SSH Tunneling in Action: direct-tcp requests [Guest Diary]
[This is a Guest Diary by Sihui Neo, an ISC intern as part of the SANS.edu BACS program]
As part of the SANS degree program curriculum, I had the opportunity to set up a honeypot to monitor log activities mimicking a vulnerable server. I used the AWS free tier EC2 instance to set up the honeypot sensor in Japan and deployed Cowrie, a SSH and Telnet honeypot designed to log brute force attacks and shell interaction performed by an attacker.
In addition to the sensor setup, to allow me to easily look at all the logs in a single platform, I purchased a separate virtual private server and installed ELK SIEM, following the setup instructions from ISC mentor, Guy Bruneau’s github page.[1] Then setup the sensor to send all logs to the SIEM server.
Since the setup of the honeypot, one of the interesting observations in logs was direct-tcp connection requests. More than 1000 different IPs within a month were seen to have made these requests and more than 75% were made to a single destination IP. In this post, I’ll cover how and why these connections are set up, and where the destination IP points to.
What did the logs look like?
Sample of direct-tcp connection request seen in honeypot logs

The sample log on the original event field seen above indicates that the request originated from 127.0.0.1 (the local loopback interface), but when looking at the source.ip in kibana, the actual source IPs were different external addresses.

125.20.251.66 was the actual source IP
Using the source IP 125.20.251.66, I took a look at the traffic before the direct-tcp connection and the PCAP traffic.

Figure 1. Logs from 125.20.251.66 at the time of the direct-tcp connection request showing source port of 32069 in a red box
In Figure 1, I extracted the logs for traffic from source IP 125.20.251.66 as seen in kibana. The line direct-tcp connection request to 77.88.21.158:25 from 127.0.0.1:32069 is highlighted in the red box, yet the source address shows 125.20.251.66 while the source port matches 32069.
Additional evidence is in the PCAP. The entire stream below showed the connection using the source port of 42948, which was indeed the source port for the initial SSH connection as seen in the Figure 1 above, highlighted in a blue box, source IP seen in the last column.

Figure 2. PCAP and TCP stream for traffic from 125.20.251.66
Lastly, the SSH banner SSH-2.0-OpenSSH_7.4 was seen in Figure 1, highlighted in green as well as in the TCP Stream at the bottom of Figure 2. All these suggested that the traffic was being forwarded or proxied to help obscure the real source IP.
So how does it work?


Reconnaissance and Initial access
As explained before, the attacker has to initiate a connection to the honeypot server to create a SSH tunnel and to do that, they require valid SSH login credentials. This is usually fulfilled by brute forcing. When looking at initial activities of IPs that had direct-tcp connection requests, they had a similar pattern of :
- Only attempting to connect to port 2222
- Throttled brute forcing attempts, meaning brute forcing attempts from the same IP were spaced out at least 2 hours if it failed.
- TTL of less than 50, means starting TTL is likely 64, which could be indicative of Linux/MAX OSX systems [3]
- SSH client hash fingerprint: acaa53e0a7d7ac7d1255103f37901306
After successfully obtaining valid SSH credentials, the SSH tunnel would usually be set up within the second.
Going somewhere?
As mentioned before, more than 1000 IPs were seen to have made these proxy connections in the honeypot and interestingly, the majority, more than 75%, were seen to be proxying to the destination IP of 77.88.21.158 at port 25.

77.88.21.158 port 25 seems to be the smtp server for yandex mail, based in Russia [4] which is a common blocked location for many countries.

Referencing the SSH tunnel diagram shown earlier, this likely means that the client set their email client to use ‘127.0.0.1:1080’ as the proxy, which instructed the email traffic to go through the established SSH tunnel to reach 77.88.21.158.
As the honeypot server does not really have SSH service on port 2222, the connection is closed quickly after the tunnel is set up and the PCAP logs do not capture outbound traffic to the destination IPs.
What’s the worst that could happen?
Direct-tcp connections are usually a form of proxy connection that uses the honeypot server in this case, as an intermidiary to either mask origin IPs or to bypass traffic rules. The reason attackers use compromised servers instead of paid or free VPN is attribution and/or possibly consistency. Commercial VPN requires sign up and services like peer-to-peer networks do not usually allow users to choose the route or hops.
Establishing a SSH tunnel does not require root and can easily be set up as long as you have a valid user’s credentials to login to the SSH server (honeypot, in this case). In fact, brute forcing is one of the more common and easy tactics to gain access to vulnerable servers due to password leaks, reusing of passwords and default passwords.
Once your server is compromised and successfully used as a proxy, your server may be susceptible to:
- Malicious Traffic Attribution: Actors can route illegal activities (hacking, fraud, DDoS) through your server, making you appear responsible.
- Bandwidth Overuse: Proxy traffic consumes resources, which can lead to throttling by your host/ISP and extra costs especially in the cloud.
- IP Blacklisting: Your server’s IP may end up on firewall blacklists preventing you from your daily activities
[1] https://github.com/bruneaug/DShield-SIEM
[2] https://ma.ttias.be/socks-proxy-linux-ssh-bypass-content-filters/
[3] https://www.imperva.com/learn/performance/time-to-live-ttl/
[4] https://search.censys.io/hosts/77.88.21.158
[5] https://www.sans.edu/cyber-security-programs/bachelors-degree/
-----------
Guy Bruneau IPSS Inc.
My GitHub Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
Setting up Your Own Certificate Authority for Development: Why and How.
There are several reasons why one would set up an internal certificate authority. Some are configured to support strong authentication schemes, some for additional flexibility and convenience. I am going to cover the second part. In particular, it can be helpful for developers to have an internal certificate authority to issue certificates for development purposes. Websites used for development and internal testing are usually only used by a few individuals and are generally only accessible via internal networks or VPNs. Often, these sites do not even use TLS. But there are a few reasons why you should consider running TLS on all sites, including internal development sites:
- Browser preferences: Browsers are increasingly "forcing" TLS. Running a site without TLS can be inconvenient. In particular, if you use features like strict transport security, setting up exceptions for development sites (in particular APIs) can be messy.
- Configuration Consistency: Keeping your development environment as close to "the real thing" as possible is best. The fewer changes you make, the less likely something will break. Some advanced JavaScript features (for example, geo-location) may not even work without TLS.
- Security: Even in a more isolated development environment, TLS still provides developers an important safeguard to not expose themselves to additional risk. Even if you manage only to use test data, attackers could still use insecure development sites to inject code to pivot into developers' machines.
The obvious, simple solution would be just using a free service like Let's Encrypt to request developer certificates. But there are a few reasons why you probably do not want to do this:
- Certificate Request Authentication: Development sites should not be exposed publicly, and the simple HTTP authentication for a website will likely not work. Alternatively, you could use DNS-based authentication schemes, but that would require providing developers with access to modify DNS settings. This can be done safely, but it takes a lot of work to get it right. Do not forget that Let's Encrypt also implements rate limits that may be exceeded if you request too many certificates.
- Certificate Transparency: Public certificate authorities must publish all certificates they issue in certificate transparency logs. An attacker can use them to easily discover development systems if you use a public certificate authority to request certificates.
- Flexibility: Your internal certificate authority does not have to comply with the same rules that public certificate authorities have to obey. Your certificates can be valid longer (or shorter), they can use internal domain names or even IP addresses. This is useful for development sites.
The next step is "how". How do you set up an easy-to-use certificate authority? OpenSSL documents the hard way. You create a certificate authority, and next, you use various scripts to create individual certificates. This works, but gets old quickly. There is a better way to set up a certificate authority that supports the "ACME" protocol to issue certificates. This is easier to manage centrally, and you will have more visibility into the issued certificates.
The easiest and cheapest way to get started is the open-source solution offered by Smallstep. Smallstep also provides several commercial solutions if you prefer support and additional integration features. As an added "bonus", it can also be used to manage SSH certificates.
The Smallstep instructions are good. One issue I ran into is that you need to initialize your CA before setting Smallstep up to run as a daemon. So follow the instructions in this order:
- Install: https://smallstep.com/docs/step-ca/installation/ (I used Ubuntu 24.04 in a minimal-sized container on Proxmox)
- Install jq if it is not already installed.
- Initialize: https://smallstep.com/docs/step-ca/getting-started/
- Run as a daemon: https://smallstep.com/docs/step-ca/certificate-authority-server-production/index.html#running-step-ca-as-a-daemon
Once it is all set up, all you need to do is
1 - Add the new certificate authority as a trusted CA to your browser (and or operating system)
2 - The first time you use "certbot" to request a certificate, add the following argument: --server https://yourinternalca/acme/acme/directory
You should be able to use various validation schemes with smallstep. Please ensure the server smallstep is running and can resolve any hostnames you may use, but adding them to a host file will work.
Note that CAs you add manually do not have to obey the same rules as public certificate authorities. Certificates may be valid for longer; you may issue certificates for IP addresses, and you do not need to configure revocation or certificate transparency.
---
Johannes B. Ullrich, Ph.D. Dean of Research, SANS.edu
Twitter|
0 Comments
Microsoft Patch Tuesday, July 2025
Today, Microsoft released patches for 130 Microsoft vulnerabilities and 9 additional vulnerabilities not part of Microsoft's portfolio but distributed by Microsoft. 14 of these are rated critical. Only one of the vulnerabilities was disclosed before being patched, and none of the vulnerabilities have so far been exploited.
Noteworthy Vulnerabilities:
CVE-2025-49695 and CVE-2025-49696: Both vulnerabilities affect Microsoft Office, are rated critical, and are considered "more likely" to be exploited by Microsoft. These issues do not require user interaction, so the user does not need to open a document. The exploit could be triggered via the preview pane. Macs are affected as well, but a patch is currently only available for Windows.
CVE-2025-49719: This vulnerability has already been made public. It does allow for information disclosure on a Microsoft SQL Server. To patch, you must patch the OLE DB Driver.
CVE-2025-49717: Exploitation is considered less likely for this vulnerability. But if exploited, it would allow code execution via a Microsoft SQL Server. Take this as additional motivation not to expose SQL servers.
CVE-2025-49704: I consider this vulnerability interesting as it appears to allow command/code injection in SharePoint. However, an attacker has to be authenticated to take advantage of this vulnerability.
| Description | |||||||
|---|---|---|---|---|---|---|---|
| CVE | Disclosed | Exploited | Exploitability (old versions) | current version | Severity | CVSS Base (AVG) | CVSS Temporal (AVG) |
| AMD: CVE-2024-36350 Transient Scheduler Attack in Store Queue | |||||||
| %%cve:2025-36350%% | No | No | - | Less Likely | Critical | 5.6 | 4.9 |
| AMD: CVE-2025-36357 Transient Scheduler Attack in L1 Data Queue | |||||||
| %%cve:2025-36357%% | No | No | - | Less Likely | Critical | 5.6 | 4.9 |
| Azure Monitor Agent Remote Code Execution Vulnerability | |||||||
| %%cve:2025-47988%% | No | No | - | Less Likely | Important | 7.5 | 6.5 |
| Azure Service Fabric Runtime Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-21195%% | No | No | - | Less Likely | Important | 6.0 | 5.2 |
| BitLocker Security Feature Bypass Vulnerability | |||||||
| %%cve:2025-48001%% | No | No | - | More Likely | Important | 6.8 | 5.9 |
| %%cve:2025-48003%% | No | No | - | Less Likely | Important | 6.8 | 5.9 |
| %%cve:2025-48800%% | No | No | - | More Likely | Important | 6.8 | 5.9 |
| %%cve:2025-48818%% | No | No | - | More Likely | Important | 6.8 | 5.9 |
| %%cve:2025-48804%% | No | No | - | More Likely | Important | 6.8 | 5.9 |
| Capability Access Management Service (camsvc) Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-49690%% | No | No | - | Less Likely | Important | 7.4 | 6.4 |
| Credential Security Support Provider Protocol (CredSSP) Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-47987%% | No | No | - | More Likely | Important | 7.8 | 6.8 |
| HID Class Driver Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-48816%% | No | No | - | Unlikely | Important | 7.8 | 6.8 |
| Kernel Streaming WOW Thunk Service Driver Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-49675%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| MITRE: CVE-2025-27613 Gitk Arguments Vulnerability | |||||||
| %%cve:2025-27613%% | No | No | - | - | - | ||
| MITRE: CVE-2025-27614 Gitk Arbitrary Code Execution Vulnerability | |||||||
| %%cve:2025-27614%% | No | No | - | - | - | ||
| MITRE: CVE-2025-46334 Git Malicious Shell Vulnerability | |||||||
| %%cve:2025-46334%% | No | No | - | - | - | ||
| MITRE: CVE-2025-46835 Git File Overwrite Vulnerability | |||||||
| %%cve:2025-46835%% | No | No | - | - | - | ||
| MITRE: CVE-2025-48384 Git Symlink Vulnerability | |||||||
| %%cve:2025-48384%% | No | No | - | - | - | ||
| MITRE: CVE-2025-48385 Git Protocol Injection Vulnerability | |||||||
| %%cve:2025-48385%% | No | No | - | - | - | ||
| MITRE: CVE-2025-48386 Git Credential Helper Vulnerability | |||||||
| %%cve:2025-48386%% | No | No | - | - | - | ||
| Microsoft Brokering File System Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-49677%% | No | No | - | Less Likely | Important | 7.0 | 6.1 |
| %%cve:2025-49694%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2025-49693%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| Microsoft Configuration Manager Remote Code Execution Vulnerability | |||||||
| %%cve:2025-47178%% | No | No | - | Unlikely | Important | 8.0 | 7.0 |
| Microsoft Edge (Chromium-based) Information Disclosure Vulnerability | |||||||
| %%cve:2025-49741%% | No | No | Less Likely | Less Likely | Important | 7.4 | 6.4 |
| Microsoft Edge (Chromium-based) Remote Code Execution Vulnerability | |||||||
| %%cve:2025-49713%% | No | No | - | Unlikely | Important | 8.8 | 7.7 |
| Microsoft Excel Information Disclosure Vulnerability | |||||||
| %%cve:2025-48812%% | No | No | - | Unlikely | Important | 5.5 | 4.8 |
| Microsoft Excel Remote Code Execution Vulnerability | |||||||
| %%cve:2025-49711%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| Microsoft MPEG-2 Video Extension Remote Code Execution Vulnerability | |||||||
| %%cve:2025-48805%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2025-48806%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| Microsoft Office Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-47994%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| Microsoft Office Remote Code Execution Vulnerability | |||||||
| %%cve:2025-49695%% | No | No | - | More Likely | Critical | 8.4 | 7.3 |
| %%cve:2025-49696%% | No | No | - | More Likely | Critical | 8.4 | 7.3 |
| %%cve:2025-49697%% | No | No | - | Less Likely | Critical | 8.4 | 7.3 |
| %%cve:2025-49699%% | No | No | - | Less Likely | Important | 7.0 | 6.1 |
| %%cve:2025-49702%% | No | No | - | Less Likely | Critical | 7.8 | 6.8 |
| Microsoft PC Manager Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-47993%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2025-49738%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| Microsoft PowerPoint Remote Code Execution Vulnerability | |||||||
| %%cve:2025-49705%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| Microsoft SQL Server Information Disclosure Vulnerability | |||||||
| %%cve:2025-49719%% | Yes | No | - | Less Likely | Important | 7.5 | 6.5 |
| %%cve:2025-49718%% | No | No | - | More Likely | Important | 7.5 | 6.5 |
| Microsoft SQL Server Remote Code Execution Vulnerability | |||||||
| %%cve:2025-49717%% | No | No | - | Unlikely | Critical | 8.5 | 7.4 |
| Microsoft SharePoint Remote Code Execution Vulnerability | |||||||
| %%cve:2025-49701%% | No | No | - | More Likely | Important | 8.8 | 7.7 |
| %%cve:2025-49704%% | No | No | - | More Likely | Critical | 8.8 | 7.7 |
| Microsoft SharePoint Server Spoofing Vulnerability | |||||||
| %%cve:2025-49706%% | No | No | - | Less Likely | Important | 6.3 | 5.5 |
| Microsoft Teams Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-49731%% | No | No | - | Less Likely | Important | 3.1 | 2.7 |
| %%cve:2025-49737%% | No | No | - | Less Likely | Important | 7.0 | 6.1 |
| Microsoft Virtual Hard Disk Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-47971%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2025-49689%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2025-47973%% | No | No | - | Unlikely | Important | 7.8 | 6.8 |
| Microsoft Virtual Hard Disk Remote Code Execution Vulnerability | |||||||
| %%cve:2025-49683%% | No | No | - | Unlikely | Important | 7.8 | 6.8 |
| Microsoft Windows QoS Scheduler Driver Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-49730%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| Microsoft Word Remote Code Execution Vulnerability | |||||||
| %%cve:2025-49700%% | No | No | - | Unlikely | Important | 7.8 | 6.8 |
| %%cve:2025-49703%% | No | No | - | Less Likely | Critical | 7.8 | 6.8 |
| %%cve:2025-49698%% | No | No | - | Less Likely | Critical | 7.8 | 6.8 |
| NTFS Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-49678%% | No | No | - | Unlikely | Important | 7.0 | 6.1 |
| Office Developer Platform Security Feature Bypass Vulnerability | |||||||
| %%cve:2025-49756%% | No | No | - | Less Likely | Important | 3.3 | 2.9 |
| Remote Desktop Client Remote Code Execution Vulnerability | |||||||
| %%cve:2025-48817%% | No | No | - | Less Likely | Important | 8.8 | 7.7 |
| Remote Desktop Licensing Service Security Feature Bypass Vulnerability | |||||||
| %%cve:2025-48814%% | No | No | - | Less Likely | Important | 7.5 | 6.5 |
| Remote Desktop Spoofing Vulnerability | |||||||
| %%cve:2025-33054%% | No | No | - | Less Likely | Important | 8.1 | 7.1 |
| SPNEGO Extended Negotiation (NEGOEX) Security Mechanism Remote Code Execution Vulnerability | |||||||
| %%cve:2025-47981%% | No | No | - | More Likely | Critical | 9.8 | 8.5 |
| Universal Print Management Service Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-47986%% | No | No | - | Unlikely | Important | 8.8 | 7.7 |
| Visual Studio Code Python Extension Remote Code Execution Vulnerability | |||||||
| %%cve:2025-49714%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| Visual Studio Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-49739%% | No | No | - | Less Likely | Important | 8.8 | 7.7 |
| Win32k Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-49727%% | No | No | - | More Likely | Important | 7.0 | 6.1 |
| %%cve:2025-49733%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-49661%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| Windows AppX Deployment Service Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-48820%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| Windows Connected Devices Platform Service Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-48000%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| Windows Connected Devices Platform Service Remote Code Execution Vulnerability | |||||||
| %%cve:2025-49724%% | No | No | - | More Likely | Important | 8.8 | 7.7 |
| Windows Cryptographic Services Information Disclosure Vulnerability | |||||||
| %%cve:2025-48823%% | No | No | - | Less Likely | Important | 5.9 | 5.2 |
| Windows Event Tracing Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-47985%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2025-49660%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| Windows Fast FAT File System Driver Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-49721%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| Windows GDI Information Disclosure Vulnerability | |||||||
| %%cve:2025-47984%% | No | No | - | Less Likely | Important | 7.5 | 6.5 |
| Windows Graphics Component Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-49732%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2025-49744%% | No | No | - | More Likely | Important | 7.0 | 6.1 |
| Windows Graphics Component Remote Code Execution Vulnerability | |||||||
| %%cve:2025-49742%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| Windows Hyper-V Denial of Service Vulnerability | |||||||
| %%cve:2025-47999%% | No | No | - | Less Likely | Important | 6.8 | 5.9 |
| Windows Hyper-V Discrete Device Assignment (DDA) Remote Code Execution Vulnerability | |||||||
| %%cve:2025-48822%% | No | No | - | Less Likely | Critical | 8.6 | 7.5 |
| Windows Hyper-V Information Disclosure Vulnerability | |||||||
| %%cve:2025-48002%% | No | No | - | Less Likely | Important | 5.7 | 5.0 |
| Windows Imaging Component Information Disclosure Vulnerability | |||||||
| %%cve:2025-47980%% | No | No | - | Less Likely | Critical | 6.2 | 5.4 |
| Windows Input Method Editor (IME) Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-47972%% | No | No | - | Unlikely | Important | 8.0 | 7.0 |
| %%cve:2025-49687%% | No | No | - | Less Likely | Important | 8.8 | 7.7 |
| %%cve:2025-47991%% | No | No | - | Unlikely | Important | 7.8 | 6.8 |
| Windows KDC Proxy Service (KPSSVC) Remote Code Execution Vulnerability | |||||||
| %%cve:2025-49735%% | No | No | - | More Likely | Critical | 8.1 | 7.1 |
| Windows Kerberos Denial of Service Vulnerability | |||||||
| %%cve:2025-47978%% | No | No | - | More Likely | Important | 6.5 | 5.7 |
| Windows Kernel Information Disclosure Vulnerability | |||||||
| %%cve:2025-26636%% | No | No | - | Less Likely | Important | 5.5 | 4.8 |
| %%cve:2025-48808%% | No | No | - | Unlikely | Important | 5.5 | 4.8 |
| Windows MBT Transport Driver Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-47996%% | No | No | - | Unlikely | Important | 7.8 | 6.8 |
| Windows Media Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-49682%% | No | No | - | Less Likely | Important | 7.3 | 6.4 |
| Windows Miracast Wireless Display Remote Code Execution Vulnerability | |||||||
| %%cve:2025-49691%% | No | No | - | Less Likely | Important | 8.0 | 7.0 |
| Windows Netlogon Denial of Service Vulnerability | |||||||
| %%cve:2025-49716%% | No | No | - | Unlikely | Important | 5.9 | 5.2 |
| Windows Notification Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-49726%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2025-49725%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| Windows Performance Recorder (WPR) Denial of Service Vulnerability | |||||||
| %%cve:2025-49680%% | No | No | - | Less Likely | Important | 7.3 | 6.4 |
| Windows Print Spooler Denial of Service Vulnerability | |||||||
| %%cve:2025-49722%% | No | No | - | Less Likely | Important | 5.7 | 5.0 |
| Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | |||||||
| %%cve:2025-49671%% | No | No | - | Unlikely | Important | 6.5 | 5.7 |
| %%cve:2025-49681%% | No | No | - | Unlikely | Important | 6.5 | 5.7 |
| Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | |||||||
| %%cve:2025-48824%% | No | No | - | Unlikely | Important | 8.8 | 7.7 |
| %%cve:2025-49657%% | No | No | - | Unlikely | Important | 8.8 | 7.7 |
| %%cve:2025-49670%% | No | No | - | Unlikely | Important | 8.8 | 7.7 |
| %%cve:2025-49672%% | No | No | - | Unlikely | Important | 8.8 | 7.7 |
| %%cve:2025-49674%% | No | No | - | Unlikely | Important | 8.8 | 7.7 |
| %%cve:2025-49676%% | No | No | - | Unlikely | Important | 8.8 | 7.7 |
| %%cve:2025-49688%% | No | No | - | Unlikely | Important | 8.8 | 7.7 |
| %%cve:2025-49753%% | No | No | - | Unlikely | Important | 8.8 | 7.7 |
| %%cve:2025-47998%% | No | No | - | Unlikely | Important | 8.8 | 7.7 |
| %%cve:2025-49663%% | No | No | - | Unlikely | Important | 8.8 | 7.7 |
| %%cve:2025-49668%% | No | No | - | Unlikely | Important | 8.8 | 7.7 |
| %%cve:2025-49669%% | No | No | - | Unlikely | Important | 8.8 | 7.7 |
| %%cve:2025-49673%% | No | No | - | Unlikely | Important | 8.8 | 7.7 |
| %%cve:2025-49729%% | No | No | - | Unlikely | Important | 8.8 | 7.7 |
| Windows SMB Server Spoofing Vulnerability | |||||||
| %%cve:2025-48802%% | No | No | - | Less Likely | Important | 6.5 | 5.7 |
| Windows Search Service Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-49685%% | No | No | - | Less Likely | Important | 7.0 | 6.1 |
| Windows Secure Kernel Mode Information Disclosure Vulnerability | |||||||
| %%cve:2025-48809%% | No | No | - | Less Likely | Important | 5.5 | 4.8 |
| %%cve:2025-48810%% | No | No | - | Less Likely | Important | 5.5 | 4.8 |
| Windows Server Setup and Boot Event Collection Remote Code Execution Vulnerability | |||||||
| %%cve:2025-49666%% | No | No | - | Unlikely | Important | 7.2 | 6.3 |
| Windows Shell Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-49679%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| Windows Simple Search and Discovery Protocol (SSDP) Service Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-47976%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2025-47975%% | No | No | - | Less Likely | Important | 7.0 | 6.1 |
| %%cve:2025-48815%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| Windows SmartScreen Security Feature Bypass Vulnerability | |||||||
| %%cve:2025-49740%% | No | No | - | Less Likely | Important | 8.8 | 7.7 |
| Windows StateRepository API Server file Tampering Vulnerability | |||||||
| %%cve:2025-49723%% | No | No | - | Less Likely | Important | 8.8 | 7.7 |
| Windows Storage Port Driver Information Disclosure Vulnerability | |||||||
| %%cve:2025-49684%% | No | No | - | Less Likely | Important | 5.5 | 4.8 |
| Windows Storage Spoofing Vulnerability | |||||||
| %%cve:2025-49760%% | No | No | - | Less Likely | Moderate | 3.5 | 3.1 |
| Windows Storage VSP Driver Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-47982%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| Windows TCP/IP Driver Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-49686%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| Windows Transport Driver Interface (TDI) Translation Driver Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-49659%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| Windows Transport Driver Interface (TDI) Translation Driver Information Disclosure Vulnerability | |||||||
| %%cve:2025-49658%% | No | No | - | Less Likely | Important | 5.5 | 4.8 |
| Windows Universal Plug and Play (UPnP) Device Host Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-48819%% | No | No | - | Less Likely | Important | 7.1 | 6.2 |
| %%cve:2025-48821%% | No | No | - | Less Likely | Important | 7.1 | 6.2 |
| Windows Update Service Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-48799%% | No | No | - | More Likely | Important | 7.8 | 6.8 |
| Windows User-Mode Driver Framework Host Information Disclosure Vulnerability | |||||||
| %%cve:2025-49664%% | No | No | - | Less Likely | Important | 5.5 | 4.8 |
| Windows Virtualization-Based Security (VBS) Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-47159%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2025-48803%% | No | No | - | Less Likely | Important | 6.7 | 5.8 |
| Windows Virtualization-Based Security (VBS) Enclave Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-48811%% | No | No | - | Less Likely | Important | 6.7 | 5.8 |
| Windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-49667%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
| Workspace Broker Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-49665%% | No | No | - | Less Likely | Important | 7.8 | 6.8 |
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
0 Comments
What's My (File)Name?
Modern malware implements a lot of anti-debugging and anti-analysis features. Today, when a malware is spread in the wild, there are chances that it will be automatically sent into a automatic analysis pipe, and a sandbox. To analyze a sample in a sandbox, it must be "copied" into the sandbox and executed. This can happen manually or automatically. When people start the analysis of a suspicious file, they usually call it "sample.exe", "malware.exe" or "suspicious.exe". It's not always a good idea because it's can be detected by the malware and make it aware that "I'm being analyzed".
From a malware point of view, it's easy to detect this situation. Microsoft offers to Developers thousands of API calls that can be used for "malicious purposes". Let's have a look at GetModuleFileName()[1]. This API call retrieves the fully qualified path for the file that contains the specified module. The module must have been loaded by the current process. Normally, a "module" refers to a DLL but, in the Microsoft ecosystem, the main program is also a "module" (like a DLL is also a PE file but with exported functions)
If you read carefully the API description, it expects 3 parameters but the first name can be omitted (set to NULL):
"If this parameter is NULL, GetModuleFileName retrieves the path of the executable file of the current process."
Let's write a small program:
using System;
using System.Runtime.InteropServices;
class Program
{
// Invoke declaration for GetModuleFileName
[DllImport("kernel32.dll", CharSet = CharSet.Auto)]
static extern uint GetModuleFileName(IntPtr hModule, [Out] char[] lpFilename, uint nSize);
static void Main(string[] args)
{
const int maxPath = 260;
char[] buffer = new char[maxPath];
uint length = GetModuleFileName(IntPtr.Zero, buffer, (uint)buffer.Length);
// Get the exec basename
string fullPath = new string(buffer, 0, (int)length);
string exeName = System.IO.Path.GetFileName(fullPath);
// List of potential sample names
string[] allowedNames = {
"sample.exe",
"malware.exe",
"malicious.exe",
"suspicious.exe",
"test.exe",
"submitted_sample.exe",
"file.bin",
"file.exe",
"virus.exe",
"program.exe"
};
foreach (var name in allowedNames)
{
if (string.Equals(exeName, name, StringComparison.OrdinalIgnoreCase))
{
// Executable name matched, silenyly exit!
return;
}
}
Console.WriteLine($"I'm {exeName}, looks good! Let's infect this host! }}:->");
}
}
Let's compile and execute this file named "ISC_20250707.exe":
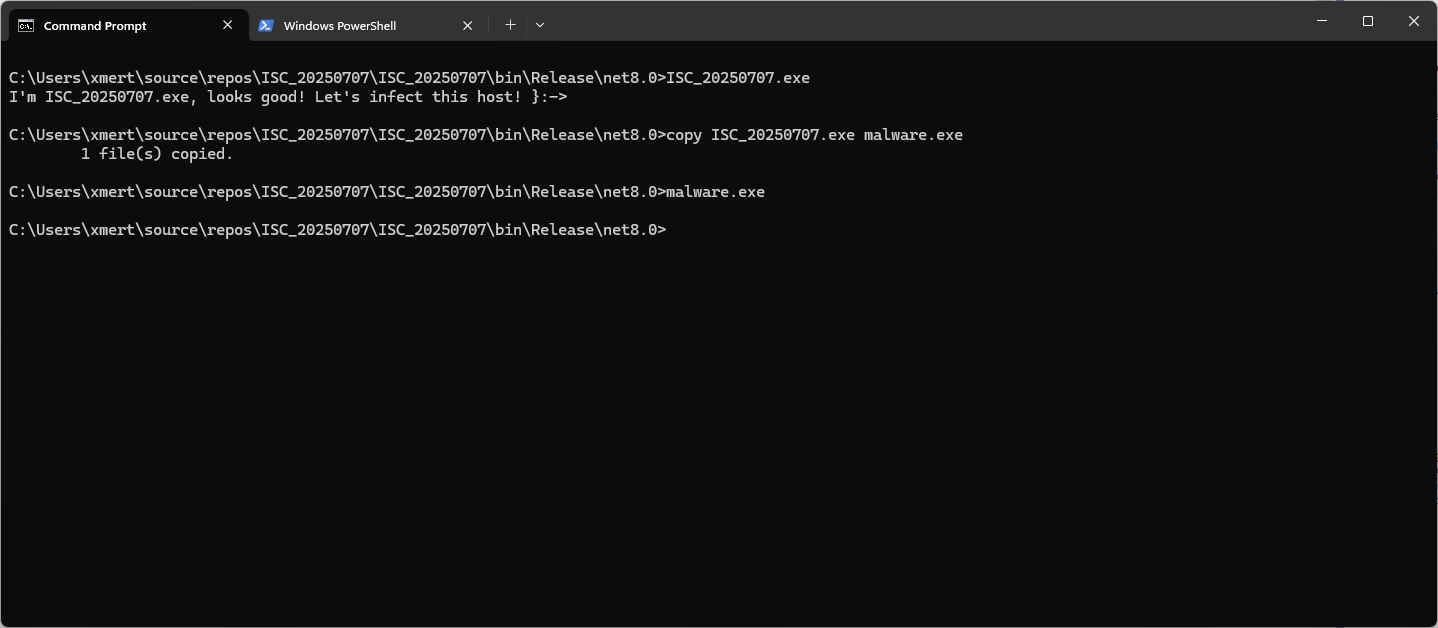
Once renamed as "malware.exe", the program will just silently exit! Simple but effective!
Of course, this is a simple proof-of-concept. In a real malware, there will be more tests implemented (ex: ignore the case) and the list of potential suspicious filenames will be obfuscated (or a dynamic list will be loaded from a 3rd-party website).
[1] https://learn.microsoft.com/en-us/windows/win32/api/libloaderapi/nf-libloaderapi-getmodulefilenamea
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
0 Comments
A few interesting and notable ssh/telnet usernames
Just looked at our telnet/ssh honeypot data, and found some interesting new usernames that attackers attempted to use:
"notachancethisisreal"
This username is likely used to detect Cowrie (and other) honeypots. Cowrie is often configured to accept logins randomly. No matter the username/password combination used, the login will succeed every few times. This is supposed to provide the illusion of a more "real" system, not just allowing some common default password, and not allowing each login to succeed. The password used with the username is "nopasswordforme73baby." Likely to pick a password that is highly unlikely to be used in a real system.
Any login that succeeds with this username and password will indicate that the system is a honeypot. So far, we have only had 31 login attempts with this username and password, all on July 1st.
"scadaadmin"
The name says it: It looks like they are looking for SCADA systems. The password used with this username is "P@$$W0rd". The password has been used "forever" and is popular, but the username is new.
The username appears to be associated with "Rapid SCADA" systems, according to some AI results, but I was not able to confirm this in the manuals. Maybe just a hallucination. However, the default password is either 12345 or blank. They are looking for users who have tried to be more secure. I am not sure how they ended up with P@$$W0rd. They also appear to use "admin" and "12345" as default credentials. It isn't a serious SCADA system if it doesn't have simple default credentials like this.
"gpu001", "gpu002"
These appear to be common hostnames for network-accessible GPUs, but I wasn't able to confirm that these are actual usernames often used for these systems. But attackers are always out for more GPU/CPU power, so they may just give this a try hoping for the best. There are a few passwords that are used with these usernames, like '7777777', 'gpu001@2025', and '1111111'.
See anything else that is new and interesting? Or have any insight into the three usernames I listed above? Let me know! (see contact link on the left).
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
0 Comments



0 Comments