Adobe Flash Player -- Windows 8.1 for x64-based systems -- 2017-3447 -- Critical
- KB4018483 -- Adobe Flash Player -- Windows RT 8.1 -- 2017-3447 -- Critical
- KB4018483 -- Adobe Flash Player -- Windows Server 2012 -- 2017-3447 -- Critical
- KB4018483 -- Adobe Flash Player -- Windows Server 2012 R2 -- 2017-3447 -- Critical
- KB4018483 -- Adobe Flash Player -- Windows Server 2016 -- 2017-3447 -- Critical


Comments