The Sad Reality of Spam/Phishing Attempts
Just for grins, I opened my spam folder on a gmail account I have and thought I'd take a look at what was in there since I hadn't looked lately. By the way, my spam folder is one of my first sources of new malware for those who ask quite regularly where they can find malware to analyze. In the last 30 days, I have approximately 707 spam emails, which averages to about 24 pieces of spam a day. I can find topics such as:
"Please i need your assistance"
and
"YOUR EMAIL HAS WON $500,000.00 USD"
to the more malware malicious ones (complete with attachments) such as:
"Kindly open the attachment"
or
"You have 1 unread Message!"
and those that ask me for my data like:
"Fill & Return For Claims"
or
"Fraud Alert!!!"
This doesn't even include the ones where I can buy drugs, save my visa card from being canceled, update my password before it expires, open a greeting card from someone I don't know, etc. I even found one in there from a friend's email address so they are either compromised or their email address is being used (yes, I'll tell them and ask them to check their system).
One would think from looking at the scam names used above; the misspellings and bad grammar in most of the emails ; the amount of publicity on the topic of spam/phishing attempts, etc. that they would not work. However, the sad reality is that spam/phishing is so rampant because it does work. We are seeing again first hand the efforts to capitalize on the Tsunami disaster that Bojan wrote about in the diary entry isc.sans.edu/diary/Tsunami+in+Japan+and+self+modifying+RogueAV+code/10543. Antivirus vendors are reporting that on average that spam makes up over 80% of email traffic. That is a significant amount of email that is spam (no wonder my spam folder is so full) and just by shear numbers, it is going to work. Many organizations at work have email gateways to filter out the miscreants, but at the same time, many do not block web based email accounts which defeats the whole purpose of having an email gateway.
According to what I have been able to research (I didn't even have a computer then to know anything about it), the first spam email was sent on May 1st, 1978. It was sent by a DEC marketing representative to every ARPANET address. Spam in one form or another has been increasing every since then and really picking up steam in the 90s. One would think that with the passage of that much time, that we would have been able to educate people how not to fall prey to such events.
I still think education of the user is key and sadly SPAM/Phishing attempts have become part of the "normal" noise on the internet. As sad as this is there is one bright note, at least with my daily dose of spam, I'll be able to have all the fresh malware I can analyze.
Adobe Flash 0-day being used in targeted attacks
Adobe posted a security advisory (http://www.adobe.com/support/security/advisories/apsa11-01.html) about a new 0-day vulnerability in Flash player. According to the post about this vulnerability (available at http://blogs.adobe.com/asset/2011/03/background-on-apsa11-01-patch-schedule.html), Adobe says that they had reports of this new vulnerability being used in targeted attacks. These attacks seem to be particularly sneaky – the Flash exploit is embedded in an Excel file which is also used to setup memory so the exploit has a higher chance of succeeding.
We will keep an eye on this and if the 0-day starts being used in the wild. If you have more information that you can share about this let us know.
--
Bojan
INFIGO IS
Tsunami in Japan and self modifying RogueAV code
A lot of people are still surprised how quickly bad guys catch up with events in the real world - this is especially true for the RogueAV/FakeAV groups which constantly poison search engines in order to lure people into installing their malware.
We can also see even many AV vendors warning people to be careful when they search for this or that (currently, obviously the search query that generates most attention is related to the disaster in Japan). While it is good to constantly raise awareness and warn people about what’s happening, one important thing to know is that the RogueAV/FakeAV guys poison search engines and modify their scripts automatically. This means that they are constantly on top of current trends and events in the world – whatever happens, their scripts will make sure that they “contain” the latest data/information about it.
Back last year I wrote two diaries explaining how a certain RogueAV/FakeAV group works; if you haven’t seen them before I’d strongly recommend that you take a look, they are available at:
http://isc.sans.edu/diary.html?storyid=9085
http://isc.sans.edu/diary.html?storyid=9103
There are many RogueAV/FakeAV groups so the analysis posted above just concerns one of them (it’s interesting to see that they are still very much active).
With the disaster in Japan striking on Friday we saw another RogueAV/FakeAV group heavily poisoning the search engines – even Google which normally removes them quickly still contains hundreds of thousands of such pages. Since this campaign can be easily identified, here is what the current count says:
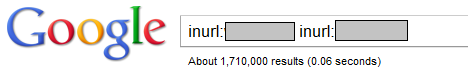
Yes, 1.7 million pages (!!!). Keep in mind that there are multiple pages listed here with different search terms (they modify search terms through a single parameter), but the number is still staggering. According to Google, in past 24 hours there have been 14,200 such pages added so it’s clear that the bad guys are very active.
This RogueAV/FakeAV group uses different code than the one I previously analyzed. They actually drop pretty interesting, self modifying PHP code.
The code contains a list of current searches/trends. The list contains hundreds of such keywords, some of which are shown below:
$lastquery = "<keys>cee-lo-green-grammyswhat-chilli-wants-finale … japan-tsunami-newsokinawa-japan-tsunami-2011tsunami-and-earthquake-in-japan</keys>";
Notice how the list is delimited by <keys> tags. This allows the owner of the script to automatically update the keywords the script will react to – by using a special parameter to identify himself, the owner can submit a new keyword and the script will modify itself by adding this parameter if it hasn’t been found in the $lastquest list before:
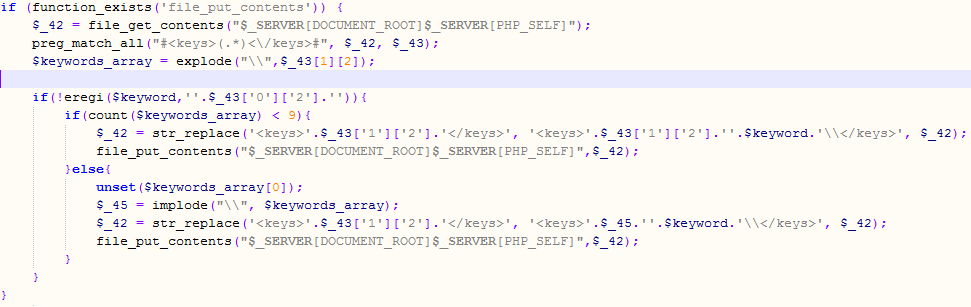
Same function is used if Google’s or another search engine’s bot visit’s the web page – the main script check’s the user agent that was submitted and even has a list of networks that can help the script owner identify “visitors” he or she does not want to get redirected to the final site hosting RogueAV.
But this is not all. When visited by a search engine’s bot, the script (among the other things) tries to create a very legitimate looking web page that should help poison the search engine. In order to create this legitimate looking web page, the script automatically queries Google to see related searches for the current search query (the hottrends web page at Google). Besides Google it will also use Yahoo to search for new pages and, what’s probably the most interesting, will retrieve images from Google images that are related to the same query term!
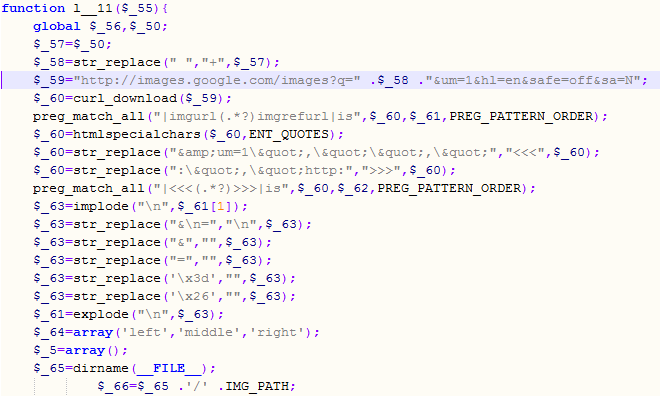
This way the RogueAV/FakeAV guys can create very realistic pages that can, unfortunately as we’ve all witnessed, successfully poison search engines.
(to be continued)
--
Bojan
INFIGO IS


Comments