One month later, Magniber ransomware is still out there
Introduction
Last month in October 2017, several sources reported a new ransomware family distributed by Magnitude exploit kit (EK) [1, 2, 3]. Security researchers dubbed the new ransomware "Magniber" because it appears to have replaced Cerber ransomware as distributed through Magnitude EK. Cerber seems to have disappeared since then, but as November 2017 progresses, we're still seeing Magniber.
Magnitude EK appears to be the sole distributer of Magniber, and it still appears to be targeting Korea as noted in the original reports. I had tried to generate infection traffic from Magniber in my home lab; however, I was never successful until I used a Korean version of Windows.
Magniber didn't run on my English version of Windows.
Details
Nothing new, really, since the original wave of reporting on Magniber. However, I wanted to show this activity is still happening. The most recent Magniber sample I can confirm is SHA256 hash 7a2697e3dc0f2a678dedc8d9842a55b8efe6e11933aa32fb856f61ad5e3eecd7 first submitted to VirusTotal last week on 2017-11-14 [4].
My thanks to researchers like @hasherezade who have submitted Magniber samples to VirusTotal and left comments with the #Magniber tag. That made recent samples much easier to find.
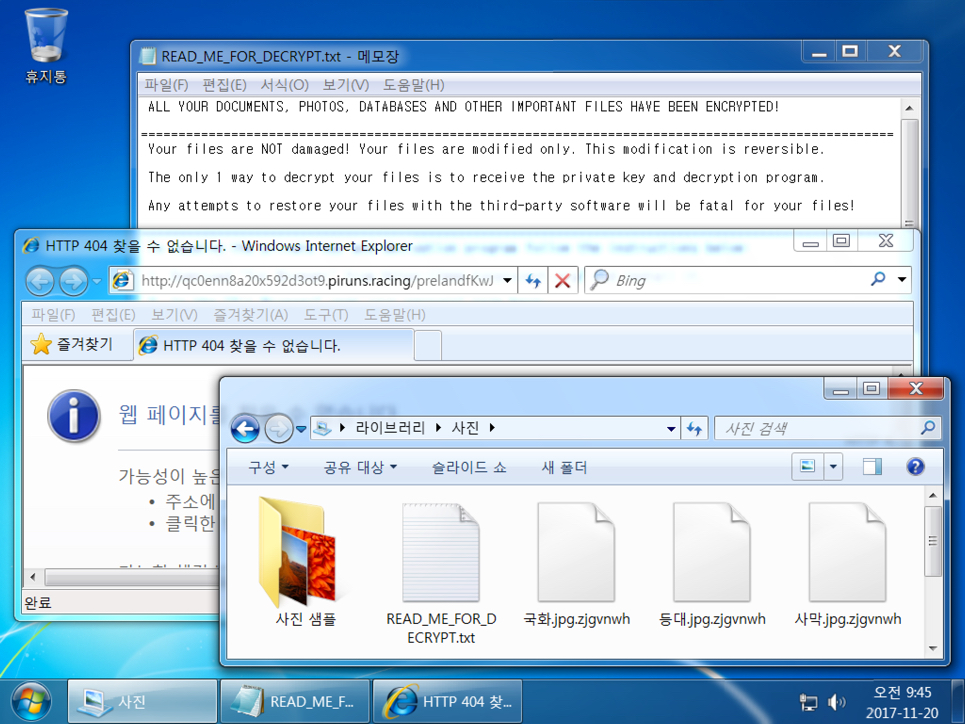
Shown above: Desktop of an infected Korean Windows computer.
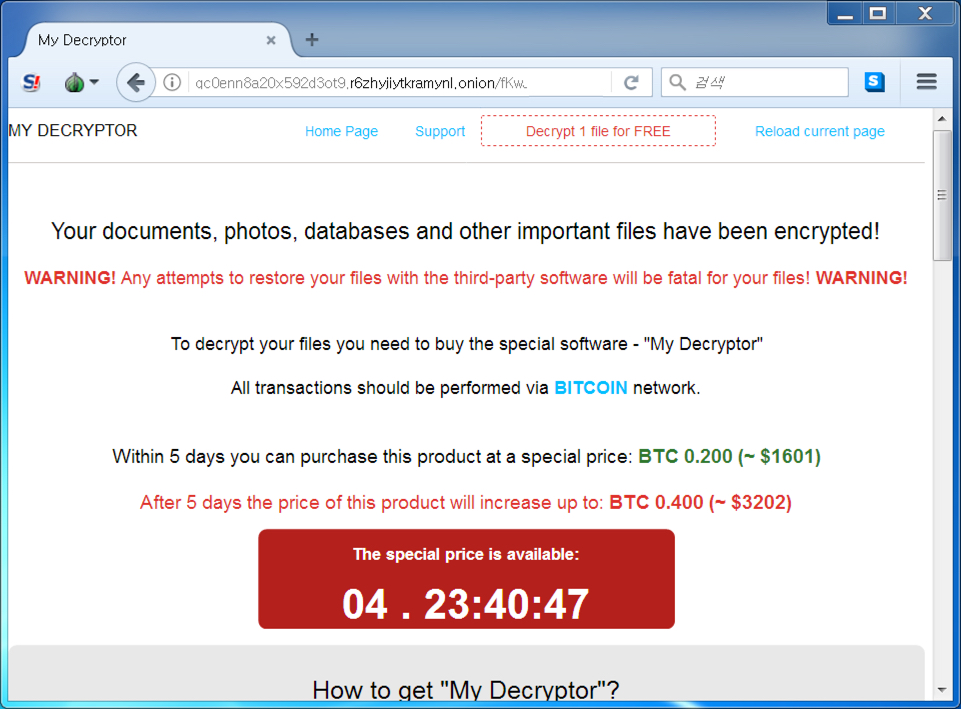
Shown above: Tor page for viewing the decryption instructions.
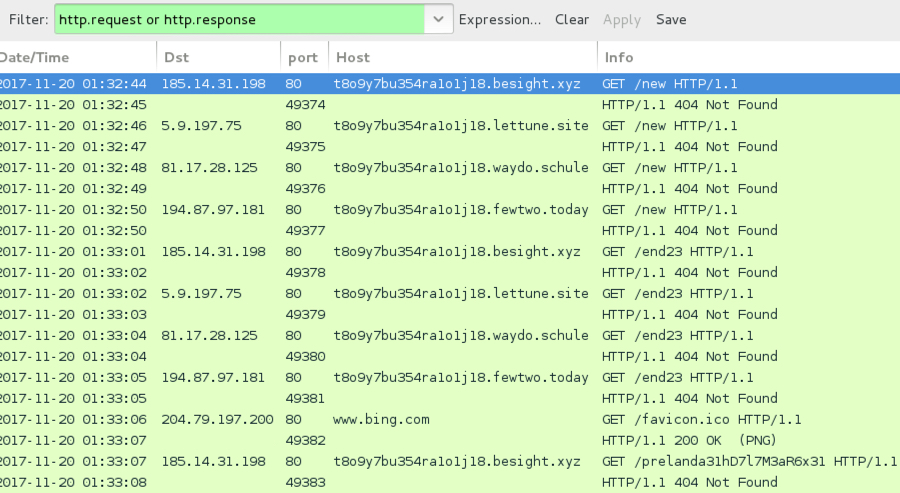
Shown above: Traffic from an infection filtered in Wireshark.
Final words
My standard disclaimer still applies. System administrators and the technically inclined can implement best practices like Software Restriction Policies (SRP) or AppLocker to prevent these types of infections.
If I can generate some Magnitude EK traffic and acquire a newer Magniber sample, I will post the updated information.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
References:
[1] http://blog.trendmicro.com/trendlabs-security-intelligence/magnitude-exploit-kit-now-targeting-korea-with-magniber-ransomware/
[2] https://blog.malwarebytes.com/threat-analysis/2017/10/magniber-ransomware-exclusively-for-south-koreans/
[3] https://www.bleepingcomputer.com/news/security/goodbye-cerber-hello-magniber-ransomware/
[4] https://www.virustotal.com/en/file/7a2697e3dc0f2a678dedc8d9842a55b8efe6e11933aa32fb856f61ad5e3eecd7/analysis/


Comments