SWOT matrix for describing security posture
"Be brief, for no discourse can please when too long." Miguel de Cervantes
"When I try to be brief, I become obscure." Quintus Horatius Flaccus
How can you outline a system's security state succinctly, yet without omitting important points? Consider using the SWOT matrix to summarize your perspective. This approach is particularly effective when communicating with managers and executives, who are usually familiar with SWOT analysis.
The acronym SWOT, which stands for Strengths, Weaknesses, Opportunities and Threats, is designed to remind you of the key factors to consider when analyzing a situation. A SWOT matrix is a table that presents these elements in a compact manner. Take a look the SWOT matrix template below. (It is based on an image from Wikipedia.)
The left column lists helpful, positive factors; the right one lists harmful, negative factors. The top row includes the factors intrinsic to the analyzed system; the bottom one includes factors external to the system.
Let's examine contents of each cell in the SWOT matrix: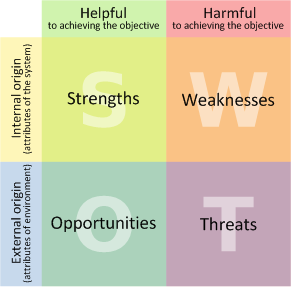
Strengths lists the most effective security aspects of the system, for example tight network access controls or comprehensive security policies. Improvements to the system's security can be accomplished by building upon these strengths.
Weaknesses outlines those aspects of the system that put it at risk, for instance poor input validation, or lack of effective log management. These aspects of the system should be improved.
Opportunities describes factors external to the system that can help improve its security. This might be the availability of security training funds for developers, or the existence of a logging system that has been purchased, but was never deployed. Items in this cell might be low-hanging-fruit--easy wins that can improve the system's security.
Threats highlights external factors that magnify the adverse effects of internal system weaknesses. For instance, the company may be subject to fine-imposing regulations, or may possess weak change management practices.
The SWOT matrix approach is particularly powerful when the company defines the objective with respect to which the system should be evaluated. In the context of information security, this usually involves agreeing on the system's risk profile, data sensitivity, business goals, and other factors that affect the system's security architecture.
If you like this approach, you are welcome to use the editable SWOT matrix template I created in Microsoft Word. You can download it from here.
Further information: For information about the classic use of SWOT analysis, take a look at the corresponding Wikipedia article. Security management topics such as SWOT analysis are explored in the SANS MGT-512 course. If you found this note useful, you may also enjoy my earlier tip on using an "elevator pitch" for explaining security risks to executives.
-- Lenny
Lenny Zeltser leads a regional security consulting team at Savvis and teaches a course on reverse-engineering malware at SANS.


Comments