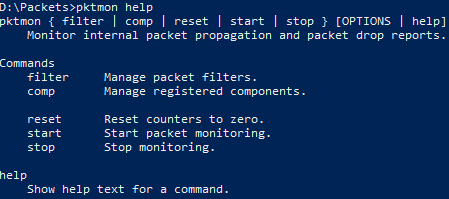
Windows 10 Built-in Packet Sniffer - PktMon
Microsoft released with the October 2018 Update a built-in packet sniffer for Windows 10 located in C:\Windows\system32\PktMon.exe. At ISC we like packets and this is one of the multiple ways to capture packets and send us a copy for analysis. Rob previously published another way of capturing packets in Windows here. If Windows 10 was compromised, this application would be a prime target by malicious actors and it need to be monitored, protected or removed in an enterprise.
In order to collect packets you need to launch a Windows 10 command prompt as admin before using PktMon.
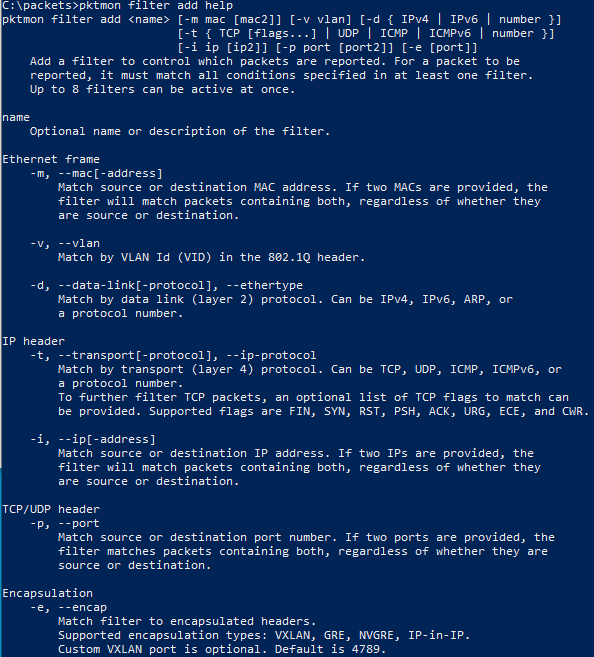
The first thing to do is figure out what can be done with PktMon, if you execute PktMon filter add help it list all posible options by MAC address, datalink, VLAN, protocol, IPv4/IPv6 and services:
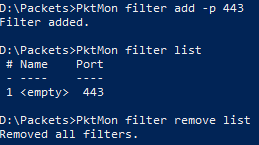
For example, let’s capture SSL traffic on port 443, the filter will look like this:
PktMon filter add -p 443
To view the port filtered list:
PktMon filter list
To remove the same filter when done will look like this:
PktMon filter remove -p 443
To clear the packet port filtered list (capture all ports):
PktMon filter remove list
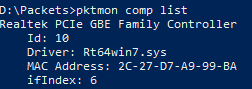
To list the interfaces available for packet capture on Windows 10, use PktMon comp list. This list can contains several interfaces (i.e. wireless, VPN, Ethernet, etc)
Starting PktMon with -p 0 to capture the entire packet (default to 128 bytes), start packet capture from Ethernet interface Id: 10 and save the packets to a log file with Event Tracing for Windows (--etw default filename is PktMon1.etl):
pktmon start --etw -p 0 -c 10
Stopping PktMon you get the traffic statistics from the interface and leave a file PktMon1.etl on the drive where PktMon was started:
The file PktMon1.etl can be converted to text:
pktmon format PktMon.etl -o https.txt
14:08:19.937939100 MAC Dest 0x000C2986BE53, MAC Src 0x247703FD6DE8, EtherType IPv4 , VlanId 0, IP Dest 192.168.25.181, IP Src 192.168.25.165, Protocol UDP , Port Dest 62594, Port Src 3389, TCPFlags 0, PktGroupId 1125899906842838, PktCount 1, Appearance 1, Direction Tx , Type Ethernet , Component 95, Edge 1, Filter 0
Finally, reset all counter back to 0 and get ready for the next packet capture:
PktMon reset
All counters reset to 0.
Microsoft Network Monitor is dated and no longer actively supported by Microsft but until the next release of PktMon in Windows 10 2004 supporting conversion to pcapng, it can be used to open and read these packet capture files or read them as text has previous demonstratred.
[1] https://docs.microsoft.com/en-us/windows/win32/etw/about-event-tracing
[2] https://isc.sans.edu/forums/diary/Packet+Editor+and+Builder+by+Colasoft/24682/
[3] https://www.microsoft.com/en-in/download/details.aspx?id=4865
[4] https://isc.sans.edu/forums/diary/No+Wireshark+No+TCPDump+No+Problem/19409/
[5] https://docs.microsoft.com/en-us/windows/whats-new/whats-new-windows-10-version-2004
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
.PNG)


Comments
Anonymous
Jun 1st 2020
5 years ago
Anonymous
Jun 1st 2020
5 years ago
Anonymous
Jun 2nd 2020
5 years ago
C:\Windows\system32\PktMon.exe
Anonymous
Jun 3rd 2020
5 years ago
-Real-time monitoring of packets
-Conversion of the log find to pcapng format
Which means that we will be able to analyze the log files in Wireshark and other 3rd party packet monitoring tools.
Details Here: https://www.helpmegeek.com/windows-10-packet-sniffer-pktmon-guide/
Anonymous
Jun 3rd 2020
5 years ago