ISC Feature of the Week: About the Internet Storm Center
Overview
Ever wondered when, how or why the Internet Storm Center started? Want to know what we do, why we do it and how you can help! We'll summarize the information from https://isc.sans.edu/about.html in this feature and you can click through to read the specific sections in full.
Features
About the Internet Storm Center - https://isc.sans.edu/about.html#about
Links to participate in the DShield program https://isc.sans.edu/participate.html and a link to details on the INFOCON threat alert https://isc.sans.edu/infocon.html.
ISC History and Overview - https://isc.sans.edu/about.html#history
Learn about what event prompted the formation of the ISC, how it went down and why.
Behind the Internet Storm Center - https://isc.sans.edu/about.html#behind
Tells about the people that make up ISC and the sensors that make DShield. The who, what and how of the Internet Storm Center and DShield sensor.
Early Warning - https://isc.sans.edu/about.html#early
How the ISC Handlers determine the significance of an event and if/how a warning is disseminated
Participating with the Internet Storm Center - https://isc.sans.edu/about.html#participate
We strongly encourange anyone who is able to contribute logs for analysis, including running a DShield sensor of your own that submits automatically. This section goes into detail of the how and benefits of submitting logs as a registered user. You can get started by visiting https://isc.sans.edu/howto.html.
The work is supported by the SANS Institute from tuition paid by students attending SANS security education programs. You can view all the SANS Site Network websites at https://isc.sans.edu/help/site_network or hold your mouse over the up/down arrows to the right of the ISC logo.
Post suggestions or comments in the section below or send us any questions or comments in the contact form on https://isc.sans.edu/contact.html#contact-form
--
Adam Swanger, Web Developer (GWEB, GWAPT)
Internet Storm Center https://isc.sans.edu
Massive spike in BGP traffic - Possible BGP poisoning?
Reader Yin wrote in after noticing a huge spike in unsolicited border gateway protocol (BGP) traffic. This same spike in BGP connections has also been noted on DShield's sensors [1]. Thankfully he provided a packet capture which contained numerous BGP OPEN [2] messages.
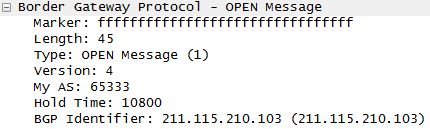
Here is a snippet of the BGP packet with the relevant details:
These messages all originated from the same system, based in Korea.
The Korean system IP is part of:
AS Number : AS9848
AS Name : SEJONGTELECOM-AS
From my understanding of BGP, this system is attempting to pass itself off as AS 65333, a private ASN [3] and poison the router with false details.
Whether misconfiguration or a malicious act is unknown at this point. Most, if not all routers should have basic protections in place to protect against this type of event having an effect [4].
Please let us know if you're seeing the same thing, can added anything further or if my analysis needs correcting.
UPDATE: Thank you to Reader Job for the clarification on private ASNs
[1] https://isc.sans.edu/port.html?port=179
[2] http://www.inetdaemon.com/tutorials/internet/ip/routing/bgp/operation/messages/open.shtml
[3] http://www.apnic.net/services/services-apnic-provides/helpdesk/faqs/asn-faqs#UsePrivateASN
[4] http://www.inetdaemon.com/tutorials/internet/ip/routing/bgp/security/index.shtml
Chris Mohan --- Internet Storm Center Handler on Duty


Comments