March 2021 Traffic Analysis Quiz
Introduction
Today's diary is a new traffic analysis quiz. For this quiz, I ask participants to write an incident report that identifies the affected Windows host and user account.
If possible, try to identify the malware family associated with this infection. But there are many different types of malware, and they're constantly evolving and multiplying, so don't worry if you don't recognize the malware family.

Shown above: So much malware out there.
The packet capture (pcap) for today's traffic analysis quiz is contained in a zip archive hosted at this Github repository. The repository also contains another zip archive with malware and artifacts recovered from the infected Windows host. Be very careful with the malware and artifacts zip. If you don't know what you're doing, do not download the malware and artifacts. I also recommend participants do this exercise in a non-Windows environment, if possible.
Unlike my previous traffic analysis quizzes, this quiz does not include any alerts on the network traffic.
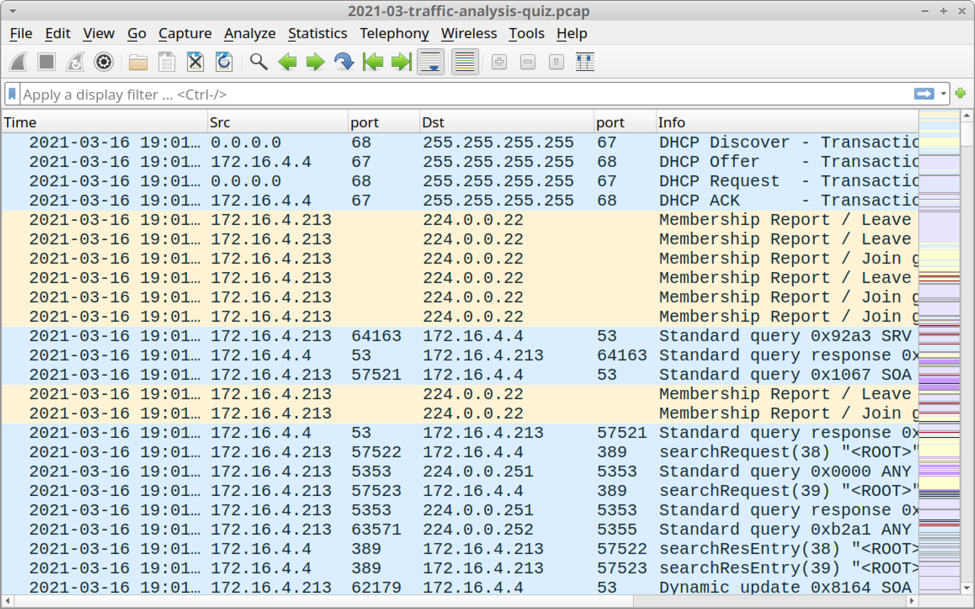
Shown above: Pcap for this traffic analysis quiz opened in Wireshark.
Requirements
This type of analysis requires Wireshark. Wireshark is my tool of choice to review pcaps of infection traffic. However, default settings for Wireshark are not optimized for web-based malware traffic. That's why I encourage people to customize Wireshark after installing it. To help, I've written a series of tutorials. The ones most helpful for this quiz are:
- Wireshark Tutorial: Changing Your Column Display
- Wireshark Tutorial: Identifying Hosts and Users
- Wireshark Tutorial: Display Filter Expressions
- Using Wireshark - Exporting Objects from a Pcap
I always recommend participants use a non-Windows environment like BSD, Linux, or macOS. Why? Because most pcaps in these traffic analysis quizzes contain traffic with Windows-based malware. If you're using a Windows host to review such pcaps, your antivirus (or Windows Defender) may delete or alter the pcap. Worst case? If you extract malware from a pcap and accidentally run it, you might infect your Windows computer.
In this case, I've also included a zip archive that contains malware and artifacts retrieved from the infected Windows host. Unless you are a skilled malware analyst, you should avoid examining the contents of that particular zip archive on a Windows computer, because it's Windows-based malware.
Active Directory (AD) Environment
The infected Windows host is part of an AD environment, so the pcap contains information about the Windows user account. The user account is formatted as firstname.lastname. The AD environment characteristics are:
- LAN segment range: 172.16.4.0/24 (172.16.4.0 through 172.16.4.255)
- Domain: baritonetv.com
- Domain Controller: 172.16.4.4 - BaritoneTV-DC
- LAN segment gateway: 172.16.4.1
- LAN segment broadcast address: 172.16.4.255
Final Words
Again, the zip archive with a pcap of the traffic for this exercise is available in this Github repository. Analysis of this infection will be posted in tomorrow's ISC diary.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments