Phishing Page Delivered Through a Blob URL
I receive a lot of spam in my catch-all mailboxes. If most of them are not interesting, some still attract my attention. Especially the one that I'll describe in this diary. The scenario is classic, an important document is pending delivery but... the victim needs to authenticate to get the precious! As you can see in the screenshot below, the phishing kit supports well-known service providers.
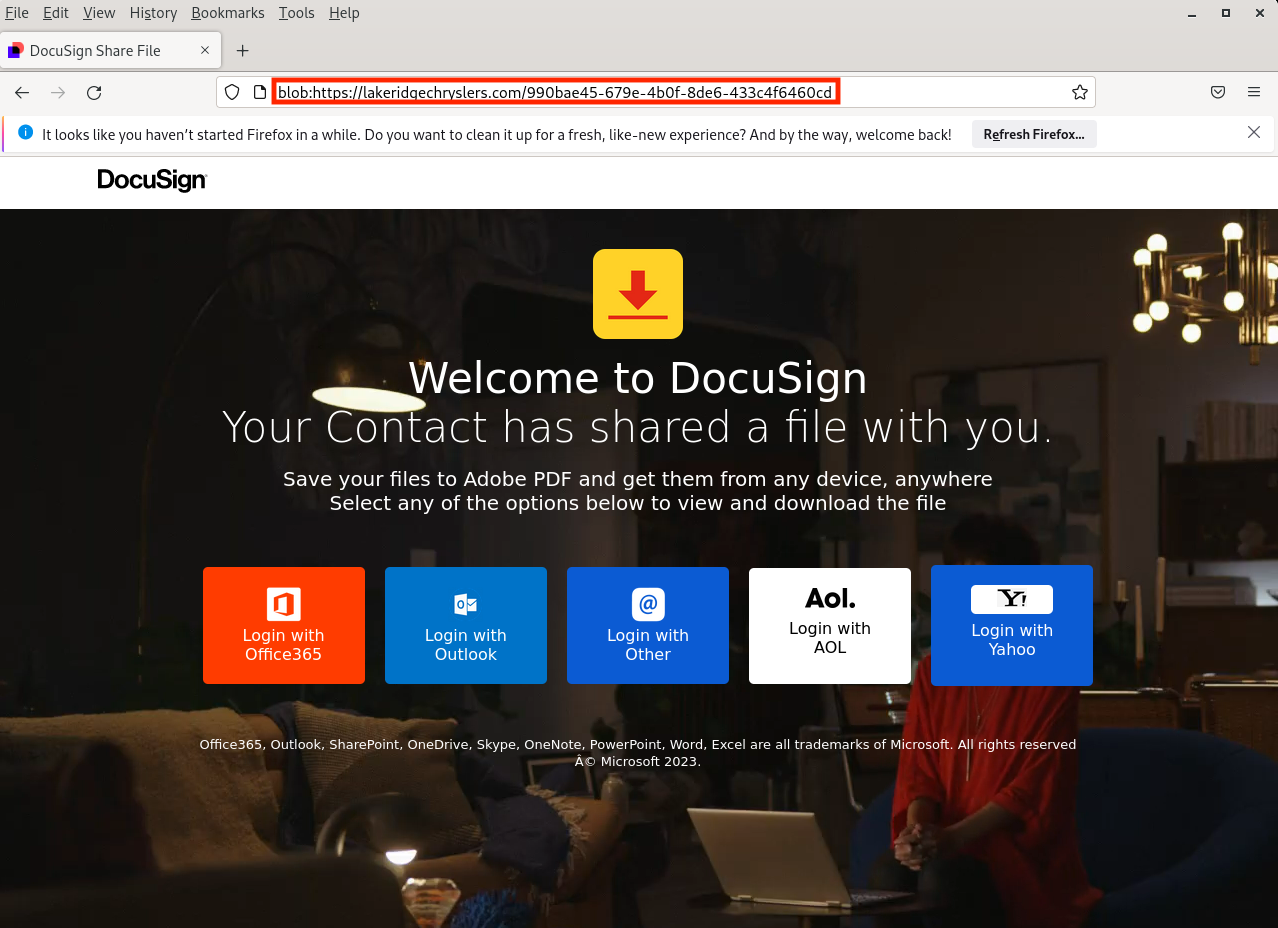
But check carefully the URL: It starts with "blob:"! Usually, BLOBs are used to represent "Binary Large OBjects". In the context of a browser, an object URL[1] is a pseudo protocol to allow blob and file objects to be used as URL sources for things like images, download links for binary data, and so forth. It's part of the URL specification for handling binary data that needs to be referenced or accessed as an actual file, even if it doesn't exist as a physical file on a server.
In the context of this phishing kit, the attacker generated the landing page in a blob to remain stealthy. Let's have a look at the code:
function saveFile(name, type, data) {
if (data != null && navigator.msSaveBlob)
return navigator.msSaveBlob(new Blob([data], { type: type }), name);
var a = $("<a style='display: none;'/>");
var encodedStringAtoB = " ... [Base64-encode-data] ... "
var decodedStringAtoB = atob(encodedStringAtoB);
const myBlob = new Blob([decodedStringAtoB], { type: 'text/html' });
const url = window.URL.createObjectURL(myBlob);
a.attr("href", url);
$("body").append(a);
a[0].click();
window.URL.revokeObjectURL(url);
a.remove();
}
In JavaScript, you create a Blob with window.URL.createObjectURL().
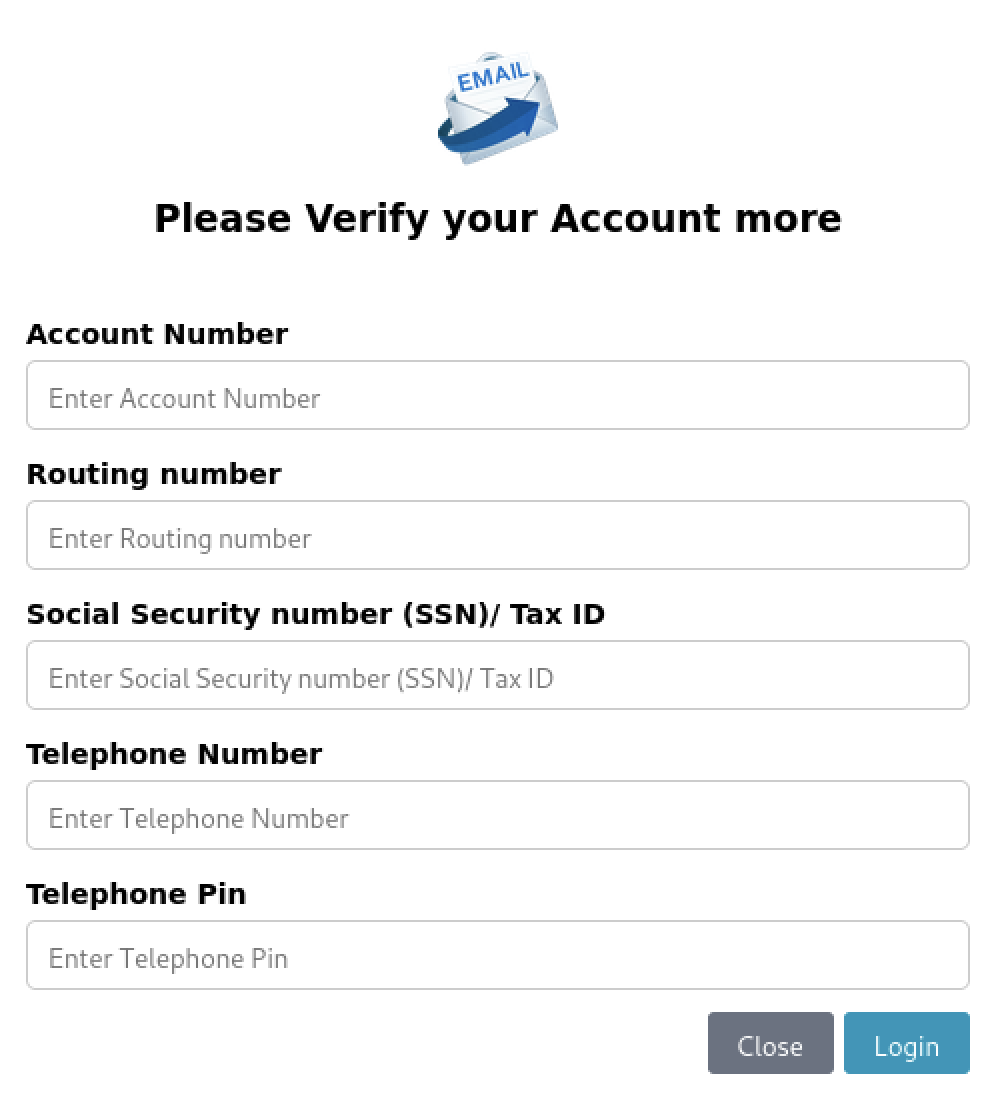
Note that if you provided "valid" credentials, the phishing kit will ask you for more personal details:
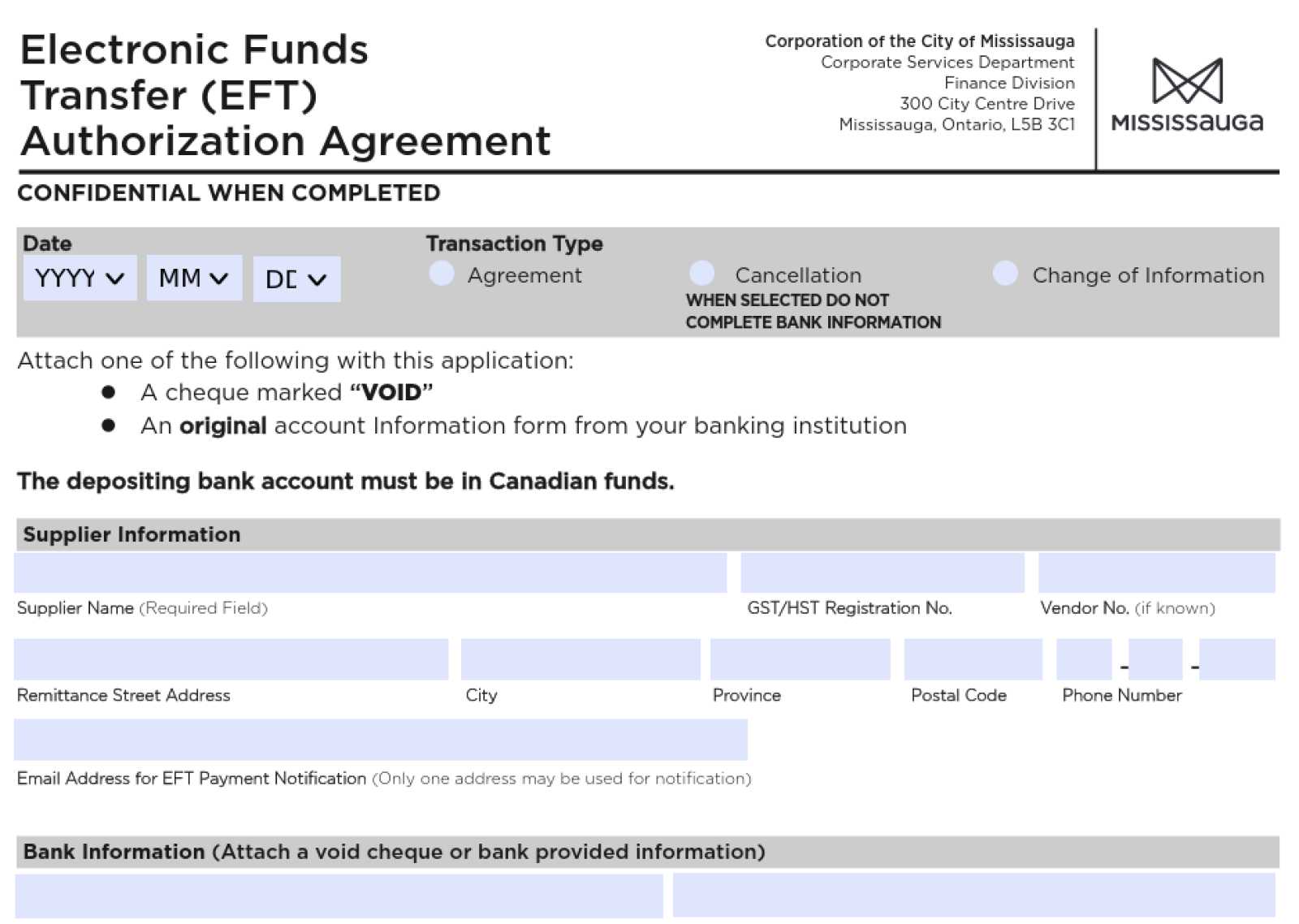
Finally, the victim will get a fake document downloaded from hxxps://www[.]Mississauga[.]ca/wp-content/uploads/2021/01/14114418/EFT-Agreement-Form.pdf:
[1] https://en.wikipedia.org/wiki/Blob_URI_scheme
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments