Windows Autorun Part-2
In previous diary I talked about startup folders and shell folders registry keys. In this diary I will continue talking about how to check if you are suspecting something malware or a compromised system.
2-Run and RunOnce registry key:
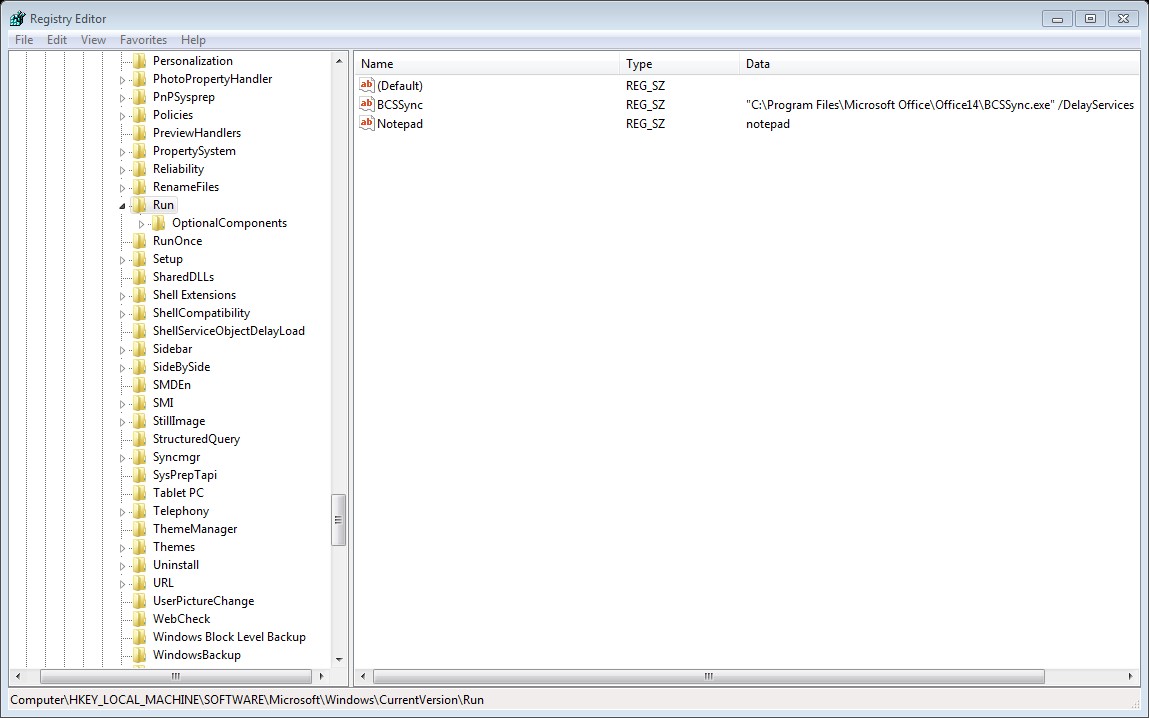
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run\
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce\
Any executable in the above registry keys will start during the system startup, the different between Run and RunOnce is that RunOnce will run the value for one time then it will be deleted ,while Run it will run every time that the system startup.
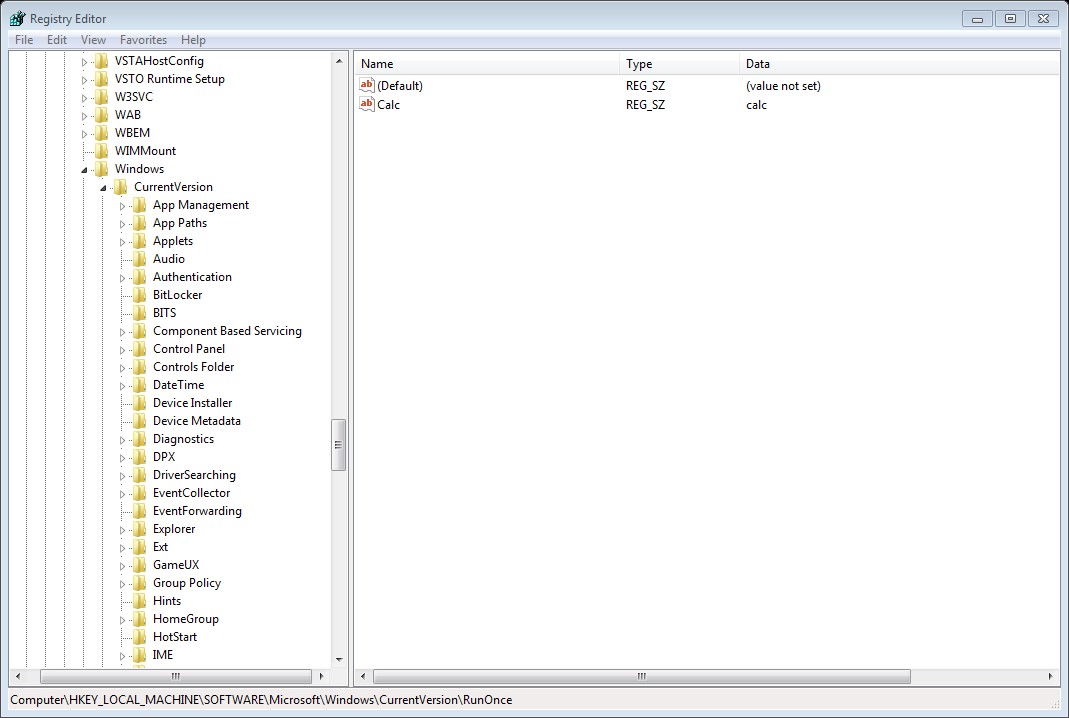
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce\
The above keys is related to specific user login, again the different between Run and RunOnce is RunOnce will run one time the the value will be deleted while run will be run every time that the specific user log on.
3- Services
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services
Here you can find the list of services that run at system startup, each service has a startup value as the following table:
|
Value |
Startup Type |
|
2 |
Automatic |
|
3 |
Manual |
|
4 |
Disabled |
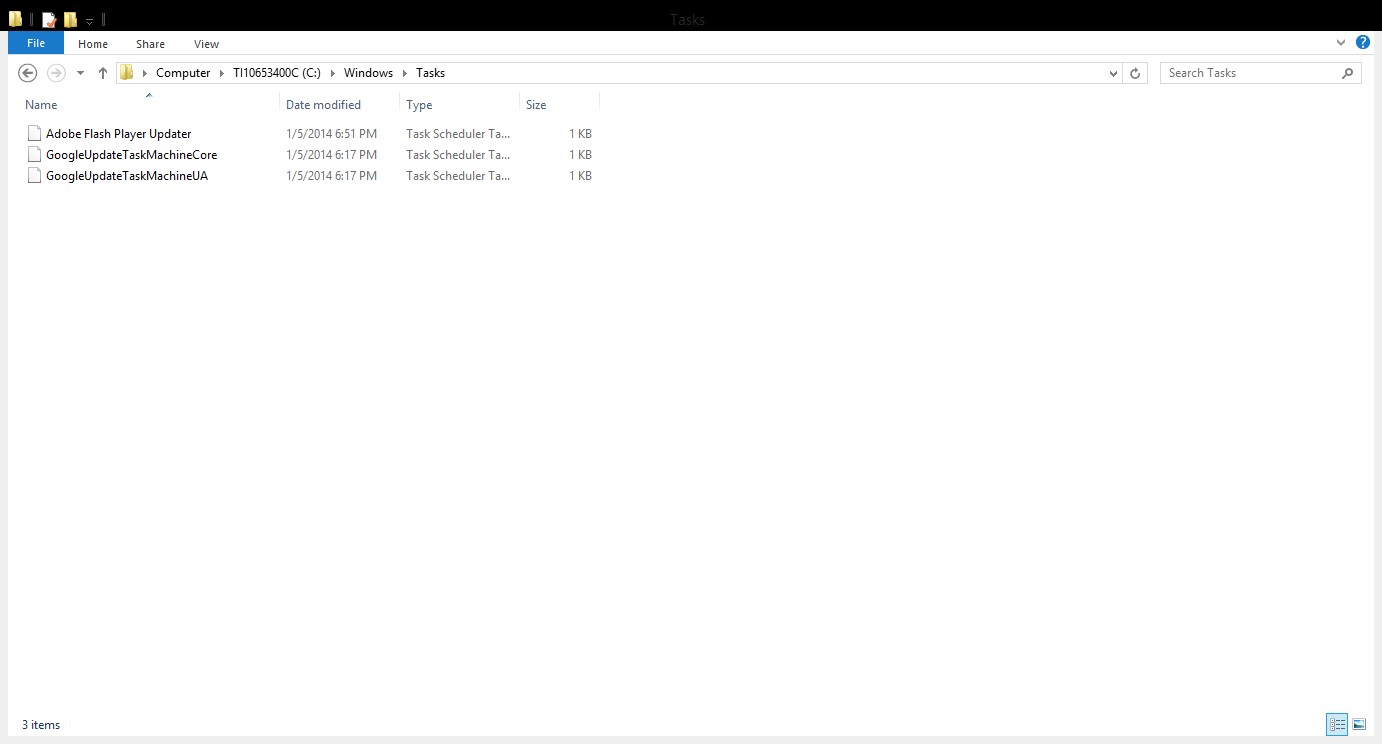
4-Schedule tasks:
Schedule task can be used to run a executable based on a schedule .The task are located in %windir%/tasks folder,of course attacker and malware will not use task name such as ‘I am malicious’ instead it will use some names that sound legitimate such ‘Windows Update’ .


Comments
Anonymous
Jan 5th 2014
1 decade ago
It's amazing how the writer makes the subject matter much more complicated than it should be.
This is an article for 1999....maybe.
Anonymous
Jan 5th 2014
1 decade ago
Anonymous
Jan 5th 2014
1 decade ago
Anonymous
Jan 5th 2014
1 decade ago
It makes sense. Autoruns is a great tool. There will be situations where you can't use the great tool; for example, understanding some things to look for in the potential analysis of an executible. You may fare better, if you know the auto start entry points.
That said.... there are a bunch of things Autoruns checks, that the author has not mentioned so far -- such as file signatures (Is the program executable being started... what you think it is, or has it been tampered with?). Autoruns also checks Shell Extensions and browser extensions that can be used to "auto start" a task, also; and Win Login notifications, Sidebar gadgets as well, Network Providers, LSA Providers, Print Monitors, Winsock LSPs, Codecs, Boot Exec.
So Autostarts is more comprehensive than the guide so far, which is just a sampling... you'll need more research
For example:
HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run
HKLM\SOFTWARE\Wow6432Node\Microsoft\Active Setup\Installed Components HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify
HKLM\Software\Wow6432Node\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects
HKLM\Microsoft\Active Setup\Installed Components
HKLM\Software\Classes\*\ShellExt\ContextMenuHandlers
HKLM\Software\Wow6432Node\Classes\*\ShellExt\ContextMenuHandlers
HKLM\Software\Classes\Drive\ShellEx\ContextMenuHandlers
HKLM\Software\Wow6432Node\Classes\Drive\ShellEx\ContextMenuHandlers
HKLM\Software\Classes\AllFileSystemObjects\ShellEx\ContextMenuHandlers
HKLM\Software\Classes\Directory\ShellEx\ContextMenuHandlers
HKLM\Software\Wow6432Node\Classes\Directory\ShellEx\ContextMenuHandlers
HKLM\Software\Classes\Directory\ShellEx\DragDropHandlers
HKLM\Software\Wow6432Node\Classes\Directory\ShellEx\DragDropHandlers
HKLM\Software\Classes\Directory\ShellEx\CopyHookHandlers
HKLM\Software\Classes\Folder\ShellEx\ContextMenuHandlers
HKLM\Software\Wow6432Node\Classes\Folder\ShellEx\ContextMenuHandlers
HKLM\Software\Classes\Folder\ShellEx\DragDropHandlers
HKLM\Software\Wow6432Node\Classes\Folder\ShellEx\DragDropHandlers
Anonymous
Jan 6th 2014
1 decade ago
ISC has multiple diary entries that could have been referenced, the search box helps a lot. A suggestion could be to add a link to search into the Diary; https://isc.sans.edu/search.html?q=autorun
dotBATman.
PS: I just wanted to remind everyone that there are cases where entries hide from Windows Registry editor - SysInternals AutoRuns or scripts can help you find those..
https://isc.sans.edu/forums/diary/Nasty+Games+of+Hide+and+Seek+in+the+Registry+Nepenthes/636
http://gallery.technet.microsoft.com/scriptcenter/b8bc5534-f4d1-49c8-b40a-dc5031ac2305 will list all Run entries and alert of those "hiding" on purpose or by accident.
PPS: Microsoft may have fixed the issue of not showing long entries - but I am not aware of this change.
Anonymous
Jan 6th 2014
1 decade ago
John
Anonymous
Jan 6th 2014
1 decade ago
Anonymous
Jan 6th 2014
1 decade ago