Cyber Security Awareness Month - Day 29 - Clear Desk: The Unacquainted Standard
A Clear Standard
A "Clear Desk Policy" is becoming a more commonly adopted STANDARD in the work place. The idea that a clean desk is a standard may seem a bit of stretch. However, it is recognized in the access control domain by ISO [1], NIST [2], and ISC2 [3]. The standard name varies a bit and often includes the "Clear Screen" title and requirements too. A Clear Desk standard is not primarily targeting the actual cleanliness of the desk, but the often seen clutter of classified information left unattended out in the open.
I have worked in environments as an infosec professional, with a Clear Desk policy in effect and without. The comparison of each environment is drastic. An ENFORCED Clear Desk Standard ultimately reduces risk and nicely faciliates efficiency and effectiveness in the work place. An unenforced standard is equivalent to no standard and creates an endless list of items for any ambitious auditor.
A highly effective execution of a defined Clear Desk Standard/Policy should include two main components.
- Awareness
- Audit
Awareness
Awareness is key. This can be very simple. Make sure your employee KNOWS the policy/standard EXISTS and that it is ENFORCED. The awareness does not need to include an expensive training module. It can be delivered with mailbox flyers, emails, or simple cascaded conversations by management. Please check out the resource link that SANS provides. [4]
Audit
Once the awareness piece is in place, regularly auditing the work place is very critical. This too, does NOT need to be expensive. It can consist of delegating a champion to schedule/execute a review of the workplace, a spreadsheet for tracking, and a pad of review slips to leave on each desk detailing the review.
Here's a simple review slip example that can be used.
Keep it simple. I created this example in MS Word in ten minutes.
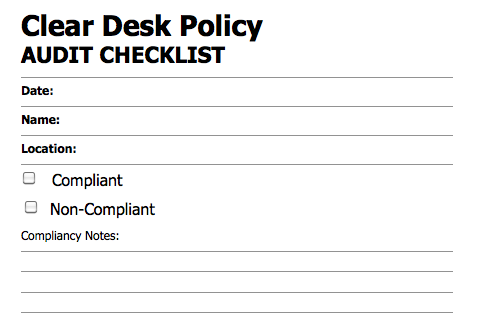
When the audit slip is left, it keeps the employee/user aware that checks are in place and the policy is enforced. This need only have to happen quarterly to be extremely effective. The spreadsheet can be used to track results and assist in accomplishing the compliancy goals of the policy. Publishing the quarterly numbers is also very effective.
Conclusion
The responsibility lies on the user to comply to any standard/policy. The responsibility lies on Management to enforce standard/policy. A lack of policy or policy enforcement can increase risk, loss of reputation and loss of data. Here is a snapshot of an assessment from a corporate envrionment where no policy existed.
.png)
These monitor notes are a simple example of the endless problems identified within an environment with little policy and enforcement. A simple expectation of a clean desk can provide an unmeasurable amount of decreased risk and positive image. The risk is tangible and the positive image is intangible. Both of which translate into increased efficiency and effectiveness by the staff and ultimately every line of business.
[1] http://csrc.nist.gov/publications/nistpubs/800-53-Rev3/sp800-53-rev3-final.pdf
[2] * Page H9 of link listed on reference [1].
TABLE H-2: MAPPING ISO/IEC 27001 (ANNEX A) TO NIST SP 800-53
[3] https://www.isc2.org/cissp-domains/default.aspx
[4] http://www.sans.org/security-resources/policies/desk-top.php
-Kevin
--
ISC Handler on Duty


Comments