More Equation Editor Exploit Waves
This morning, I spotted another wave of malicious documents that (ab)use again CVE-2017-11882 in the Equation Editor (see my yesterday's diary[1]). This time, malicious files are RTF files. One of the samples is SHA256:bc84bb7b07d196339c3f92933c5449e71808aa40a102774729ba6f1c152d5ee2 (VT score: 19/57[2]).
Once opened, it downloads a payload via the bit.ly URL shortening service. The URL is:
hxxps://bitly[.]com/2EapuIc
bit.ly is very convenient for security analysts because, adding a "+" sign at the end of the URL, you can see what is the original URL but also some statistics. It always impresses me to see how many times such URLs are visited:
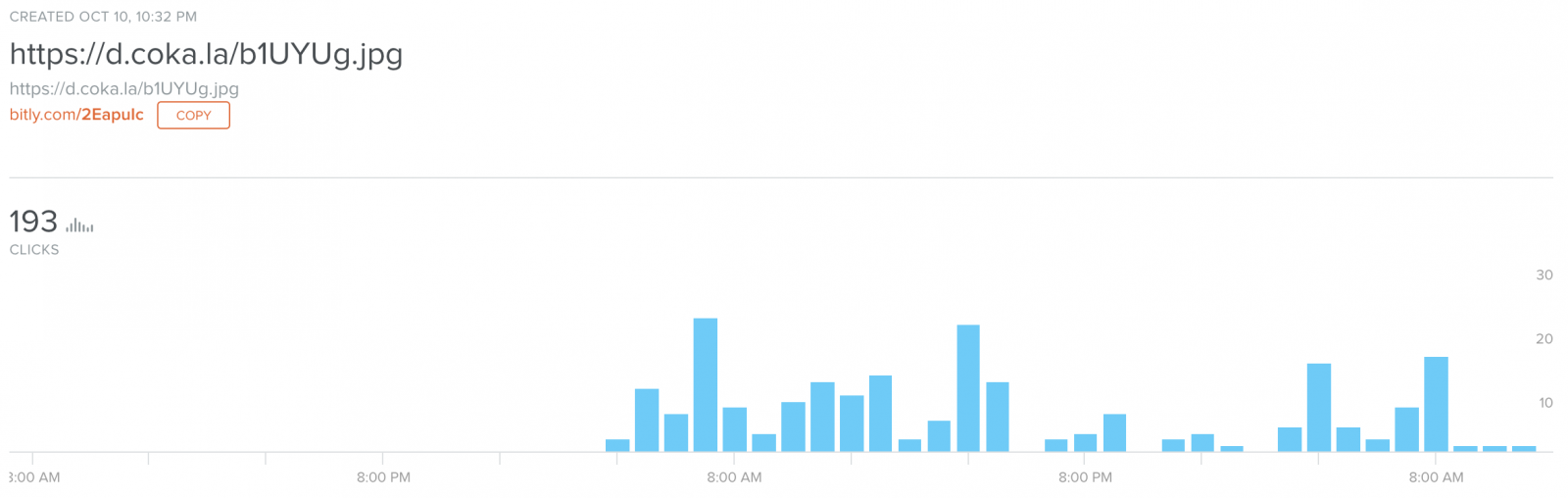
We can see that 193 "clicks" have been performed in this URL, which means that the RTF document has successfully exploited the vulnerability 193 times only for this URL. In the meantime, I spotted others bit.ly URLs:
/2QJY8dD /2QGnbyg /2EdlK92 /2QKOqaX /2yry5A8 /2EdlAOO
Of course, the shortened URLs are not images but a malicious PE file (SHA256:a4dd1c849d1e66faecbf29c0304cc26c7948e96ead0e73896f15b0db44bed3fa - VT Score: 30/67[3])
This means, that this Equation Editor vulnerability is still present on many computers.
[1] https://isc.sans.edu/forums/diary/New+Campaign+Using+Old+Equation+Editor+Vulnerability/24196/
[2] https://www.virustotal.com/#/file/bc84bb7b07d196339c3f92933c5449e71808aa40a102774729ba6f1c152d5ee2/details
[3] https://www.virustotal.com/#/file/a4dd1c849d1e66faecbf29c0304cc26c7948e96ead0e73896f15b0db44bed3fa/detection
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments