Guilty by association
Loyal reader Carlos submitted another suspicious file, found with a ransomware infection. The executable is very large, 25MB, too large to be submitted via our form. Carlos shared the link for the download:
hxxps://github[.]com/mailchuck/PyBitmessage/releases/download/v0[.]5[.]8/Bitmessage-0[.]5[.]8[.]exe
As you can see, it's hosted on GitHub.
Analyzing a 25MB PE file can be a huge task. Fortunately for me, this PE file is a compiled Python program. Decompiling the PE file resulted in a Python program, that did not seem to contain malicious code (I did not look at the modules).
Doing a dynamic analysis in a sandbox, I saw the following:
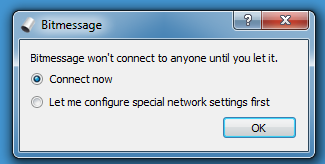
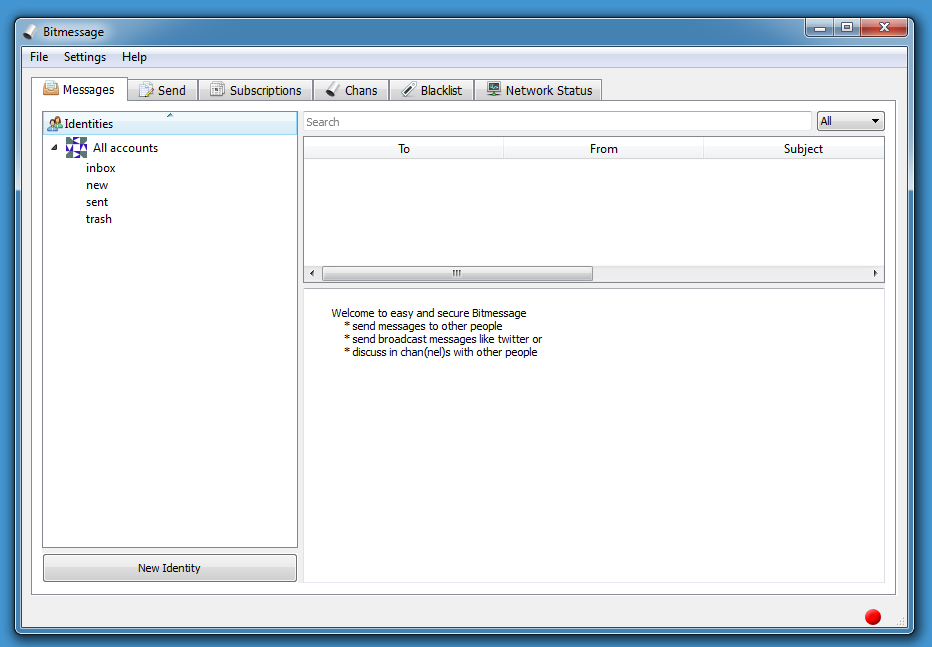
This looks like a genuine messaging app (BitMessage). So maybe this sample is trojanized. But analyzing a 25MB PE file looking for malicious code, can be difficult. Let's see what VirusTotal has to say:
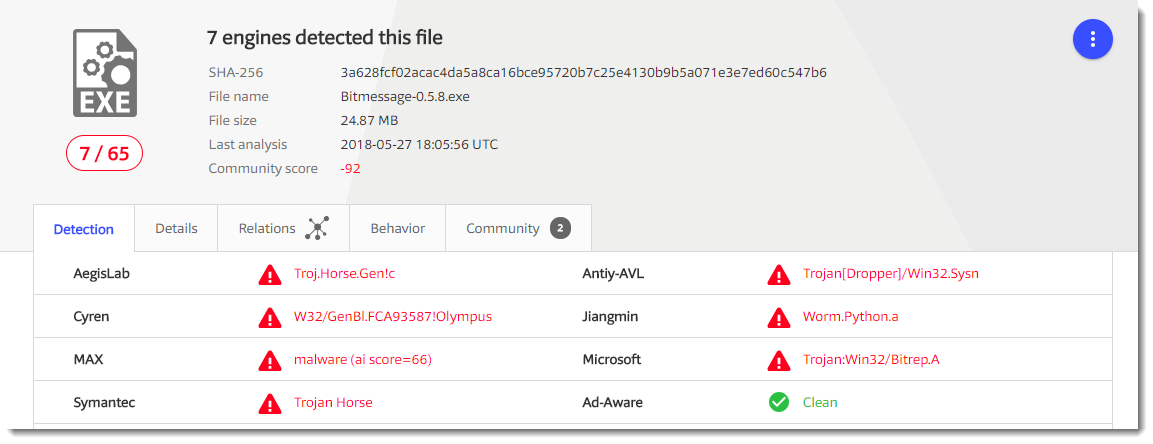
7 detections for ransomware is not much. Before I started to look at the sample again, I did some research with the help of Google.
I discovered that there have been several reports of ransomware cases, where the criminals "invited" their victims to download this specific version of BitMessage to communicate with them.
Like this ransom note:
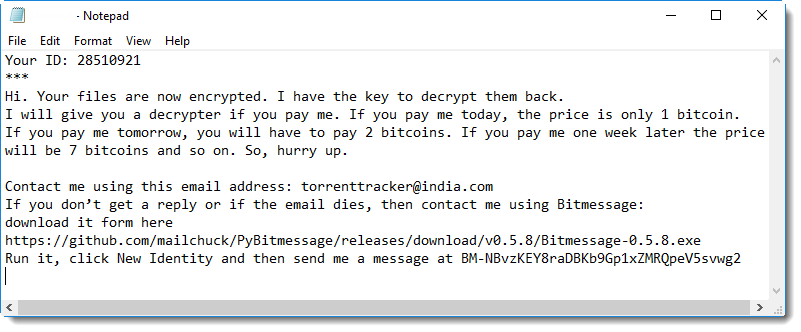
My conclusion: this BitMessage application, a fork of the official BitMessage application, is most likely not malicious, although proving this with 100% certainty is impossible. There is simply too much code to analyze.
The detections reported on VirusTotal are most likely the result of "guilt by association". This specific version of BitMessage has been found in several ransomware cases, and users and automatic sandboxes have submitted this sample to VirusTotal, sharing it with anti-virus vendors. It's a bit like the empty file (MD5 d41d8cd98f00b204e9800998ecf8427e): it has been found so many times on malware infected machines (for example because of failed dynamic analysis), that it has a large number of downvotes on VirusTotal:
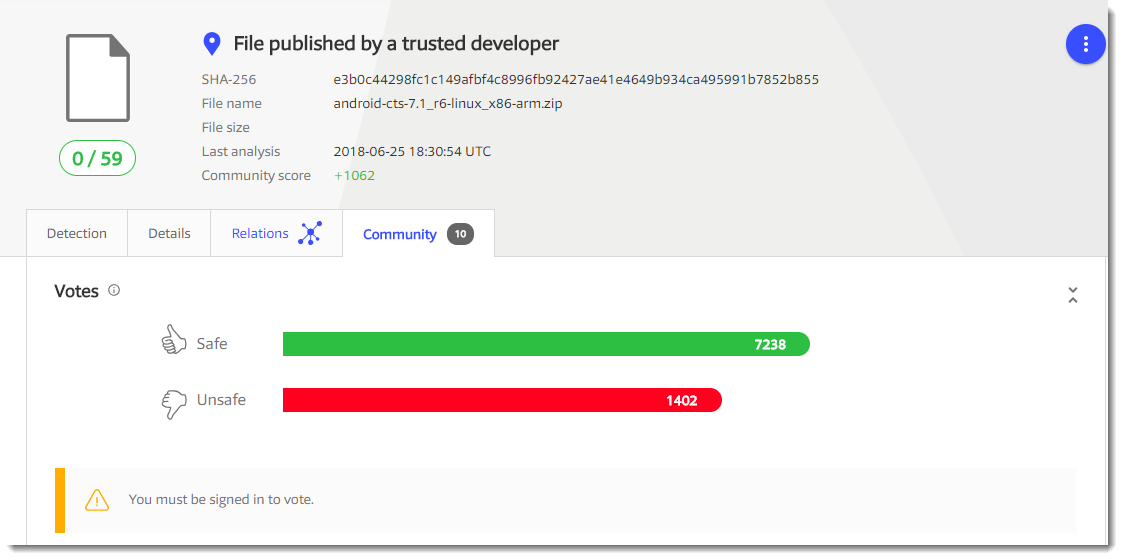
While the number of (malicious) bytes it contains is ... zero.
Conclusion: when you investigate infections, files that are detected by anti-virus programs might actually be bening, but still provide clues to help you further in your analysis.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com


Comments
Carlos
Anonymous
Jun 25th 2018
7 years ago
PyInstaller is used by some malware, and this often leads to executables also using PyInstaller (like the windows executable for PyBitmessage) to be flagged as harmful as well. I now rebuild the PyInstaller bootloader, which reduces the likelihood of a false positive. It's remotely possible that the VM I built 0.5.8 on was infected as the security procedures used in the build process were more relaxed at that time, but probably it was just a false positive. It is also possible that the binary was somehow manipulated, this you can check with the PGP signature which is still available on the github releases page. Since I have a smart card for signing the likelihood that both the binary and the signature were compromised is very small.
Since then I joined the official project, the build process has been documented and hardened and I now have a code signing certificate for Windows executables (also on a smart card).
Anonymous
Jun 26th 2018
7 years ago