Malspam delivers NanoCore RAT
Introduction
NanoCore is a Remote Access Tool (RAT) that's currently available for a $25 license [1]. However, like many other RATs, NanoCore has been used by criminal groups to take over Windows computers. Beta versions of NanoCore RAT have been available to criminals since 2013 [2], and a cracked full version was leaked last year in 2015 [3].
Since then, the NanoCore RAT has been used in targeted phishing campaigns that are subtle and harder to detect [4]. Earlier this year, we saw it used in tax-themed emails as part of an increased distribution of the full-featured NanoCore RAT through phishing [5].
Since then, I haven't noticed any public reporting on specific campaigns, even though I've noticed NanoCore RAT-based phishing emails on a near-daily basis. These recent emails don't seem subtle, and the vast majority of them are blocked. I consider these recent examples malicious spam (malspam). They either have attached zip archives containing an executable file, or they have attached Microsoft Office documents with malicious macros designed to download and execute the NanoCore RAT. One such malspam with a zip attachment was recently sent to my malware-traffic-analysis.net email address. That one was easily caught by my spam filter.
Due to a relative lack of publicly-posted info on recent NanoCore RAT malspam campaigns, I thought I'd examine the email I received for today's dairy.
The email
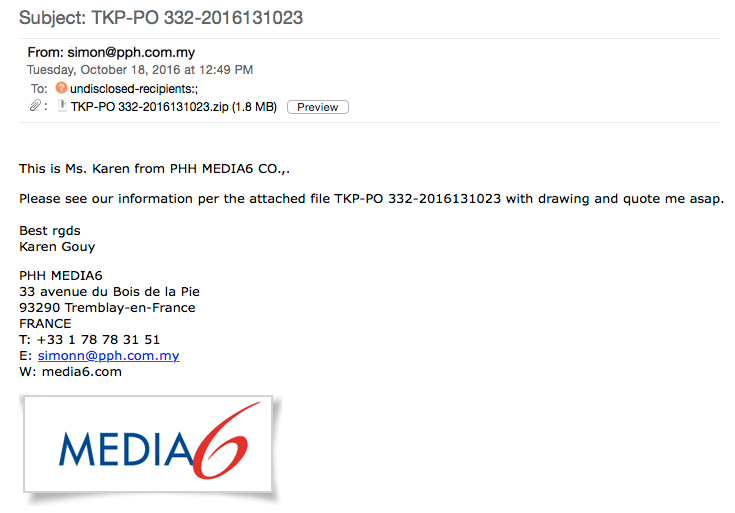
The malspam was a fake purchase order, spoofed to seem that it came from Media6, a company that specialized in Point of Sale (POS) marketing.
- Date/time: 2016-10-18 17:49 UTC
- From: [email protected]
- To: [email protected]
- Subject: TKP-PO 332-2016131023
- Attachment (zip archive): TKP-PO 332-2016131023.zip
- Malware from the zip archive: TKP-PO 332-2016131023.exe
Examining the email headers, we find the email came from a mail server at ps1.700tb.com on 119.18.103.60. The sending email address may or may not be spoofed. Since the mail server domain is registered to a person from Malaysia, the sending address of [email protected] might possibly be a real, but compromised, email account.
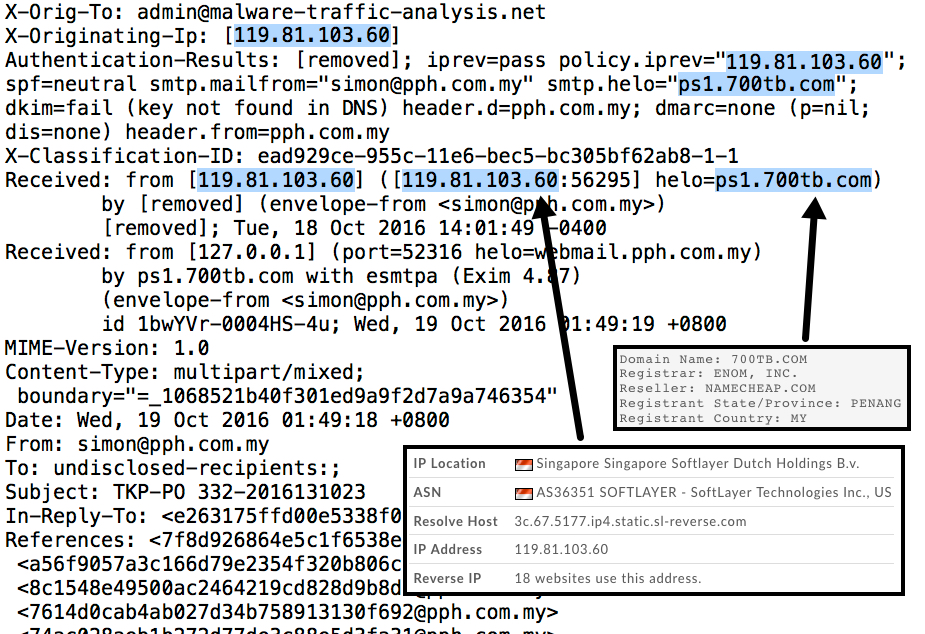
Shown above: Email headers for the malspam.
The malware
As far as malspam goes, the attachment isn't anything tricky. It's just an executable file in a zip archive. These types of emails can easily be blocked by most corporate email filtering. And why would you have an icon for the Chrome web browser for a file that's supposed to be a purchase order? That just doesn't make sense to me.
- File name: TKP-PO 332-2016131023.exe
- SHA256 hash: 69c32f18a33f922e253d39025e773211223c9af832314103410ca9eccf1a90f2
- VirusTotal link - Malwr.com link - Payload Security link
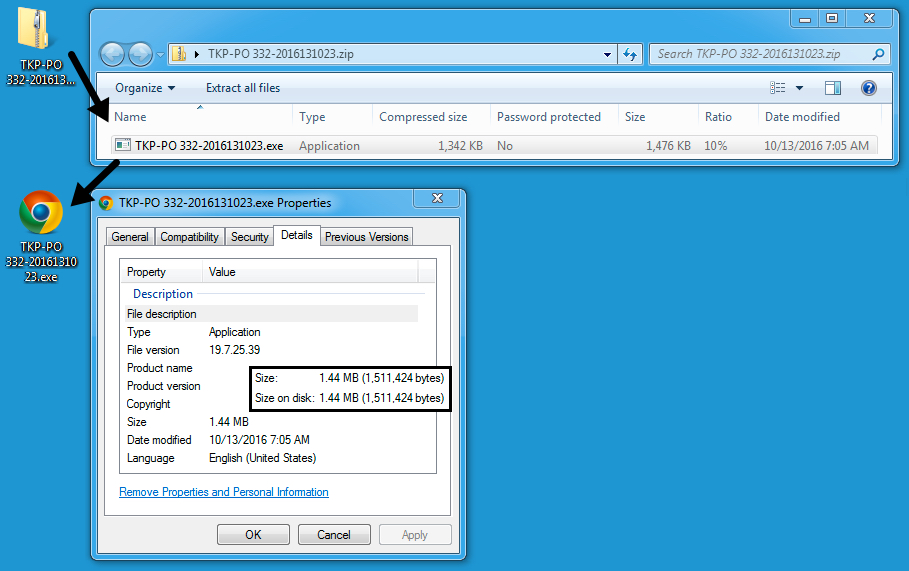
Shown above: The attached zip archive and extracted malware.
The traffic
Running the malware on a host in my lab environment gave me post-infection activity on 137.74.157.90 as encoded or encrypted traffic over TCP port 33338.
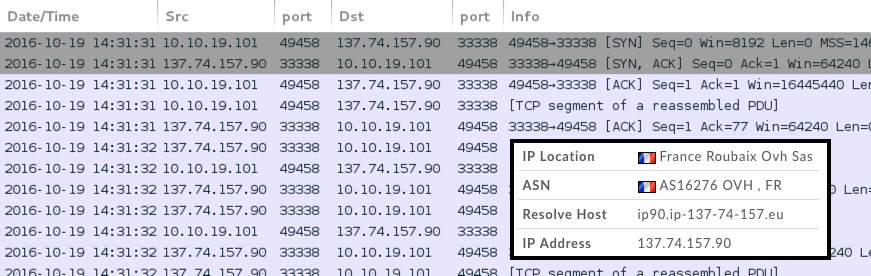
Shown above: Callback traffic from an infected host shown in Wireshark.
I checked the traffic against Snort 2.9.8.3 using the Snort subscription ruleset, and I also checked it on Security Onion running Suricata with the ET PRO ruleset. The Snort ruleset showed alerts for NanoBot activity (a botnet with hosts controlled by the NanoCore RAT). The ET PRO ruleset called it NanoCore RAT activity.
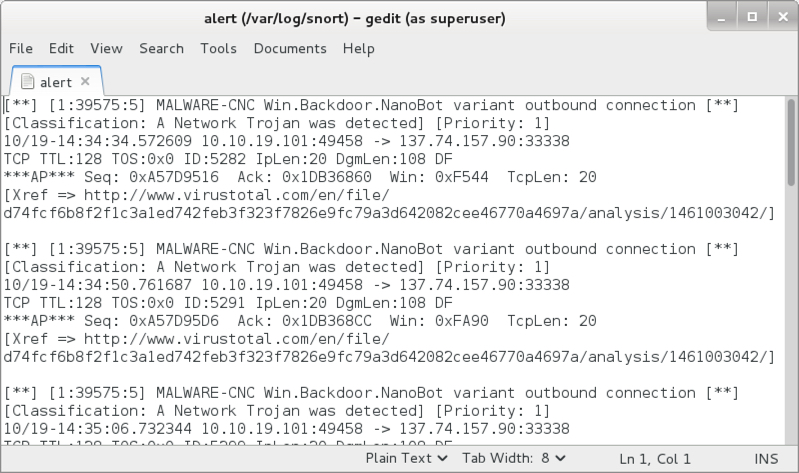
Shown above: Alerts from the Snort ruleset.
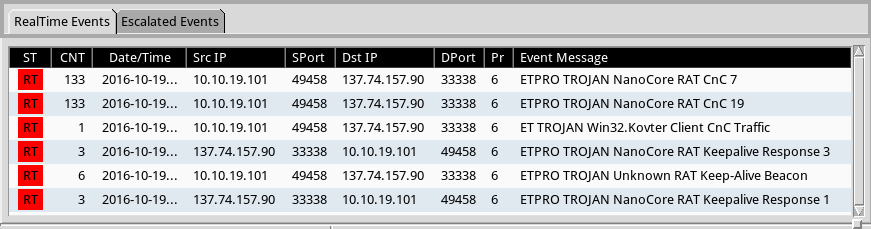
Shown above: Alerts from the ET and ET PRO rulesets.
Final words
The NanoCore RAT is a tool that has been used in targeted phishing attacks, but I've noticed it in daily waves of what appear to be malspam. In fact, my publicly-known blog email address got hit with an example. That leads me to believe most of the threat from NanoCore RAT is through mass distribution.
With proper filtering, these emails are easily blocked. With proper network monitoring, traffic from an infection is easily detected. I figure these waves of NanoCore RAT-based malspam are geared towards home users and anyone else without sufficient security controls.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
[1] https://nanocore.io/purchase/
[2] https://www.digitrustgroup.com/nanocore-not-your-average-rat/
[3] https://www.symantec.com/connect/blogs/nanocore-another-rat-tries-make-it-out-gutter
[4] http://blogs.cisco.com/security/talos/sysadmin-phish
[5] http://researchcenter.paloaltonetworks.com/2016/02/nanocorerat-behind-an-increase-in-tax-themed-phishing-e-mails/


Comments