Use of Alternate Data Streams in Research Scans for index.jsp.
Our network of web application honeypots delivered some odd new URLs in the last 24 hrs:
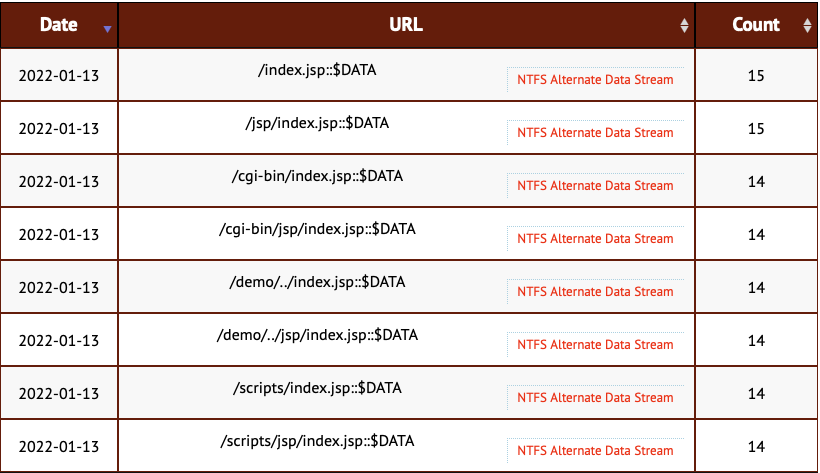
/index.jsp::$DATA
/jsp/index.jsp::$DATA
/cgi-bin/index.jsp::$DATA
/cgi-bin/jsp/index.jsp::$DATA
/demo/../index.jsp::$DATA
/demo/../jsp/index.jsp::$DATA
/scripts/index.jsp::$DATA
/scripts/jsp/index.jsp::$DATA
I am not 100% sure what these scans are after, but my best guess right now is that they are attempting to bypass filters using NTFS alternate data streams.
The Windows NTFS file system includes the ability to connect to alternate data streams. This has been documented in the past as a technique to hide data or to bypass URL filters [1][2].
In this case, the scans originate from 64.39.106.87 , an IP associated with vulnerability scanning company Qualys. It appears to be hunting for index.jsp, a default for Java applications. Inside the cgi-bin or scripts directory, it may very well lead to code execution and may be protected by a WAF that the attacker attempts to bypass. I assume that right now, this is likely just a Qualys research project, but a good reminder to double-check your URL filters
Any other ideas? Let me know.
[1] https://owasp.org/www-community/attacks/Windows_alternate_data_stream
[2] https://owasp.org/www-community/vulnerabilities/Unrestricted_File_Upload
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments