IOS SSL vulnerability also present in OS X
Friday Apple released an update to IOS, to versions 7.0.6 and 6.16, to fix an SSL Authentication flaw. Indication is that this flaw is easily exploitable, so this update should be applied as soon as practical. Apple has also indicated that this flaw also appears in OS X and that a patch is "coming soon". In the meantime be careful where you browse with your OS X based machines.
Adam Langley at the ImperialViolet blog has created a test page to help you determine if your browser is vulnerable to this attack. If you can load content from the test page you are at risk, an error indicates you should be ok.
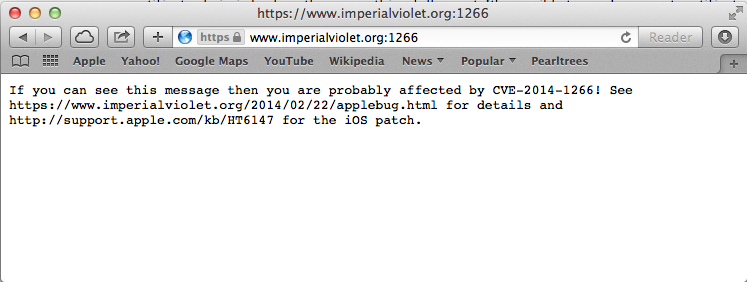
On my two OS X based machines with current versions of Firefox, Chrome and Safari, only Safari displayed the vulnerability. Both Chrome and Firefox appeared to be ok. Below is the Firefox output.
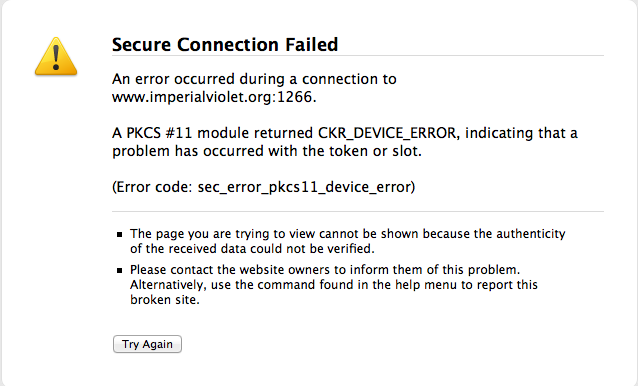
Chrome just displayed its "This webpage is not available" error.
Researchers have determined that the flaw is caused by an errant goto statement. I realize that, although progress has been made, effective code review, code coverage, and code regression process and tools continue to challenge software development, but this seems like an easy one to catch.
-- Rick Wanner - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)


Comments
Anonymous
Feb 23rd 2014
1 decade ago
EDITED LATER TO ADD: The answer became clear when 10.9.2 came out, not that I excuse the delay. http://www.zdnet.com/apple-what-took-so-long-7000026780/
Anonymous
Feb 25th 2014
1 decade ago