5Ghoul: Impacts, Implications and Next Steps
The introduction of 5G networks has brought increased quality-of-life upgrades such as increased network speeds, the ability to handle concurrent users/network congestion and improved secure communication protocols compared to 4G technology. These benefits are expected to assist sectors such as medical, automation and internet-of-things (IoT) deployments where low-latency network communication is required. Ensuring the fidelity and security of 5G is imperative as organizations and users increasingly adopt it in their lives. Today, the Automated Systems SEcuriTy (ASSET) Research Group from the Singapore University of Technology and Design (SUTD) revealed the 5Ghoul family of implementation-level vulnerabilities in commercial 5G mobile network modems from major chipset vendors such as Qualcomm and MediaTek [1]. In this diary, I will give a brief background on 5G and 5Ghoul, highlight affected products and discuss the next steps affected users/organizations could consider.
A conventional 5G connection involves three key components – the gNodeB (gNB), User Equipment (UE) and the Core Network. The gNB is also known as the base station in traditional cellular networks and serves as the access point for wireless communication between the UE and 5G core network. UE refers to devices used by end users, such as 5G smartphones, tablets or mobile routers. Finally, the Core Network is the backbone of the 5G network architecture, providing control and management functions such as authentication, security, mobility management, session establishment, and data routing between network entities. With reference to Figure 1, an illustration of a clean 5G Standalone (SA) connection process between a 5G UE device (e.g., a smartphone) and a legitimate gNB is shown. Protocols such as Radio Resource Control (RRC), Non-Access Stratum (NAS), Medium Access Control (MAC), Packet Data Convergence Protocol (PDCP) and Radio Link Control (RLC) from both network layer (OSI layer 3) and data link layer (OSI layer 2) are involved to ensure that the connection is established successfully and securely.
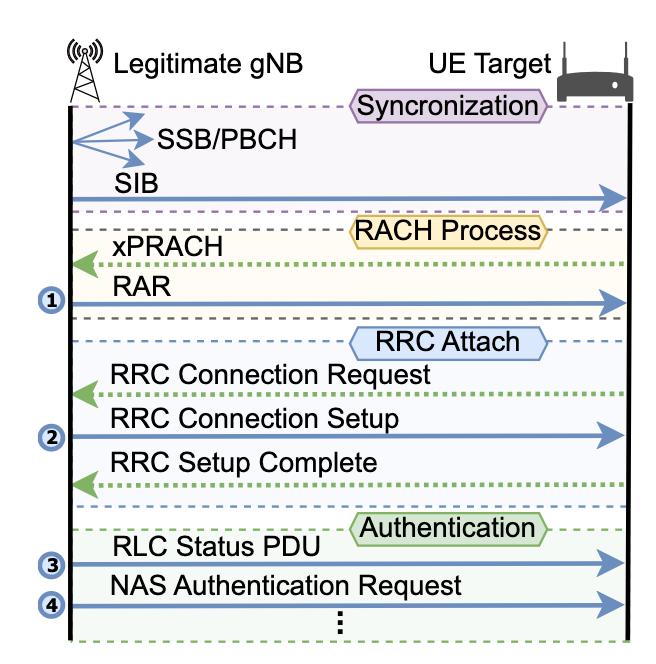
Figure 1: Illustration of 5G Standalone (SA) Connection Procedure Between Legitimate gNB and UE (figure reproduced with permission from ASSET Research Group)
The code name “5Ghoul” was coined from 5G and the word ghoul. In popular legends, a ghoul is a demon-like creature which tries to distract travellers and preys on them once it is successful [1]. Similarly, for the 5Ghoul family of vulnerabilities, UEs could be continuously exploited (e.g. dropping connections, freezing connections, which requires manual rebooting, or downgrading a 5G connection to 4G) once they are connected to the malicious 5Ghoul gNB. A total of 16 vulnerabilities were uncovered, of which 10 Common Vulnerabilities and Exposures (CVE) Identifiers (IDs) were issued, and 2 CVE IDs were pending assignment. The summary of vulnerabilities, affected devices and patch status are outlined in Table 1 below.
| Vendor/Product |
5G Modem
|
Type
|
Firmware/ |
CVE ID
|
Patch Status
|
|---|---|---|---|---|---|
|
Quectel RM500Q-GL
|
Qualcomm X55
|
USB Modem
|
Aug 03 2021
|
CVE-2023-33042 |
Not Yet Available* |
|
Simcom SIM8202G
|
Qualcomm X55
|
USB Modem
|
SIM8202G-M2_V1.2
|
CVE-2023-33042 |
Not Yet Available*
|
|
Fibocom FM150-AE
|
Qualcomm X55
|
USB Modem
|
89602.1000.00.04.07.20
|
CVE-2023-33042 |
Not Yet Available*
|
|
Telit FT980m
|
Qualcomm X55
|
USB Modem
|
38.23.001-B001-P0H.000640 |
CVE-2023-33042 |
Not Yet Available*
|
|
OnePlus Nord CE 2 5G
|
MediaTek Dimensity 900 5G
|
Smartphone
|
M_V3_P10 |
CVE-2023-20702 |
Not Yet Available*
|
|
Xiaomi Redmi K40
|
MediaTek Dimensity 1200 5G
|
Smartphone
|
MOLY.NR15.R3.TC8.PR2.SP.V2.1.P70
|
CVE-2023-20702 |
Not Yet Available*
|
|
Asus ROG Phone 5s |
Qualcomm X60
|
Smartphone
|
M3.13.24.73-Anakin2
|
CVE-2023-33042 |
Not Yet Available* |
At the point of writing, security patches for the devices listed in Table 1 were unfortunately not yet available. However, Qualcomm and MediaTek have already released security patches to the product vendors at least two months in advance before making the issues publicly available in their security bulletins. The corresponding security bulletins that covered the CVE IDs have just been published this week on December 4, 2023 [2, 3].
The 5Ghoul vulnerabilities were implementation-based (i.e., vulnerabilities were caused by implementing the 5G protocol in the affected products). It is trivial to exploit by an attacker as no information about the victim’s SIM card is required. Most vulnerabilities would lead to a Denial-of-Service (DoS), except for one vulnerability that led to a downgrade of 5G connectivity to 4G [1]. There are two scenarios where adversaries could target their victims. In the first scenario, a UE may not have yet connected to any gNB (e.g., alighting from a plane and their devices being in airplane mode). Upon turning the UE on and in the vicinity of a 5Ghoul-enabled gNB, the user will experience a DoS or downgrade attack (depending on the attacks being executed by the 5Ghoul-enabled gNB). In the second scenario, a user has an existing connection with a benign 5G gNB. An adversary could utilize various techniques (e.g. frequency jamming or social engineering to enable airplane mode on a smartphone briefly) to get the UE disconnected from the benign 5G gNB while having a 5Ghoul-enabled gNB broadcast at a stronger signal strength. After the victim attempts to reconnect to the 5G network, the stronger signal strength of the 5Ghoul-enabled gNB would make the UE connect to it, thus exposing the victim to 5Ghoul attacks.
The potential scale of devices affected by 5Ghoul is not merely limited to the seven devices listed in Table 1. Based on the devices that used vulnerable 5G modems from Qualcomm and MediaTek identified by the researchers and with reference to Figure 2, a total of 714 smartphone models were estimated to be affected (a wide variety of Android phone brands and Apple devices) [1]. However, it should also be noted that the affected 5G modems could be used in other 5G-enabled environments such as Industrial IoT solutions, home appliances and IP Cameras [2].
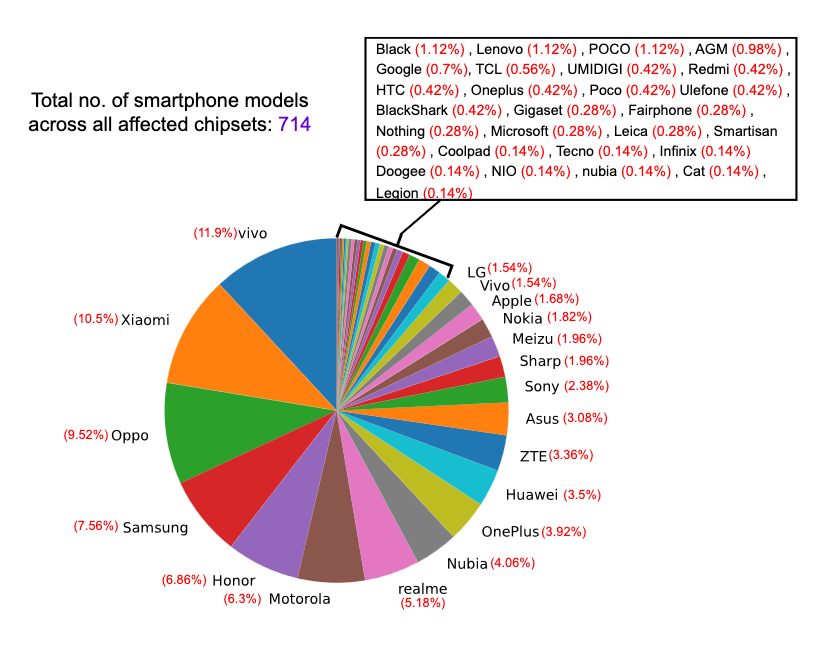
Figure 2: Breakdown of Device Brands Affected by 5Ghoul (figure reproduced with permission from ASSET Research Group)
How should everyone handle the usage of 5G-enabled devices, especially if the devices used are affected by 5Ghoul? One piece of good (or not so good) news is that 5Ghoul affects 5G Standalone (SA) mode only, so setting your device to connect to 5G Non-Standalone (NSA) mode could help reduce the risk brought by 5Ghoul. The downside is that the benefits brought by 5G SA would not be utilized. A slightly more drastic measure would be avoiding using 5G entirely, meaning a self-imposed DoS from 5G. Looking out for suspicious adversaries may not work if a network of well-established 5Ghoul-enabled gNBs with strong signal strength is deployed and the victim steps into the signal zone.
For end users, checking if the security patches are available for your device is highly recommended. As most of the 5Ghoul attacks are DoS related, a loss of 5G connection, especially if your phone was using 5G SA mode, could indicate that a 5Ghoul attack is ongoing. A persistent 4G connection, despite being in an area where a 5G signal is usually received, could also indicate an attack.
Organizations, governments, and critical infrastructure may also be using affected components. If stakeholders are still determining the extent of 5G usage and the associated devices, an audit of the devices/components in use should be carried out. A risk assessment should also be conducted to assess the risk posed by 5Ghoul to users or day-to-day operations. Keeping in mind the attack vector, an interim measure could very well be a policy to use 5G NSA or avoid the use of 5G while affected devices are patched/replaced.
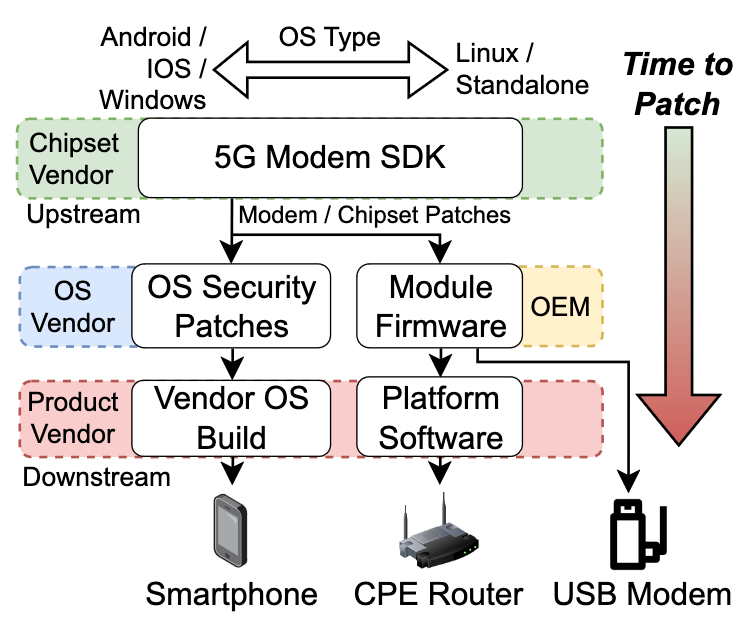
Figure 3: 5G UE Software Supply Ecosystem (figure reproduced with permission from ASSET Research Group)
Finally, for 5G product vendors and service providers, it is highly recommended to contact the researchers for the PoC to test products for 5Ghoul vulnerabilities [4] now or implement the security patches that Qualcomm or MediaTek has provided. With reference to Figure 3, the importance of all involved parties (Chipset vendor, OS vendor and Product vendor) cannot be underestimated. A well-tested software development kit (SDK), along with well-tested implementations of technologies such as 5G, can affect the whole technology ecosystem. Chipset vendors must execute carrier recertification for every upstream 5G modem software version change before the updated firmware can be included in the OS security patches (e.g. Android/iOS). Additional time will also be needed by product vendors who may need to tweak the various smartphone firmware based on their product customizations. Equipment such as Customer Premises Equipment (CPE) routers and USB modems also face similar situations, albeit having matters slightly easier since adherence to the release schedule of OS vendors is not required. Security patches received from the chipset vendors could be directly implemented into their platform software (usually a customized Linux OS). As customers and users increasingly discern the need for their privacy and data to be protected, it is in the vendors’ best interests to ensure product security for continued presence in the market.
References:
[1] https://www.5ghoul.com
[2] https://docs.qualcomm.com/product/publicresources/securitybulletin/december-2023-bulletin.html
[3] https://corp.mediatek.com/product-security-bulletin/December-2023/
[4] https://github.com/asset-group/5ghoul-5g-nr-attacks
-----------
Yee Ching Tok, Ph.D., ISC Handler
Personal Site
Mastodon
Twitter


Comments