Your Bill Is Not Overdue today!
Just as little as yesterday's order that "proceeded." It Look like today's ransomware subject is "Your Bill is Overdue." But then again, don't bother blocking it. Block ZIP'ed visual basic scripts. This round of Locky makes blocking a tad harder by using "application/octet-stream" as a Content-Type instead of "application/zip."
(and about 2 hrs after publishing this diary, another small update: the Content-Type now changed to application/x-compressed . Makes you wonder if they are reading this ;-) )
It may be safe to strip everything with an "application/octet-stream" attachment.
For the last 30 minutes, I received just about 1,000 attachments like that, and about 4000 total. The first one I received arrived just after 8 am UTC.
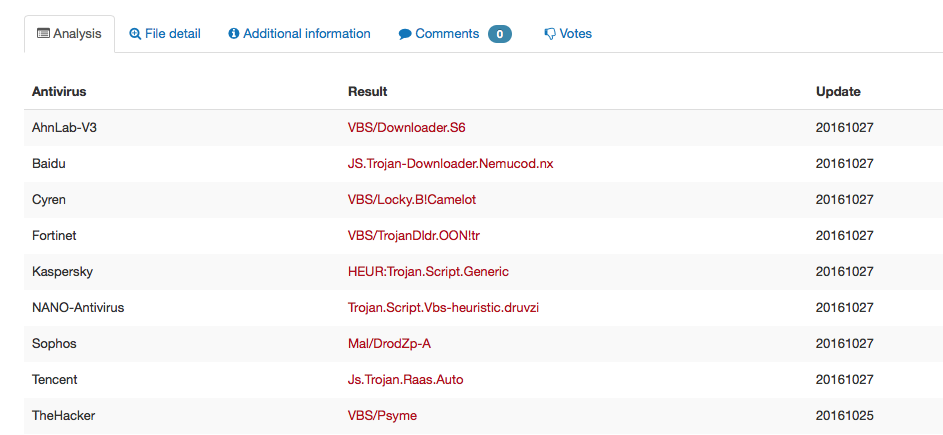
Anti-Virus coverage is spotty as usual. Kaspersky and Sophos seem to be doing a rather good job lately detecting the initial downloaders
As usual, Xavier's mime-zip-trojan script does a beautiful job of keeping these attachments out of your inbox:
https://github.com/xme/toolbox/blob/master/mime-zip-trojan.pl
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
The attached file was titled "statement_[ourdomain]_#####.doc" (5 digits)
dotBATman
Anonymous
Oct 27th 2016
9 years ago
btw,
I have a open source / free App that will make domain whitelisting management a lot easier for the IT dept and might help educate users as well.
This is how it works
-set workstation dns server to 127.0.0.1
-configure App to point to your corporate DNS server
-configure App to trust Alexa top 10,000 domains or more if you want.
-Note App uses dnsjack.js, 287 beautiful lines of javascript written by @mafintosh.
-App will NOT bypass your DNS server. Anything blocked on DNS server will be blocked for the user.
-If a user clicks on a phishing link, the user will have to approve the domain, and click the link again.
https://pbs.twimg.com/media/CvkM3vVWgAAm_uv.jpg
https://pbs.twimg.com/media/CvkM5ZrWgAAD9Ui.jpg
Please DM me on twitter if you want more info.
@mabraFoo
Washington D.C.
Anonymous
Oct 27th 2016
9 years ago
Domain whitelisting may help some but it's not really a complete solution. PLENTY of maliciousness can potentially come from domains you will whitelist / the Alexa top whatever. Not saying it won't cut the noise considerably but realistically if the user clicked the link they'll click the approve button too because they didn't open the page by accident. Their logic is "I clicked this of course I want to go here. I get this dumb page any time I'm trying to do anything on the web." It will become automatic. You will be mocked and resented by your users just like Vista users did Microsoft when all the UAC popups started happening.
Anonymous
Oct 27th 2016
9 years ago
Another advantage that an App like this could help with is auditing DNS events. Also, I don't know of a way to easily configure DNS to be strict for some departments and more open for other departments in a company.
Mick Douglas knows a lot more than I do about preventing malware / ransomware. I recommend everyone watch his Derbycon talk. Great stuff!
https://www.youtube.com/watch?v=4MdMSoTiqDM
Anonymous
Oct 27th 2016
9 years ago
technet.microsoft.com/en-us/windows-server-docs/networking/dns/what-s-new-in-dns-server
New functionality: DNS Policies
You can configure DNS policies to specify how a DNS server responds to DNS queries. DNS responses can be based on client IP address (location), time of the day, and several other parameters. DNS policies enable location-aware DNS, traffic management, load balancing, split-brain DNS, and other scenarios.
Anonymous
Oct 28th 2016
9 years ago