Dalexis/CTB-Locker malspam campaign
Malware Every Day
Malicious spam (malspam) is by sent by botnets every day. These malspam campaigns send malware designed to infect Windows computers. I'll see Dridex or Upatre/Dyre campaigns a daily basis. Fortunately, most of these emails are blocked by our spam filters.
This diary concerns a recent malspam wave on Tuesday 2015-04-28 from a botnet pushing Dalexis/CTB-Locker.
What is Dalexis/CTB-Locker?
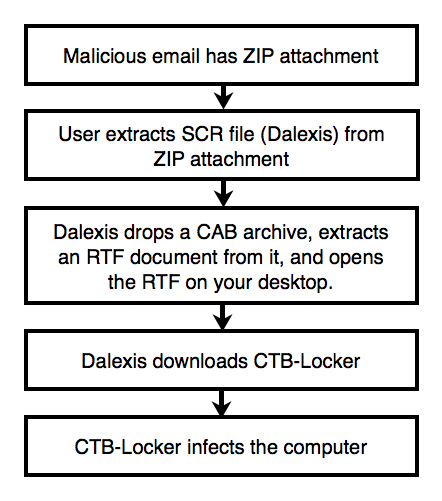
Dalexis is a malware downloader. It drops a CAB file with embedded document that's opened on a user's computer [1] then downloads more malware. Dalexis is often used to deliver CTB-Locker [2][3]. CTB-Locker is ransomware that encrypts files on your computer. In exchange for a ransom payment, the malware authors will provide a key to decrypt your files. Behavior of this malware is well-documented, but small changes often occur as new waves of malspam are sent out.
A similar wave of malspam from Monday 2015-04-27 was reported by techhelplist.com [4]. The next day saw similar activity. This campaign will likely continue. Below is a flow chart from Tuesday's wave of Dalexis/CTB-Locker malspam:
The messages have slightly different subject lines, and each email attachment has a different file hash. I infected a host using one of the attachments. Below are links to the associated files:
- Extracted malware (Dalexis downloader): https://malwr.com/analysis/OTVjMzRjZDFjNWYwNDlmYzk4MTVmOWRlM2IzMmVkN2Y/
- CTB-Locker downloaded by Dalexis: https://malwr.com/analysis/M2NlYmU3YmIwMzM0NGY1NTk4MTBjMzM0ZmZmZmZmZTE/
- PCAP from the infected host (10.8 MB): http://www.malware-traffic-analysis.net/2015/04/28/2015-04-28-Dalexis-and-CTB-Locker-traffic.pcap.zip
- ZIP file of 24 Dalexis samples from this malspam wave: http://www.malware-traffic-analysis.net/2015/04/28/2015-04-28-Dalexis-samples.zip
The ZIP file is password-protected with the standard password. If you don't know it, email [email protected] and ask.
Infection as Seen from the Desktop
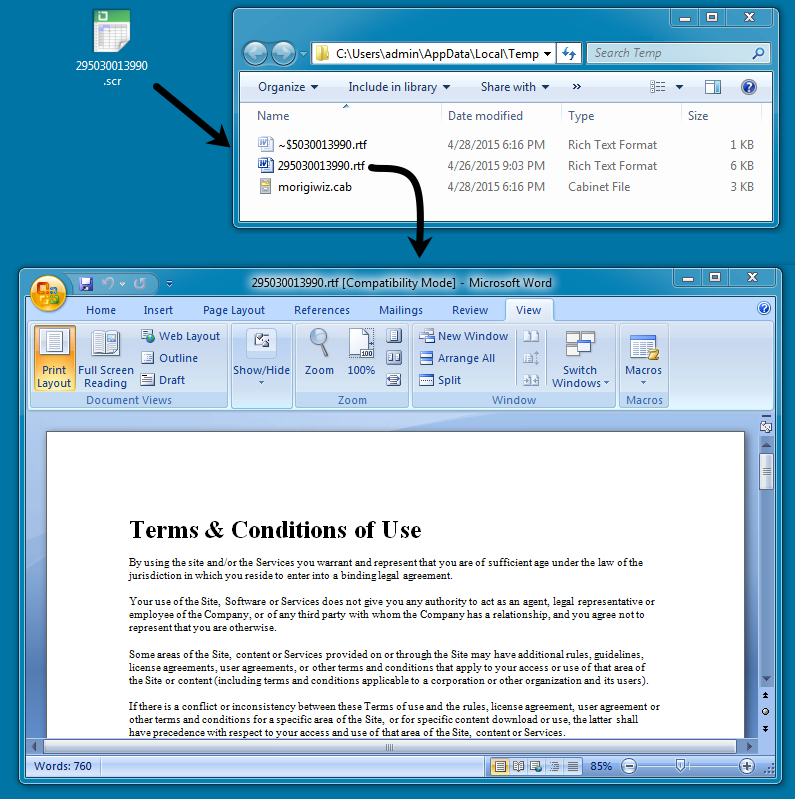
Extracted malware from these email attachments is an SCR file with an Excel icon. The following image shows what happened immediately after opening this Dalexis malware on the desktop:
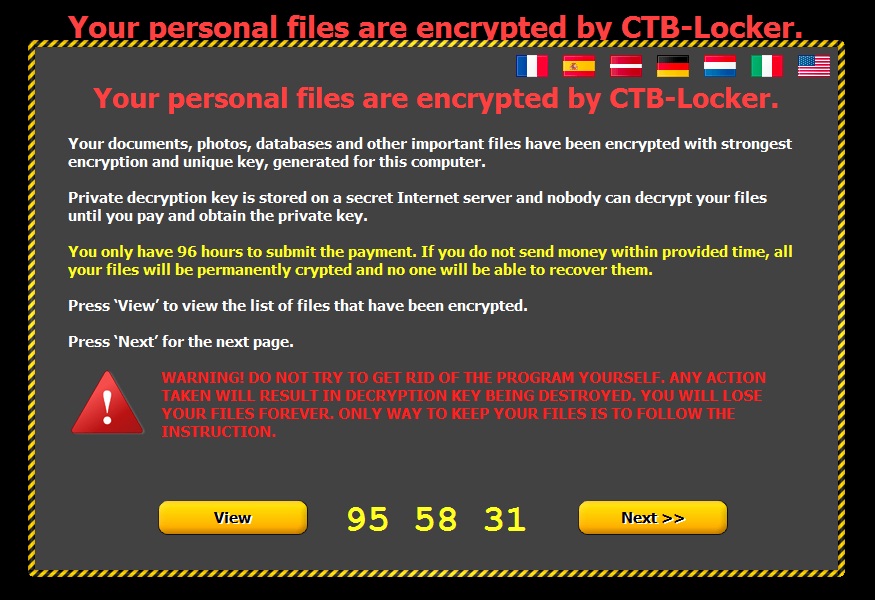
A few minutes later, the desktop shows signs of infection by CTB-Locker:
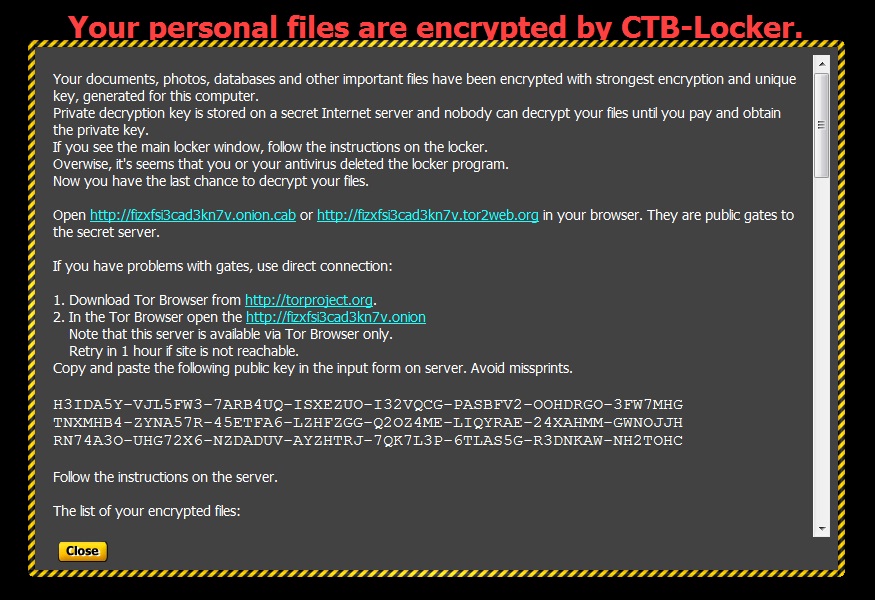
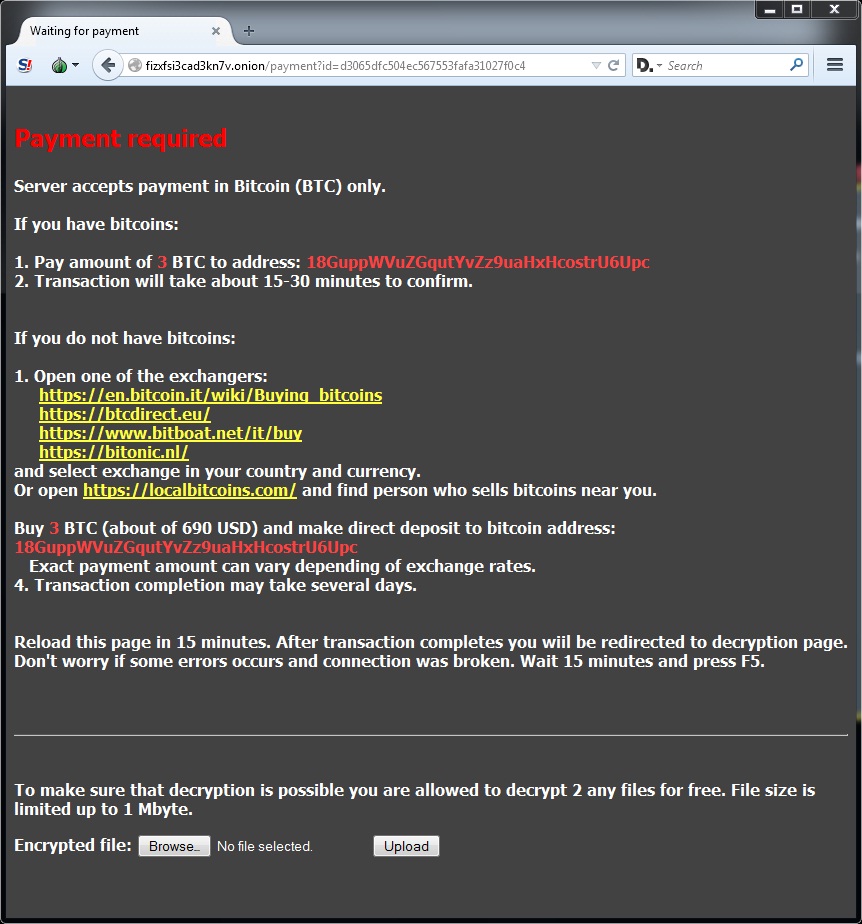
Instructions for decrypting your files are shown below:
Had to download a Tor browser to get at the decryption instructions. The bitcoin address for the ransom payment is: 18GuppWVuZGqutYvZz9uaHxHcostrU6Upc (check here to see if any transactions have been made by this bitcoin account).
Traffic from the Infected Host
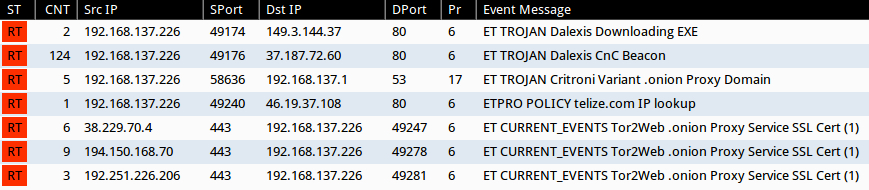
Below is an image from Sguil on Security Onion for some of the EmergingThreats and ETPRO snort events seen during this infection:
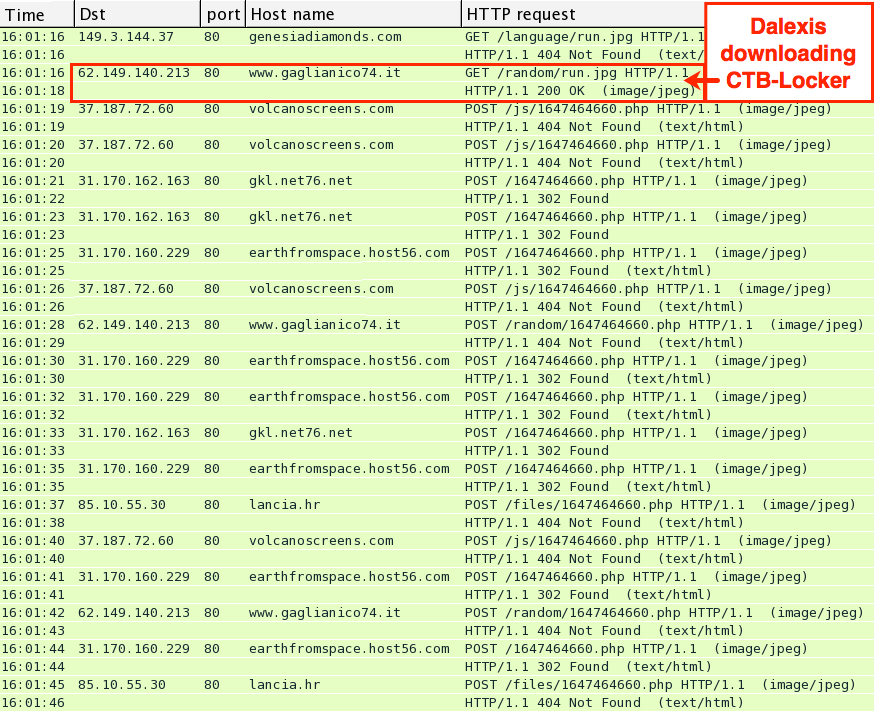
Dalexis uses an HTTP GET request to download CTB-Locker. The file is encrypted in transit, but I retrieved a decrypted copy from the infected host. Dalexis reports to a command and control (CnC) server after the malware is successfully downloaded.
In the image below, you'll find HTTP POST requests to different servers as Dalexis tries to find a CnC server that will respond. This sample of Dalexis did 124 HTTP POST requests before a server finally replied with a 200 OK.
For indicators of compromise (IOCs), a list of domains unique to this infection follows:
(Read: IP address - domain name)
- 31.170.160.229 - earthfromspace.host56.com
- 31.170.162.163 - gkl.net76.net
- 37.187.72.60 - volcanoscreens.com
- 46.19.37.108 - ip.telize.com
- 62.149.140.213 - www.gaglianico74.it
- 85.10.55.30 - lancia.hr
- 192.185.224.67 - bdfschool.net
- various - fizxfsi3cad3kn7v.tor2web.org
- various - fizxfsi3cad3kn7v.onion.cab
Example of Malspam From Tuesday 2015-04-28
From: Eda Uhrhammer
Date: Tuesday, April 28, 2015 at 16:16 UTC
To: [redacted]
Subject: [Issue 5261CC6247C37550] Account #295030013990 Temporarily Locked
Dear user,
We detect unauthorized Login Attempts to your ID #295030013990 from other IP Address.
Please re-confirm your identity. See attached docs for full information.
===
Eda Uhrhammer
Millard Peter
111 Hunter Street East, Peterborough, ON K9H 1G7
CANADA
705-759-7751
Attachment: 295030013990.zip
NOTE: The emails contain various international names, addresses, and phone numbers in the signature block.
Emails Collected
Start time: 2015-04-28 10:00:13 UTC
End time: 2015-04-28 16:16:28 UTC
Emails found: 24
Senders and Subject Lines
- Sender: [email protected] - Subject: [Issue 35078504EBA94667] Account #59859805294 Temporarily Locked
- Sender: [email protected] - Subject: [Issue 84908E27DF477852] Account #40648428303 Temporarily Locked
- Sender: [email protected] - Subject: [Issue 8694097116D18193] Account #257547165590 Temporarily Locked
- Sender: [email protected] - Subject: [Issue 11123E749D533902] Account #621999149649 Temporarily Locked
- Sender: [email protected] - Subject: [Issue 24789101648C8407] Account #250874039146 Temporarily Locked
- Sender: [email protected] - Subject: [Issue 6412D16736356564] Account #238632826769 Temporarily Locked
- Sender: [email protected] - Subject: [Issue 9139F9678C9A7466] Account #216021389500 Temporarily Locked
- Sender: [email protected] - Subject: [Issue 982886631E9E7489] Account #114654416120 Temporarily Locked
- Sender: [email protected] - Subject: [Issue 4895D8D81ADE1399] Account #843871639720 Temporarily Locked
- Sender: [email protected] - Subject: [Issue 72986FD85CE93134] Account #622243029178 Temporarily Locked
- Sender: [email protected] - Subject: [Issue 27883AA546718876] Account #475770363394 Temporarily Locked
- Sender: [email protected] - Subject: [Issue 5384A21F5AB26075] Account #717973552140 Temporarily Locked
- Sender: [email protected] - Subject: [Issue 5694B0643FCD587] Account #642271991381 Temporarily Locked
- Sender: [email protected] - Subject: [Issue 8219423F8CFB6864] Account #692223104314 Temporarily Locked
- Sender: [email protected] - Subject: [Issue 70308834A3929842] Account #339648082242 Temporarily Locked
- Sender: [email protected] - Subject: [Issue 33190977A2D04088] Account #831865092451 Temporarily Locked
- Sender: [email protected] - Subject: [Issue 706584024E142555] Account #196387638377 Temporarily Locked
- Sender: [email protected] - Subject: [Issue 830689BB76F4615] Account #162723085828 Temporarily Locked
- Sender: [email protected] - Subject: [Issue 46714D12FB834480] Account #526735661562 Temporarily Locked
- Sender: [email protected] - Subject: [Issue 39494AFE933A5158] Account #552561607876 Temporarily Locked
- Sender: [email protected] - Subject: [Issue 974641F53DD66126] Account #325636779394 Temporarily Locked
- Sender: [email protected] - Subject: [Issue 7505716EA6244832] Account #603263972311 Temporarily Locked
- Sender: [email protected] - Subject: [Issue 50438E220A5D7432] Account #906152957589 Temporarily Locked
- Sender: [email protected] - Subject: [Issue 5261CC6247C37550] Account #295030013990 Temporarily Locked
NOTE: The sending email addresses might be spoofed.
Attachments
- 114654416120.zip - 19,135 bytes - MD5 hash: 1a9fdce6b6efd094af354a389b0e04da
- 162723085828.zip - 20,688 bytes - MD5 hash: a1b066361440a5ff6125f15b1ba2e1b1
- 196387638377.zip - 20,681 bytes - MD5 hash: 01f8976034223337915e4900b76f9f26
- 216021389500.zip - 19,135 bytes - MD5 hash: ab9a07054a985c6ce31c7d53eee90fbe
- 238632826769.zip - 19,135 bytes - MD5 hash: 899689538df49556197bf1bac52f1b84
- 250874039146.zip - 19,135 bytes - MD5 hash: eea0fd780ecad755940110fc7ee6d727
- 257547165590.zip - 19,114 bytes - MD5 hash: f236e637e17bc44764e43a8041749e6c
- 295030013990.zip - 20,168 bytes - MD5 hash: eda8075438646c617419eda13700c43a
- 325636779394.zip - 20,177 bytes - MD5 hash: d00861c5066289ea9cca3f0076f97681
- 339648082242.zip - 20,703 bytes - MD5 hash: 657e3d615bb1b6e7168319e1f9c5039f
- 40648428303.zip - 19,113 bytes - MD5 hash: b7fe085962dc7aa7622bd15c3a303b41
- 475770363394.zip - 20,642 bytes - MD5 hash: 2ba4d511e07090937b5d6305af13db68
- 526735661562.zip - 20,710 bytes - MD5 hash: 24698aa84b14c42121f96a22fb107d00
- 552561607876.zip - 20,709 bytes - MD5 hash: 04abf53d3b4d7bb7941a5c8397594db7
- 59859805294.zip - 19,071 bytes - MD5 hash: b2ca48afbc0eb578a9908af8241f2ae8
- 603263972311.zip - 20,175 bytes - MD5 hash: fa43842bda650c44db99f5789ef314e3
- 621999149649.zip - 19,135 bytes - MD5 hash: 802d9abf21c812501400320f2efe7040
- 622243029178.zip - 20,681 bytes - MD5 hash: 0687f63ce92e57a76b990a8bd5500b69
- 642271991381.zip - 20,644 bytes - MD5 hash: 0918c8bfed6daac6b63145545d911c72
- 692223104314.zip - 20,703 bytes - MD5 hash: 2e90e6d71e665b2a079b80979ab0e2cb
- 717973552140.zip - 20,721 bytes - MD5 hash: 5b8a27e6f366f40cda9c2167d501552e
- 831865092451.zip - 20,718 bytes - MD5 hash: 9c1acc3f27d7007a44fc0da8fceba120
- 843871639720.zip - 20,713 bytes - MD5 hash: 1a6b20a5636115ac8ed3c4c4dd73f6aa
- 906152957589.zip - 20,134 bytes - MD5 hash: b9d19a68205f2a7e2321ca3228aa74d1
Extracted Malware
- 114654416120.scr - 98,304 bytes - MD5 hash: 46838a76fbf59e9b78d684699417b216
- 162723085828.scr - 90,112 bytes - MD5 hash: 8f5df86fdf5f3c8e475357bab7bc38e8
- 196387638377.scr - 90,112 bytes - MD5 hash: 59f71ef10861d1339e9765fb512d991c
- 216021389500.scr - 98,304 bytes - MD5 hash: 0baa21fab10c7d8c64157ede39453ae5
- 238632826769.scr - 98,304 bytes - MD5 hash: f953b4c8093276fbde3cfa5e63f990eb
- 250874039146.scr - 98,304 bytes - MD5 hash: 6580e4ee7d718421128476a1f2f09951
- 257547165590.scr - 94,208 bytes - MD5 hash: 6a15d6fa9f00d931ca95632697e5ba70
- 295030013990.scr - 86,016 bytes - MD5 hash: 54c1ac0d5e8fa05255ae594adfe5706e
- 325636779394.scr - 94,208 bytes - MD5 hash: 08a0c2aaf7653530322f4d7ec738a3df
- 339648082242.scr - 94,208 bytes - MD5 hash: 1aaecdfd929725c195a7a67fc6be9b4b
- 40648428303.scr - 94,208 bytes - MD5 hash: f51fcf418c973a94a7d208c3a8a30f19
- 475770363394.scr - 81,920 bytes - MD5 hash: dbea4b3fb5341ce3ca37272e2b8052ae
- 526735661562.scr - 94,208 bytes - MD5 hash: c0dc49296b0aec09c5bfefcf4129c29b
- 552561607876.scr - 98,304 bytes - MD5 hash: 9239ec6fe6703279e959f498919fdfb0
- 59859805294.scr - 86,016 bytes - MD5 hash: a9d11a69c692b35235ce9c69175f0796
- 603263972311.scr - 94,208 bytes - MD5 hash: bcaf9ce1881f0f282cec5489ec303585
- 621999149649.scr - 98,304 bytes - MD5 hash: 70a63f45eb84cb10ab1cc3dfb4ac8a3e
- 622243029178.scr - 90,112 bytes - MD5 hash: d1b1e371aebfc3d500919e9e33bcd6c1
- 642271991381.scr - 81,920 bytes - MD5 hash: 15a5acfbccbb80b01e6d270ea8af3789
- 692223104314.scr - 94,208 bytes - MD5 hash: fa0fe28ffe83ef3dcc5c667bf2127d4c
- 717973552140.scr - 98,304 bytes - MD5 hash: 646640f63f327296df0767fd0c9454d4
- 831865092451.scr - 98,304 bytes - MD5 hash: ec872872bff91040d2bc1e4c4619cbbc
- 843871639720.scr - 98,304 bytes - MD5 hash: b8e8e3ec7f4d6efee311e36613193b8d
- 906152957589.scr - 94,208 bytes - MD5 hash: 36abcedd5fb6d17038bd7069808574e4
Updates
- Shortly after I composed this diary entry, techhelplist.com posted an article about this particular wave of malspam on 2015-04-28 at: https://techhelplist.com/index.php/spam-list/798-issue-account-temporarily-locked-various-malware
- The Dalexis/CTB-Locker malspam campaign continued on Wednesday 2015-04-29 with subject line of: Your account [random number] has been banned
---
Brad Duncan, Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] http://www.microsoft.com/security/portal/threat/encyclopedia/entry.aspx?Name=TrojanDownloader:Win32/Dalexis#tab=2
[2] https://heimdalsecurity.com/blog/ctb-locker-ransomware/
[3] https://blogs.mcafee.com/mcafee-labs/rise-backdoor-fckq-ctb-locker
[4] https://techhelplist.com/index.php/spam-list/796-your-account-has-been-something-bad-various-malware


Comments
18d3b77237f967e9c908e122dd4f6f73 392831579511.scr
209b52131f620e4332124260cb8df4b8 428171617658.scr
ac748525dad247828d15184e505d9561 836753228073.scr
7c724fd7ccf8961951e06c23429c2442 428171617658.zip
cb046e111cac090f9566c1e38a44c3fa 836753228073.zip
We recently started doing user education using phishme.com (shameless plug) and it's been paying off. Our users are paying more attention now and actually reporting phish. Also, the Outlook users now have a phishme-provided plugin so it's just one button-click to submit it to our ticketing system (where I get full headers - everything I need to dig the email out of the logs and pick apart any malware/URLs).
Give a report I can usually find out who else got it (are they targeting specific groups of users), did anyone fall for it (searching DNS query logs for URL hostnames or hostnames the attached malware queries for), and proactively block any hostnames the malware uses for a 2nd stage download or an HTTP POST, etc.
Anonymous
Apr 30th 2015
1 decade ago