Volatility rules...any questions?
As I sit in my hotel room in Washington DC at the SANSFIRE 2013 conference, preparing to present Memory Analysis with Volatility to a SANS@Night crowd (7:15 International Ballroom Center), an opportunity arose from which to get you warmed up for tonight's talk or inspire you to become a Volatility user (you should be already).
We received an advisory from a faithful reader indicating that he had uploaded "a dropper we got blitzed with from a spam campaign today" to ISC. We love us some malware samples, so I got busy. A typical review of the sample (invoice.exe) on a Windows VM gave us the basic behavioral details as seen in this ProcDOT visualization (ProcDOT also rules).
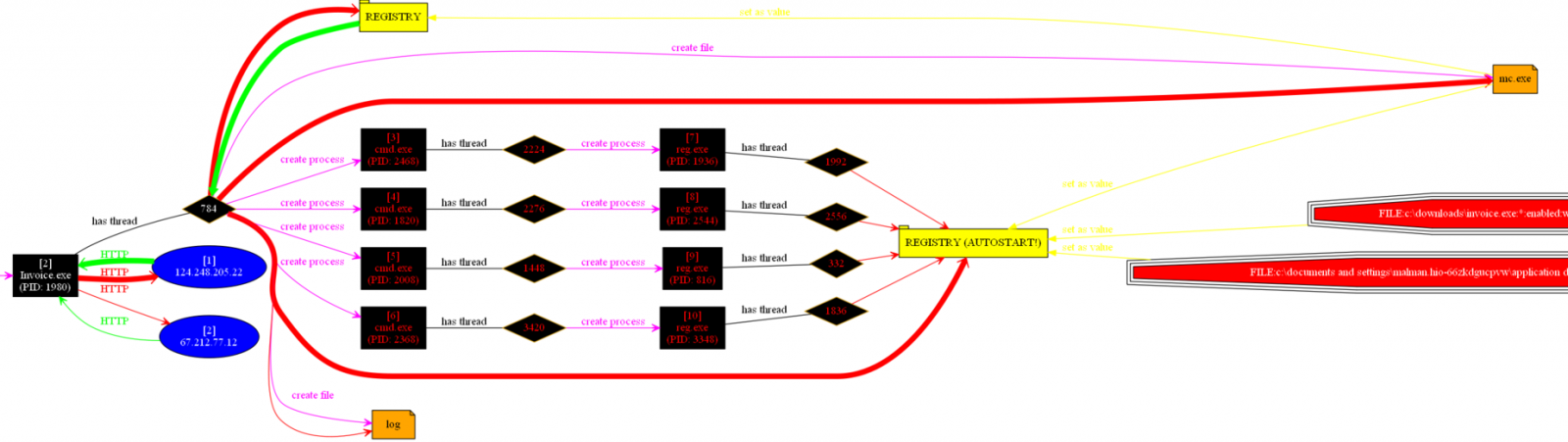
We can see that the invoice.exe process makes two Internet calls, spawns some shells to run reg.exe to create some registry entries, and creates a log file along with replicating itself to mc.exe in the victim user Application Data directory, before hiding itself from visible user APIs. Anubis provides better detail, but of concern was that fact that invoice.exe and mc.exe (same file, same hash) exhibited only one AV detection via Virustotal as this was written (certain to change soon). As such, we don't have much to go from as to what malware family we're really dealing with here.
But wait...Volatility to the rescue. I grapped a memory image from the compromised VM, copied the memory dump to my faithful SIFT 2.14 VM, and issued three simple commands that gave me all I needed to know.
- vol.py --profile=WinXPSP3x86 connscan -f invoice.raw
- vol.py --profile=WinXPSP3x86 pslist -f invoice.raw
- vol.py --profile=WinXPSP3x86 malfind -p 268 -D ~/Desktop/output/ -f invoice.raw
Here's the play by play.
- Step 1 indicated that Process ID (PID) 268 was responsible for an connection to 124.248.205.22 over port 80 in Hong Kong (oh boy, we know this doesn't end well).
- Step 2 indicated that PID 268 belonged to invoice.exe (our intial sample, we're on the right track).
- Step 3 dumped PID 268 to the SIFT desktop as process.0x86372a38.0x400000.dmp
I upload said .dmp file to Virustotal and voila, now we know what we're dealing with. Our faithful reader is the proud owner of a W32.Shadesrat (Blackshades) variant. This is one malware family where they apparently caught the bad guy last year (not before he sold his warez to many a miscreant as is evident here).
Wise man say "What I hear I forget, what I see I remember, what I do with Volatility I understand."
Hope to see you tonight at SANSFIRE 2013 for some Volatility 101 across the full lifecycle of security analytics (penetration testing, monitoring, incident response).
EMET 4.0 is now available for download
Somewhere I know TJ O'Connor is a very happy analyst. EMET 4.0 has been released in its final version and is now available for download.
Download here: http://www.microsoft.com/en-us/download/details.aspx?id=39273
Microsoft blogpost: http://blogs.technet.com/b/srd/archive/2013/06/17/emet-4-0-now-available-for-download.aspx
TJ O'Connor's Nuclear Scientists, Pandas, and EMET Keeping Me Honest, an ISC guest diary posting: https://isc.sans.edu/diary/Nuclear+Scientists%2C+Pandas+and+EMET+Keeping+Me+Honest/15890
For those of you who are new to EMET:
"The Enhanced Mitigation Experience Toolkit (EMET) is designed to help prevent hackers from gaining access to your system. Software vulnerabilities and exploits have become an everyday part of life. Virtually every product has to deal with them and consequently, users are faced with a stream of security updates. For users who get attacked before the latest updates have been applied or who get attacked before an update is even available, the results can be devastating: malware, loss of PII, etc."
EMET 4.0 features and updates incude:


Comments