SSH Scans by Clients Types
I'm always curious what is scanning my honeypot but I was particularly interested what kind of client applications are used to attempt to login via SSH into that service. This graph shows the activity for the past week, including 500+ attempts for a period of 8 hours on the 31 Dec which when pretty much flat from 31 Dec 1200Z to 1 Jan 2018 1200Z while everyone celebrated New Year.
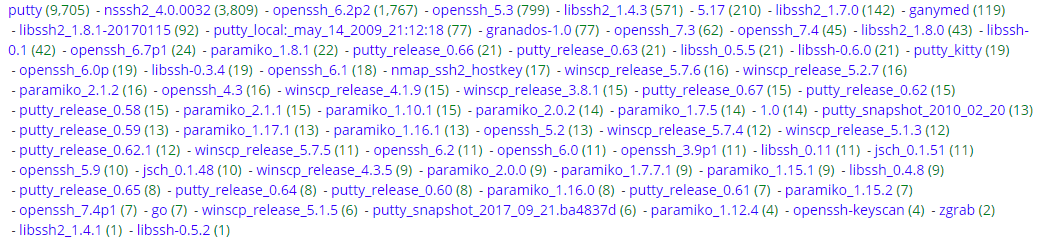
Over the past 1, I picked up 18,309 SSH attempt to login the SSH server (graph below) which resulted in detecting 76 different client applications (see graph). Some of those clients are quite common (various release of putty, winscp, etc) while other I have never heard of before (paramiko, jsch, putty_kitty, etc).
I reviewed the 417 list of username use to attempt to "login" for a total of 61,199 attempts over this past week. The most common username are in list such as root, admin, user, etc to various other funny names like superman, ragnarok, sickrage, etc.
[1] https://www.lag.net/paramiko/
[2] http://www.jcraft.com/jsch/examples/Shell.java.html
[3] https://www.fosshub.com/KiTTY.html
-----------
Guy Bruneau IPSS Inc.
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu





Comments
iptables -A BLOCKME -p tcp --dport ssh -m string --string "SSH-2.0-libssh" --algo bm -j SET --add-set filter-tempblock src
Other clients include "SSH-2.0-sshlib" "SSH-2.0-ZGrab" "SSH-2.0-Go" "SSH-2.0-ssh2js" "SSH-2.0-Ganymed" "SSH-2.0-JSCH" "SSH-2.0-Granados" "SSH-2.0-OpenSSH_6.7p1 Raspbian" "SSH-2.0-paramiko"
Anonymous
Jan 8th 2018
7 years ago