Decoding Cobalt Strike Traffic
In diary entry "Example of Cleartext Cobalt Strike Traffic (Thanks Brad)" I share a capture file I found with unencrypted Cobalt Strike traffic. The traffic is unencrypted since the malicious actors used a trial version of Cobalt Strike.
This weekend I carried on with the analysis of that traffic, you can see my findings in this video and read the diary entry below.
Reader binarysheperds posted a comment to point out packet 8241, that looks like containing output of a UAC bypass command:
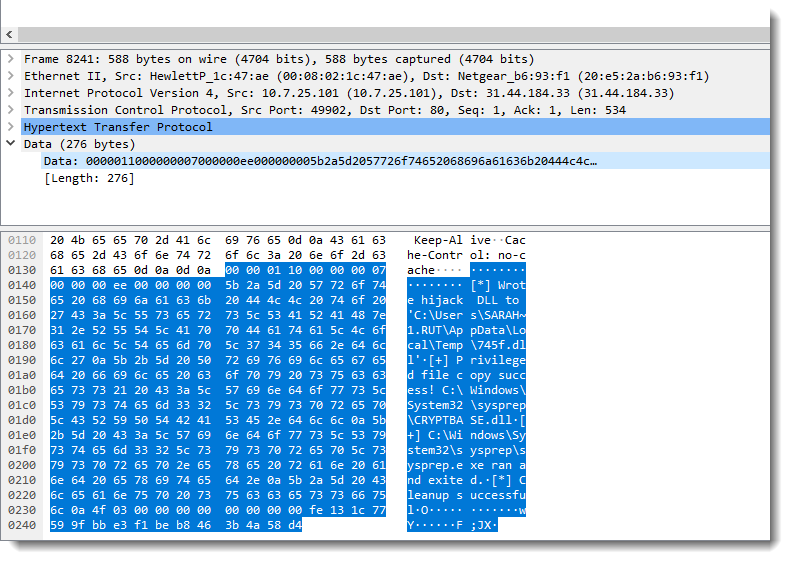
Yesterday I took a closer look at the binary protocol, started to see some patterns (like an epoch value), and then I found Python code on Github that handles Cobalt Strike's encrypted traffic.
This allowed me to write a decoding tool: parse-cs-http-traffic.py. It takes the pcap file as argument and relies on Python module pyshark to parse the pcap file. I then extract the traffic and parse it. The parsing code is still incomplete because of inciomplete understanding of the protocol.
Here is the output of my tool for the UAC bypass:
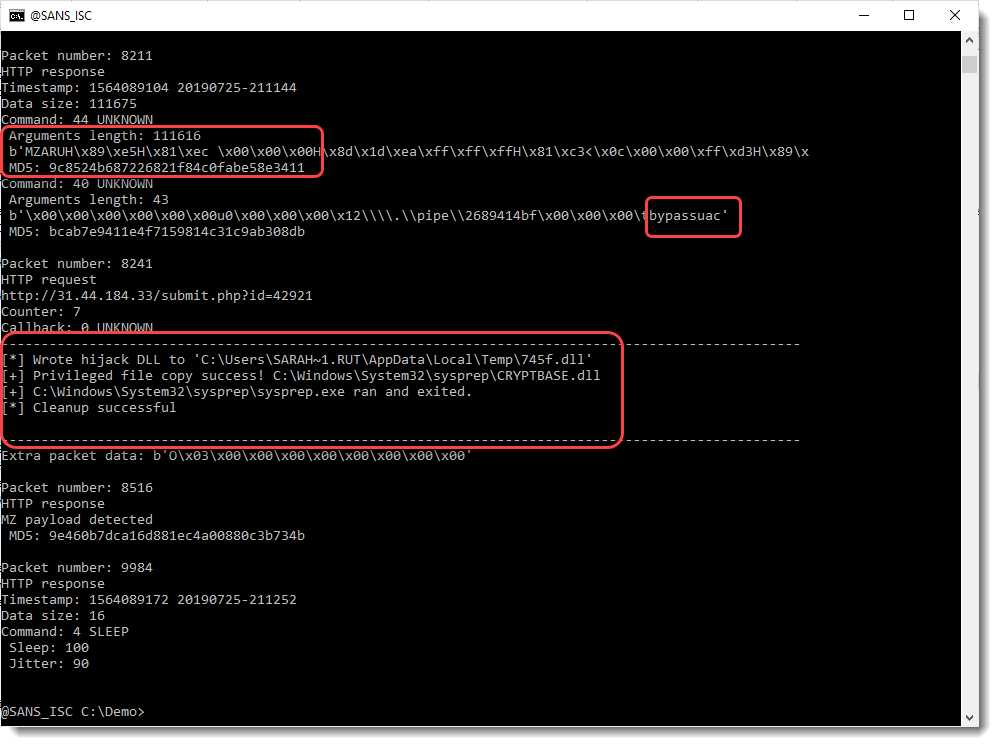
First, with an HTTP response, commands are delivered to the beacon: download a DLL and do a UAC bypass.
Second, the output (text) is send to the C2 with an HTTP POST request.
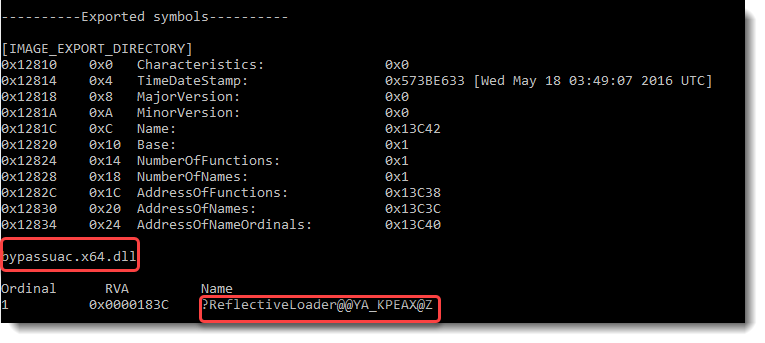
This DLL is a reflective loader to perform a UAC bypass:
I also found portscanning activity. You can watch the complete analysis in this video:
And here are 2 videos by Cobalt Strike developer Raphael Mudge on portscanning and UAC bypass.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments
Anonymous
Apr 19th 2021
4 years ago
When using Fireeye's floss tool to view its strings, the DLL is found in this JS. This JS should be the one reflectively loaded into sysprep.exe to privilege escalation.
https://gist.github.com/dfirnewbie/daaf5be41cc3061bd1c3cc9531c30bea
Anonymous
Apr 20th 2021
4 years ago