Using AutorunsToWinEventLog
Using AutorunsToWinEventLog
One of the main limitations of autorun by Microsoft Sysinternals is that it doesn’t scale very well.
Palantir AutorunsToWinEventLog can help to resolve this issue.
Palantir AutorunsToWinEventLog
Palantir AutorunsToWinEventLog is a PowerShell script that runs autorunsc and converts it to Windows Events.
What does AutorunsToWinEventLog do?
“Autoruns conveniently includes a non-interactive command line utility. This code generates a CSV of Autoruns entries, converts them to JSON, and finally inserts them into a custom Windows Event Log. By doing this, we can take advantage of our existing WEF infrastructure to get these entries into our SIEM and start looking for signs of malicious persistence on endpoints and servers.”[1]
AutorunsToWinEventLog can be obtained from https://github.com/palantir/windows-event-forwarding/tree/master/AutorunsToWinEventLog
once you download the script, you can run the following command from an admin PowerShell console.
|
.\Install.ps1 |
The script will do the following by default :
- Creates the directory structure at c:\Program Files\AutorunsToWinEventLog
- Copies over AutorunsToWinEventLog.ps1 to that directory
- Downloads Autorunsc64.exe from https://live.sysinternals.com
- Sets up a scheduled task to run the script daily @ 11am
Since it’s a PowerShell script, it can be modified with a very basic knowledge of programming.
Now after running the script lets check the windows events viewer
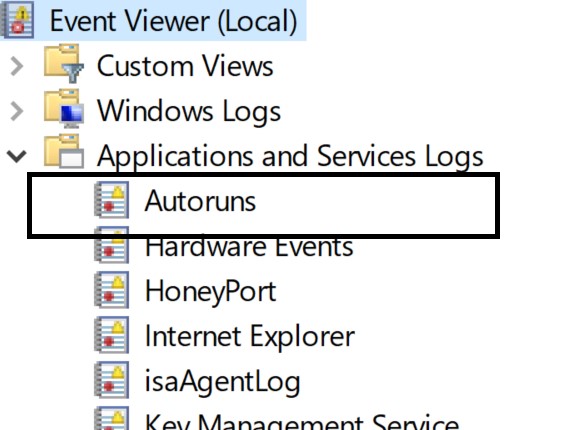
As you can see in the above picture , you have Autoruns under Applications and Services Logs.
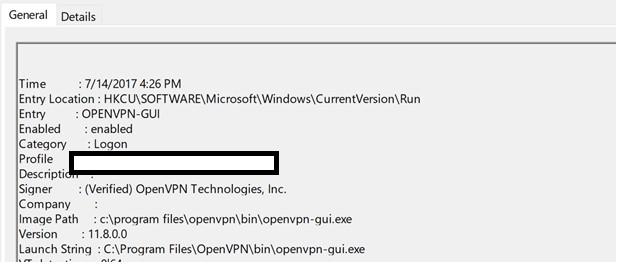
In the above picture, you can see sample events of OpenVPN that will run when the user login.
But what’s the point if having AutorunsToWinEventLog if you are not going to forward the events logs to SIEM?
Here is a sample event from Splunk interface
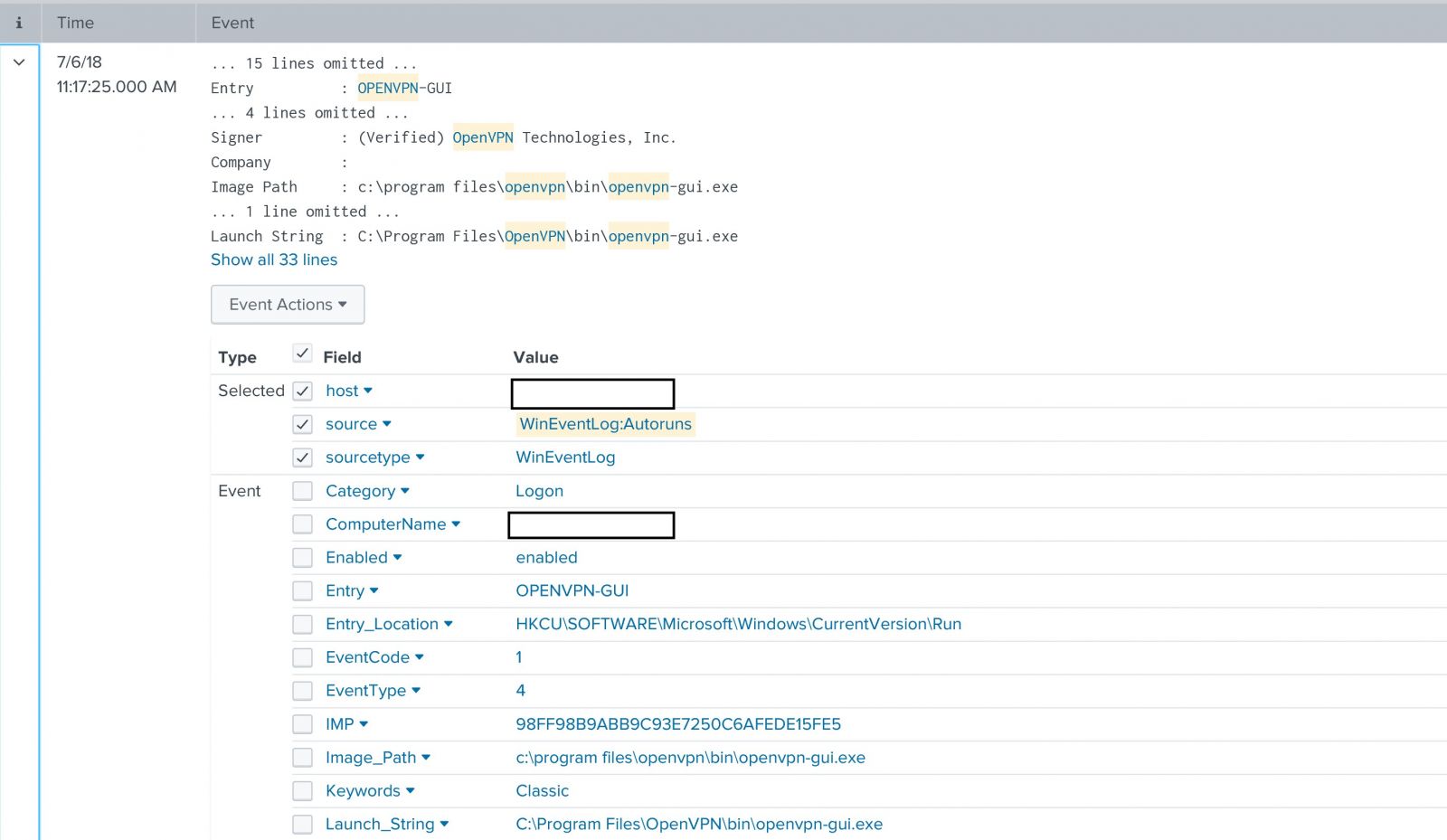
And since we are using autorunsc ,autorunsc can query virustotal by sending the file hash(by using the -v switch ), and AutorunsToWinEventLog is doing that by default. So we can check if there is any entry that triggered virustotal alert.
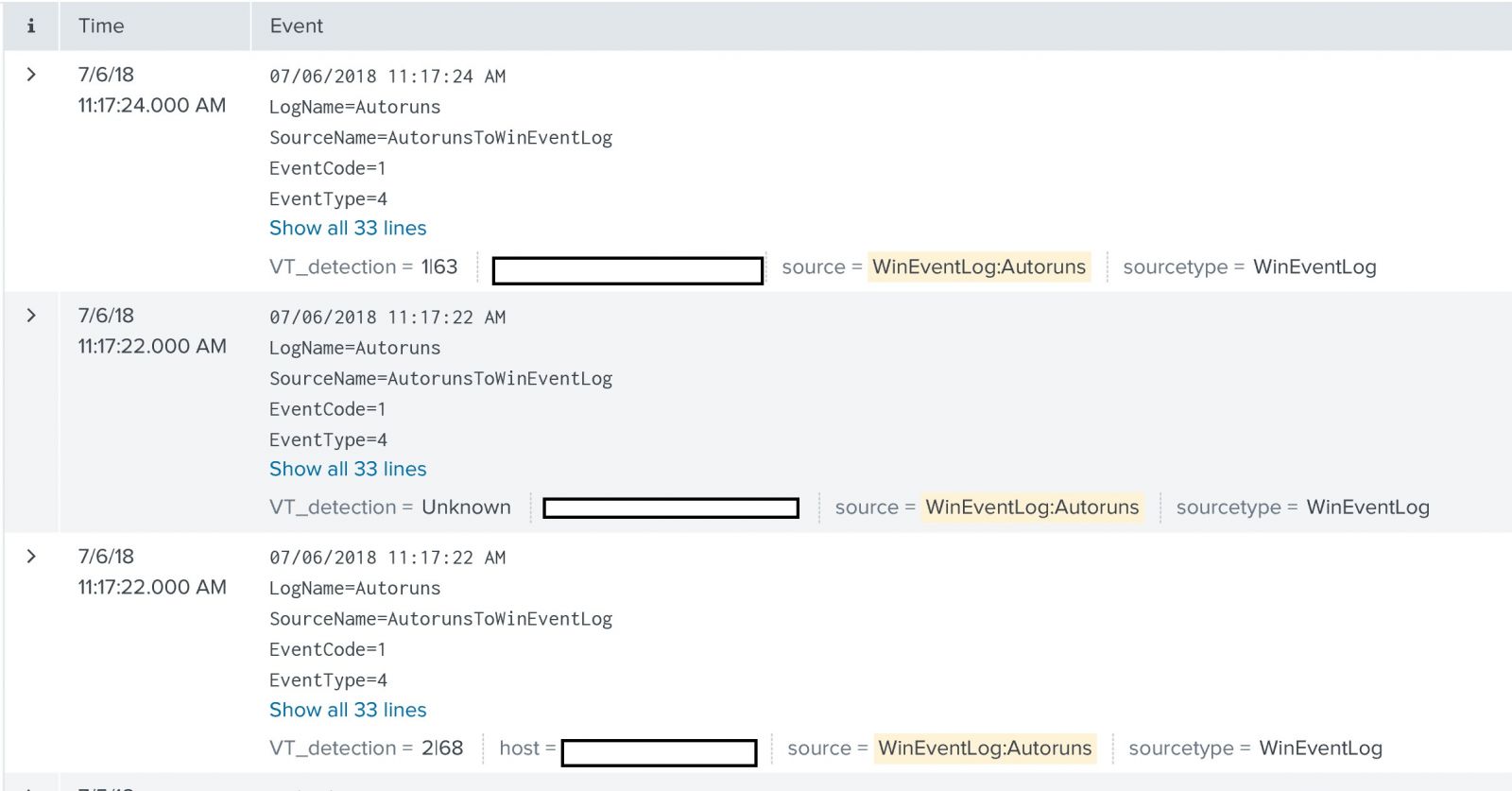
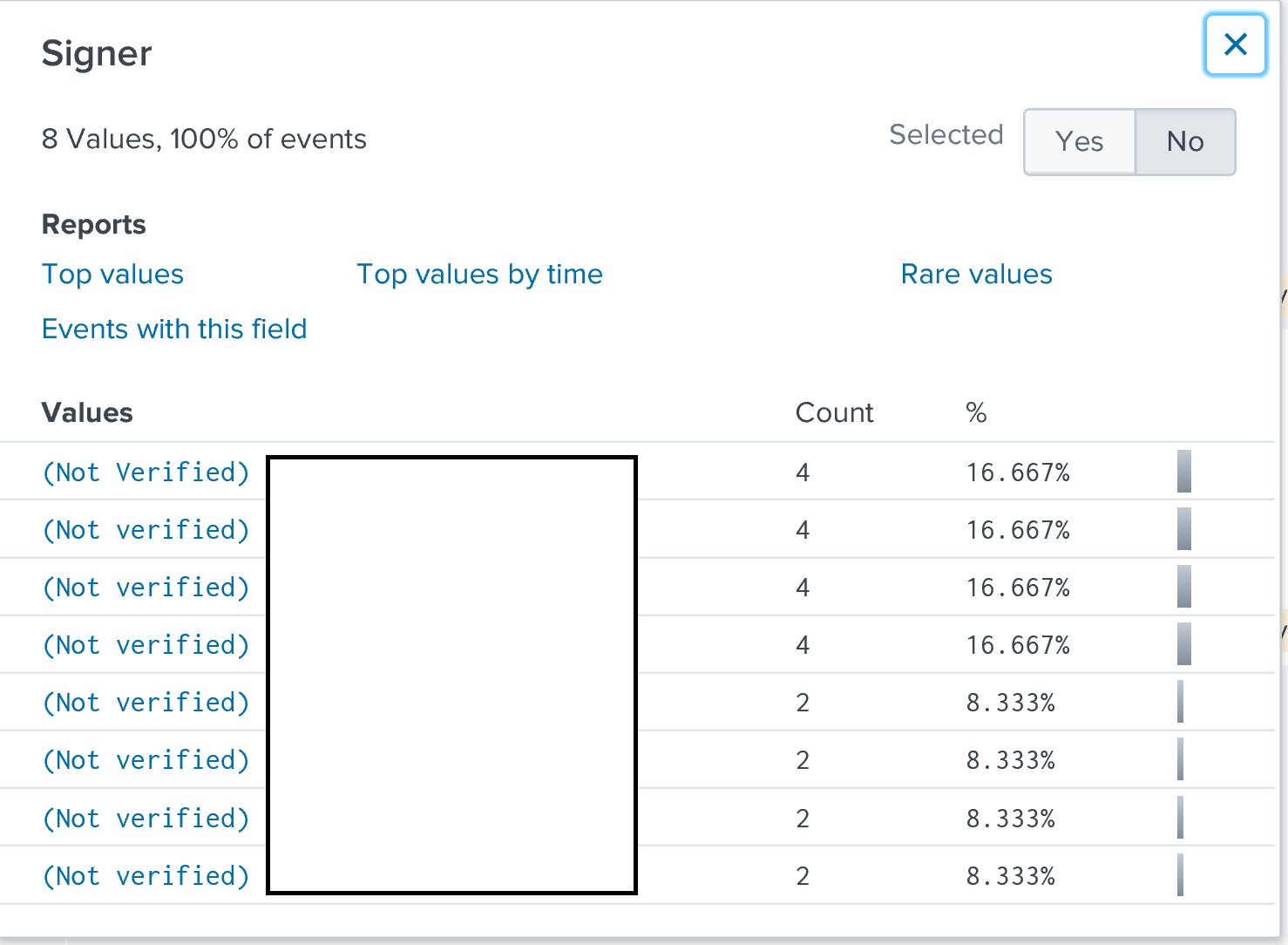
Or we can check if the signer is not verified
[1] https://github.com/palantir/windows-event-forwarding/tree/master/AutorunsToWinEventLog


Comments