YARA-X 1.14.0 Release
YARA-X's 1.14.0 release brings 4 improvements and 2 bugfixes.
One of the improvements is a new CLI command: deps.
This command shows you the dependencies of rules.
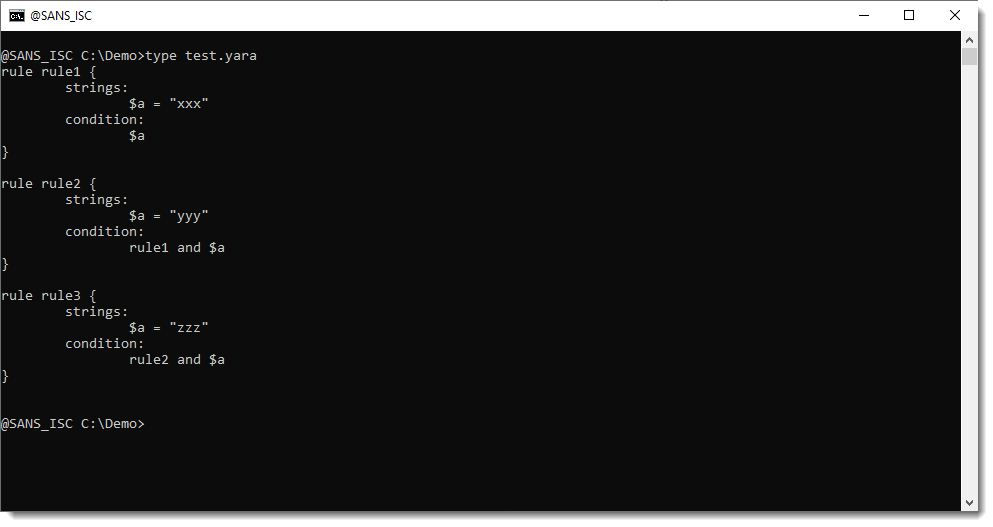
Here is an example. Rule rule1 has no dependencies, rule rule2 depends on rule rule1 and rule rule3 depends on rule rule2:
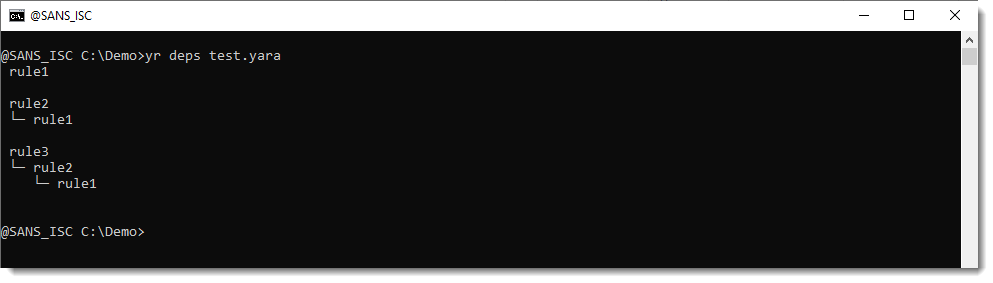
Running the deps command on these rules gives you the dependencies:
Didier Stevens
Senior handler
blog.DidierStevens.com
Keywords:
0 comment(s)
×
![modal content]()
Diary Archives


Comments