Next-generation Web browsers?
A couple of weeks ago I was presenting at the III OWASP Spain Chapter Meeting about "Web security threats and incidents" (presentation in Spanish). I tried to emphasize one of the (if not THE) biggest security threats nowadays: Web-based attacks. Everybody runs at least an operating system, a mail reader (except for Web mail, so even this one is optional) and a Web browser; conclusion: the attackers are focused on breaking into computers through out the latter.
A few days after the conference, Jesus (who attended the meeting) wrote me in commenting about a specific case he saw when browsing what seemed to be a legitimate site. After browsing to the site, the main page contained an ads-related script tag loading ads contents from "feed.peakclick.com", specifically from "res.php" with some additional parameters like the subscriber id, keyword, and referrer:
<script>hxxp://feed.peakclick.com/res.php?pin=d0..67&id=1&keyword=isc&num=3
&utf=1&ref=hxxp://original_site</script>
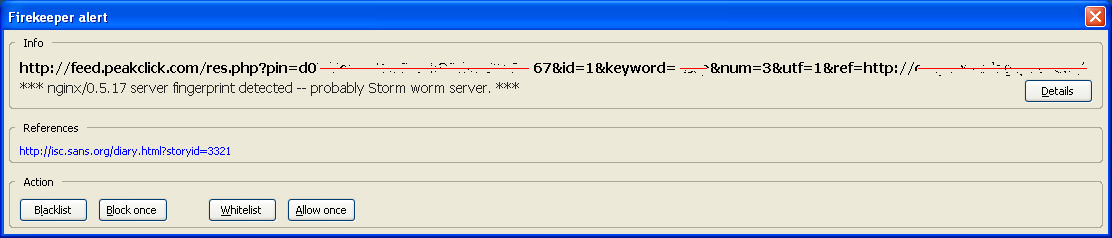
At this point is when the user could get suspicious if he is using the Firekeeper Firefox extension, as it generates an alert:
Although Web-based malware is extremely common nowadays, as the alert signature referenced us (the ISC) directly, I decided to research it in-depth. Unfortunately (from a research perspective), it was a false positive and there was no malicious content loaded from peakclick. The script simply loads an ad and includes links to the company being announced. If the user click on these links, he can reach to the final ad content after five HTTP redirections (302 Found responses).
The alert is generated because there is a Firekeeper experimental rule that matches if any of the HTTP headers contain the string "nginx/0.5.17". This server string corresponds to the Engine X small Web server, widely used for malware distribution and the Storm Worm. However, the existence of this server does not directly mean malicious content, as in this case.
Although the signature is too generic, the idea behind the Firekeeper tool (we mentioned it a year ago) is great, as it provides IDS/IPS capabilities where they are required today, at the browser level, after decompression and decryption (https) have been applied. The tool is based on rules (similar to Snort), although it only implements a small set at this point. Unfortunately, the latest version, 0.2.14 (October 2007), is still in alpha status and somehow not very active.
Definitely, we need more tools like this one in order to enforce advanced security policies at the Web browser level (not talking about Web privacy or anti-phising toolbars). I guess we will start to see some compartmentalization built-in inside the browsers soon, trying to stop very common attacks such as CSRF (Cross-Site Request Forgery). Some Web browsing recommendations (some of them previously mentioned at the ISC) are:
- Run the latest Web browser version and apply all available security patches and updates.
- Secure your Web browser (US-CERT) and tweak the browser security settings.
- Increase the security stance of the browser using IE Zones (for Internet Explorer) or add-ons on Firefox, such as NoScript. Additionally, there are multiple ways of stopping Web scripts at the infrastructure (from a previous ISC post).
- Run the Web browser with a non-privileged user different from the one you run your OS session with, trusting OS filesystem ACLs. I'm assuming you are not running as Administrator / root, are you? :)
- Use two Web browsers: one just for critical access, and a different one for casual Web browsing.
- Run the Web browser inside an "isolated" environment (sandbox), such as SandboxIE, or with minimum privileges, using DropMyRights.
- Run the Web browser in a virtual machine, custom-made or a public one, such as the VMware Browser Appliance (Ubuntu + Firefox).
- Use more advanced add-ons, such as Firekeeper (still alpha), FlashBlock or Adblock (there are hundreds).
- Or a combination of some of the above...
Unfortunately, some of these recommendations only apply to the security or IT professional and cannot be applied yet to end users. We need to increase the usability of some of the currently available options for widespread usage. It is time for the next-generation Web browsers!
Happy and safe Web browsing! If you have other tips & tricks for safe Web browsing, let us know, and I'll update this post.
--
Raul Siles
www.raulsiles.com
UPDATE: Dave wrote in (thanks!) to mention a MS tool called MakeMeAdmin. As I denoted above, my post works under the assumption that you are using a regular user and running only specific tasks as Administrator (Windows) or root (Unix/Linux) using "RunAs" or "sudo" respectively. Sometimes you need to perform several high privilege tasks (or overcome some OS restrictions) and use "RunAs" to run explorer.exe or "su".
The main drawback of "RunAs" exists when you need to access network resources with a domain account, or you need to use settings from your (regular) profile. This is where MakeMeAdmin is extremely useful and provides you a command prompt with Administrator rigths (very similar to a Unix/Linux "su" command).


Comments
Ron
Mar 29th 2008
1 decade ago