Tsunami in Japan and self modifying RogueAV code
A lot of people are still surprised how quickly bad guys catch up with events in the real world - this is especially true for the RogueAV/FakeAV groups which constantly poison search engines in order to lure people into installing their malware.
We can also see even many AV vendors warning people to be careful when they search for this or that (currently, obviously the search query that generates most attention is related to the disaster in Japan). While it is good to constantly raise awareness and warn people about what’s happening, one important thing to know is that the RogueAV/FakeAV guys poison search engines and modify their scripts automatically. This means that they are constantly on top of current trends and events in the world – whatever happens, their scripts will make sure that they “contain” the latest data/information about it.
Back last year I wrote two diaries explaining how a certain RogueAV/FakeAV group works; if you haven’t seen them before I’d strongly recommend that you take a look, they are available at:
http://isc.sans.edu/diary.html?storyid=9085
http://isc.sans.edu/diary.html?storyid=9103
There are many RogueAV/FakeAV groups so the analysis posted above just concerns one of them (it’s interesting to see that they are still very much active).
With the disaster in Japan striking on Friday we saw another RogueAV/FakeAV group heavily poisoning the search engines – even Google which normally removes them quickly still contains hundreds of thousands of such pages. Since this campaign can be easily identified, here is what the current count says:
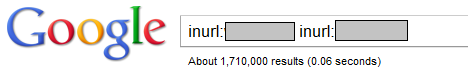
Yes, 1.7 million pages (!!!). Keep in mind that there are multiple pages listed here with different search terms (they modify search terms through a single parameter), but the number is still staggering. According to Google, in past 24 hours there have been 14,200 such pages added so it’s clear that the bad guys are very active.
This RogueAV/FakeAV group uses different code than the one I previously analyzed. They actually drop pretty interesting, self modifying PHP code.
The code contains a list of current searches/trends. The list contains hundreds of such keywords, some of which are shown below:
$lastquery = "<keys>cee-lo-green-grammyswhat-chilli-wants-finale … japan-tsunami-newsokinawa-japan-tsunami-2011tsunami-and-earthquake-in-japan</keys>";
Notice how the list is delimited by <keys> tags. This allows the owner of the script to automatically update the keywords the script will react to – by using a special parameter to identify himself, the owner can submit a new keyword and the script will modify itself by adding this parameter if it hasn’t been found in the $lastquest list before:
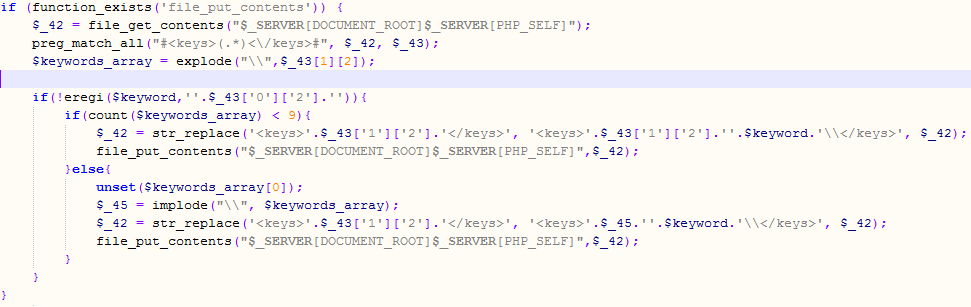
Same function is used if Google’s or another search engine’s bot visit’s the web page – the main script check’s the user agent that was submitted and even has a list of networks that can help the script owner identify “visitors” he or she does not want to get redirected to the final site hosting RogueAV.
But this is not all. When visited by a search engine’s bot, the script (among the other things) tries to create a very legitimate looking web page that should help poison the search engine. In order to create this legitimate looking web page, the script automatically queries Google to see related searches for the current search query (the hottrends web page at Google). Besides Google it will also use Yahoo to search for new pages and, what’s probably the most interesting, will retrieve images from Google images that are related to the same query term!
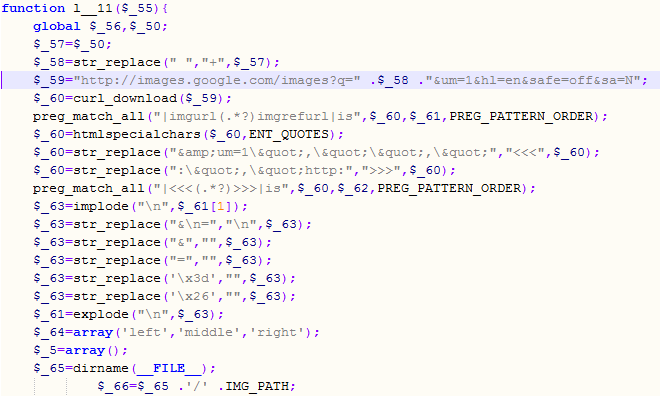
This way the RogueAV/FakeAV guys can create very realistic pages that can, unfortunately as we’ve all witnessed, successfully poison search engines.
(to be continued)
--
Bojan
INFIGO IS
| Web App Penetration Testing and Ethical Hacking | Amsterdam | May 18th - May 23rd 2026 |


Comments