Qakbot activity resumes after holiday break
Introduction
Although the botnet infrastructure behind Qakbot was active as we entered this year, we hadn't seen any active campaigns spreading Qakbot. Qakbot had been quiet since a few days before Christmas. We saw no new malicious spam (malspam), and we saw no new Excel spreadsheets that we typically find during active campaigns.
It had been relatively quiet for Qakbot until Tuesday 2021-01-19, when we started seeing malicious spam (malspam) pushing Qakbot again. @BushidoToken tweeted about it here.
Today's diary examines a Qakbot infection from Tuesday 2021-01-19.
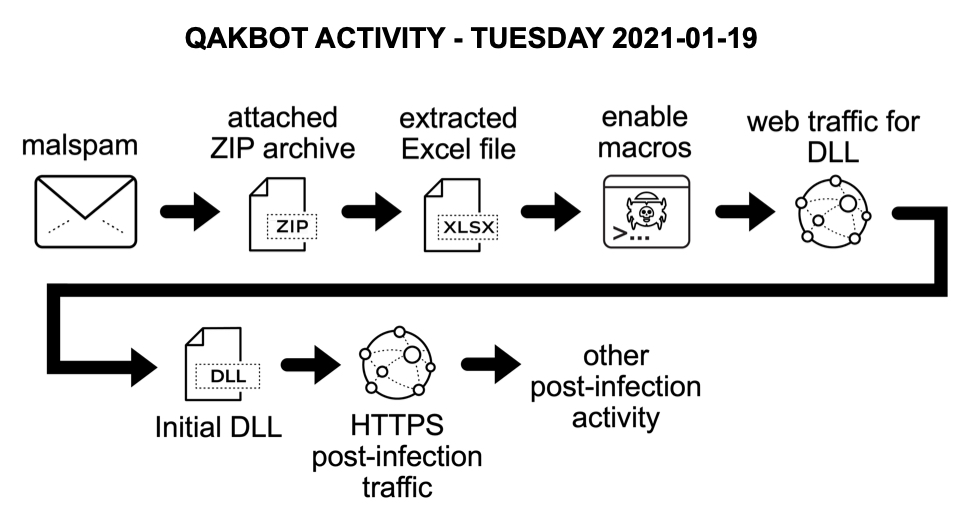
Shown above: Flow chart for recent Qakbot activity.
The malspam
No changes here. Qakbot malspam typically spoofs stolen email chains from previously-infected Windows hosts, and it feeds the data to currently-infected Windows hosts that send new malspam pushing updated files for Qakbot. See the image below for an example from Tuesday 2021-01-19.
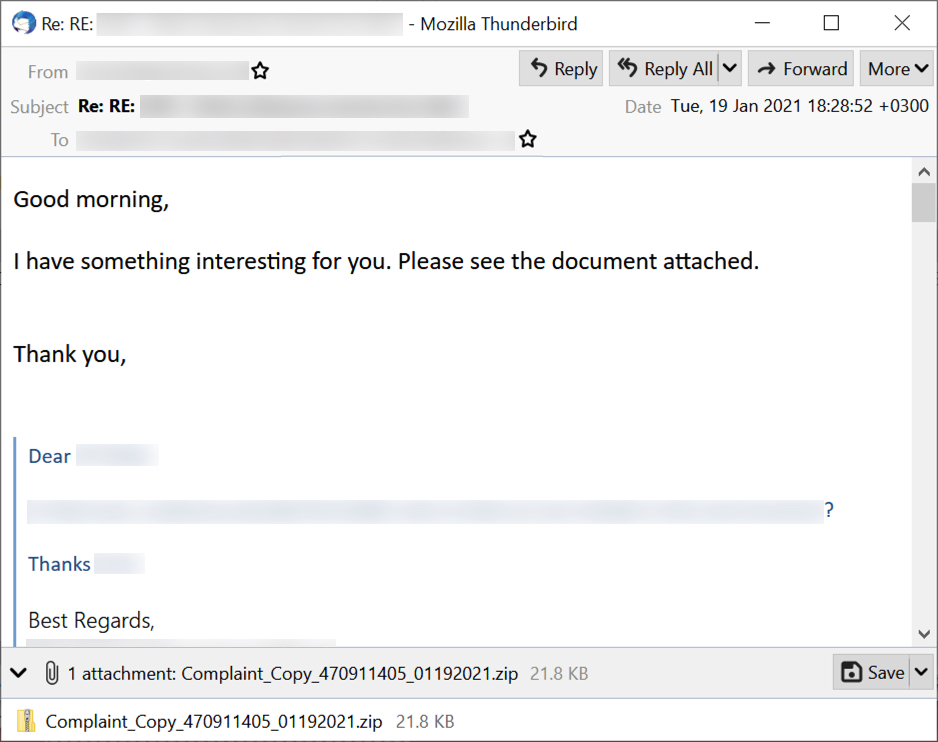
Shown above: An example of Qakbot malspam from Tuesday 2021-01-19.
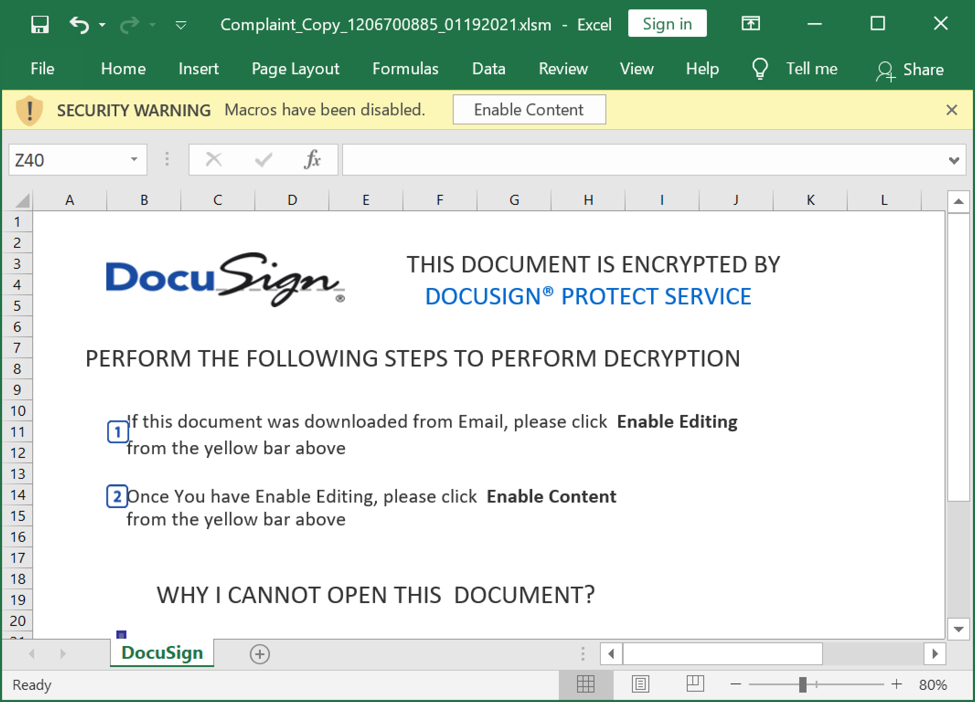
Shown above: Screenshot from one of the spreadsheets I used to infected a Windows host with Qakbot.
Infection traffic
See the images below for my analysis of network traffic from the Qakbot infection.
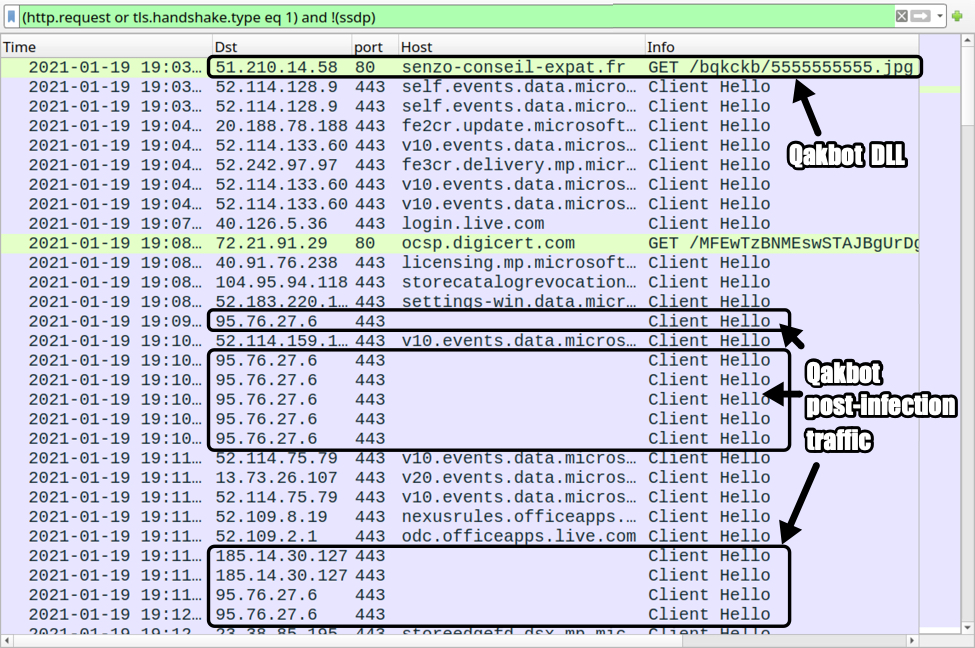
Shown above: Traffic from the Qakbot infection filtered in Wireshark.
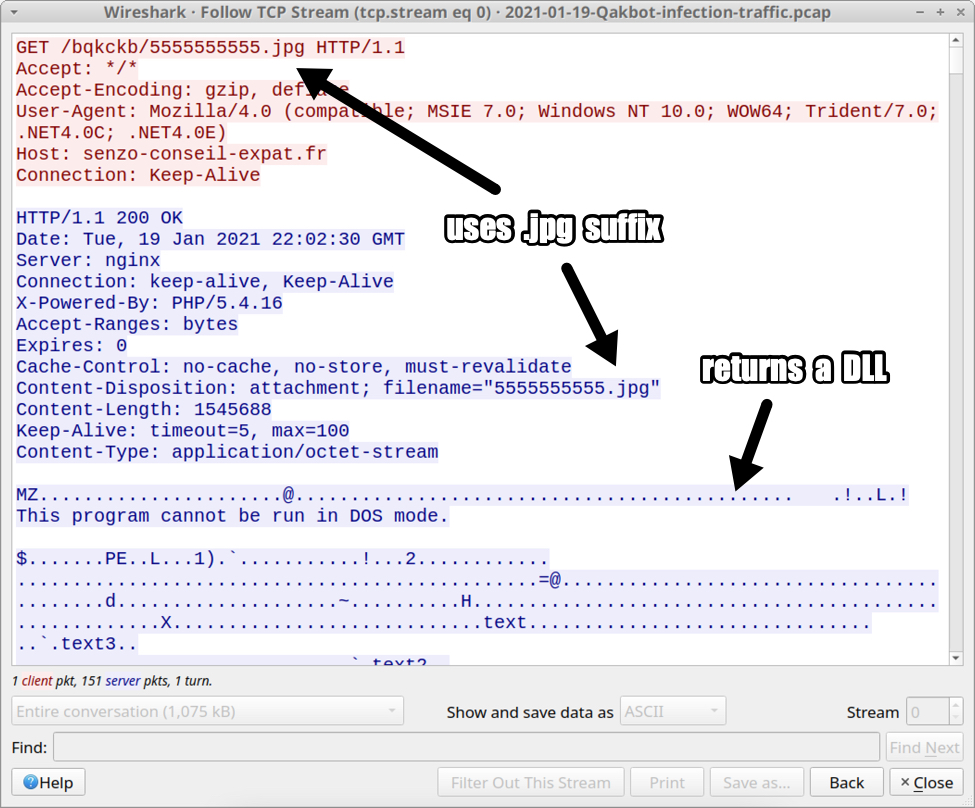
Shown above: Excel macro retrieving the initial DLL file for Qakbot.
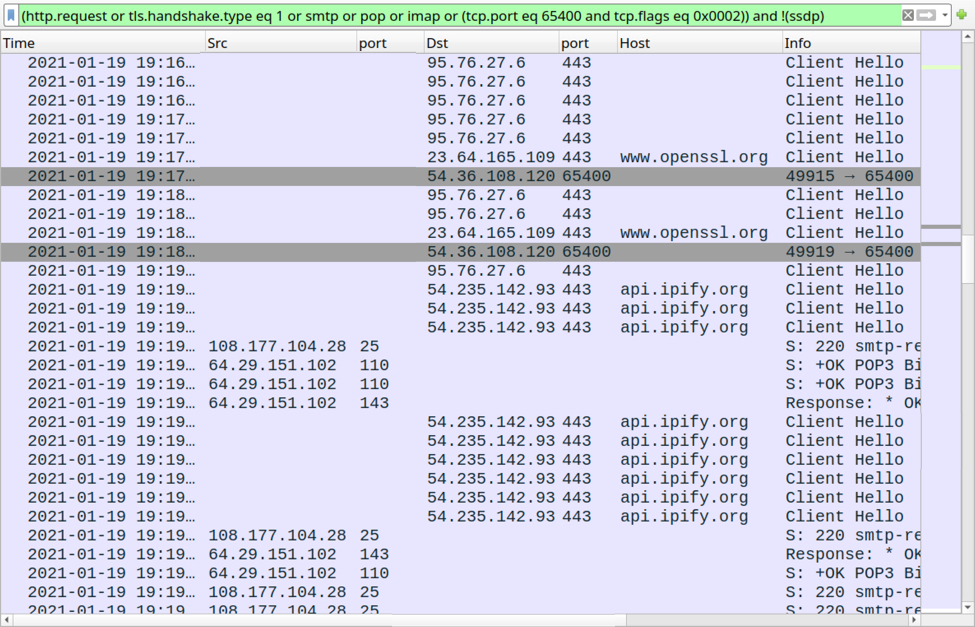
Shown above: More post-infection activity from the Qakbot-infected Windows host.
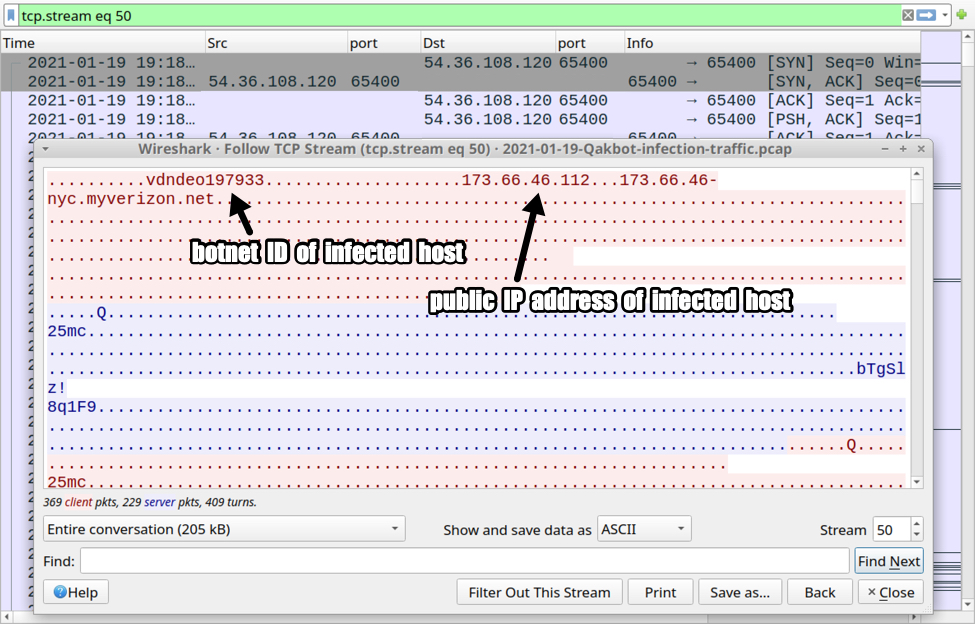
Shown above: Traffic over TCP port 65400 caused by Trickbot.
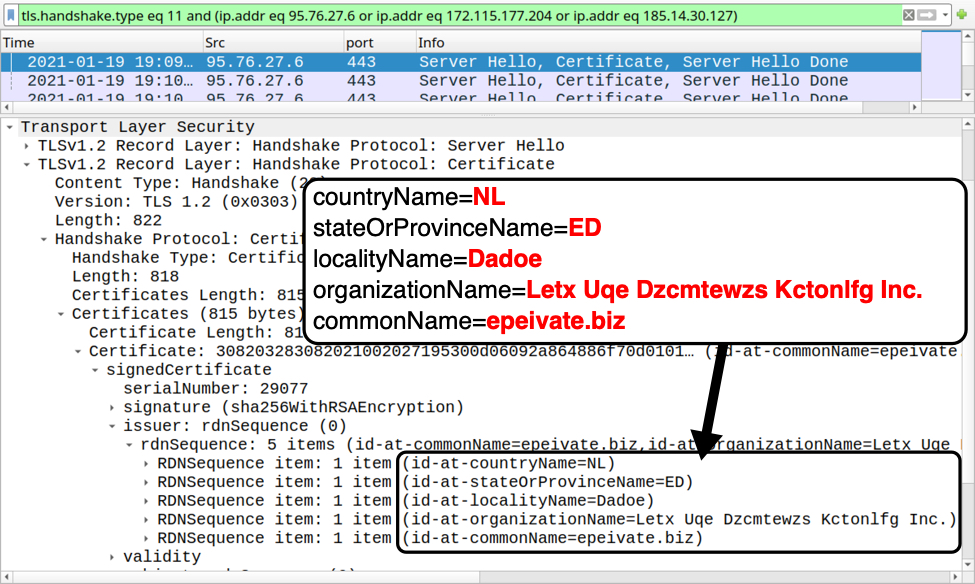
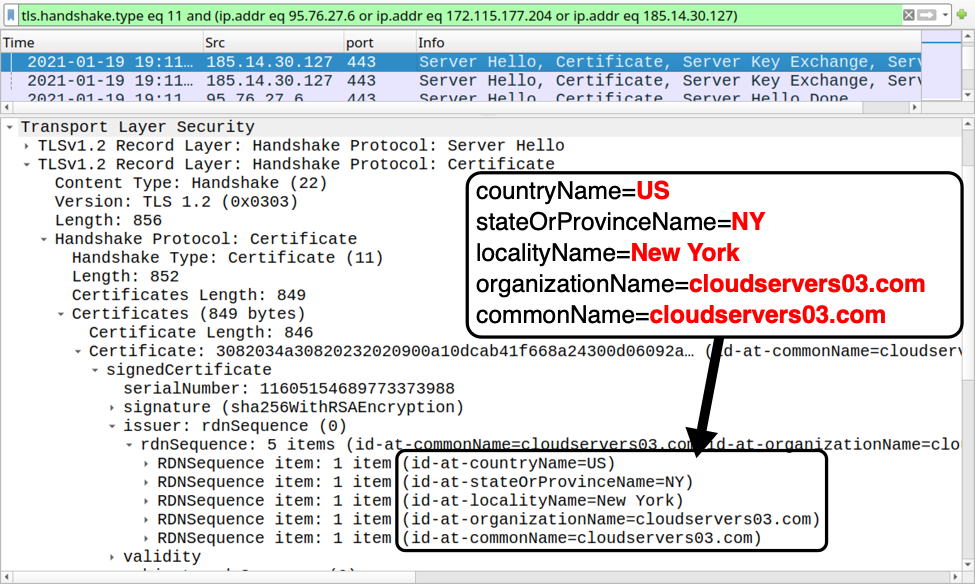
Shown above: Certificate issuer data for HTTPS traffic caused by Qakbot (example 1 of 3).
Shown above: Certificate issuer data for HTTPS traffic caused by Qakbot (example 2 of 3).
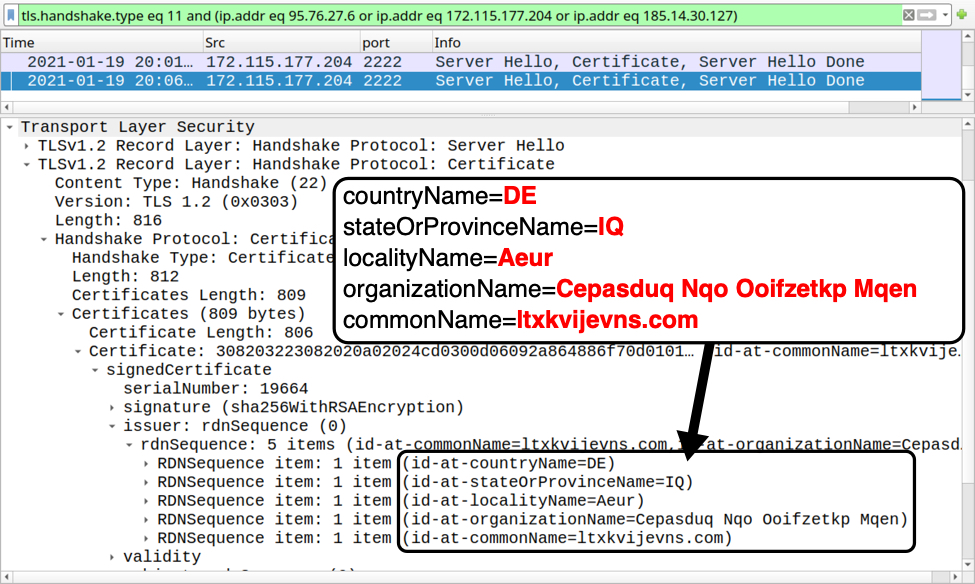
Shown above: Certificate issuer data for HTTPS traffic caused by Qakbot (example 3 of 3).
Forensics on infected Windows host
See the images below for my forensic investigation on the infected Windows host.
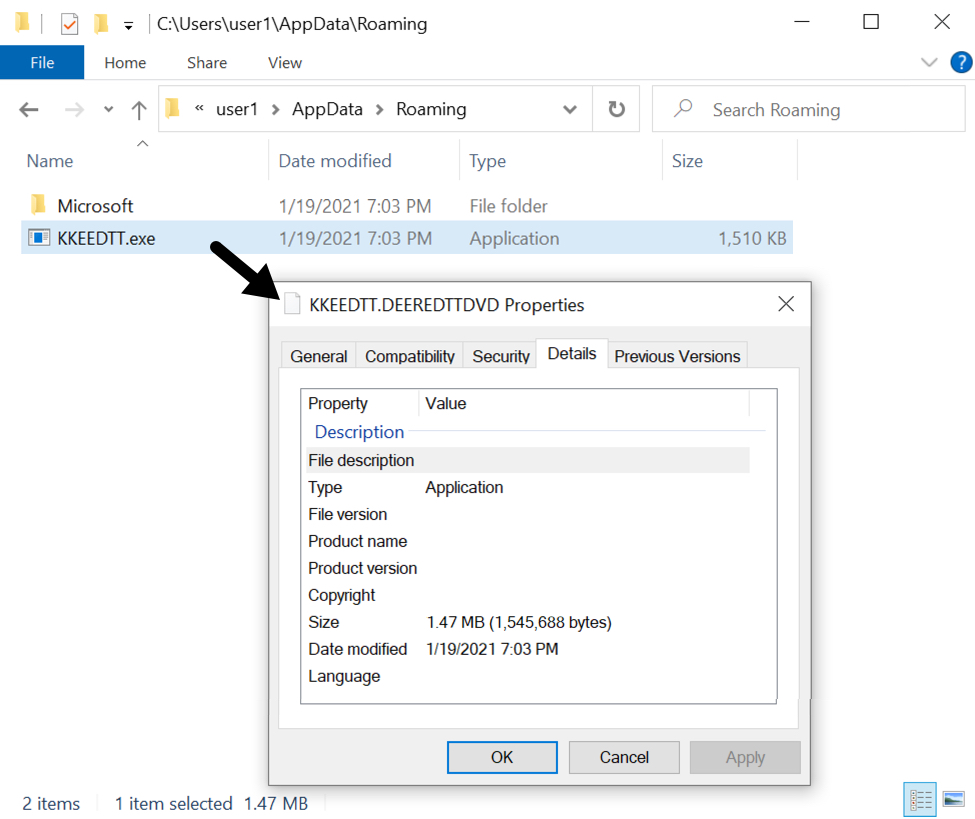
Shown above: Initial Qakbot DLL saved to the infected Windows host.
Shown above: Other artifacts from the infected Windows host.
Shown above: Windows registry updates caused by Qakbot on the infected host.
Indicators of Compromise (IOCs)
SHA256 hash: 8ebba35fa60f107aa4e19fa39ae831feab4ffb1718bdca016670d3898b2fe4fc
- File size: 25,543 bytes
- File name: Complaint_Copy_1206700885_01192021.xlsm
- File description: Spreadsheet with macro for Qakbot
SHA256 hash: f9560829534803161c87666795f0feab028ff484fac5170b515390b50e8050fd
- File size: 1,545,688 bytes
- File location: hxxp://senzo-conseil-expat[.]fr/bqkckb/5555555555.jpg
- File location: C:\Users\[username]\AppData\Roaming\KKEEDTT.DEEREDTTDVD
- File description: Initial DLL for Qakbot
- Run method: rundll32.exe [filename],DllRegisterServer
HTTP request caused by Excel macro to retrieve DLL for Qakbot:
- 51.210.14[.]58 port 80 - senzo-conseil-expat[.]fr - GET /bqkckb/5555555555.jpg
HTTPS traffic from the infected host:
- 95.76.27[.]6 port 443
- 185.14.30[.]127 port 443
- 172.115.177[.]204 port 2222
Web traffic connectivity checks from the infected host (HTTPS traffic):
- port 443 - www.openssl.org
- port 443 - api.ipify.org
TCP traffic from the infected host:
- 54.36.108[.]120 port 65400
Connectivity checks to mail servers from the infected host:
- 172.217.195.109 port 993 - imap.gmail.com
- 108.177.104.28 port 25 - smtp-relay.gmail.com
- 108.177.104.28 port 465 - smtp-relay.gmail.com
- 108.177.104.28 port 587 - smtp-relay.gmail.com
- 64.29.151.102 port 110 - mail.myfairpoint.net
- 64.29.151.102 port 143 - mail.myfairpoint.net
- 74.6.106.29 port 995 - inbound.att.net
Certificate issuer data for HTTPS traffic to 95.76.27[.]6 over TCP port 443:
- id-at-countryName=NL
- id-at-stateOrProvinceName=ED
- id-at-localityName=Dadoe
- id-at-organizationName=Letx Uqe Dzcmtewzs Kctonlfg Inc.
- id-at-commonName=epeivate.biz
Certificate issuer data for HTTPS traffic to 185.14.30[.]127 over TCP port 443:
- id-at-countryName=US
- id-at-stateOrProvinceName=NY
- id-at-localityName=New York
- id-at-organizationName=cloudservers03.com
- id-at-commonName=cloudservers03.com
Certificate issuer data for HTTPS traffic to 172.115.117[.]204 over TCP port 2222:
- id-at-countryName=DE
- id-at-stateOrProvinceName=IQ
- id-at-localityName=Aeur
- id-at-organizationName=Cepasduq Nqo Ooifzetkp Mqen
- id-at-commonName=ltxkvijevns.com
Final words
A pcap of the infection traffic along with malware (Excel file and DLL) from an infected host can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments