Remote Desktop Protocol (RDP) Discovery
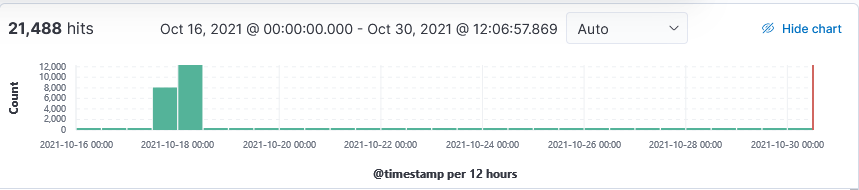
I have noticed a surge in probe against the RDP service in the past 2 weeks. In August, a remote code execution (RCE) critical patch was released to fix an exploit related to CVE-2021-34535 which include a POC to exploit this vulnerability. This vulnerability is also affecting Microsoft Hyper-V Manager “Enhanced Session Mode” [5] and Microsoft Defender’s Application Guard (WDAG) [6].
According to Shodan [7], there are over 4.89M IPs with TCP:3389 listening and over 3.9M IPs with RDP listening on other ports but mainly on 3388 [8]. Beside TCP:3389, my honeypot logged mstshash probe against other port such as 21, 23, 80, 8000, 8080.
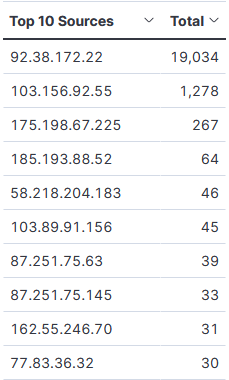
20211018-022140: 192.168.25.9:3389-92.38.172.22:5616 data
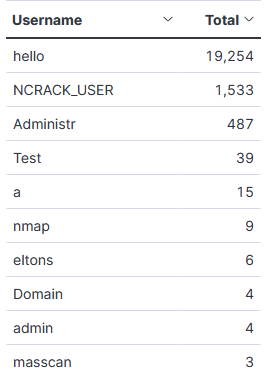
\x03\x00\x00+&\xe0\x00\x00\x00\x00\x00Cookie: mstshash=hello\r\n\x01\x00\x08\x00\x03\x00\x00\x00
[2021-10-30 08:42:54] [1558] [ftp_21_tcp 16145] [77.83.36.32:65158] recv: .../*......Cookie: mstshash=Administr
Top 10 Usernames
Top 10 Sources
If using RDP, Microsoft provided the following information on "Security guidance for remote desktop adoption".
[1] https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-31968
[2] https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-34535
[3] https://vuldb.com/?id.180474
[4] https://nvd.nist.gov/vuln/detail/CVE-2021-34535
[5] https://docs.microsoft.com/en-us/virtualization/hyper-v-on-windows/user-guide/enhanced-session-mode
[6] https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-application-guard/md-app-guard-overview
[7] https://www.shodan.io/search?query=port:3389
[8] https://www.shodan.io/search?query=Remote+Desktop+Protocol
[9] https://www.microsoft.com/security/blog/2020/04/16/security-guidance-remote-desktop-adoption/
[10] https://isc.sans.edu/forums/diary/Random+Port+Scan+for+Open+RDP+Backdoor/24422/
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu


Comments
Anonymous
Nov 5th 2021
4 years ago