Brute-Force ZIP Password Cracking with zipdump.py
Gebhard's diary entry "Brute Forcing Simple Archive Passwords" inspired me to make an update to my zipdump.py tool to add brute-force password cracking.
Years ago, I added dictionary password cracking to zipdump.py (a tool to analyze ZIP files).
Hence adding a brute-force attack mode would be simple.
One can start a zipdump dictionary attack with options -P (passwordfile) or --passwordfilestop. You give it a text file with passwords to try (like rockyou), or you use file name ".", and then it uses a small builtin list (that's John-the-Ripper public domain password list).
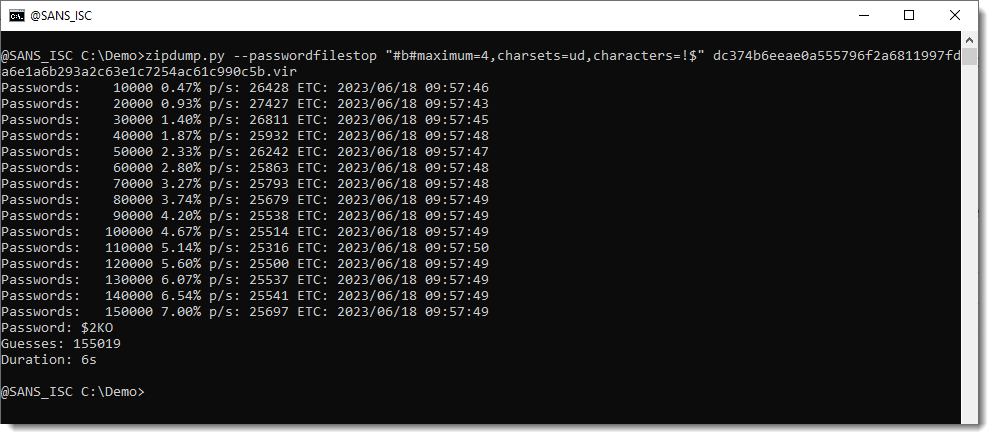
Now, with the latest version, you can start brute-force attack mode with the following special filename: #b#.
This starts a brute-force attack, with password guesses from 1 to 3 characters long, and characters selected from these sets of characters: uppercase and lowercase ASCII letters, digits, all punctuation characters (Python's definition) and space character.
When I run this on Gebhard's sample, the password is not recovered:
The brute-force attack ran almost at 25.000 password guesses per second on the laptop I tested this on.
Now let's change some parameters. Gebhard found that the password is 4 characters long, and consisted of uppercase letters and digits.
I'm using these parameters: maximum=4,charsets=lud
This starts a brute-force attack of passwords consisting of uppercase and lowercase letters and digits, between 1 and 4 characters long.
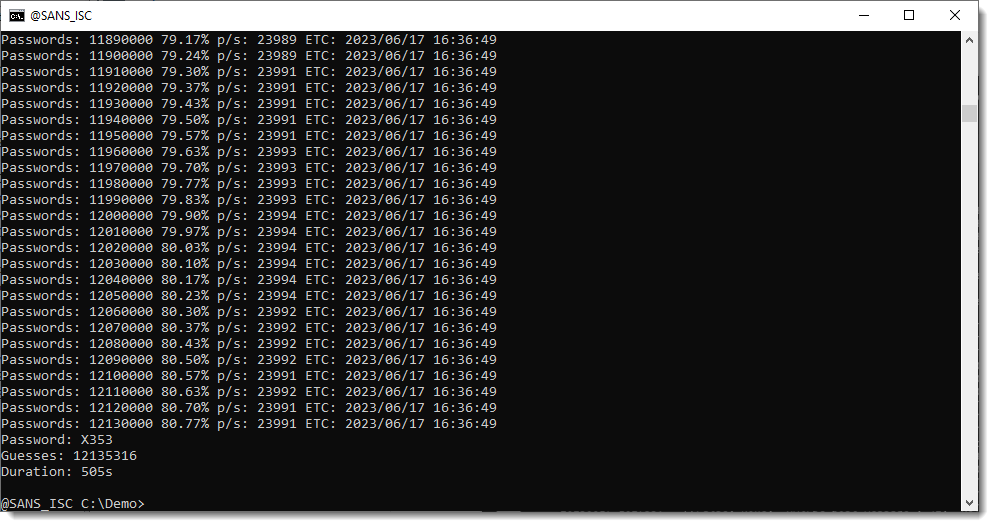
With these parameters, it took 505 seconds to recover the password: X353.
ZIP files that are encrypted with AES (like the samples you get from Malware Bazaar) requier installation of the pyzipper module and are way slower to crack (less than 2.000 password guesses per second on the same laptop).
Remark that this solution only handles ZIP files, and not all archive types like Gebhard's shell script.
zipdump can also generated false positives. ZIP files that can be openened with a guessed password through the zipfile/pyzipper API, may still throw an error when the full content is actually read:
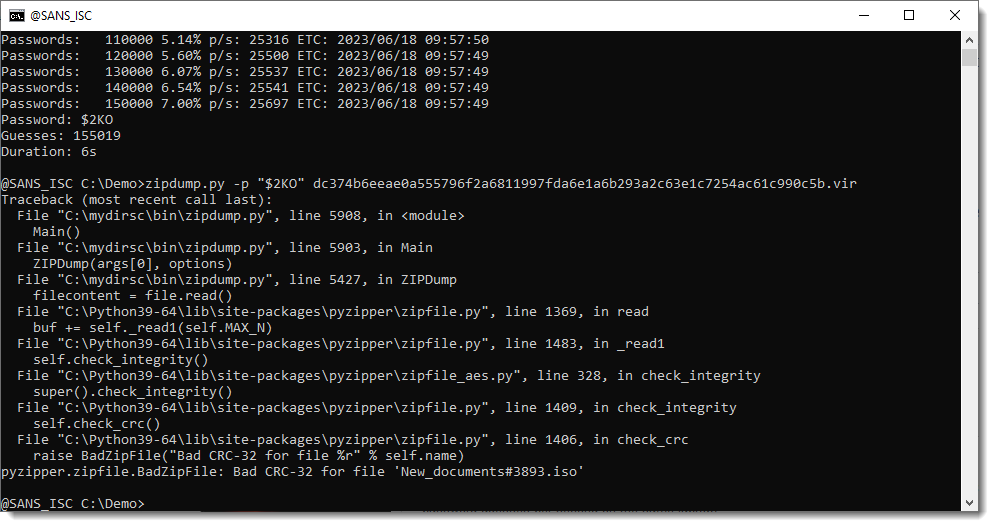
This is something I will fix in an upcoming version.
This dictionary and brute-force password cracking is just a convenience feature for me, to crack simple or popular passwords. For more complex passwords, I use hashcat.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com


Comments