Management of DMARC control for email impersonation of domains in the .co TLD - part 1
by Manuel Humberto Santander Pelaez (Version: 1)
There is a cybersecurity risk inherent to the human being that we will not be able to eliminate completely and it is the implicit need to "click" on links that come to us, especially through email, which may be the prelude to the materialization of a cyber attack through an APT.
One of the favorite ways for attackers to trigger social engineering attacks is to impersonate domains that are considered trusted by companies. This allows potential victims to trust incoming emails by the email address that sends them and from there trigger the delivery of the threat.
There is a simple control to implement and it is DMARC, which is a control whose purpose is to avoid the impersonation of domains through emails. It requires as a prerequisite the implementation together of two others (SPF and DKIM). In this diary we will review the DKIM configuration status for all the CO tld with the active domain zone as of April 2023 from the zonefiles.io website. Here are some relevant numbers from the sample:
| Total domains in zone from zonefiles.io | 388802 |
|---|---|
| Total of reachable domains | 371374 |
| com.co domains | 32498 (8.75%) |
| net.co domains | 1393 (0.37%) |
| gov.co domains | 3468 (0.93%) |
| nom.co domains | 67 (0.01%) |
What are the results with the DMARC policy?
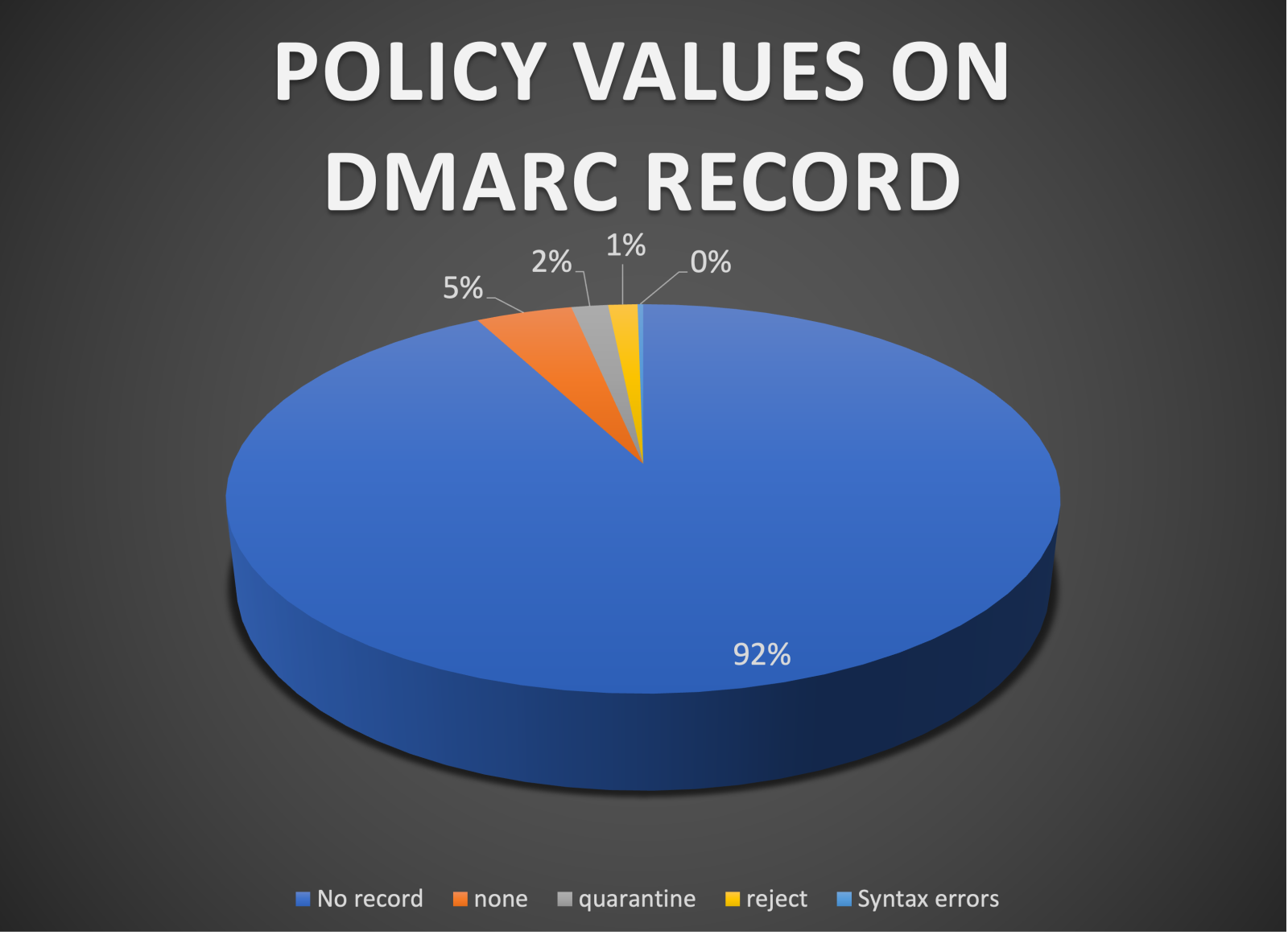
This means 96.94% of the domains do not have any DMARC protection, 1.7% has a quarantine policy and 1.36% a reject policy, which is quite bad as the attackers has an open field to invade with attacks like spearphishing. Syntax errors are 0.26%
Let's see how this goes with com.co domains:
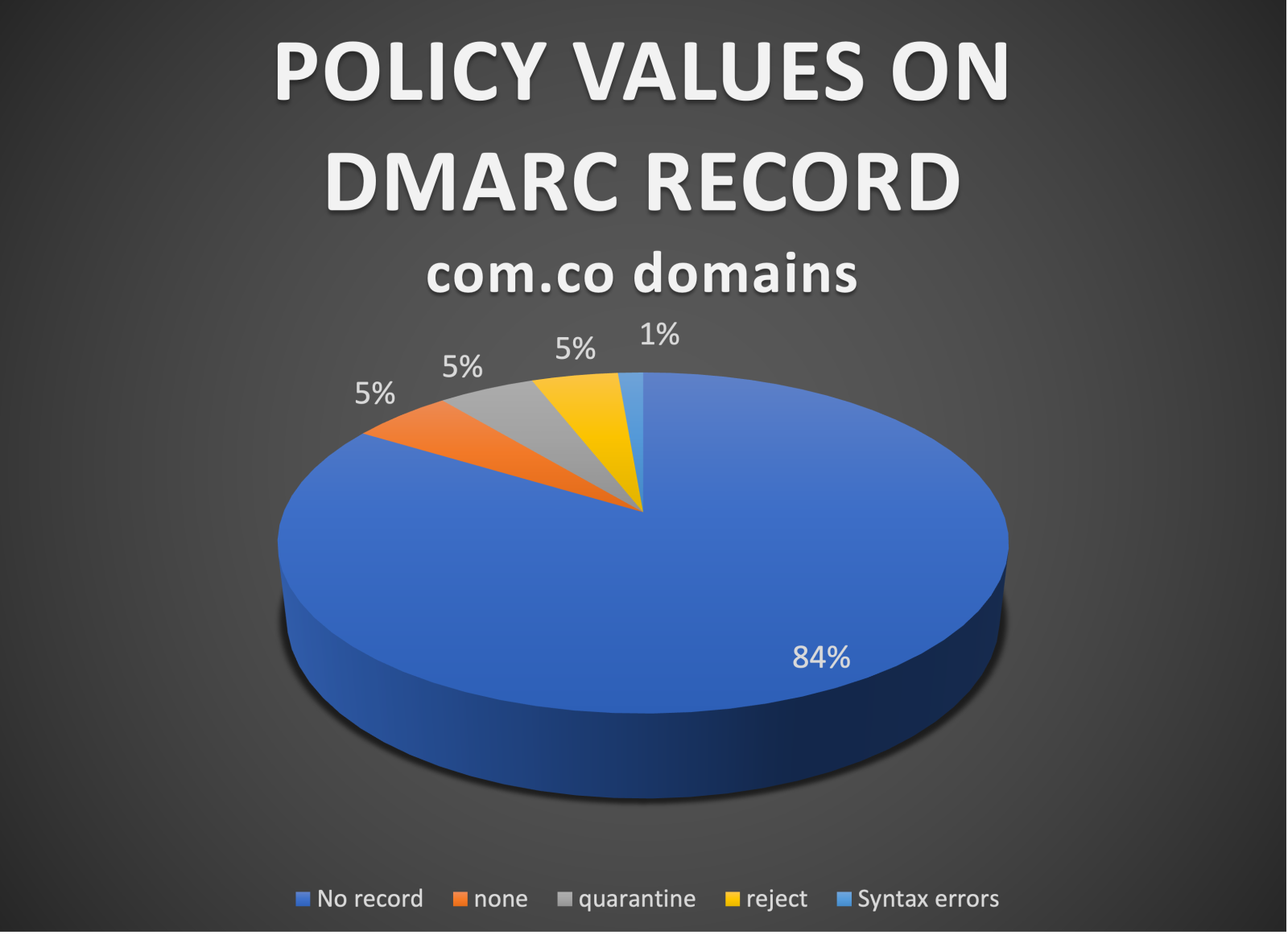
This means 89.03% of the domains do not have any DMARC protection, 5.09% has a quarantine policy and 4.56% a reject policy, which is also quite bad as the attackers has an open field to invade with attacks like spearphishing. Syntax errors increased this time to 1.33%.
Email domain impersonation risk in the .co TLD is quite high. Domain admins should implement DMARC as it's quite easy:
- If you have office365, you can follow this tutorial.
- If you have google, you can follow this tutorial.
- If you have linux DNS and email, you can follow this tutorial.
--------------------------------------- BEGIN OF SPANISH SECTION ----------------------------------------------------------------
Existe un riesgo de ciberseguridad inherente al ser humano que no vamos a poder eliminar por completo y es la necesidad implícita de “clickear” en los enlaces que nos llegan, especialmente a través del correo electrónico, que puede ser la antesala de la materialización de un ciberataque a través de una APT.
Una de las formas favoritas de los atacantes para desencadenar ataques de ingeniería social es hacerse pasar por dominios que las empresas consideran de confianza. Esto permite que las víctimas potenciales confíen en los correos electrónicos entrantes por la dirección de correo electrónico que los envía y desde allí desencadenar la entrega de la amenaza.
Hay un control sencillo de implementar y es DMARC, que es un control cuyo fin es evitar la suplantación de dominios a través de correos electrónicos. Requiere como requisito previo la implementación en conjunto de otros dos (SPF y DKIM). En este diario revisaremos el estado de configuración de DKIM para todos los CO tld con la zona de dominio activa a partir de abril de 2023 desde el sitio web zonefiles.io. Aquí hay algunos números relevantes de la muestra:
| Total de dominios en la zona obtenidos de zonefiles.io | 388802 |
|---|---|
| Dominios alcanzables | 371374 |
| Dominios com.co | 32498 (8.75%) |
| Dominios net.co | 1393 (0.37%) |
| Dominios gov.co | 3468 (0.93%) |
| Dominios nom.co | 67 (0.01%) |
¿Cuáles son los resultados con la política DMARC?
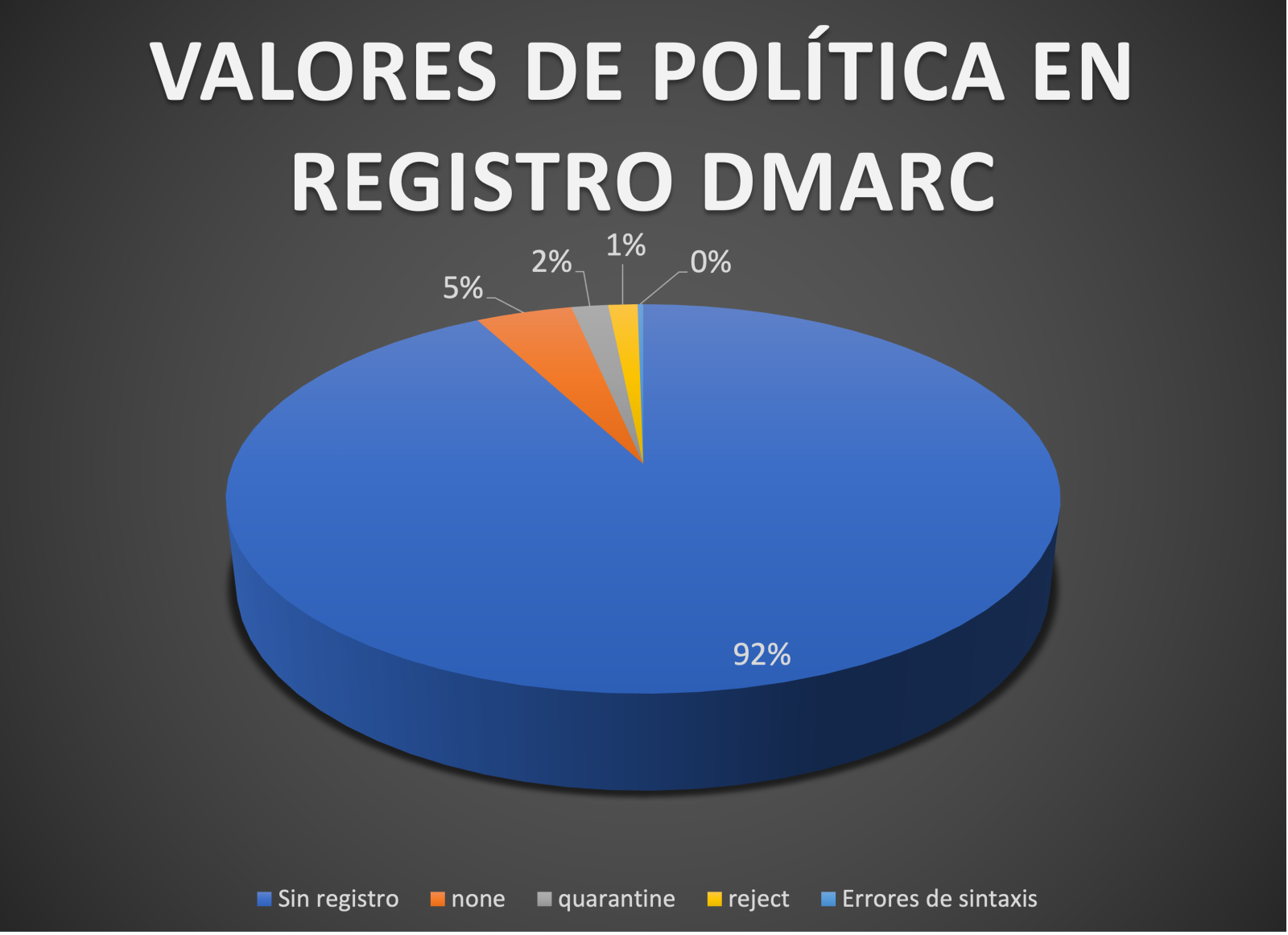
Esto significa que el 96,94 % de los dominios no tienen ninguna protección DMARC, el 1,7 % tiene una política de cuarentena y el 1,36 % una política de rechazo, lo cual es bastante malo ya que los atacantes tienen un campo abierto para invadir con ataques como el spearphishing. Los errores de sintaxis son 0.26%
Veamos los resultados asociados a los dominios com.co:
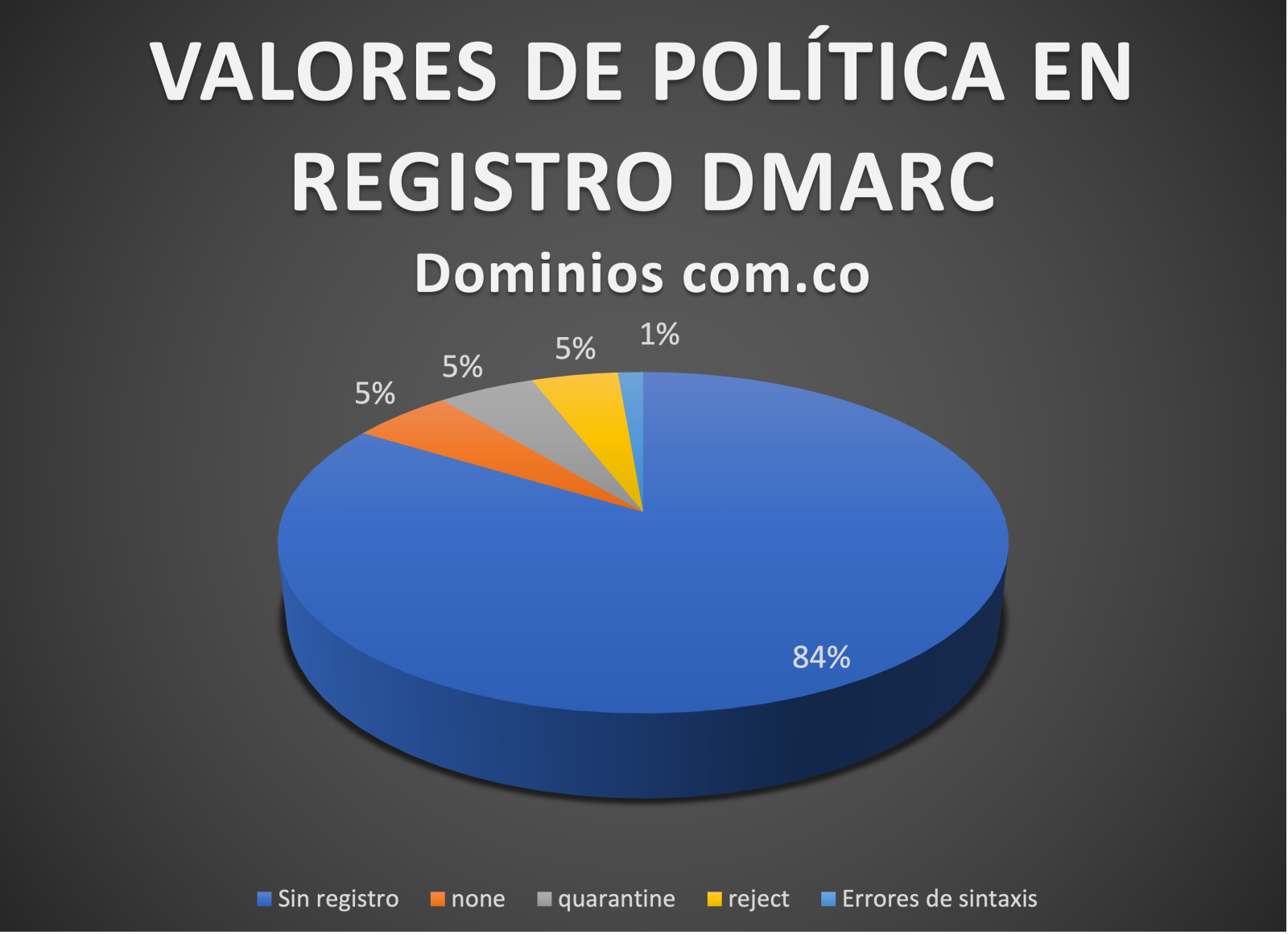
Esto significa que el 89,03 % de los dominios no tienen ninguna protección DMARC, el 5,09 % tiene una política de cuarentena y el 4,56 % una política de rechazo, lo que también es bastante malo ya que los atacantes tienen un campo abierto para invadir con ataques como el spearphishing. Los errores de sintaxis aumentaron esta vez al 1,33%.
El riesgo de suplantación de dominio de correo electrónico en el TLD .co es bastante alto. Los administradores de dominio deben implementar DMARC ya que es bastante fácil:
- Si tiene Office365, puede seguir este tutorial.
- Si tienes google, puedes seguir este tutorial.
- Si tiene DNS y correo electrónico de Linux, puede seguir este tutorial.
Manuel Humberto Santander Peláez
SANS Internet Storm Center - Handler
Twitter: @manuelsantander
Mastodon:[email protected]
Linkedin:manuelsantander
email:[email protected]


Comments
jjm
Apr 23rd 2023
2 years ago
The small businesses also don't care about things like DMARC and aren't going to read the reports or do anything with it because it's too hard for them. Let's not forget that DMARC is just a policy so a sending domain can tell a receiving email server what to do if SPF and/or DKIM fail. Without DMARC that decision is left up to the receiving email server which for all but those in need of the highest security is usually fine. But I do like the DMARC reports if you can digest them into one big report and see attackers trying to spoof your domain over time, and with a DMARC policy in place you will know those emails didn't make it. I mostly see DMARC putting marketing emails sent from third party marketing companies in quarantine because of SPF/DMARC configuration errors and I really don't feel terrible about that, haha.
In a perfect world I think these tools should be used such that all of your emails are signed (DKIM) but only "your" email servers are listed on your SPF policy (sort of like DNSWL.org..."hey, these are my servers, nothing to see here") and the DMARC policy tells the receiving email server to reject what fails (with aspf in relaxed mode, and dont forget that subdomain policy). Then if SPF AND DKIM fail it will be rejected but if just one of them fails it can be quarantined or whatever the receiving email server wants and business can continue as usual.
It's not perfect but there are so few standards as to how to use these tools that someone needs to do something or it isn't going to work. Microsoft will go along treating SPF as if it's written in stone while Google cares mostly about DKIM and everyone will be confused about why email lands in quarantine (this is just a random example and not actually how Microsoft and Google work). Meanwhile BIMI is just a distraction and no one really cares because your official logo appearing or not never stopped someone from clicking a link (and who is stopping to inspect that it's the official logo and not some ripoff one anyway).
Thanks for reading my email rant and keep up the good work over there!
Sam
Apr 24th 2023
2 years ago
Sam
Apr 24th 2023
2 years ago
SPF record for domain 'bluehost.com': invalid
Error: Too many DNS lookups (12 > 10).
fab23
Apr 25th 2023
2 years ago
The compacted SPF also has the issue of legit things getting bounced because one of the providers made changes which happen without notice.
It really seems like SPF should not be using DNS for hosting the authorization list, or at least provide a way to host the list off a web server or other method without the current DNS lookup limits.
Dingbat
Apr 28th 2023
2 years ago
Let's take Bluehost and a conduct a little bit of OSINT
Bluehost are owned by NewFold and they also have many other providers in their portfolio
All are vulnerable to direct domain impersonation and it's trivial to do.
python3 edsquery.py -d "bluehost.com newfold.com crazydomains.co.uk hostgator.com networksolutions.com register.com web.com" --dmarc
Querying 7 domains...
bluehost.com
DMARC record: v=DMARC1; p=none; rua=mailto:[email protected]; ruf=mailto:[email protected]; rf=afrf; pct=10;
newfold.com
DMARC record: v=DMARC1; p=none;
crazydomains.co.uk
DMARC record: v=DMARC1; p=none
hostgator.com
DMARC record: v=DMARC1; p=none; rua=mailto:[email protected]; ruf=mailto:[email protected]; rf=afrf; pct=10;
networksolutions.com
DMARC record: v=DMARC1; p=none; rua=mailto:[email protected]; ruf=mailto:[email protected]; fo=1
register.com
DMARC record: v=DMARC1; p=none; rua=mailto:[email protected]; ruf=mailto:[email protected]; fo=1
web.com
DMARC record: v=DMARC1; p=none; rua=mailto:[email protected]; ruf=mailto:[email protected]; fo=1
7 of 7 domains returned
Another thing, many just focus on the primary domain, what about all the others?
NewFold likely own these, they redirect to their website (there are more).
python3 edsquery.py -d "newfold-digital.com newfolddigital.com" --spf --dmarc --mx
Querying 2 domains...
newfold-digital.com
SPF record: v=spf1 include:spf.protection.outlook.com -all
DMARC record: A DMARC record does not exist for this domain or its base domain
MX Records: 0 newfolddigital-com01i.mail.eo.outlook.com.
newfolddigital.com
SPF record: v=spf1 include:spf.protection.outlook.com -all
DMARC record: A DMARC record does not exist for this domain or its base domain
MX Records: 0 newfolddigital-com.mail.eo.outlook.com.
2 of 2 domains returned
v=DMARC1; p=none; is pointless without the RUA tag. You have no visibility while in monitor mode and you'd be guessing when trying to configure your authorised sending services for DMARC alignment.
Don't bother with SPF hard-fail, just use soft-fail, why?
A) False sense of security because hard-fail is easily bypassed. RFC5321_Mail.From will be the attacker domain and RCF5322_From will be the impersonation.
B) Hurts DMARC reporting. MTAs may honour that hard-fail and reject the message, so you'll never receive the DMARC aggregate report. The mail will be rejected as instructed, before the 'data' command and "354 Start mail data, end with CRLF.CRLF" response.
Misconception I sometimes hear, SPF soft-fail overrides DMARC enforcement (quarantine / reject). The reality is, with DMARC enforcement, SPF authentication failure is a hard-fail.
Finally, too many just focus on sending domains. Non-sending domains, should be locked down with SPF, DKIM and DMARC to instruct recipients to reject all messages.
Bob
Sep 23rd 2023
2 years ago