Are Roku Streaming Devices Safe from Exploitation?
I have noticed in the past several weeks random scans specifically for Roku streaming devices (and likely other types) captured by my honeypot. If they can be compromised, what can be gain? Settings like stored payment information, personal information (email/password), subscription, App selected, etc. Like any other devices, it is important to keep the OS and Apps up-to-date.
Traffic Activity
20220421-180039: 192.168.25.9:81-159.65.4.198:56874 data
GET /stream/live.php HTTP
Host: 184.146.XX.XX:81
User-Agent: Roku/DVP-9.10 (289.10E04111A)
Accept-Encoding: gzip, deflate
Accept: */*
Connection: keep-alive
20220421-180046: 192.168.25.9:8088-159.65.4.198:52264 data
GET /flu/403.html HTTP/1.1
Host: 184.146.XX.XX:8088
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/74.0.3729.169 Safari/537.36
Accept-Encoding: gzip, deflate
Accept: */*
Connection: keep-alive
Indicators
159.65.4.198
159.65.144.167
188.166.54.150
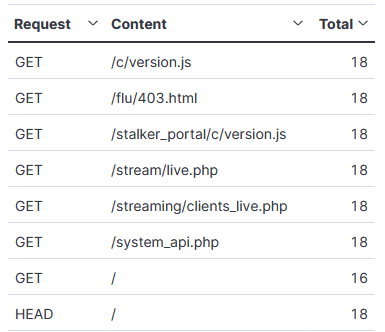
Get Requests
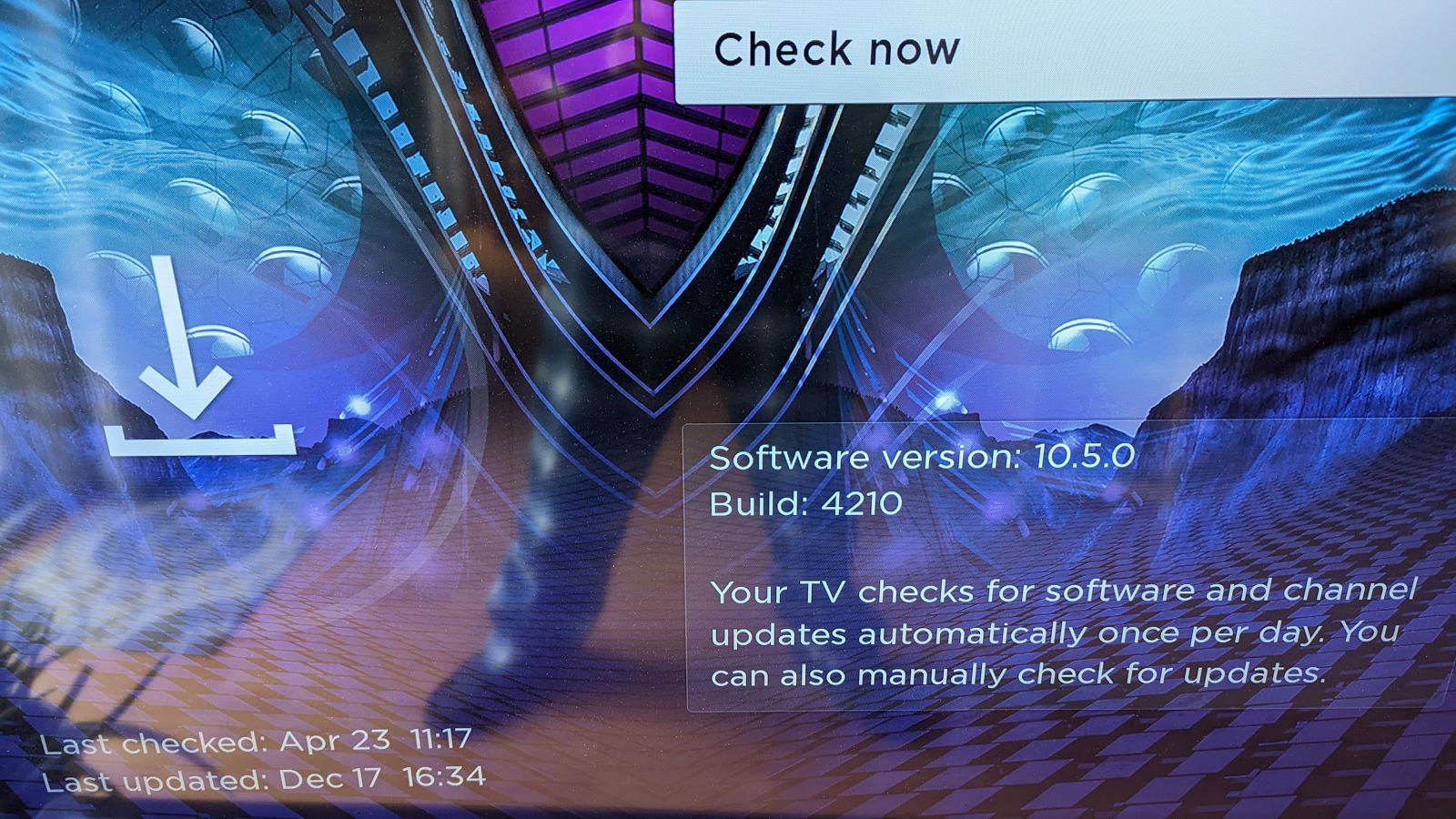
It is a good idea to regularly review the information stored in setting and make sure the Roku device is up-to-date.
[1] https://www.shodan.io/search?query=Server%3A+Roku+
[2] https://isc.sans.edu/forums/diary/Who+Is+Hunting+For+Your+IPTV+SetTop+Box/27912/
[3] https://support.roku.com/
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu


Comments
Anonymous
Apr 24th 2022
3 years ago