KPOT Analysis: Obtaining the Decrypted KPOT EXE
In diary entry "KPOT Deployed via AutoIt Script" I obtained 3 files:
- A legitimate, signed AutoIt interpreter (this is not malware)
- A heavily obfuscated AutoIt script, that is encoded as a PEM certificate
- An encrypted EXE: KPOT info stealer
In this diary entry, I'll share more details on how I obtained the decrypted KPOT EXE. Also take a look at "Reader Analysis: "Dynamic analysis technique to get decrypted KPOT Malware.", a reader's analysis.
To obtain the decrypted EXE, I used dynamic analysis. By executing the AutoIt interpreter with the decoded AutoIt script, the shellcode in the AutoIt script decrypted the KPOT EXE and injected it in a dllhost.exe process (process hollowing):
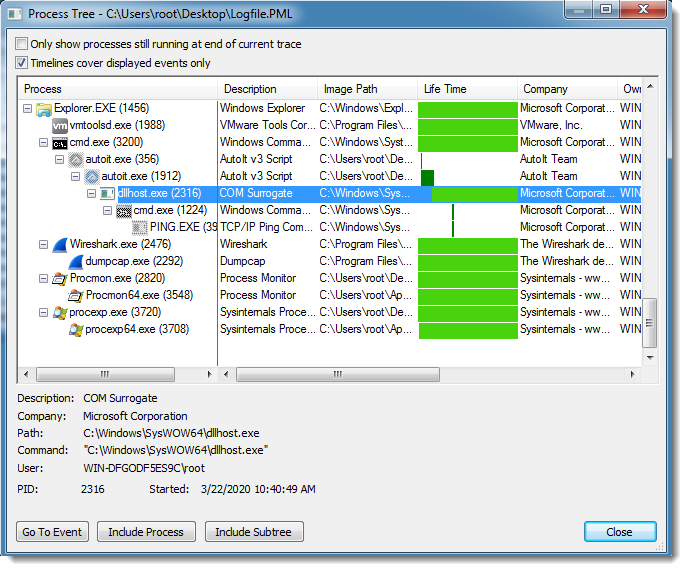
While dllhost.exe was running, I created a process dump for it with procdump. I used option -mp to dump all read/write memory pages.
Then I used my tool pecheck.py to carve PE files:
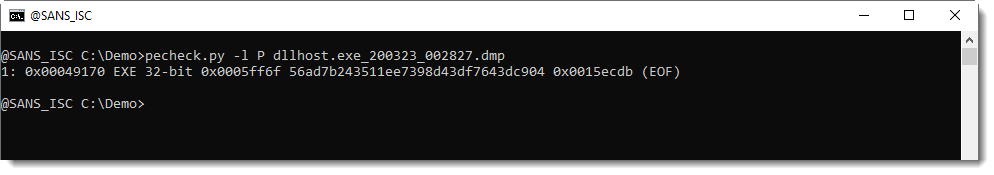
As can be seen, one 32-bit executable was found inside the process memory dump. As this EXE was not present on VirusTotal, I had to extract it like this:
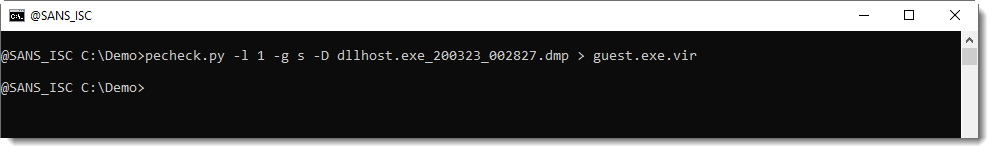
With option -l 1, I select the first PE file found inside the memory dump, with option -g s, I extracted the stripped PE file (e.g. PE file without overlay), and option -D is required to produce a binary dump (default is hex/ascii dump).
I submitted the EXE to VirusTotal: 56ad7b243511ee7398d43df7643dc904.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments