A Tale of Two Phishies
Introduction
Has anyone read A Tale of Two Cities, the 1859 novel by Charles Dickens? Or maybe seen one of the movie adaptations of it? It's set during the French Revolution, including the Reign of Terror, where revolutionary leaders used violence as an instrument of the government.
In the previous sentence, substitute "violence" with "email." Then substitute "government" with "criminals." Now what do you have? Email being used as an instrument of the criminals!
I know, I know... No real ties to Dickens' novel here. A pun for the title is, quite literarily, the best I could do.

Shown above: That's all I got--a somewhat clever title for this diary.
This diary briefly investigates two phishing emails. It's a "Tale of Two Phishies" I ran across on Monday 2017-06-26.
First example: an unsophisticated phish
The first example went to my blog's admin email address. It came from the mail server of an educational institution in Paraguay, possibly used as a relay from an IP address in South Africa. For email headers, you can only rely on the "Received:" header right before the message hits your mail server. Anything before that can be spoofed.
It's a pretty poor attempt, because this phishing message is very generic. I'm educated enough to realize this didn't come from my email provider. And the login page was obviously fake. Unfortunately, some people might actually be fooled by this.
The compromised website hosting a fake login page was quickly taken off line. You won't be able to replicate the traffic by the time you read this. It's already been submitted to PhishTank.
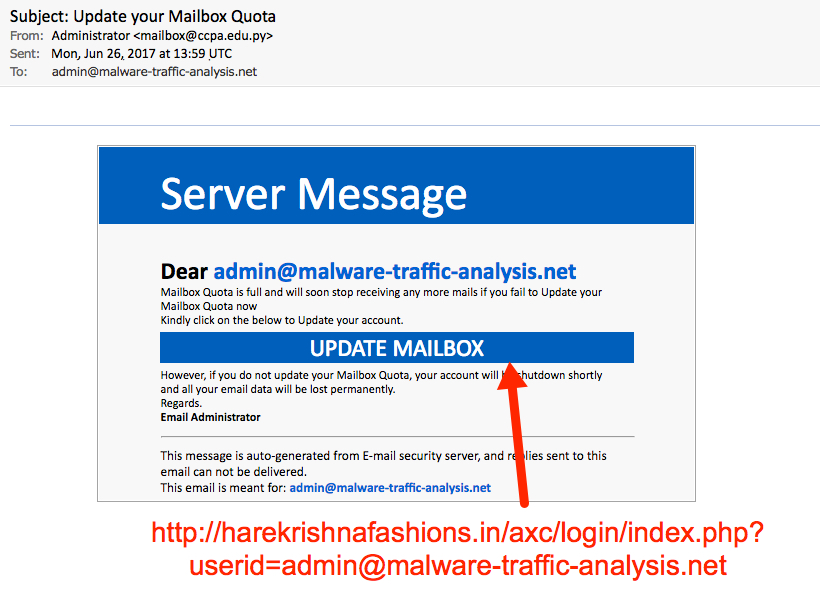
Shown above: The first phishing email.
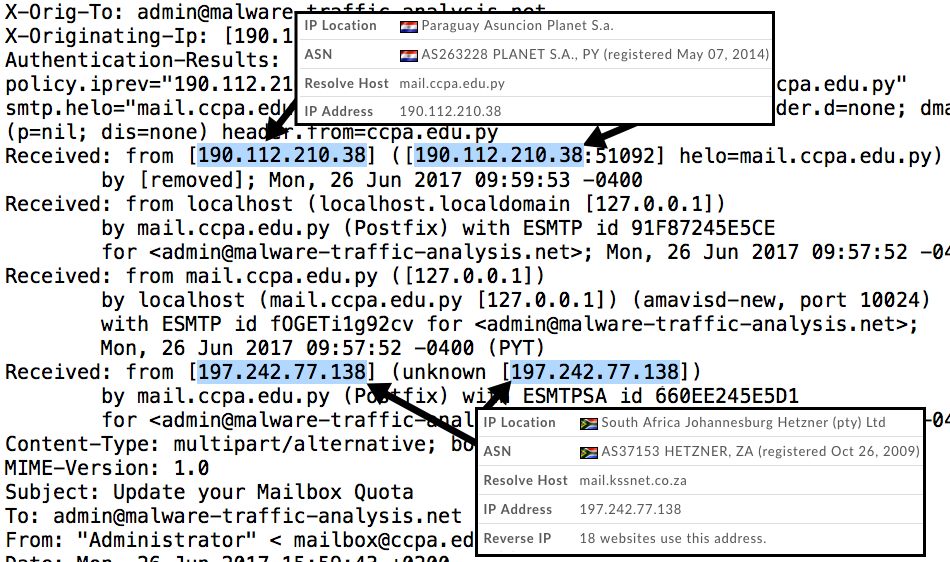
Shown above: Email headers from the first phishing email.
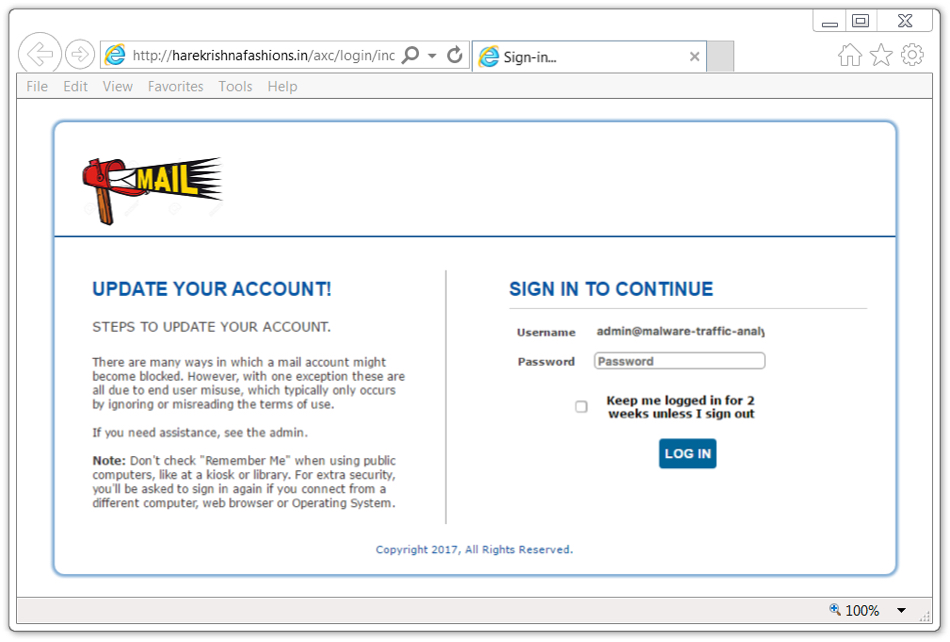
Shown above: The fake login page from link in the phishing email.
Second example: a slightly more complex phish
Every time I see a phishing message like this second example, I hope there's malware involved. But in this case, the email has a PDF attachment with a link to a fake Adobe login page.
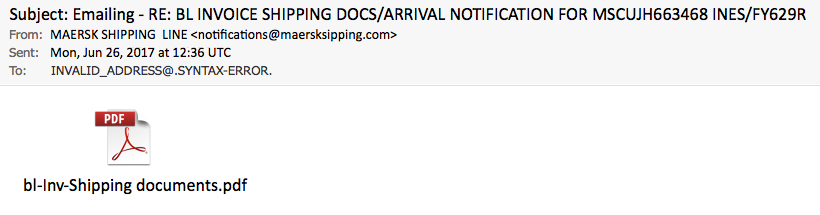
Shown above: The second phishing email.
Examining the PDF attachment, I quickly realized the criminals had made a mistake. They forgot to put .com at the end of the domain name in the URL from the PDF file. lillyforklifts should be lillyforklifts.com. I'd checked the URL early Monday morning with .com at the end of the domain name, and it worked. When I later checked again for this diary, it had already been taken down.
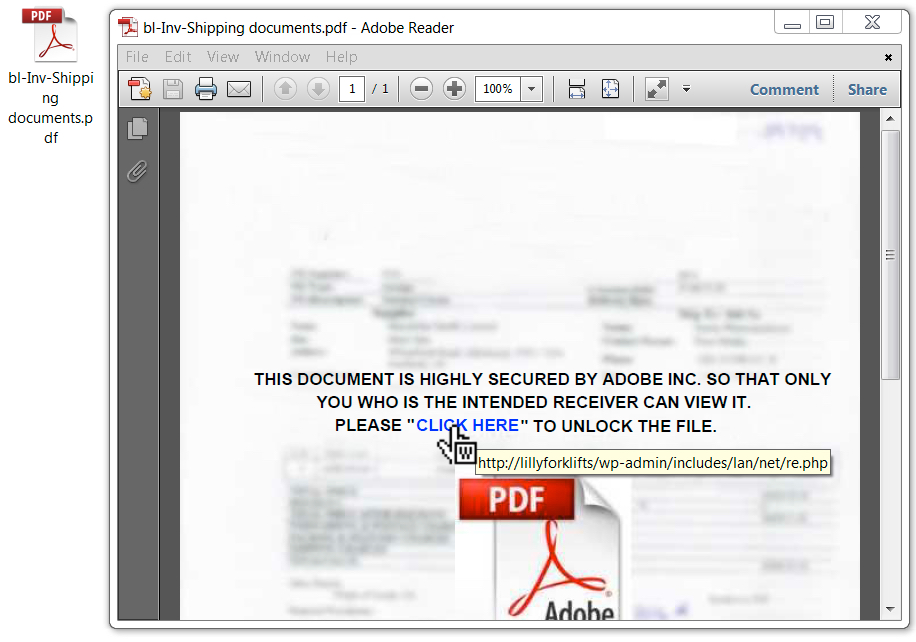
Shown above: PDF attachment from the second phishing email.
An elephant in the room
These types of phishes are what I call an "elephant in the room." That's an English-language metaphor. "Elephant in the room" represents an obvious issue that no one discusses or challenges. These types of phishing emails are very much an elephant in the room for a lot of security professionals. Why? Because we see far more serious issues during day-to-day operations in our networks. Many people (including me) feel we have better things to worry about.
But these types of phishing emails are constantly sent. They represent an on-going threat, however small they might be in comparison to other issues.
Messages with fake login pages for Netflix, Apple, email accounts, banks, and other organizations occur on a daily basis. For example, on Phishtank.com, the stats page indicates an average of 1,000 to 1,500 unique URLs were submitted on a daily basis during the past month. Stats for specific months show 58,556 unique URLs submitted in May 2017 alone.
Fortunately, various individuals on Twitter occasionally tweet about the fake login pages they find. Of course, many people also notify sites like PhishTank, scumware.org, and many other resources to fight this never-ending battle.
So today, it's open discussion on these phishing emails. Do you know anyone that's been fooled by these messages? Are there any good resources covering these phishing emails I forgot to mention? If so, please share your stories or information in the comments section below.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments
Just look at the fake sweepstakes "You might have won millions...." via paper mail that is still getting enough people to fall for it to be economically viable.
Via email the costs are even significantly lower, so phishing (and spam) will continue to exist as long as they are economically viable to exploit human weaknesses.
Anonymous
Jun 27th 2017
8 years ago
https://cdn2.hubspot.net/hubfs/241394/Knowbe4-May2015-PDF/SocialEngineeringRedFlags.pdf?
Of course it doesn't cover all situations, but I think it provides some helpful information. Knowbe4 also has phishing tests that you can send out to your users; if they click the link it displays the original email with highlighted comments as to why it should've been suspect.
Anonymous
Jun 27th 2017
8 years ago
Anonymous
Jun 27th 2017
8 years ago
How about:
Give a man a phish, he'll be in trouble for a day.
Teach him how to phish, he'll be in trouble for a lifetime.
Anonymous
Jun 28th 2017
8 years ago
The consequences can indeed be significant. In this case, the individual was a senior thought-leader in his field working for a global organization. Fortunately the criminals who got his creds just used his account to send more generic phishing messages to random people. If they'd mined his email box and address list for contacts and sent targeted messages tailored to be "from" him, the consequences to the organization could have been very serious.
Anonymous
Jun 28th 2017
8 years ago
Anonymous
Jun 28th 2017
8 years ago